

Emerging Threats Intelligence
Proofpoint ET Intelligence delivers the most timely and accurate threat intelligence. Our fully verified intel provides deeper context and integrates seamlessly with your security tools to enhance your decision-making.
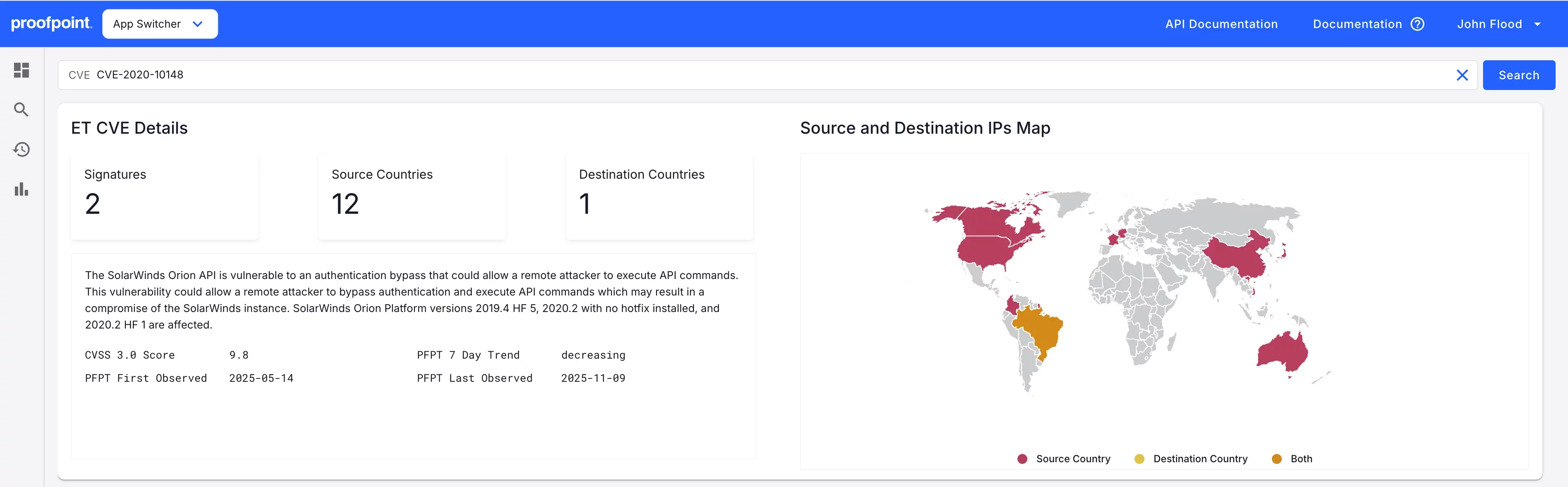
Rich Threat Intelligence and Context Portal
Knowing what types of threats exist is no longer enough to protect your people, data, and brand. Emerging Threat (ET) intelligence helps prevent attacks and reduce risk by helping you understand the historical context of where these threats originated, who is behind them, when have they attacked, what methods they used, and what they're after. Get on-demand access to current and historical metadata on IPs, domains, and other related threat intelligence to help research threats and investigate incidents.
In addition to reputation intel, you get condemnation evidence, deep context, history, and detection information. It's all searchable in an easy-to-use threat intelligence portal that includes:
- Trends and timestamps of when a threat was seen and the associated category
- Type of threat and exploit kit names when available
- Related samples used in associated or related attacks.
Actionable IP and Domain Reputation
Emerging Threat (ET) Intelligence provides actionable threat intel feeds to identify IPs and domains involved in suspicious and malicious activity. All threat intelligence feeds are based on behavior observed directly by Proofpoint ET Labs. And they can all be directly fed to SIEMs, firewalls, intrusion detection systems (IDS), intrusion protection systems (IPS), and authentication systems.

Emerging Threat (ET) Intelligence highlights:
Separate lists for IP addresses and domains
IP and domains that are classified into over 40 different categories
IP and domains are assigned a confidence score for each category
Scores indicate recent activity levels and are aggressively aged to reflect current conditions
Hourly list updates
Multiple formats supported, including TXT, CSV, JSON, and compressed
Tap into our expertise with Threat Intelligence Services
Easy Integration with security tools
Emerging Threat (ET) Intelligence is easily digested by your existing SIEM tools such as Splunk, QRadar, and ArcSight and by threat intelligence platforms (TIPs)

Subscribers get free use of our Splunk technology add-on (Proofpoint Splunk TA). The add-on integrates Emerging Threat (ET) Intelligence reputation into Splunk to quickly surface log entries that appear on reputation lists and is compatible with existing Splunk reporting. Threat intelligence is directly available for use though Anomali (formerly ThreatStream).
Emerging Threat (ET) Intelligence lists can also be downloaded into the Bro IDS format.
For OEM licensing enquiries, please contact our OEM sales
Related Resources
White Paper
Osterman Research: The Value of Threat Intelligence
Data Sheet
Emerging Threats Intelligence
Data Sheet
ET Pro Ruleset
Data Sheet
Emerging Threats Intelligence Features and Usage
Data Sheet
Proofpoint Threat Intelligence Services










