Table of Contents
SQL injection (often abbreviated as SQLi) is a cyber threat that targets applications that use SQL (Structured Query Language) databases. Attackers exploit vulnerabilities in an application’s code by injecting malicious SQL code into queries, enabling them to gain unauthorized access to a private database that may contain potentially valuable information.
An SQL injection attack can lead to various negative consequences, including data breaches, data corruption, and loss of system control. These cyber-attacks target any application that uses an SQL database, with websites being the most vulnerable and commonly exploited targets.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
How an SQL Injection Works
SQL injection exploits the way an application interacts with its backend SQL database. Here’s a concise breakdown of how an SQL injection works:
- Query Construction: Applications often use SQL queries to interact with databases, typically retrieving or storing data. These queries might sometimes be constructed by concatenating, or connecting, strings, with parts of the string coming from user input.
- Malicious Input: If an application doesn’t handle user input correctly, an attacker can provide input with SQL code. Instead of the application recognizing this input as regular data, the database executes it as part of the SQL query.
- Manipulated Queries: When the malicious input is concatenated into the SQL query, it changes the structure or intent of the query. This can allow an attacker to retrieve unauthorized data, bypass authentication, or even execute administrative operations on the database.
The success of an SQL injection attack largely depends on how the application constructs its SQL queries and how it handles user input. Proper measures to sanitize and validate input help prevent these vulnerabilities.
What Are SQL Queries?
SQL is the standard programming language for managing data held in a relational database management system (RDBMS) or stream processing in a relational data stream management system (RDSMS). In simple terms, it’s the declarative programming language used to store, update, remove, search, and retrieve information from the database.
SQL queries are structured commands or instructions written in the Structured Query Language to interact with relational databases. These queries allow users to perform various operations on the data stored in a database, such as retrieving, inserting, updating, and deleting data.
SQL queries can execute a wide range of specific functions within a database, including:
- Retrieve data from a database
- Insert, update, or delete records in a database
- Create entirely new databases
- Build new tables in a database
- Establish stored procedures in a database
- Create views in a database
- Set permissions on tables, procedures, and views
SQL queries are specific commands structured as statements. They are aggregated into programs that allow users to add, modify, or retrieve data from databases.
A few basic examples of SQL queries include:
- SELECT: Intended to retrieve data from tables.
SELECT column1, column2 FROM tablename WHERE condition; - INSERT INTO: Intended to insert new data into a table.
INSERT INTO tablename (column1, column2) VALUES (value1, value2); - UPDATE: Intended to modify existing data in a table.
UPDATE tablename SET column1=value1 WHERE condition;
These are fundamental examples of SQL queries. With capabilities ranging from simple data retrieval to intricate data transformations and analytics, SQL is a powerful and versatile language that allows complex operations and manipulations of relational data.
Types of SQL Injection
SQL injection vulnerabilities arise when malicious SQL codes are interjected into input fields, influencing the subsequent SQL operations. These threats can be broadly segmented into three categories: In-band SQLi, Inferential SQLi, and Out-of-band SQLi.
1. In-band SQLi
This is the most prevalent and straightforward form of SQL injection. In-band SQLi allows the perpetrator to inject malicious code and receive feedback through the same medium. The two most common types of in-band SQL Injection are Error-based SQLi and Union-based SQLi.
Error-based SQLi
By manipulating queries, attackers extract valuable database information from the server’s error messages. Sometimes, this method can even map out the complete database.
Union-based SQLi
This technique hinges on the UNION SQL operator. Attackers merge results from multiple SELECT operations, and the combined data gets reflected in the application’s response.
2. Inferential SQLi
Inferential SQL Injection, unlike in-band SQL Injection, may take longer for an attacker to exploit, but it can still be very effective. In this type of attack, no data is actually transferred via the web application, and the attacker cannot see the result of an attack in-band (i.e., in the HTML of the application’s response). Alternatively, threat actors can reconstruct the database structure by sending payloads and observing the web application’s response and database server behavior. The two primary forms of inferential SQLi are Blind-boolean-based SQLi and Blind-time-based SQLi.
Blind-boolean-based SQLi
Boolean-based SQL Injection works by submitting an SQL query to the database and forcing the application to produce a different response depending on whether the query returns TRUE or FALSE.
Blind-time-based SQLi
Time-based SQL Injection is an inferential SQL Injection technique that sends an SQL query to the database, forcing the application to wait for a specified amount of time (in seconds) before responding.
3. Out-of-band SQLi
Out-of-band SQL Injection is not very common, as it requires that the targeted database can connect back to the attacker’s machine. This type of SQL Injection occurs when an attacker cannot use the same channel to launch the attack and gather results. Instead, the attacker uses a different channel, such as an email, to launch the attack.
To recap, in-band SQLi is the most common and easy to exploit, while Inferential SQLi may take longer for an attacker to exploit but can still be very effective. Out-of-band SQLi is not very common, as it requires that the targeted database can connect back to the attacker’s machine.
SQL Injection Example
While SQL injections can be elaborate attacks, this simplified example puts into perspective how they work.
Suppose there are two database tables, Users Logins and Customer Info. The table for User Logins has two fields for Username and Password. The Customer Info table has additional data, like First Name, Last Name, Address, Email, Phone Number, and Credit Card Number.
An attacker can insert malicious code into a login form to retrieve a user's username and password from the User Logins table. If the attacker enters the following code into the username field,
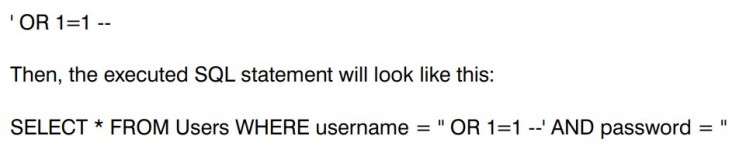
The double hyphen at the end of the statement is used to comment out the remainder of the original SQL statement, which would have also checked the password.
The statement above will always return true because 1=1 is always true, and the double hyphen comments out the rest of the statement. As a result, the password check is ignored, and the attacker can log in without a valid password.
Impacts of an SQL Injection Attack
SQL injection attacks can have various consequences, depending on the attacker’s skills, intent, and the system’s vulnerability. When unauthorized access is achieved, the potential impacts of SQLi attacks include:
- Data Breach: One of the most immediate and damaging effects of SQLi is unauthorized access to the database’s records. Attackers can view sensitive information, such as user credentials, personal details, financial data, etc.
- Data Loss or Corruption: Malicious actors can modify, insert, and delete records, potentially causing loss of data integrity, rendering the data useless, or introducing false information.
- Denial of Service: By locking records, deleting tables, or otherwise disrupting the database, attackers can make the application unavailable to legitimate users.
- Database Server Takeover: Advanced SQLi attacks can result in attackers gaining control over the database server. In cases where the database server isn’t properly segregated from the rest of the network, this can be a steppingstone to further compromises.
- Remote Code Execution: Some database systems allow the execution of system-level commands through SQL. If an attacker discovers and exploits an SQLi vulnerability in such systems, they can potentially execute arbitrary commands on the server, leading to full system compromise.
- Data Exposure: Attackers can utilize SQLi to modify the application’s behavior, potentially revealing confidential information that isn’t normally accessible to users.
- Identity Theft and Fraud: With access to personal and financial details, attackers can commit identity theft, unauthorized transactions, and other fraudulent activities.
- Reputational Damage: Beyond the direct technical implications, companies that fall victim to SQLi attacks risk severe reputational damage. Customers and partners might lose trust in a company’s ability to safeguard their data.
- Financial Consequences: Cleaning up after an SQLi attack can be costly. There might be expenses related to technical remediation, legal consultations, public relations efforts, compensating affected users, and potential fines for data protection regulation violations.
- Disclosure of Intellectual Property: Businesses may store proprietary algorithms, business plans, and other intellectual property in their databases. An SQLi attack can lead to the theft of this valuable data.
Understanding the potential impacts of SQLi underscores the importance of adopting secure coding practices, regular vulnerability assessments, and penetration testing to protect databases and applications from such threats.
Prevention and Detection of SQL Injection Attacks
Preventing and detecting SQL injection attacks requires a combination of secure coding, infrastructure hardening, monitoring, and education. Here are the best practices for SQL injection attack prevention and detection:
Prevention
- Use Parameterized Queries (Prepared Statements): Always use parameterized queries or prepared statements with SQL. This ensures that user input is always treated as data and never as executable code.
- Use Stored Procedures: By using stored procedures, you can abstract out and centralize the data access, limiting the exposure to raw SQL commands.
- ORM (Object-Relational Mapping): Utilize ORMs as they often build on parameterized queries and reduce direct handling of raw SQL, but ensure the chosen ORM is secure against SQLi.
- Escape All User Input: If you must insert data into SQL queries directly, ensure all user input is escaped properly. This can be a backup measure, but it shouldn’t be the primary defense.
- Least Privilege Principle: Ensure that SQL database accounts used by web applications have the minimum necessary privileges. For example, a user account that retrieves data should not have insert or delete permissions.
- Web Application Firewalls (WAFs): Deploy a WAF to filter and monitor HTTP traffic between the web application and the Internet. WAFs can block many injection attacks.
- Disable Verbose Error Messages: Ensure database error messages are generic and do not leak details about the database structure.
- Input Validation: Use a whitelist approach for input validation. Validate all user inputs against a set of strict rules (e.g., type, length, format, and range).
- Regularly Update and Patch: Regularly update database software, web application frameworks, and libraries to protect against known vulnerabilities.
Detection
- Regular Security Audits and Penetration Testing: Periodically conduct security audits and penetration testing to uncover and rectify potential vulnerabilities.
- SQL Query Monitoring: Monitor SQL queries executed against your database to detect unusual or unexpected queries that might indicate SQLi attempts.
- Error Monitoring: Monitor for unusual system or application error messages that might indicate attack attempts.
- Intrusion Detection Systems (IDS): Deploy IDS solutions to monitor and alert malicious activities.
- Log Monitoring and Analysis: Regularly review logs and use automated log analysis to detect signs of attacks.
- Database Integrity Checks: Regularly compare current database structures and contents against a known good backup or baseline to detect unauthorized modifications.
- Educate Developers and IT Staff: Ensure all team members know SQLi risks and prevention techniques.
- Honeypots: Deploy database honeypots to divert and study attackers, which can help detect new SQLi techniques.
Incorporating both prevention and detection mechanisms and maintaining a proactive security posture is essential to guard against SQL injection and other threats effectively.
How Proofpoint Can Help
Proofpoint provides industry-leading cybersecurity solutions that can help combat SQL injection attacks. Some of the company’s solutions in this arena include:
- Insider Threat Management (ITM): Proofpoint’s comprehensive ITM solutions help organizations protect sensitive data from insider threats and data loss. It provides deep visibility into user activities, identifies user risk, detects insider-led data breaches, and accelerates security incident response.
- Advanced Threat Protection (ATP): Proofpoint’s enhanced ATP service includes inline capabilities for stopping zero-day injection attacks.
- Emerging Threat Intelligence: Proofpoint’s emerging threat intelligence solutions provide visibility into the latest tactics, techniques, and procedures conducted by threat actors. With this intelligence, organizations can stay informed about the latest SQLi methodologies and adapt their defenses accordingly.
Organizations that use these Proofpoint products enhance their security posture and protect their databases from SQL injection attacks. For more information, contact Proofpoint.
Get Ahead of Tomorrow’s Threats with Proofpoint
Anticipating the nature of certain cyber threats helps organizations identify where their defenses are weak and which protective measures to prioritize. Most organizations are more resilient through layered strategies that leverage detection and prevention technologies, real-time threat intelligence, and user-focused training programs to reduce the risk of attacks via email and cloud environments. As threats like phishing, BEC, ransomware, and credential theft evolve, it’s important to have the right mix of tools and processes to keep your data and your people protected. Take ownership to protect against threats and make strides to improve your cybersecurity effectiveness.
Leverage the capabilities trusted by 83 of the Fortune 100 companies. Contact Proofpoint to learn more.
Related Resources
The latest news and updates from Proofpoint, delivered to your inbox.
Sign up to receive news and other stories from Proofpoint. Your information will be used in accordance with Proofpoint’s privacy policy. You may opt out at any time.














