Proofpoint Actionable Insights are the additional metrics and insights that the Proofpoint Threat Protection Platform can deliver through our combined data, detection and research. These insights provide the additional detail and context needed to fully understand your threats and the actions you can take to defend against them.
The first installment of our “Actionable Insights” blog series focused on insights around people risk and the meaningful actions organizations can take using those insights. In our second post, we focused more on risk origination, including how we can easily view this information in the Proofpoint Targeted Attack Protection (TAP) dashboard and the different actions we can take with that information.
In this post, we cover business email compromise (BEC) and how you can use targeted controls to reduce your organization’s “BEC risk.”
Visibility is a must for understanding the types of BEC schemes and preventing attacks
Business email compromise (BEC) is a top-of-mind threat for most organizations, and with good reason: In 2021, this technique accounted for almost 20,000 victims in the United States alone, with an adjusted loss of nearly $2.4 billion — making it the #1 internet crime type by victim loss, according to the FBI’s Internet Crime Complaint Center.
Employing attack techniques like impersonation and account compromise, BEC ranks alongside ransomware in terms of both potential business impact and executive focus. That’s why it’s crucial for information security leaders to have visibility into not only what types of BEC schemes attackers are using to target their specific organization, but also how these attacks occur and how to prevent them.
Insights
The Threat Insight dashboard in Proofpoint TAP responds to this need for visibility by continuing to expand on its existing capabilities for reporting and analysis of BEC activity and risk in an organization. Recently added trend reports and threat breakdowns bring even more actionable insights to the existing people-centric reports, providing a complete picture of the BEC activity targeting your organization, including what controls you can implement to help prevent these attacks.
In this section, we’ll dive into five critical questions about BEC that you can answer with the insights found in some of these trend reports.
Question #1. Is my organization protected against BEC threats?
The first step toward understanding your organization’s risk from BEC threats is to measure their prevalence within your overall volume of malicious messages. Then, you can assess the relative effectiveness of your solutions against them.
The Email Threats Effectiveness Overview report shows you how well your organization is protected against all malicious messages combined, as well as by Threat Type. Within the Threat Type breakdown, Impostor Threats represent the BEC messages sent to your organization.
Email Threats Effectiveness Overview
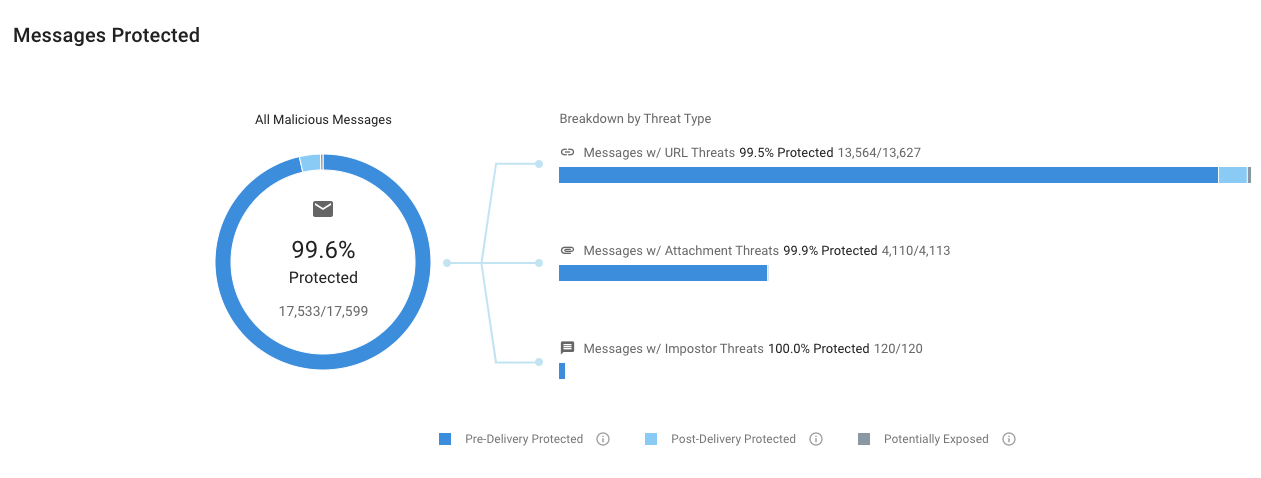
Figure 1. Email Threats Effectiveness Overview summary chart in the Proofpoint TAP Threat Insight dashboard.
Although BEC attacks (Impostor Threats) may represent a small fraction of your organization’s overall malicious message volume, their risk to your business can be disproportionately high. These threats tend to be extremely targeted and will not generate the same volumes that other commodity-based threats tend to generate.
Tracking your overall effectiveness against these threats is important. But having the ability to gauge your effectiveness over time allows your organization to recognize sudden changes in attack volume or success rates so you can adapt your protections appropriately.
You can filter the Messages Protected Trend report to show BEC messages over time and how any changes in volume might have an impact on your effectiveness against them.
BEC Effectiveness
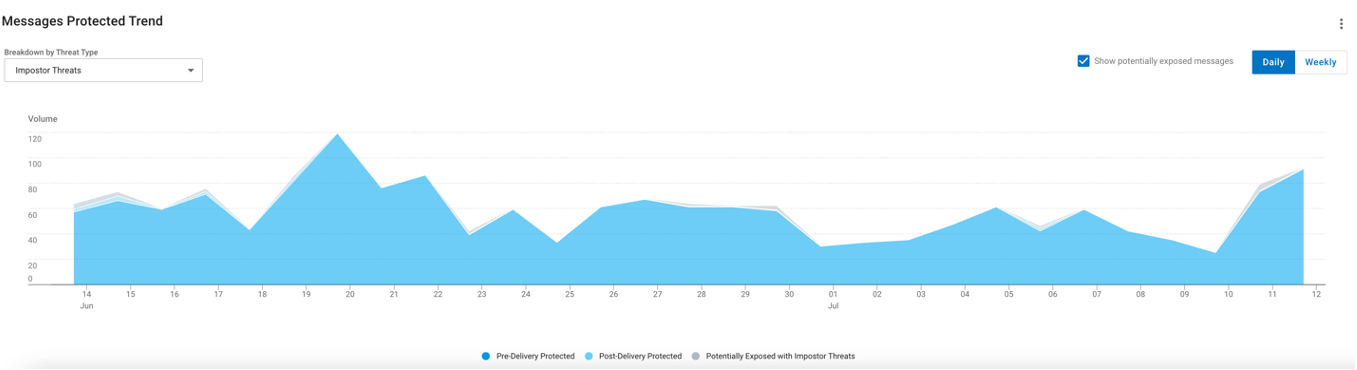
Figure 2. BEC Effectiveness trend chart in the Proofpoint TAP Threat Insight dashboard.
Question #2. How were certain threats determined to be BEC threats?
Having insight into why specific messages were identified and condemned as BEC threats is an important part of this effective reporting. The Observations section in the message reports details on which indicators were detected for a given message, giving investigation and incident response teams deeper insight into the actions of their Proofpoint solutions.
For example, the Uncommon Sender observation indicates that the sender of the message isn’t a regular correspondent with the intended recipient’s organization, while the various forms of spoofing and telltale words point to the suspect nature of the message. Taken as a whole, these combined indicators enable the integrated, holistic BEC protection capabilities from Proofpoint to make high-confidence condemnations of BEC attempts against your users.
At the same time, these observations furnish a trove of information about the specific deception techniques employed by BEC actors. It can also help guide the criteria for defining your organization’s user awareness training content.
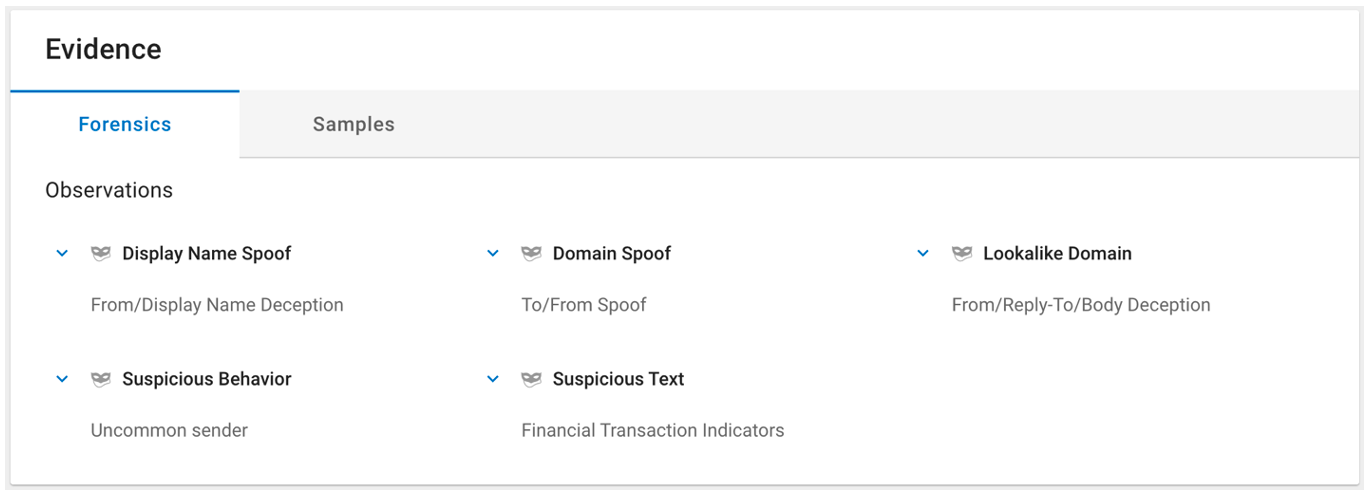
Figure 3. Example of BEC detection Observations in the Proofpoint TAP Threat Insight dashboard.
Question #3. What BEC themes are used against my organization?
BEC threats are not monolithic; in fact, Proofpoint researchers have shown that BEC includes a wide range of tactics and themes. Understanding which themes your organization faces and to what extent is another vital piece of information for understanding your overall BEC risk.
The Top Threat Themes chart provides this insight by allowing you to see which BEC-specific themes attackers are using against your organization.
Top Threat Themes (BEC)
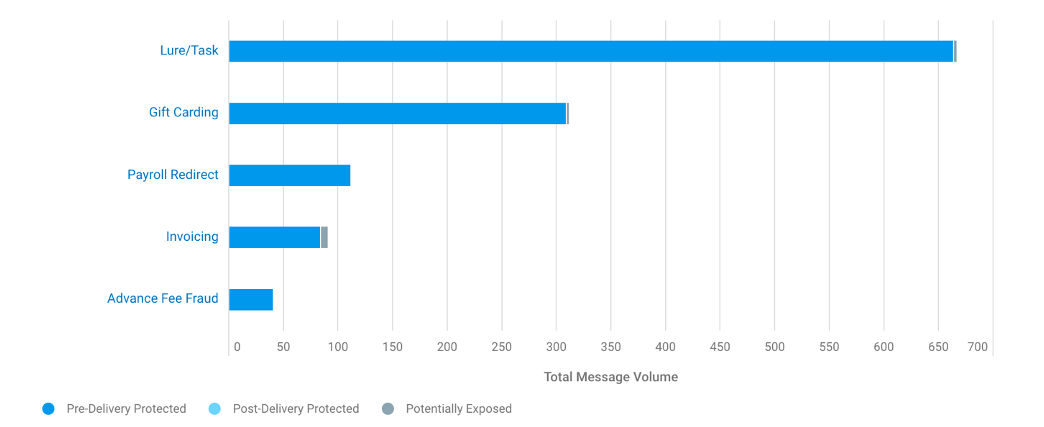
Figure 4. Top Threat Themes for BEC chart in the Proofpoint TAP Threat Insight dashboard.
Question #4. How is each BEC theme being used against my organization?
Just as malware and phishing campaigns will leverage different lures based on the season or news events to improve their social engineering value, Proofpoint threat researchers have found that BEC themes can also vary with the season, breaking news topics or other external events. For example, BEC messages focused on gift card theft might increase in prevalence during the holiday season, while messages designed to steal personally identifiable information (PII), W-2 forms or other user information can predominate in January and February.
Understanding how these trends manifest in your organization’s mail flow—as well as changes in who they target—can help your organization better prepare for likely shifts in BEC threat activity with focused training and additional controls.
The Top Messages Trend chart can be filtered to show BEC Themes and how each one might increase or decrease along with external events.
BEC Themes
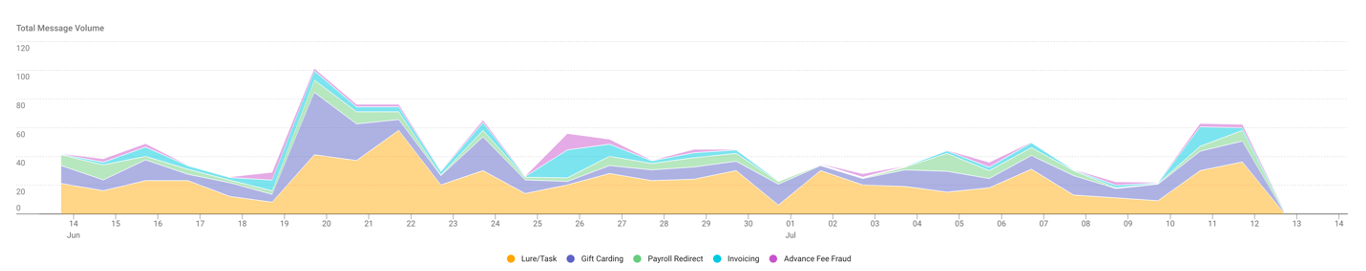
Figure 5. BEC Themes trend chart in the Proofpoint TAP Threat Insight dashboard.
Question #5. Who is being targeted by BEC threats in my organization?
Executives and other sensitive recipients in your organization are often the primary focus of BEC attacks due to their access to sensitive information or ability to transfer funds and carry out transactions.
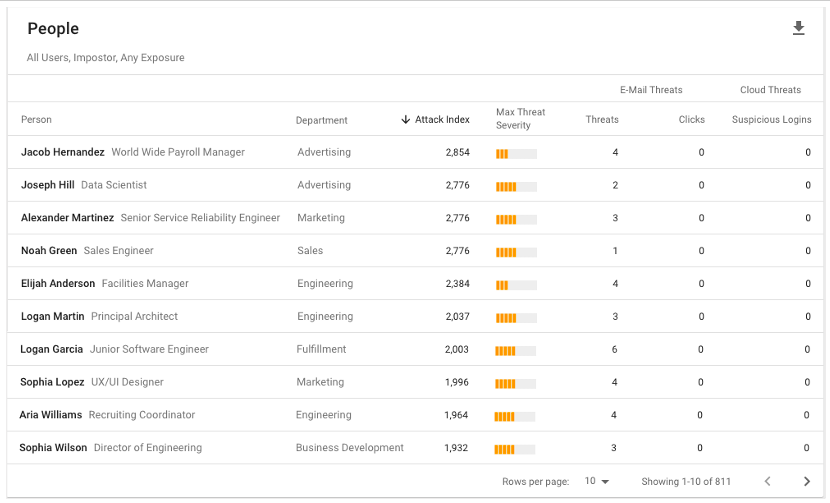
Our People report can be filtered for VIPs who are targeted by BEC campaigns to show you exactly who these people might be.
VIPs targeted by BEC
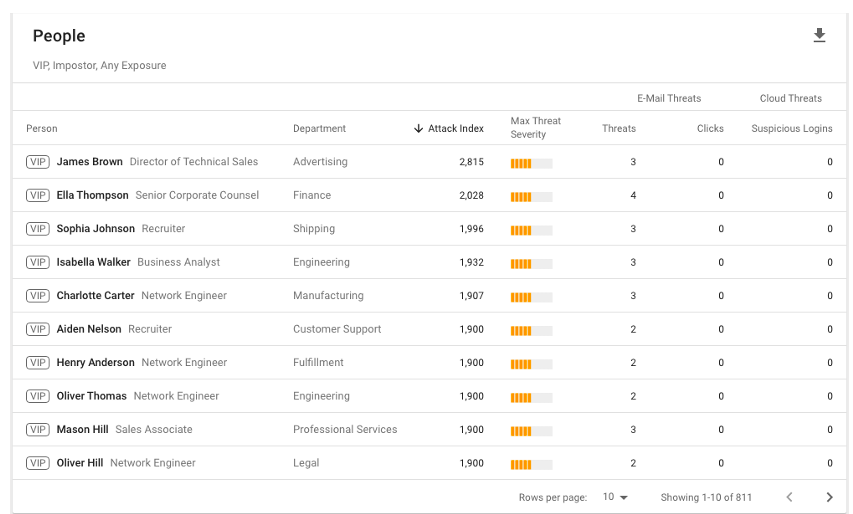
Figure 6. People report of VIP users targeted by BEC in the Proofpoint TAP Threat Insight dashboard.
Beyond that first rank, however, are many employees in your organization who may be subject to less scrutiny or controls but nonetheless may be frequent targets for BEC actors. You can use the same People report to identify this set of users. Then, you can take action based on these insights, such as providing these users with more training or applying more controls to help further reduce the organization’s BEC risk.
Top intended BEC recipients
Figure 7. People report of top intended recipients for BEC messages in the Proofpoint TAP Threat Insight dashboard.
Targeted controls
Going beyond standard reporting and forensics, the actionable insights around BEC in the Proofpoint TAP Threat Insight dashboard enable organizations to also understand which actions they should take to defend themselves, based on the tactics attackers are using to target them.
Frequently recommended actions and controls based on these reports include:
- Providing additional training for frequently targeted users, with training focused on the BEC themes the organization is seeing
- Updating business processes for certain scenarios, such as:
- Account changes
- New account requests
- Employee payroll changes
- Applying additional financial controls for users targeted by BEC
- Implementing Proofpoint Threat Response Auto-Pull (TRAP) to pull back delivered BEC messages
If you’d like help identifying the biggest digital threats to your business, please reach out for a free digital risk assessment from Proofpoint. Our complimentary risk assessments are conducted by Proofpoint security experts who can help you identify some of the most significant threats to your organization—including your BEC risk—and show you how to mitigate them.
To learn more about the capabilities that Proofpoint provides to help protect your organization from BEC and other email threats, see this page on our website.