Have you ever stopped to think about the countless choices you make each day? From ordering your morning coffee to deciding which email to open first, choices are an integral part of our lives.
Many of these choices are influenced by nudges—interventions designed to guide our decisions toward an optimal outcome, often without us even realizing it. This is also known as “nudge theory.”
What exactly is a nudge?
Nudges are deliberate interventions designed to shape human behavior. They gently steer people toward desired choices. They are rooted in the principles of behavioral science and choice architecture and use cognitive biases and heuristics to guide us in a particular direction.
Let’s consider a familiar scenario: Picture yourself at an ATM, about to withdraw cash. As you complete the transaction and eagerly await your money, the machine returns your debit card first before dispensing the cash.
This seemingly minor design choice is a nudge—a gentle push that reduces the probability that you will make the “post-completion error” of forgetting to take your debit card.

Figure 1. ATM machine returning an ATM card.
Why are nudges seen as teaching tools?
Consider the ATM example. When you have achieved your goal (get cash), you may not think about what needs to happen next (retrieve your debit card). The nudge is a teaching tool in that it helps your mind to learn that the goal is not finished until you have your debit card in-hand. Being nudged to retrieve your debit card creates a habit.
Applying nudges in security awareness education
The fascinating aspect of nudges is that they extend beyond everyday scenarios like the ATM example. They can also be applied in security awareness training, where shaping human behavior plays a crucial role in mitigating cybersecurity risks.
Consider the Google Chrome browser, which employs various nudges to protect users. The lock icon in the address bar, for instance, provides a visual cue indicating a secure connection.
Google Chrome warns you when you are redirected to a common URL that is misspelled (see Figure 2). You are asked right away if you want to go to the more commonly known URL. This nudge helps users identify potential homographic spoofing attempts, where malicious websites imitate legitimate ones by using similar-looking characters.
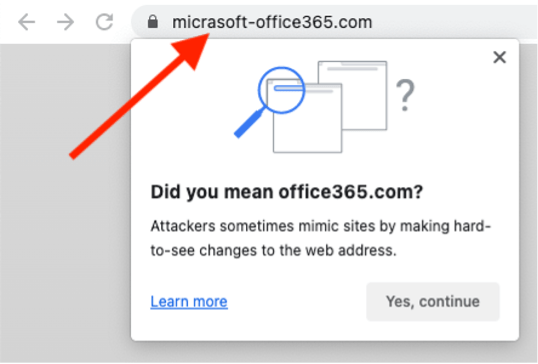
Figure 2. Web-browser nudge prompting user to double-check the URL.
The implementation of Email Warning Tags (EWT) in corporate email systems is another example. These tags serve as reminders for users to exercise caution and evaluate the trustworthiness of emails from external sources. By highlighting that a message came from outside the business, users are nudged to apply a more critical mindset when assessing potential security risks.
What’s more, some implementations, such as from Proofpoint, include a “Report Phishing” button that makes it easier to finish the desired action. The user can choose to continue their interaction with the message. But if they believe the message is malicious, they can report it with a simple click of a button.
Harnessing nudges for positive security behaviors
Nudges in security awareness training focus on highlighting risks—but they also aim to reinforce and drive positive security behaviors. By incorporating nudges that promote password best practices and hygiene, secure browsing habits, and cautious email practices, businesses can strengthen their security postures. Nudges serve as gentle reminders, guiding users toward making choices that mitigate common vulnerabilities. That, in turn, helps to foster a security-conscious culture.
For example, you can use nudge theory to encourage employees to create strong, unique passwords. By implementing password complexity meters and providing immediate feedback (see Figure 3), users are nudged toward selecting more robust passwords.
You can also use nudges to remind users to verify the authenticity of websites before sharing sensitive information. This helps to promote safe browsing habits.
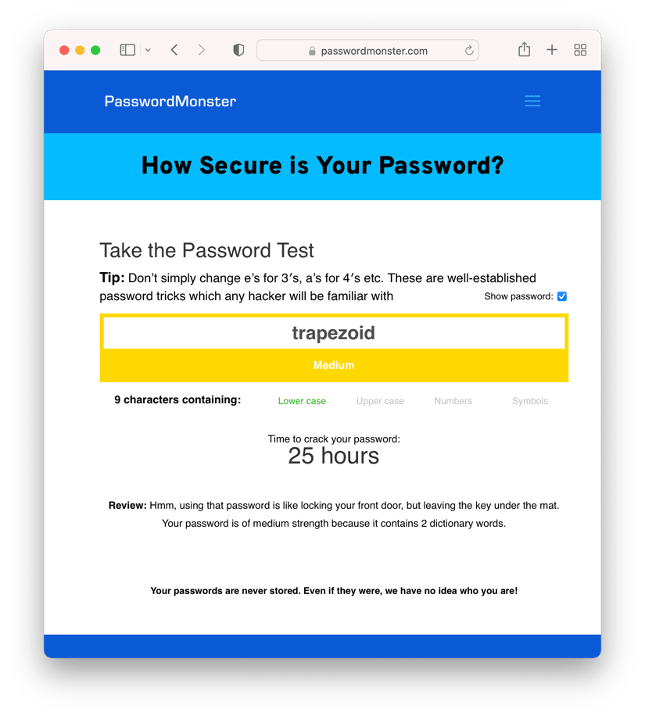
Figure 3. Example of a nudge that includes a complexity meter.
Nudge limitations
Nudges offer valuable contributions to security awareness training, but they have limitations.
First, the nature of a choice architecture is limited in some companies that are under strict compliance requirements. For example, in this environment if you give employees a choice to ignore a warning message it can have a disastrous impact on the business. Further, if you provide guard rail it may also not be ideal. Consider the previous password example. Technically, users could create simpler passwords that are more likely to be cracked while still adhering to password policies.
On the flip side, developing nudges that are extremely intrusive to an employee’s everyday life could have the opposite effect of the desired reaction. For instance, locking up a computer after short periods of inactivity is a nudge to prevent unauthorized access. But frustrated users may find workarounds, such as placing a clock under an optical mouse to trick the system into believing they are active. This example highlights the delicate balance required when implementing nudges, as user satisfaction and ease of use must be considered.
Finally, another limitation is the potential for users to simply resist the nudge. If nudges are too intrusive or complex, it’s more likely users will become frustrated and ignore the warnings. It’s crucial to strike the right balance between nudging users toward secure behaviors and respecting their autonomy.
The need for a holistic approach: nudges + behavioral learning principles
Overcoming the limitations of nudges in security awareness training requires a more comprehensive approach. The solution involves combining nudges with learning science principles to create a dynamic, adaptive security awareness training program.
Learning science principles consider the complexities of human behavior. They also provide a framework for sustained behavioral change. Behavioral learning programs use elements like personalized feedback, interactive learning modules and continuous reinforcement to help users become active participants in their cybersecurity journeys.
An example of this strategy is to combine simulated phishing exercises with personalized feedback. Employees are exposed to simulated phishing emails, and their responses are tracked. Instead of just nudging them when they fall for a phishing attempt, learning science principles can be applied to provide personalized feedback, highlight the red flags they missed and explain potential risks.
This approach enhances learning and helps employees develop critical-thinking skills so that they can better evaluate future email threats.
More to come on nudges
Nudges can be powerful tools for shaping behavior, and they have a role to play in security awareness training. But they also have limitations when it comes to addressing the intricate challenges of cybersecurity.
In the next blog in this series, we’ll delve deeper into the concept of behavioral learning and its integration with nudges. By combining nudges with learning science principles, companies can create a comprehensive training program that empowers users to make informed decisions and take an active role in safeguarding against cybersecurity threats.
Meanwhile, if you’d like to explore this topic further, you can download our white paper. You’ll get more insight into the role of nudges with learning science in cybersecurity awareness.











