Bad actors commonly impersonate senders in email attacks, which can include everything from phishing to business email compromise (BEC) and ransomware. One way to protect against these types of attacks is to check if a message is being sent by an authorized source.
Email authentication provides a proven way to verify the authenticity of an email message, ensuring that it was sent by the sender it claims to be, and verifying that it hasn't been tampered with during transit.
Below are the standard email authentication methods in use today:
- SPF (Sender Policy Framework). SPF allows domain owners to specify the IP addresses authorized to send email on behalf of their domain.
- DKIM (DomainKeys Identified Mail). DKIM adds a digital signature to each outgoing email.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance). DMARC builds on SPF and DKIM to provide additional email authentication and reporting capabilities.
For email that passes DMARC, visual indicators also indicate an email is safe. For example, a brand logo may be displayed in email clients that support BIMI (Brand Indicators for Message Identification), or a blue checkmark verification icon may appear next to the brand’s name in Gmail.
Recent headlines, however, have put the effectiveness of SPF into question. In one recent attack, emails impersonating a large shipping carrier were labeled as authentic under Gmail’s blue checkmark verification program. The attacker was able to impersonate an authorized sender by exploiting an overly permissive SPF record. The attacker’s messages passed SPF, so they met the DMARC requirement to display a brand logo and a blue check in Gmail. Ultimately, the incident led Google to require that messages pass DKIM validation and not rely on SPF for authentication.
Should security teams be concerned about SPF?
Given the vulnerability raised above, the short answer is yes. The longer answer, however, takes into account the fact that SPF supports important mail flows by identifying authorized sending servers and can’t be removed from the suite of useful email authentication technologies. DKIM alone, for example, may fall prey to replay attacks that may be detected if the malicious messages are sent from unauthorized servers.
The next question, then, is how can you effectively deploy and manage a reliable set of SPF records? Below are some suggestions. More detailed information can also be found in the “Best Practices for Managing SPF Records” published by the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG).
Tips for minimizing the risk that SPF can be abused
1. Strive to only publish dedicated IP addresses in your SPF record
Risk Scenario: When you authorize a service to send email to your customers on behalf of your domain, it’s inherently risky. You must rely on the service to maintain a positive reputation for the IP addresses used to send email for you. Should another customer of the service send spam, any shared IP addresses will adversely impact the reputation of your mail flow. If the service doesn’t provide adequate control over shared features, you want the ability to clearly segment your flow from other potentially problematic flows.
While not always possible, the most effective way to control what servers are authorized to send email on behalf of your domain is to identify them directly. And, preferably, the authorized IP addresses would be either in your direct control or at least dedicated for your use. Some SaaS partners offer the option to pay for dedicated IPs. But if getting dedicated IPs is not an option, you can always use an email gateway solution, which can relay your messages through dedicated IPs.
Unfortunately, most cloud-based services share IP addresses across all their clients, which leads to the next point about minimizing the allowed addresses.
2. Minimize IP Addresses in your SPF record, especially shared IP space
Risk Scenario: In this example, let’s look at a broad include record: “include:spf.protection.outlook.com”. This record allows anyone that uses the recommended include to send as their domain and pass SPF (and potentially DMARC).
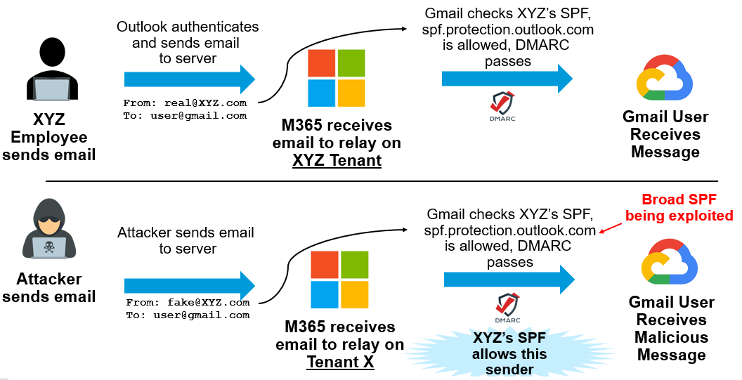
Example of broad "SPF Include" being abused.
Most reputable large-scale sending services provide controls that are designed to protect against multi-tenant abuse. Unfortunately, abuse is still possible by bad actors that have valid accounts using the shared service. For this reason, it’s important to minimize exposure by only including the fewest authorized SPF records possible.
3. Carefully consider and deploy dynamic SPF macros
Risk Scenario: When publishing a complete, static SPF record, you are announcing to the world all the IP addresses being authorized. This gives an attacker the ability to easily detect what services your company uses and to quickly deploy an effective attack strategy without tipping you off.
While most email administrators are familiar with static SPF records, dynamic SPF macros can be intimidating to set up and manage. Any reasonably complex sending architecture, where you rely on dozens of independent services sending on your behalf, can benefit from a well-designed dynamic SPF macro. Not only will it mask authorized services from malicious actors reconnoitering how to attack your mail flows, but it can vastly improve your effectiveness in monitoring and managing your SPF record as discussed next.
NOTE: Dynamic SPF macros can be complicated to set up correctly. Moreover, some SPF macros don’t handle unexpected queries properly, which means spoofed emails will get delivered even if the DMARC policy is set to reject or quarantine. So, if you’re thinking about migrating to hosted SPF services, take some time and make sure to choose the right vendor. Look for one that has experienced professional service resources to ensure proper implementation.
4. Regularly audit your SPF record
Risk Scenario: Two years ago, your marketing department started using a third-party email marketing provider and requested that the provider be added to your SPF record. However, that relationship ended a couple of months ago. But you were not informed, so it is still listed as an approved sender. Recently, the provider became compromised and started sending malicious emails to your customers. These emails will pass authentication, and your brand reputation may suffer as a result.
Think about issues that have plagued firewalls for decades where rules are added but never audited and deleted, which leads to an overly permissive policy. It’s the same with your SPF. That’s why it is a best practice to audit the usage of SPF entries. This ensures that only necessary entries remain. Having a solution that supports visibility across all three types of email (inbound, B2C and B2B) and SPF telemetry can help to identify inactive senders as well as draw attention to large, shared IP ranges that can be a source of attack, like in the first risk scenario above.
Having a solution that supports SPF telemetry can help spot these inactive accounts as well as draw attention to large IP ranges that could be a source of attack.
Proofpoint Can Help
You can minimize your risks by actively managing your SPF record and applying best practices. And the good news is you don’t have to do this all on your own.
Proofpoint offers a wide range of solutions. We offer everything from secure email gateways that enable sending messages from dedicated IPs, to email authentication solutions including hosted DKIM and hosted SPF. In fact, SPF telemetry is now a standard feature in the hosted SPF service provided by Proofpoint Email Fraud Defense. It provides complete visibility into authorized sending IPs so that you can see which IPs are actively sending and which are not.
For more information, contact your Proofpoint account team to discuss how we can help improve your security posture and reduce your overall risk.











