Overview
Threat actors are always looking for ways to exploit vulnerabilities and as a cyber security community, our goal is to minimize their effectiveness and act quickly when vulnerabilities are discovered. When cyber security professionals find a weakness or a loophole that allows protections to be bypassed, it is incumbent on them to bring awareness to those that can correct it.
Cooperation can sometimes come from the least likely source. Case in point, Proofpoint’s Email Fraud Defense consultants discovered a vulnerability in a competitor’s solution, Valimail, and holding true to their belief that protecting customers comes first, they reached out to Valimail with the details of this vulnerability so threat actors could not exploit it before it could be remediated.
So, what was the vulnerability, how did Proofpoint discover it and what has Valimail done to address it? Let’s take a closer look at each of these points.
The Vulnerability
The problem arose because of how temporary errors were handled in Valimail’s SPF (Sender Policy Framework) macro solution, a competitive solution to Proofpoint’s Hosted SPF solution. This vulnerability allowed potential attackers to bypass an organization's DMARC (Domain based Message Authentication, Reporting, and Conformance) policy, enabling successful domain spoofing, even in cases where a DMARC reject, or quarantine was set.
The issue was present because their macro uses a HELO/EHLO as a parameter for querying the SPF macro. The HELO/EHLO is set by the sender when they are sending the message and can be defined by the sender. If the sender set the HELO/EHLO to a value that causes a DNS (Domain Name Service) error from Valimail’s DNS, such as a word containing an underscore, then this would result in an SPF temperror. Based on the DMARC specification, the advertised DMARC policy should not be applied in the event there is an SPF temperror and DKIM (Domain Key Identified Mail) does not pass, allowing for this policy to be bypassed and the domain to be successfully spoofed.
The Vulnerability: How It Works
The vulnerability centers around Valimail's SPF macro, which is incorporated into a customer's SPF record when opting for their SPF hosting service. SPF macros are used by various vendors to enable a vendor to host and manage your SPF record.
Valimail's current SPF macro include is as follows:
include:%{i}._ip.%{h}._ehlo.%{d}._spf.vali.email
Valimail has three parameters in this record:
%{i} – IP of the sender
%{h} – HELO/EHLO domain
%{d} – Domain of the sender
While the sender's IP address and domain are fixed values determined by the source and envelope sender of the message, the HELO/EHLO domain parameter can be customized by the sender. Our research revealed that setting the HELO/EHLO to a value containing an underscore resulted in a REFUSED response from Valimail's DNS.
This REFUSED response triggers a SERVFAIL when the receiver queries the SPF record, causing the SPF result to become a temperror. Section 6.6.2. of the DMARC specification (RFC 7489) states the following about the handling of temporary errors within SPF or DKIM when no other methods pass for DMARC:
“If neither SPF nor DKIM passes and one or both fail due to a temporary error, the advertised DMARC policy of reject or quarantine should not applied.”
By being able to consistently create a temporary error for any customer using Valimail’s SPF macro a threat actor would be able to reliably prevent the DMARC policy of reject or quarantine from being applied to any recipient that was following the DMARC specification and successfully spoof their domain.
The Vulnerability: Wide Reach
Extensive testing revealed that major email providers like Yahoo, AOL, Verizon, Outlook, Sbcglobal, BTInternet, and Orange.fr adhere to the DMARC specification and do not apply the advertised DMARC policy when faced with a SPF temperror result is returned. Consequently, any domain employing Valimail's SPF macro, with a DMARC reject or quarantine policy, was susceptible to this bypass attack.
The Vulnerability: Example
When a valid query is made, the Valimail SPF macro returns "v=spf1 ~all". For instance, with the parameters set as follows:
%{i} – 1.1.1.1
%{h} – validhelo
%{d} – valimail.com
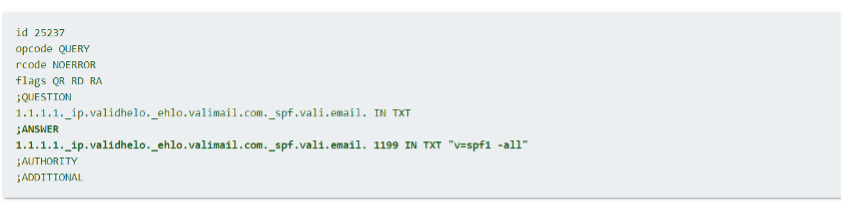
Figure 1. Screenshot of response from a dig query to Valimail’s DNS providing the expected response.
However, when the HELO/EHLO parameter is modified to contain an underscore, such as “test_helo” Valimail’s DNS would respond back with a REFUSED, leading to a SERVFAIL. In the below query the parameters were set as follows:
%{i} – 1.1.1.1
%{h} – test_helo
%{d} – valimail.com
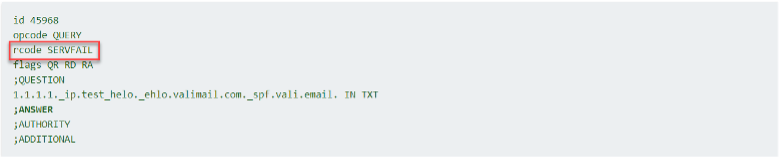
Figure 2. Screenshot of response from a dig query to Valimail’s DNS with an RCODE of SERVFAIL which would cause an SPF temperror.
The headers below show that an example to Yahoo where an SPF temperror resulted in delivery of the message, even though the domain was at p=reject and the message did not pass DKIM.
Received: from 161.35.127.159 (EHLO test_helo)
by 10.217.151.75 with SMTP; Thu, 22 Oct 2020 00:25:31 +0000
X-Originating-Ip: [161.35.127.159]
Received-SPF: error (error in processing macrotest.dmarclab.com)
Authentication-Results: atlas303.free.mail.ne1.yahoo.com;
dkim=unknown;
spf=temperror smtp.mailfrom=macrotest.dmarclab.com;
dmarc=success(p=REJECT) header.from=macrotest.dmarclab.com;
To: macrotesting@yahoo.com
From: test@macrotest.dmarclab.com
Subject: test
The Vulnerability: Responsible Disclosure and Remediation
Proofpoint reached out to Valimail to disclose its findings. Valimail has addressed the vulnerability with an update to their SPF macro solution ensuring their DNS is able to handle responding to queries where the EHLO/HELO includes an underscore.
Conclusion
The successful identification and resolution of the vulnerability in Valimail's SPF macro solution underscores the paramount importance of continuous collaboration within the cyber security community, especially in the face of evolving threats.
We all need to stay one step ahead of the latest threats, which means actively monitoring your SPF record and taking advantage of Hosted SPF solutions that can limit your IP exposure. DKIM and DMARC are also essential email authentication protocols to protect against sender impersonation attacks.
When it comes to successfully implementing and maintaining your SPF, DKIM and DMARC implementations, it is important to partner with a company that has the knowledge, experience, and expertise to guide you on your journey. One that has the skills to detect vulnerabilities and will work for the greater good to get them resolved.
Armed with one of the largest and most diverse data sets in the industry, Proofpoint’s Email Fraud Defense consultants offer unrivaled expertise in email authentication, going beyond just helping customers get to DMARC reject but helping to understand and mitigate ongoing risks and ensuring optimal email hygiene.
For more information on Proofpoint’s Email Fraud Defense solution, visit: https://www.proofpoint.com/us/products/email-protection/email-fraud-defense.











