Phishing is one of the most common attack strategies for cyber criminals. Why? Because it works.
Research for our latest State of the Phish report found that 84% of organizations in 15 countries around the globe experienced at least one successful phishing attack in 2022. And more than half (54%) of businesses included in our survey reported facing three or more of these attacks.
While we all might get tired of dealing with the constant threat of phishing emails, attackers certainly don’t tire of using this tactic. In fact, they probably never will. Phishing is the easiest and cheapest way to obtain what they want—whether it’s monetary gain or access to sensitive data or systems.
Before we look at some common and emerging phishing methods, here’s a quick definition of phishing: It’s a common type of cyber attack and a form of social engineering that targets individuals through email, text messages, phone calls and other forms of communication. While attackers’ goals vary, the general aim of phishing is to steal personal information or credentials.
An overview of evolving techniques to help with understanding phishing emails
To learn how to avoid phishing effectively, you have to know how to identify phishing emails, of course. But understanding what to look out for isn’t easy. Because phishing is so “cost-effective” for cyber criminals, they keep evolving their methods, innovating new techniques to bypass security controls.
Here are some examples of evolving phishing tactics to recognize:
MFA phishing
As multi-factor authentication (MFA) becomes a security standard for organizations, attackers have figured out ways to bypass this critical security control.
Attackers have developed phishing toolkits that can bypass MFA or steal user credentials and MFA tokens. In an MFA phishing attack, attackers trick their targets into giving up the additional credentials that are used for authentication. Or malicious actors can trick victims into approving a fraudulent login request generated by an MFA solution.
EvilProxy is a popular example of an MFA phishing toolkit. When victims click on a malicious URL they are presented with what appears to be the login page of a legitimate site. But rather than just stealing those credentials, a proxy on the page communicates with the legitimate site, authenticating the login and sending back server responses to the actor-controlled site. That way, the victim believes they are interacting with the site as normal, while the attacker can log in using the stolen authentication cookie.
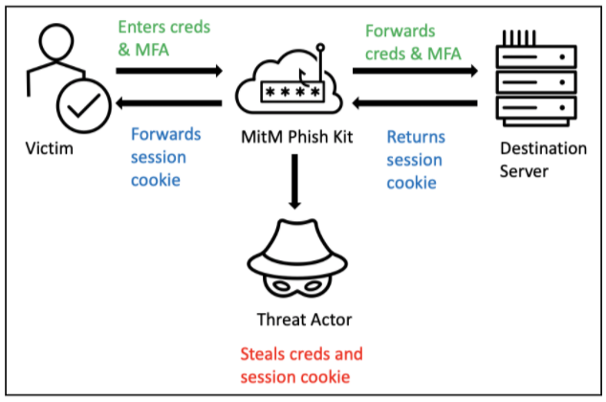
EvilProxy uses a transparent reverse proxy to fool victims into thinking they are interacting with the legitimate site as normal, allowing attackers to capture credentials in real time.
Telephone-oriented attack delivery (aka callback phishing)
Telephone-oriented attack delivery (TOAD) is another emerging threat. It combines email and voice phishing techniques. A TOAD attack often starts with an email in which attackers pretend to be someone from a customer service or support department.
Bad actors will trick victims into calling the number enclosed in the email, offering to help resolve a problem that didn’t exist in the first place. The end game is to get victims to disclose sensitive information over the phone, such as credit card numbers, login credentials or personal information. Attackers may also persuade victims to enable remote access or even install malware on their own machines.
As we noted in our State of the Phish report, Proofpoint has observed, at peak, over 600,000 TOAD messages sent per day. The number has been steadily rising since the technique first appeared in 2021.
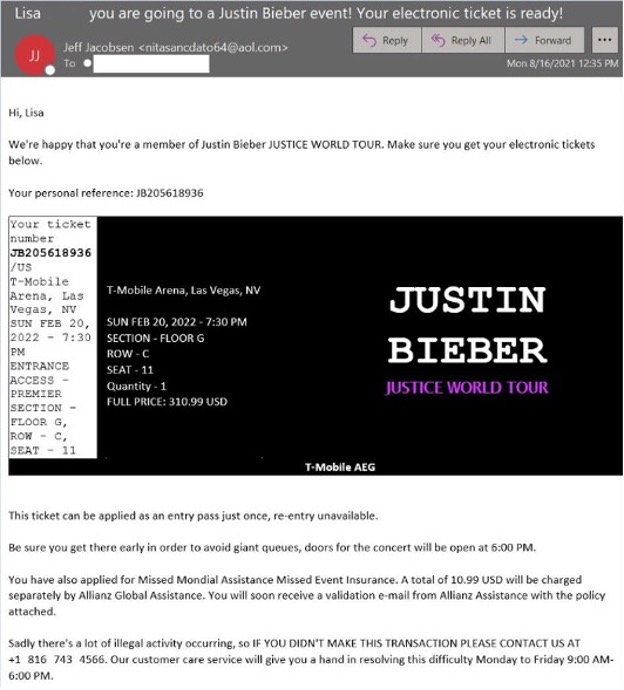
The phone number in this Justin Bieber-themed email scam took victims to the BazaCall threat actors.
Chatbot phishing
Generative AI (gen AI) has become a trending topic. You can bet that attackers are already exploring ways to make the most of this emerging technology in their phishing attacks. ChatGPT, for instance, can be used to generate the email body for a phishing threat, or improve grammar or randomize attacks.
While ChatGPT has not been broadly used in targeted spear-phishing attacks—yet—it may soon be able to produce extended prose in the style of famous reporters, authors, bloggers or anyone else who is active in publishing comments on social media platforms. In short, cyber criminals could use an AI-powered chatbot to improve the credibility and the quality of their phishing emails.
How to spot a phishing email: common characteristics
Since people are the primary target of these evolving phishing attacks, you want to empower them with the right knowledge and tools to recognize phishing emails and protect themselves and your organization. Here are some tips to share with your employees on how to identify phishing emails.
Fear or dear
Nine times out of 10, attackers and scammers will try to manipulate our emotions. And one of the most common emotional tools that we see in phishing attacks is fear. There’s fear of missing an opportunity, fear of money loss, fear of offending somebody, fear of getting locked out of the account—the list goes on.
Sometimes it’s the opposite—attackers may lure victims with things that seem “too good to be true.” This is where attackers offer victims something valuable, such as gift cards, free money or free tickets. For instance, during the pandemic, we saw a lot of COVID-19-themed scams in which fraudsters tricked their targets with fake pandemic-relief stimulus checks.
To obtain these lucrative “free goods,” attackers only ask for something with little cost to the targets, like filling out a quick survey or a simple form. They convince their targets to interact with a phishing link in the email designed to steal their credentials or get them to download a piece of malware.
A sense of urgency
In phishing attacks, fear and a sense of urgency often go hand in hand. Attackers will urge victims to take immediate action, so they don’t have time to think, increasing the success rate of their attack. Common themes that are used to create a sense of urgency include:
- Suspended account
- Urgent payment request
- Unauthorized charges
Remind your employees to beware of urgent or threatening language in the email’s subject line or email body. If they ask you how to stop a phishing email, tell them that thinking twice before they act on a request will go a long way toward avoiding a successful attack.
Someone you trust
It’s much easier to trick people if a phishing email appears to come from someone they trust. Often, an attacker will pretend to be the victim’s manager or colleague. Gift card scams and payroll redirect scams typically involve requests that appear to come from a colleague.
In recent years, attackers have even turned the supply chain into another threat vector, impersonating suppliers or using compromised third-party accounts to get to their targets. One of the most concerning business email compromise (BEC) themes is supplier invoicing fraud, in which fraudsters trick their victims into making a wire transfer or financial payment with a fake invoice or a forged bank account change request.
Sad though it is to say, where email is concerned it’s important that we trust no one. Don’t believe everything we see. Even if the email seems to come from someone we know or from a well-known brand, it could be a phishing email. Phishers know this game extremely well—brand logos, layout, language and email addresses are well-tailored to the recipients. Just because emails look legitimate, it doesn’t mean they are.
Display name spoofing
Spoofing the display name of an email is a favorite phishing tactic. The email appears legitimate because most inboxes and mobile devices only present the display name.
Many of us access our email via mobile phones. When we glance at an email that seems to be from a trusted brand or someone we know, we tend to respond to it. However, if we take an extra step by hovering over the display name, it is obvious that the sender is not who they say they are.
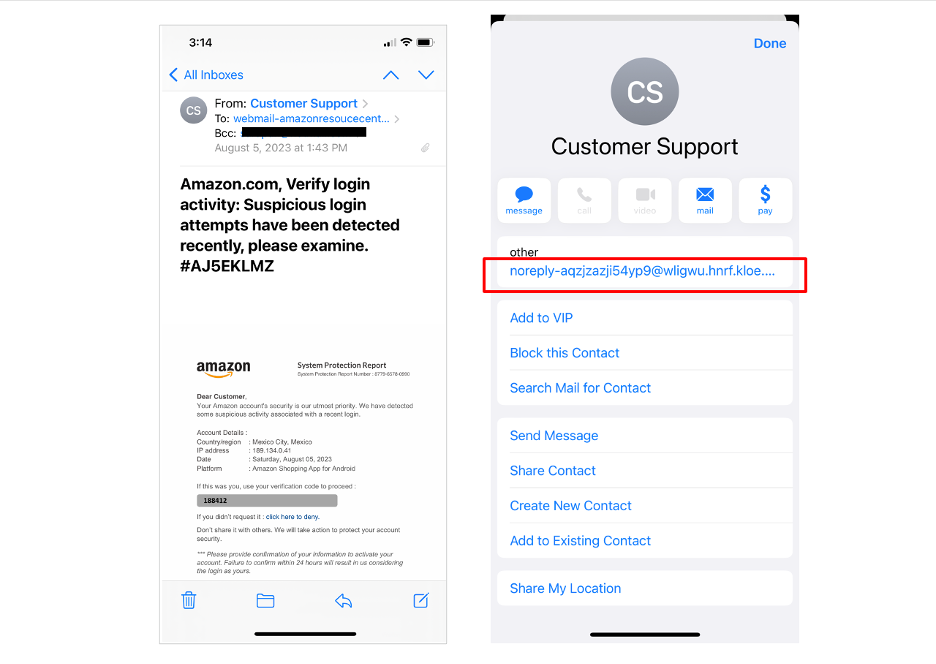
This email appears to come from Amazon’s customer support. Clicking on the display name shows that the sender’s email is not from Amazon.
Quick tips on how to spot phishing emails and avoid them: Do’s and don’ts
We just reviewed some commonly used phishing tactics and evolving strategies. Now, here is a brief overview of some do’s and don’ts for your employees to keep in mind as they learn how to avoid phishing and become more proactive defenders.
Do:
- Report anything suspicious
- Validate the sender’s email address
- Beware of urgent language
- Confirm the request via another channel
- Open a new window to access the official website
Don’t:
- Be so quick to reply
- Trust the display name
- Give up personal or company information
- Click on unexpected URLs or attachments
- Believe everything you see
These tips can help your users learn how to identify phishing emails more effectively—and answer the common question, how can you identify a phishing email in the real world—and reduce the risk that they will respond to or otherwise interact with a phishing ploy. (If that happens, here is what to do if they respond to a phishing email and ways to help mitigate the damage.)
Case studies of real phishing attacks
If you’re looking for real-world examples of phishing attacks to help educate your users, download a copy of Phish in a Barrel. It includes several recent case studies from around the globe and includes recommendations for helping employees learn how to identify a phishing email.
Prevention: more resources to help users learn how to avoid phishing
No matter if it’s MFA phishing, TOAD attacks or ChatGPT phishing, attackers rely on people to activate these threats. They exploit human vulnerability by manipulating our emotions and trust.
National Cybersecurity Awareness Month in October is an ideal time to focus on empowering your employees by educating them on trending threats and the tactics used to target them. To jump-start your Cybersecurity Awareness Month planning, check out our Cybersecurity Awareness Hub, where you can find resources, including a complimentary cybersecurity awareness kit, podcasts, e-books and more.
For more information about how Proofpoint can help drive behavior change and reduce people risk, check out Proofpoint Security Awareness.
To learn more about how Proofpoint stops evolving phishing attacks, review our blog post, “A Defense-in-Depth Strategy to Phishing Prevention.”
For details on our industry-leading anti-phishing security platform, see this page.











