We’ve just wrapped up the first day of Proofpoint Protect 2023, and I can’t want to share a few of the highlights of our premiere customer event. It’s our first in-person conference since the pandemic—and not surprisingly, the energy is off the charts. I couldn’t be more excited to reconnect with our customers and other cybersecurity leaders from all over the world.
For those who couldn’t attend, here are just some of the highlights of day one.
Proofpoint innovations in AI and ML
Proofpoint continues to innovate to help organizations break the attack chain at every stage. We have one of the most comprehensive human communication data sets in the security industry, scanning:
- 2.8 trillion email messages per year
- 17 trillion URLs per year
- 1.3 trillion SMS and MMS per year
We also provide data loss prevention (DLP) across 46 million end users. We are the market leader in insider threat management and the No. 2 (and fastest-growing) DLP vendor in the world.
All of this matters because it allows us to deliver ML- and Al-based innovations that actually help our customers. The breadth and depth of our data set means unmatched visibility into today’s most advanced threats.
Pre-delivery large language model (LLM)-based threat detection
In an industry first, we’re deploying the Bidirectional Encoder Representations from Transformers LLM family, better known as BERT, to detect threats before they’re delivered to your users. This approach is designed to dramatically lower your risk. Other AI-based tools identify threats only after they’re in users’ inboxes—in many cases after the user has already clicked or responded.
Pre-delivery detection is critical. Our research has found that users click nearly 1 in 7 malicious URLs in less than 1 minute and respond to nearly 1 in 3 BEC messages in less than 5 minutes. Whether deployed as an MX- or API-based solution, our approach avoids the risk of a user interacting with a threat before it’s identified and resolved.
Clearer, plain-language explanations of why we blocked an email in the TAP dashboard
Our customers have told us that they need to understand and explain to their managers and executives what’s getting blocked—and just as important, why it’s getting blocked. And they want this information pre-packaged and ready to communicate to others.
A new tab in the Evidence section of the TAP dashboard’s threat details page offers easy-to-grasp explanations of BEC emails that were blocked, an overview of all threat campaign activity and the top factors that led to the email being blocked.
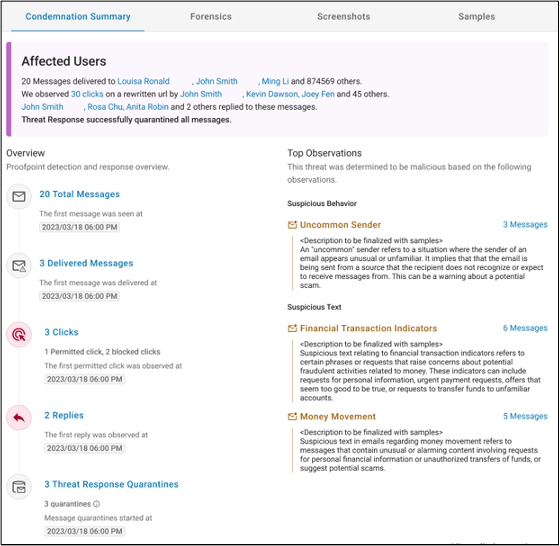
TAP dashboard's threat details page features a condemnation summary showing why we blocked specific emails.
This new information gives you more visibility into why a threat, or threats in a campaign, were found to be malicious. It also gives you an unmatched overview of the threat detection and response timeline.
Surfacing identity-based risks of targeted users
Another feature we’re adding to the TAP dashboard is the attack-path risk column. By bringing data together across the attack chain, we can help your security team understand how many “paths” a compromised identity could be used by attackers to escalate privilege and move laterally within your environment.
This information can be invaluable for assessing user risk. The more paths available, the higher the risk of threats such as ransomware or data theft succeeding.
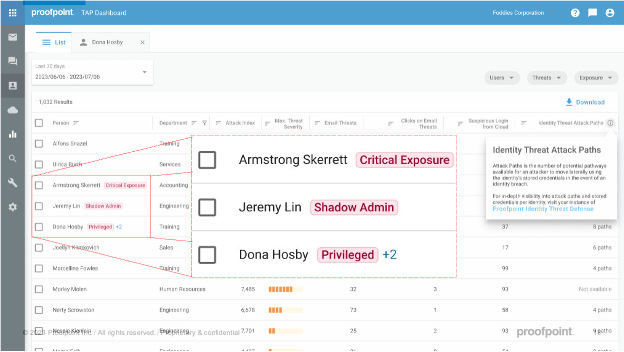
The TAP dashboard highlighting identity-based attack-path risks of selected users.
Stopping data loss through misdirected email
Not all insider-led data loss is intentional. Sometimes it can stem from something as simple as an email accidentally sent to the wrong email address. The autocomplete feature of most email clients or a colleague with a common name can result in a few wayward keystrokes turning into a data loss incident.
Using machine learning, Proofpoint Misdirected Email analyzes the content of outgoing email and past email activity to warn users or block the send when the recipient appears to be the wrong person.
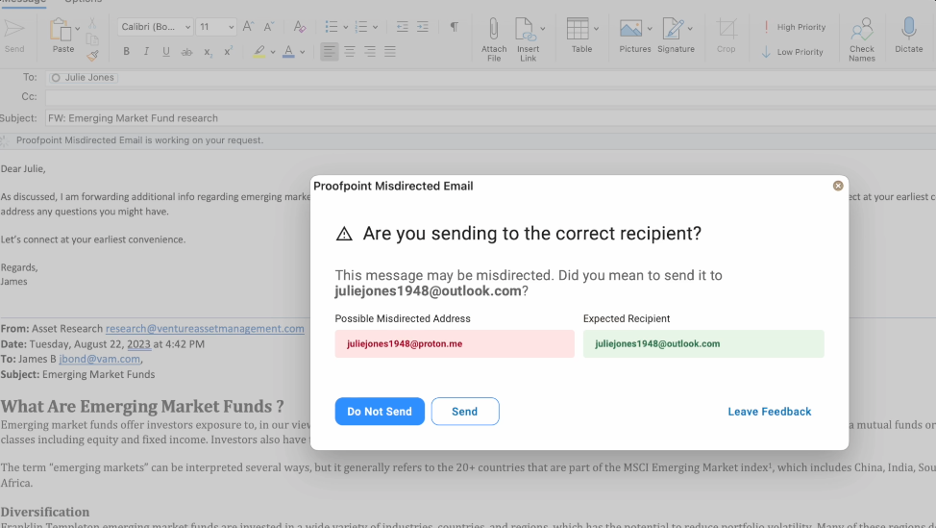
Proofpoint Misdirected Email analyzes an email’s contents and past activity to warn users sending email to someone unexpected.
AI-based assistant for natural-language insights and recommendations
One of the most powerful features of generative AI is the ability to process natural-language questions and synthesize answers based on massive volumes of data. We’re applying that technology to the data in your own Proofpoint deployment.
Proofpoint Security Assistant lets analysts ask natural language questions and get actionable insights and recommendations based on the trillions of combined data points across our platforms.
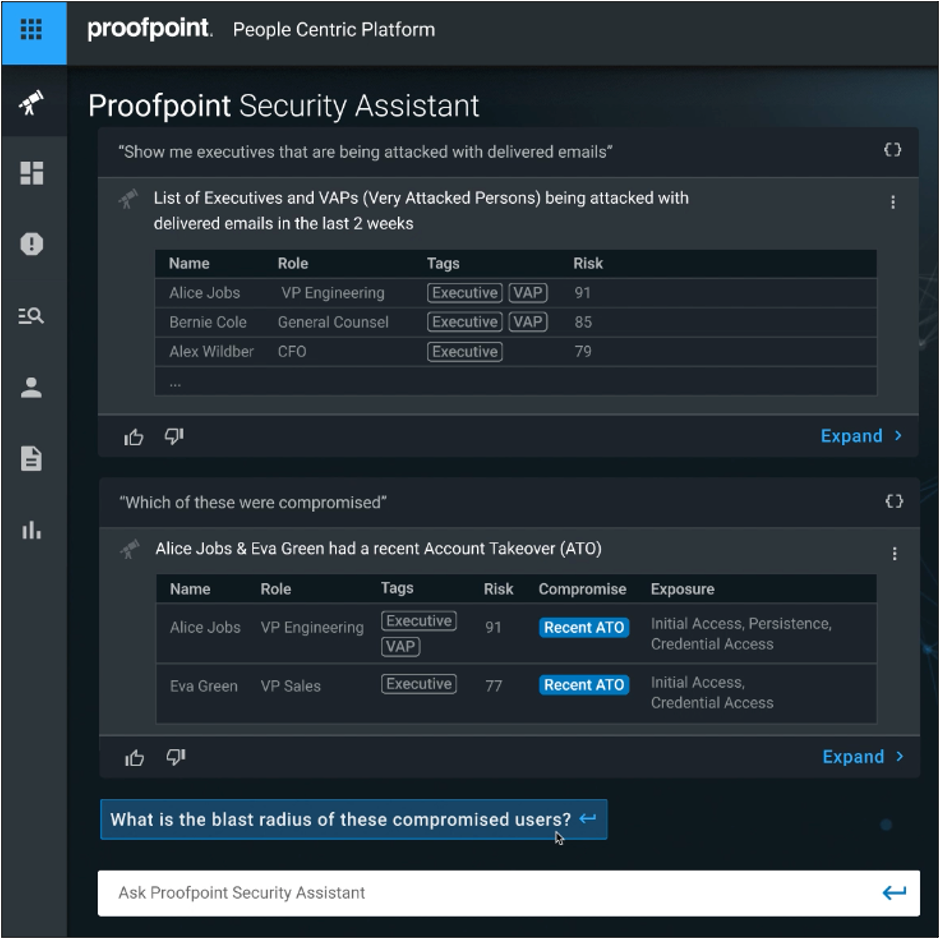
The Proofpoint Security Assistant provides actionable insights based on natural-language queries.
For example, a security analyst can ask Security Assistant “show me John Doe’s exfiltration attempts and recommend which DLP controls we should add” and get clear next steps. “Show me executives that are being attacked with delivered emails” brings up a list of targeted leaders. And a follow-up question “Which of these were compromised” shows which of these users’ accounts were compromised.
Security Assistant will begin rolling out for our Proofpoint Sigma information protection platform in Q4 as a technology preview. Over time, we’ll expand it to the Proofpoint Aegis threat protection and Identity Threat Defense platforms.
How AI and ML are reshaping cybersecurity
Proofpoint Executive Vice President for Cybersecurity Strategy Ryan Kalember took us through a Taylor Swift-themed history of how Proofpoint has used AI and ML—and where these technologies are headed.
But AI is a double-edged sword. Threat actors are also looking at how the technology can augment and scale their efforts. Ryan led a panel discussion on whether attackers are using AI in attacks, how they might exploit weaknesses in large language models (LLMs) what defenders can do to stay ahead.

Customer insights
One of my favorite parts of Protect is hearing from customers. Whether they’re sharing best practices, recounting their experiences from the front lines of cybersecurity, or giving us real-world examples of the challenges they face, customers are the centerpiece of every Protect event we put on.
This year, security leaders from PennyMac, Teradyne and FiServ joined us for a panel on “Breaking the Attack Chain.” Our panelists discussed the importance of disrupting threat actors at every stage of the attack chain, not just at the initial compromise.
Brent Kennedy, PennyMac’s senior vice president and head of information security, compared the traditional protect-the-perimeter approach to M&M candy—hard on the outside but soft on the inside, where attackers can run unchallenged. Instead, Kennedy prefers a “Jawbreaker” approach—hard for attacks right down to the core.
“Before, you had one M&M,” he said during the panel discussion. “Today you have multiple bags of M&Ms because of your environment. It’s very hybrid, from on-premises, the cloud, SaaS and so on. If someone’s in your environment, you want to know what they’re looking at.”
Kennedy uses the Proofpoint Identity Threat Defense platform to cut off threat actors’ attack paths and “build that jawbreaker.”

Panel discussion: “Breaking the Attack Chain — Putting It Into Practice with Proofpoint.”
In our CISO panel, security leaders from the City of New York Department of Education, Jefferies and Medtronic discussed data protection in the context of the attack chain. Protecting data without impeding business operations or getting in users’ way is a constant struggle. And like most security challenges, data loss prevention boils down to people.
“DLP is not a security-only problem,” said Jeffries Global Chief Information Security Officer Jerry Kowalski. “It has to be around the data owners. Just going in with a fancy tool isn’t going to get you anywhere except hundreds of (support) tickets and upset users. It has to be user-centric.”
The threat landscape
I led a roundtable discussion with our threat researchers on the evolving threat landscape and an explosion of creativity among threat actors over the last year. We covered the gamut of advanced threats, including:
- EvilProxy campaigns, a growing threat that bypasses multifactor authentication (MFA)
- Supplier account takeover and follow-up attacks that stem from compromised accounts
- The convergence of phishing and text messaging
- Telephone-oriented attack delivery (TOAD), a type of phishing that moves the conversation from email to a phone call
- The evolution of ransomware, including an ecosystem that has led to threat actor specialization
- How threat actors exploit every stage of the attack chain
Our threat researchers will dive even deeper into these topics at our ThreatCon session on Thursday.
Putting it all together
Protect 2023 is more than just a conference. It's a celebration of our collective achievements as a cybersecurity community, a glimpse of our vision for a more secure future and a tangible reminder of our commitment to delivering the best solutions for protecting people and defending data.
I can’t wait for to see what’s in store for day two.











