At the heart of most cyber-attacks is an attempt to persuade someone to do something that isn’t in their best interests. That might be logging into a phishing site, changing the payment details on an invoice, or opening a file containing malware—the details change, but the basic goal is the same. That’s why we talk about having a people-centric approach to security. People are the target, and people, aided by the right training and safeguards, are also the best line of defense.
What sometimes gets forgotten in this set up is that cyber attackers are people too. And like any other group, some of them can get pretty weird. In this post we’re going to round up some of the stranger lures and social engineering tactics we saw last year.
Here’s our top five social engineering tactics for 2021:
5. Soccer Scouting
It’s the world’s most popular sport, where both players and their agents can make millions if they catch the eye of the right club.
Last year, our researchers saw multiple social engineering campaigns using soccer lures to deliver malware to clubs in France, Italy and the UK. The threat actor in these cases posed as a sports agent representing young players from Africa and South America, seeking their big break into one of the sport’s richest leagues.
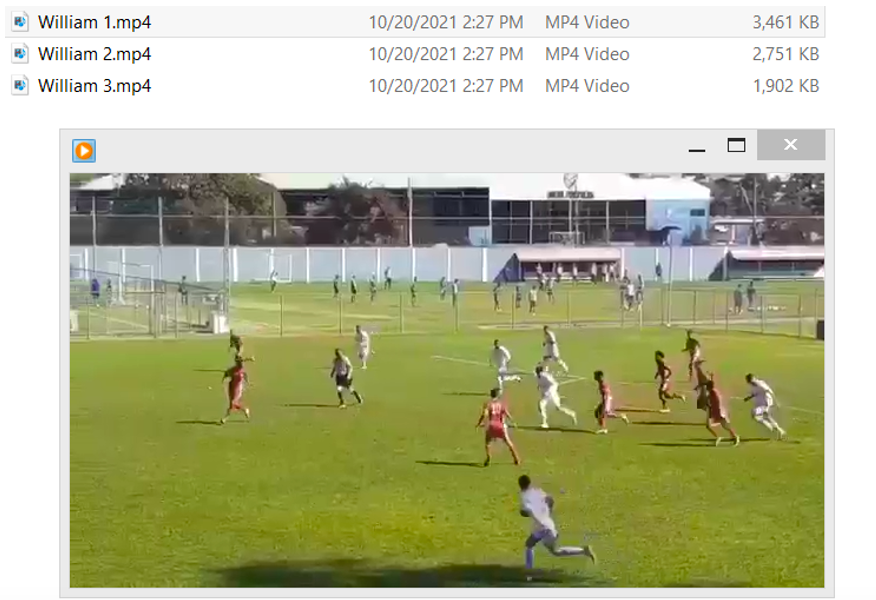
Fig. 1 A benign video containing genuine footage of a young soccer player named William.
The emails sent to targeted clubs included seemingly legitimate video files and YouTube links showing training and match highlights. The practice of video scouting is quite common, especially for prospects based outside Europe, and some of the YouTube links sent in the campaign were publicly accessible. However, any victim intrigued enough by the footage to download and enable the attached Microsoft Excel document found themselves infected with Formbook malware.
As this example demonstrates, cyber attackers will go to great lengths to familiarize themselves with the conventions of even the most niche or specialized businesses.
4. Spoofing Scholars
A lot of cyber attackers rely on high volume, low-specificity email lures, casting a wide net in the hope of finding one unwitting victim who will give them access to a valuable corporate network. But this isn’t everyone’s M.O.
Last summer, we reported on some activity involving TA453, an Iran-aligned actor, targeting European academics and policy experts. What set this campaign apart is the nature and duration of the engagement between attacker and victim.
In early 2021, TA453 began posing as a senior research fellow at University of London’s SOAS institute, using a lookalike email address spoofing a real scholar. SOAS specializes in the study of Asia, Africa and the Near and Middle East, giving TA453 an ideal pretext for contacting various experts in Middle East society and politics.

Fig. 2 A fake conference invitation used as part of TA453’s campaign.
The goal of the social engineering campaign was to steal credentials via a fake webinar sign up page, but before setting this endgame in motion, the attacker invested significant time in building relationships. And it wasn’t just limited to email communication, with TA453 attempting to engage via phone calls and videoconferencing in the course of building rapport with victims.
3. Fake but Functional
Last year saw some high-profile social engineering campaigns involving finely crafted but non-functioning lures, the most famous of which was perhaps BravoMovies – a fake streaming site used to delivery BazaLoader malware.
However, some attackers went beyond the merely superficial. In an August 2021 malware delivery campaign, attackers sent a Microsoft Excel file containing an apparently functional freight calculator.
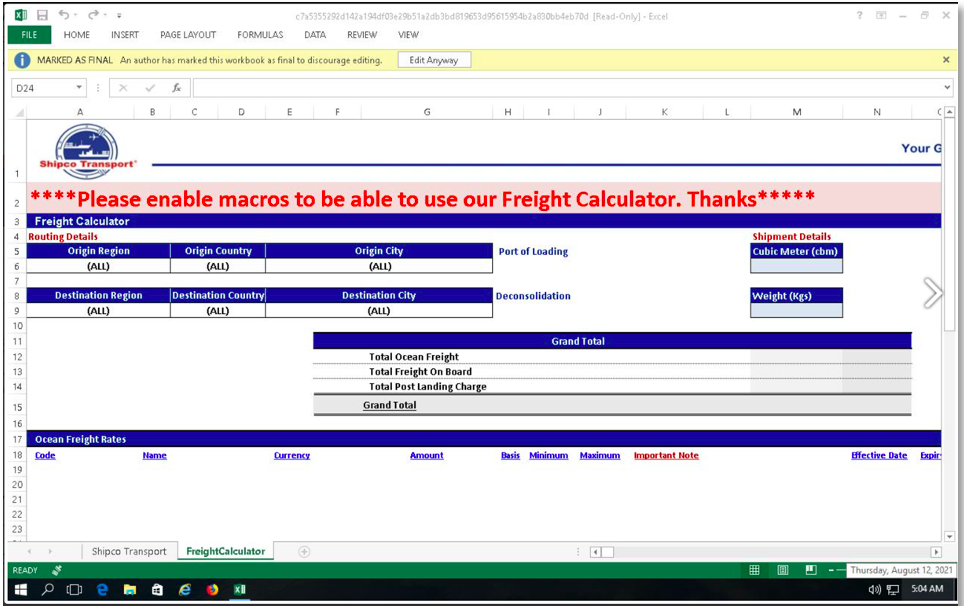
Fig. 3 A functional freight calculator spreadsheet delivering Dridex malware.
Unfortunately, if the victim was persuaded by the lure’s convincing design, they found that their shipping quote came with a bonus delivery of Dridex malware.
2. Good News, Bad News
A/B testing will be a familiar concept to most marketers, but it seems that some cyber attackers might also be experimenting with this social engineering technique. A campaign launched just before Christmas 2021 saw some recipients receive a message informing them that their employment had been terminated, while others got news of promotion and a holiday bonus.
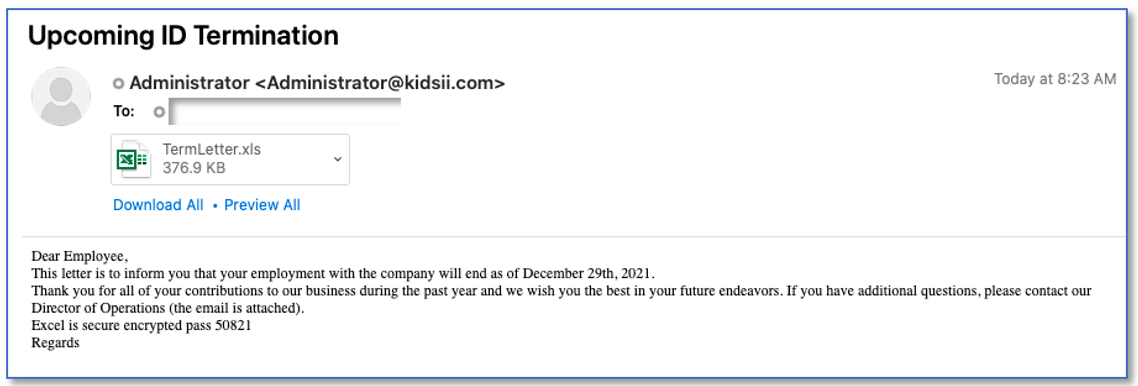
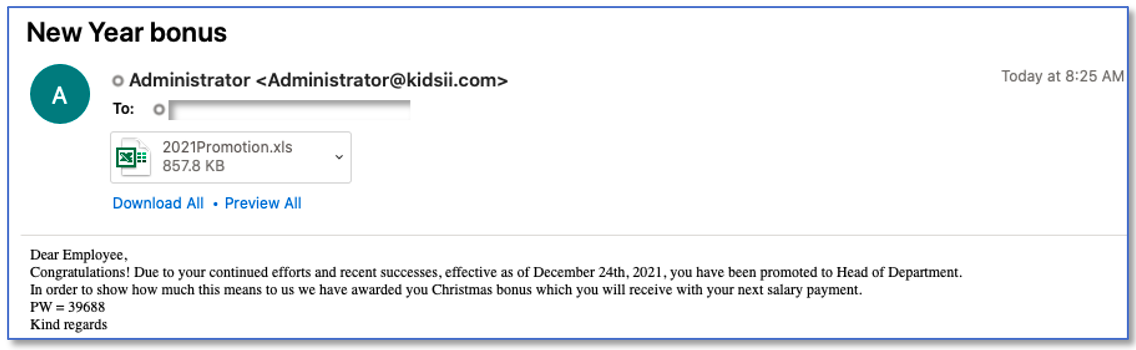
Fig. 4 Termination and bonus-themed lures from the same Dridex delivery campaign.
However, despite the apparent difference in fortune, both messages were really delivering bad news. Downloading the attached Excel file and clicking ”Enable Content” resulted in a Dridex banking Trojan being dropped on the victim’s computer.
And as a cheerful kicker, victims were rewarded with a “Merry Xmas” pop-up once the malware download began…
1. Inheritance or Lottery Win—Why Not Both?
You have received an unexpected inheritance of $2.5 million! Wait, actually, it’s a lottery win of the same amount. But the Royal Bank of Canada is hell-bent on confiscating your windfall, or at least they were until Prime Minister Justin Trudeau intervened on your behalf.
Now, none other than the Chief Justice of Canada is emailing you to let you know that all of this can be resolved for the modest sum of just $100. Oh, and once you pay, your winnings will be made available to you in the form of an ATM Visa Card.
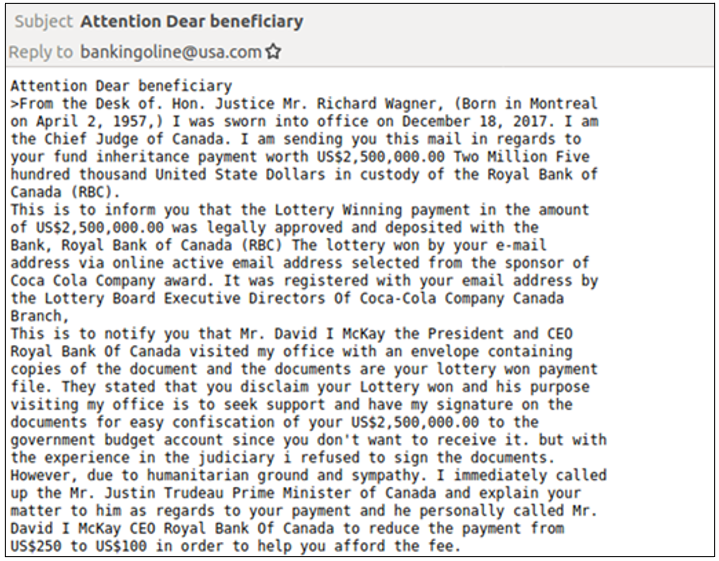
Fig. 5 An elaborate advance fee fraud email lure.
This is the elaborate spell one email fraudster attempted to weave last year, in the process claiming the prize for the strangest lure we’ve seen for quite a while. Advance fee fraud is renowned for occasionally outlandish social engineering tactic, but for its sheer range and variety, this one takes the cake. Or the biscuit. Or the cookie.
To learn more, check out the Proofpoint Threat Hub, your home for the latest research and insights.











