Welcome to the second part of our blog series on using attack path management (APM) to secure your network. In our first post, we examined the importance of using APM to identify and remediate identity-centric attack paths before attackers exploit them. We also emphasized that the compromise of tier-zero assets —aka the “IT crown jewels”—is a top objective for attackers.
Attack path management (APM) is a process by which you discover all the existing paths that an attacker can exploit to reach tier-zero assets within your environment. APM plays a pivotal role in helping security teams pinpoint vulnerable identities. It provides a holistic view of the available attack paths that an attacker could use to move laterally in the quest to reach your IT crown jewels.
In this blog, we introduce a crucial APM concept known as the identity blast radius. We explore the use cases for this view. And we highlight how it is similar but distinct from the attack path view.
What you can learn from identity blast radius analysis
An identity blast radius represents the potential impact of an attacker who is moving laterally using a compromised identity. It presents how the compromise of one particular identity can help an attacker reach other identities or assets in the network. Discovering the identity blast radius before attackers do is essential to prevent a minor compromise from turning into a major security incident.
To see how this works, it’s helpful to visualize it. Below is an illustration of the vulnerabilities related to a user named Brian Rivera. It’s just one example of how attackers can abuse Active Directory ACLs.
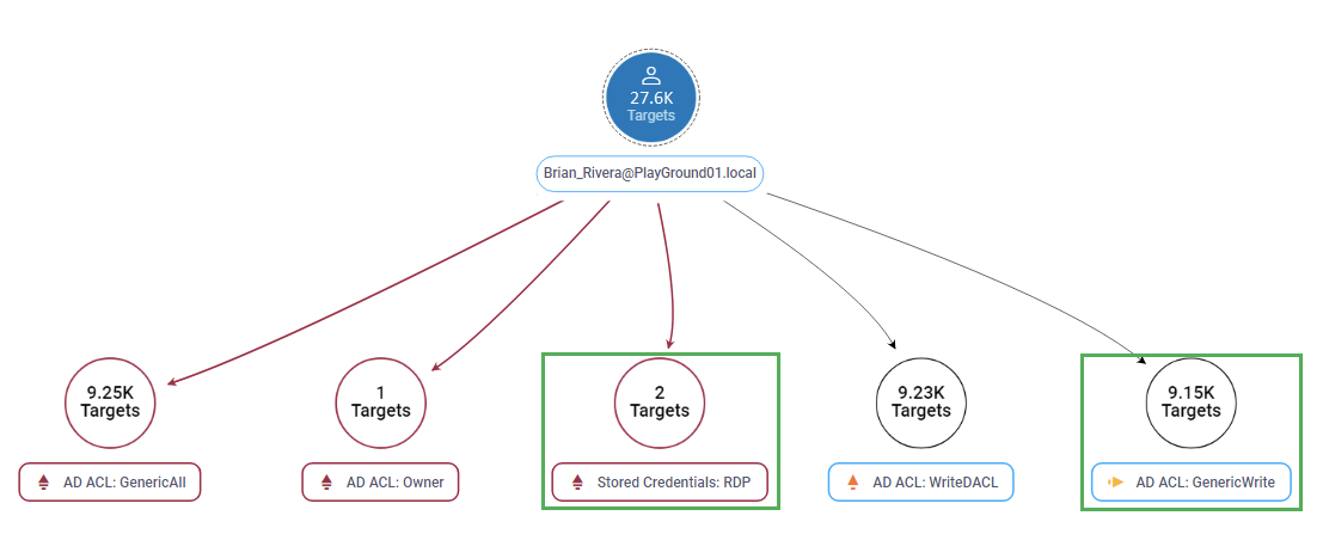
Example view of an identity blast radius.
In the blast radius view above the subject identity for Brian Riviera serves as the “tree root” of the view. Branching off the tree root are all the assets and privileges that that specific user can invoke. These include:
- Stored credentials. If an attacker compromises hosts where Brian’s Remote Desktop Protocol (RDP) credentials are stored, they can use those credentials to move laterally to the indicated hosts.
- Active Directory ACL assignments. An attacker that compromises Brian’s identity can use his GenericWrite permission in Active Directory to:
- Gain code execution with elevated privileges on a remote computer
- Delete files and data
- Introduce malicious files or code on the flagged targets
Identity blast radius use cases
The identity blast radius view supports powerful use cases that support attack path analysis, including:
- Post-compromise analysis. After an attacker gets control of an identity, the blast radius view can help you identify other identities and assets that are vulnerable to lateral movement or other malicious actions.
- What-if analysis. Your security teams can use the identity blast radius view to assess the potential impact of an attack on high-value targets like your chief financial officer or a senior IT administrator. With that insight, they can apply other compensating controls.
- Changes in access privileges. It can also help you identify the potential impact of changes in access privileges. These often occur when employees move between roles. You can use this insight to ensure that an employee’s access is properly managed. This can prevent an excessive accumulation of privileges.
Assets vs. identities: Differences between tier-zero asset views and identity blast radius views
The figure below shows how the tier-zero asset view illustrates paths that ascend from different entities to the tier-zero asset root.
In contrast, the identity blast radius view positions the subject identity as the tree root. Paths extend downward to various entities that are reachable through diverse relations like Active Directory ACL assignments or stored credentials.
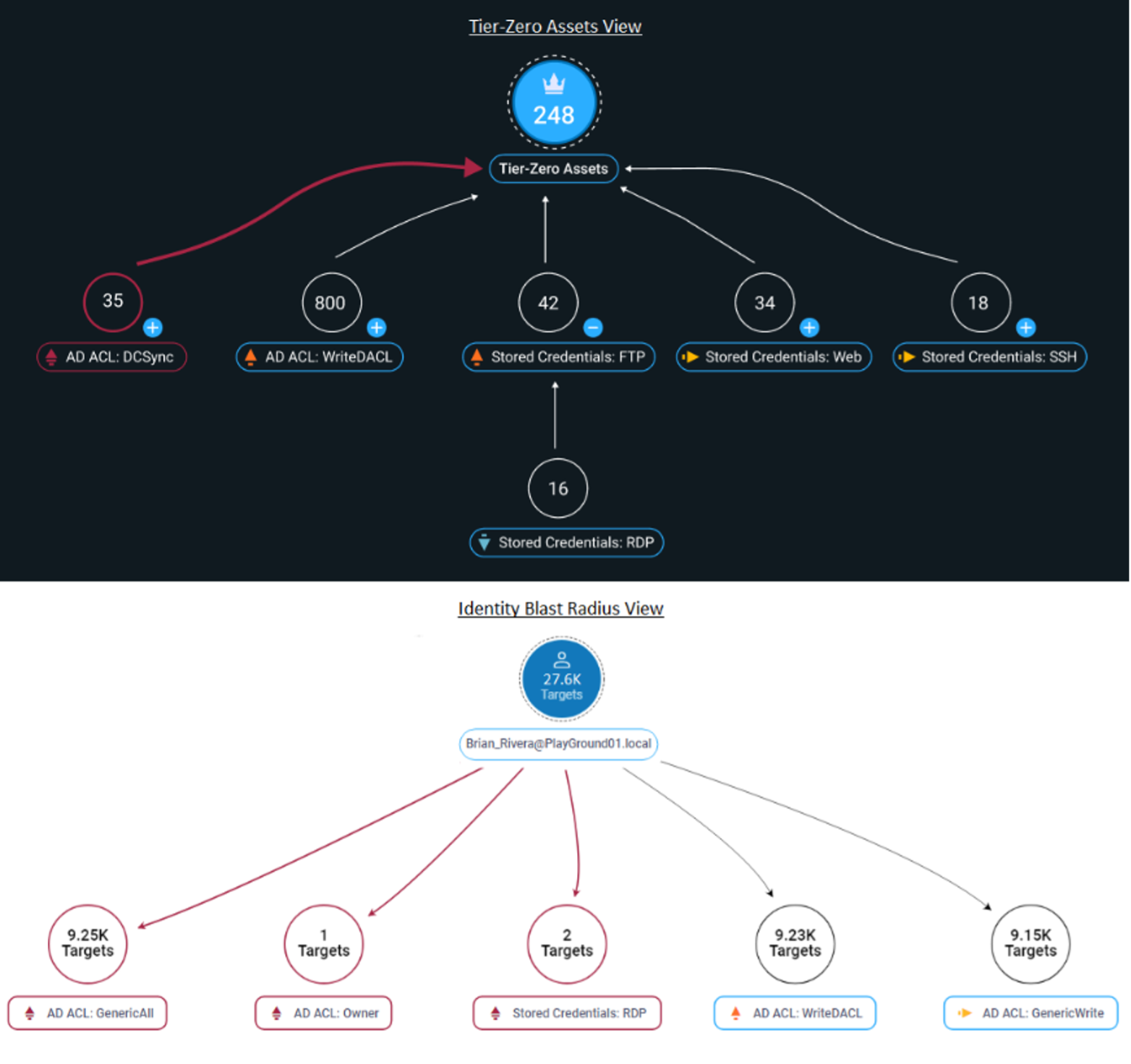
Comparison of the tier-zero assets view versus the identity blast radius view.
These two views offer different perspectives. But both are powerful tools to help you visualize identity-related vulnerabilities. These insights will enable you to move fast to fix vulnerabilities before attackers can find and exploit them.
For example, let’s consider the tier-zero assets view. If you removed FTP-, Web-, SSH-, and RDP-stored credentials on endpoints, multiple existing exploitable paths to the tier-zero assets would go away. Similarly, look at the identity blast radius view of Brian Rivera. If you did a deep audit of his AD Access Control Lists (ACLs) permissions to make sure they aligned with the company’s security policies, you could significantly reduce risks. Just imagine what would happen if Brian Rivera’s account was popped before these ACL remediations have been implemented!
Stay tuned to learn more
The identity blast radius view can provide a strategic tool in your efforts to stop cyberthreats before they occur. When you combine those insights with the asset-oriented tier-zero asset view, you can create a robust defense against identity-centric threats.
Stay tuned for the next blog in our series where we will continue to explore how to apply attack path management as a vital part of your security strategy. Meanwhile, you can sign up for a free demo to explore how Proofpoint Identity Threat Defense identity blast radius capabilities can help you stop attackers from escalating privileges and moving laterally.











