If you want to understand how cybercriminals cause business-impacting security breaches, the attack chain is a great place to start. The eight steps of this chain generalize how a breach progresses from start to finish. The most impactful breaches typically follow this pattern:
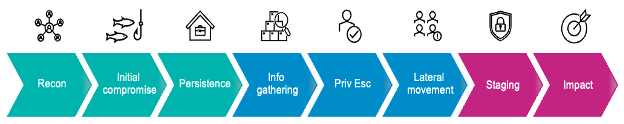
Steps in the attack chain.
In this blog post, we will simplify the eight steps of an attack into three stages—the beginning, middle and end. Our focus here will primarily be on the middle stage—info gathering, privilege escalation and lateral movement, which is often the most challenging part of the attack chain to see and understand.
The middle steps are often unfamiliar territory, except for the most highly specialized security practitioners. This lack of familiarity has contributed to significant underinvestment in security controls required to address attacks at this stage.
But before we delve into our discussion of the middle, let’s address the easiest stages to understand—the beginning and the end.
The beginning of the attack chain
A cyberattack has to start somewhere. At this stage, a cybercriminal gains an initial foothold into a target’s IT environment. How do they do this? Mainly through phishing. A variety of tactics are used here including:
- Stealing a valid user’s login credentials
- Luring a user into installing malicious software, such as Remote Access Trojans (RATs)
- Calling the company’s help desk to socially engineer the help desk into granting the attacker control over a user’s account
Much ink has been spilled about these initial compromise techniques. This is why, in part, the level of awareness and understanding by security and non-security people of this first stage is so high. It is fair to say that most people—IT, security and everyday users—have personally experienced attempts at initial compromise. Who hasn’t received a phishing email?
A great deal of investment goes into security tools and user training to stop the initial compromise. Think of all the security technologies that exist for that purpose. The list is very long.
The end of the attack chain
Similarly, the level of awareness and understanding is also very high around what happens at the end of the attack chain. As a result, many security controls and best practices have also been focused here.
Everyone—IT, security and even everyday users—understands the negative impacts of data exfiltration or business systems getting encrypted by ransomware attackers. Stories of stolen data and ransomed systems are in the news almost daily.
Now, what about the middle?
The middle is where an attacker attempts to move from the initially compromised account(s) or system(s) to more critical business systems where the data that’s worth exfiltrating or ransoming is stored.
To most people, other than red teamers, pen testers and cybercriminals, the middle of the attack chain is abstract and unfamiliar. After all, regular users don’t attempt to escalate their privileges and move laterally on their enterprise network!
These three stages make up the middle of the attack chain:
- Information gathering. This includes network scanning and enumeration.
- Privilege escalation. During this step, attackers go after identities that have successively higher IT system privileges. Or they escalate the privilege of the account that they currently control.
- Lateral movement. Here, they hop from one host to another on the way to the “crown jewel” IT systems.

Steps in the middle of the attack chain.
Relatively few IT or security folks have experience with or a deep understanding of the middle of the attack chain. There are several good reasons for this:
- Most security professionals are neither red teamers, pen testers, nor cybercriminals.
- The middle stages are “quiet,” unlike initial compromise-focused phishing attacks or successful ransomware attacks, which are very “loud” by comparison.
- Unlike the front and back end of the attack chain, there has been little coverage about how these steps actually occur. To learn the details of how attackers traverse the middle requires diving deeply into threat research.
Finally, can you think of any security defensive products that specifically address this part of the attack chain? There are few. What has your business deployed to address the middle of the attack chain? If you answered an identity threat detection and response solution, you are way ahead of the curve.
3 Stages of the middle of the attack chain
The remainder of this blog is focused on the three stages of the middle of the attack chain. While there are many tools that attackers can use to help execute and automate traversing each of these stages, we’ll keep things simple and focus on one popular tool per stage.
Information gathering with Nmap
The goal of this step is to gather specific and deeper information about the target network that is visible from the threat actor’s initially compromised endpoint.
Remember, the attacker is trying to get from the initially compromised machine or account (which generally has little immediate value to them) to a critical system that stores the data or hosts the business processes that can generate a big payday.
The point is, once landed, threat actors need to look around the environment to see what’s what and where they want to go next. Nmap or Network Mapper helps them to do just that. It is an open-source penetration testing tool that runs on Windows, Linux or Mac and is used for network exploration and enumeration. It can discover other endpoints and services that are running in the network.
Nmap scans and identifies open ports on systems, which helps an attacker understand the services that are running around them on the network. The tool also discovers other hosts or endpoints that are running on the network from the perspective of the threat actor’s machine.
Nmap can also automatically determine the version of services running on the network, the operating system on the other systems, and what systems are available for scriptable interactions. If you want to learn more about Nmap, check out this YouTube tutorial. Keep in mind that Nmap is not considered malware, so its use on a network is not necessarily a sign of attacker activity. This is another reason why traditional security systems have a hard time detecting and stopping attacks in the middle of the attack chain.
Privilege escalation with Mimikatz
Mimikatz is a well-known and widely used tool that automates the retrieval of credentials from endpoints running Windows. As such, it is a highly effective tool to perform privilege escalation on a compromised system.
Mimikatz enables privilege escalation by helping to support:
- Credential dumping. Mimikatz will automatically extract plaintext passwords, hashes and Kerberos tickets from memory, even if the Windows Local Security Authority protects those systems.
- Executing pass-the-hash attacks. Attackers can use stolen hashed passwords to authenticate and gain elevated privileges without needing the underlying plaintext password from the hash.
- Performing a gold ticket attack. Adversaries can use Mimikatz to create forged Kerberos tickets (golden tickets) that grant access to a Windows domain and go around normal authentication processes.
Once an attacker has escalated their privilege, they can gain greater control and access within the targeted company. Then, they can plant malware, launch internal phishing campaigns, exploit existing software vulnerabilities, perform reconnaissance for future attacks, and further escalate their privilege to seek even higher levels of access or administrative rights. And, of course, they can move laterally in the network to reach an even more interesting business-sensitive host.
And just like Nmap, Mimikatz is not inherently malware. It is a legitimate tool developed by Benjamin Delpy for educational and security research. But of course, it can, and often is, used by attackers to carry out malicious activities. Thus, many companies ban it and try to detect its use within their network.
Lateral movement with RDP
Attackers can use many tools to move laterally. For example, there are inherently malicious tools like RATs, which allow them to access compromised systems remotely. Tools like Cobalt Strike, Empire and QuasarRAT are a few popular RATs.
The upside—from an attacker’s point of view—is that these tools are highly effective at helping them reach the end of the attack chain. The downside for attackers is that these tools are obviously malicious, have no positive use within an enterprise, and are relatively easy to spot and block by security systems.
How can cybercriminals avoid being detected and blocked and still get the job done? The answer is to “live off the land.”
The Remote Desktop Protocol (RDP) is a Microsoft protocol that is installed on essentially all Windows machines that a threat actor would be interested in. As a legitimate tool developed by Microsoft, RDP is intended for IT administrators to conduct remote administration of their company’s Windows clients and servers. However, cybercriminals can abuse RDP to move laterally after they have gained initial access to an RDP-enabled host.
With RDP, attackers can jump from one compromised system to another if those systems can connect to each other via the network. For a cybercriminal who wants to move around quietly and dwell for an extended period without being caught, the key advantage of RDP is that whether the IT team or attackers are using the protocol, the network activity all looks the same.
In short, RDP has the advantage of being both ubiquitous in Windows networks and appearing to be legitimate from a security monitoring perspective. That’s a bad combination for defenders.
Building your defense
By tying together and repetitively using Nmap, Mimikatz and RDP tools (or equivalent alternatives) threat actors can move from an initial compromise to the attack endgame without being deep experts at each step. With that in mind, here are two questions for you to consider:
- What can our company do to address this challenge?
- What security controls do we have in place that can reasonably detect and stop an attacker who is attempting to traverse the middle of the attack chain?
Some piecemeal security systems can apply aspects of a defense against privilege escalation and lateral movement. But until recently, no tool has been designed specifically for this purpose. Fortunately, identity threat detection and response (ITDR) systems, as coined by Gartner, have emerged. Their mission is to defend the middle of the attack chain.
If you would like to learn more about our perspective on the pressing need for ITDR solutions, check out the new Proofpoint e-book, Identity Threat Detection and Response: Challenges and Solutions. You can also explore the capabilities of Proofpoint Identity Threat Defense by downloading our solution brief. Or, you can check out our new Buyer’s Guide to Identity Threat Detection and Response.











