This blog post is adapted from our e-book, Getting Started with DLP and ITM.
The last few years have brought unprecedented change. An increasingly distributed workforce, access to more data through more channels and a shift to the cloud have transformed the nature of work. These trends have made protecting sensitive data more complicated and demanding.
What’s clear is that organizations are struggling to rise to the challenge. Between 2020 and 2022, insider threats increased by a staggering 44%. And the costs of addressing them increased 34%—from $11.45 million to $15.38 million.
This upswing mainly comes down to two factors. For starters, most security teams have little visibility into people-caused data loss and insider-led security incidents. And few have the tools or resources to handle it.
That’s why Gartner sees platforms for data loss prevention and insider threat management (DLP and ITM) increasingly converging. Businesses need tools and processes that give them holistic, contextualized insights that take user behavior into account. It’s no longer enough to focus on data—and where it’s moving.
To prevent data loss, industry leaders need to take a people-centric approach that expands beyond traditional drivers like compliance. In this blog post, we’ll explore some basics for designing an ITM and DLP program. This can help you approach information protection in a way that’s built for how modern organizations work.
Why information protection is so challenging
Risks are everywhere in today’s complex landscape. Here are a few changes making it difficult for companies to protect their data.
- More data is open to exposure and theft. As businesses go digital, more data is being generated than ever before. According to IDC’s Worldwide Global DataSphere Forecast, the total amount of data generated data will double from 2022 to 2026. That means malicious insiders will have more access to more sensitive data through more channels. It will also be easier for careless users to expose data inadvertently. Plus, any security gap between channels, any misconfiguration or any accidental sharing of files can give external attackers more opportunities to steal data.
- New data types are hard to detect. Data isn’t just growing in volume. It’s also becoming more diverse, which makes it harder to detect and control. With traditional DLP program tools, data typically fits within very tightly defined data patterns (such as payment card number). But even then, it generates too many false positives. Now, key business data is more diverse and can be graphical, tabular or even source code.
- The network security perimeter no longer exists. With more employees and contractors working remotely, the security perimeter has shifted from brick and mortar to one based on people. Add to the mix bring-your-own-device (BYOD) practices, where the personal and professional tend to get blurred, and security teams have even more risks to contend with. In a survey for the 2023 State of the Phish report from Proofpoint, 72% of respondents said they use one or more of their personal devices for work.
- Employee churn is high. Tech industry layoffs in 2022 and 2023 have seen many employees leaving and joining businesses at a rapid rate. The result is greater risk of data exfiltration, infiltration and sabotage. Security leaders know it, too—39% of chief information security officers rated improving information protection as the top priority over the next two years.
- Security talent is in short supply. A lack of talent has left many security teams under-resourced. And the situation is likely to get worse. In 2023, the cybersecurity workforce gap hit an all-time high—there are 4 million more jobs than there are skilled workers.
DLP vs. ITM
What’s the difference between DLP and ITM? Both DLP and ITM work to prevent data loss. But they achieve it in different ways.
DLP tracks data movement and exfiltration
DLP monitors file activity and scans content to see whether users are handling sensitive data in line with corporate policy. DLP is used across an enterprise with low-risk, everyday users in mind.
ITM focuses on user behavior
ITM, meanwhile, analyzes application use, user interface actions, website access and file movement. Its purpose is to detect risky user behavior and prevent data loss, system sabotage and other compliance violations. It also captures screenshots of high-risk activity for visual evidence in case of an investigation.
ITM applies to risky users, such as:
- Departing employees
- Privileged users
- Very Attacked People™ (VAPs)
- Contractors
- Employees on a performance plan
Why ITM and DLP programs are converging
DLP and ITM are joining forces because the nature of work is evolving. To protect data today, you can’t focus on content alone. You need visibility into what insiders are doing with data. And you need a clear strategy to prevent and mitigate threats.
A modern ITM and DLP program is:
- Content aware, so that it can accurately identify sensitive and regulated data
- Behavior aware, so it can determine which user behaviors are risky, which are likely indicators of malicious intent, and which types of access are unusual
- Threat aware, so it can identify compromised accounts or tell when users have fallen victim to a phishing attack, OAuth abuse or malware
Connecting these dots can provide additional context, streamline investigations and reveal intent—something that’s not always clear when you use traditional DLP tools.
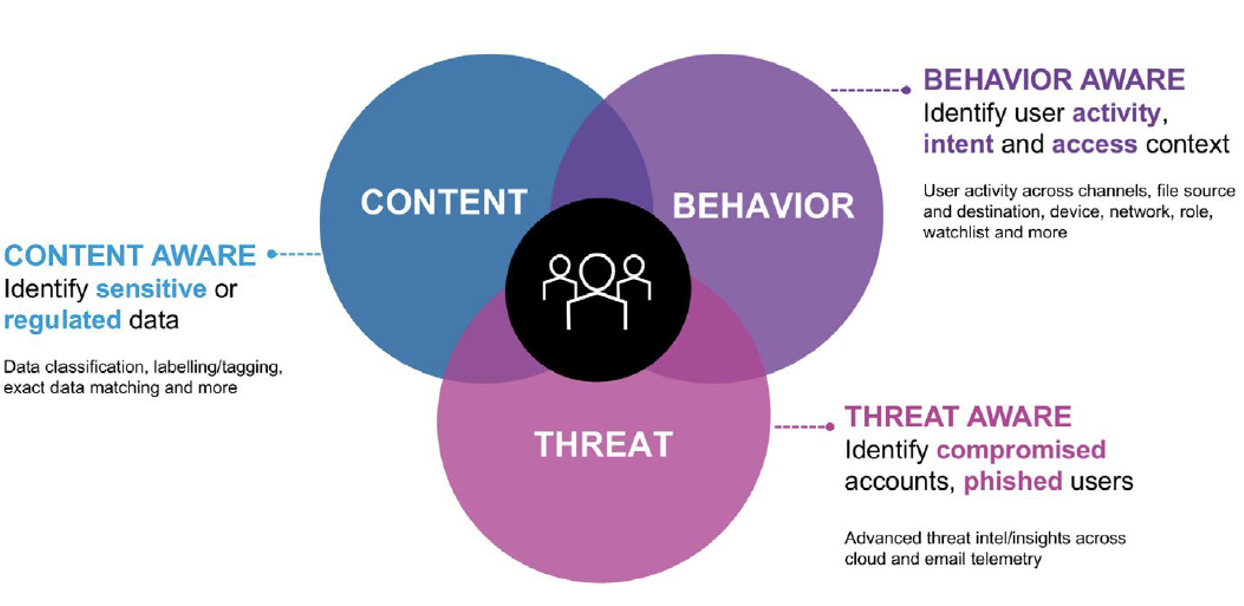
The three pillars of modern data loss prevention.
6 Steps to create a successful ITM and DLP program
Here’s a basic overview of the steps you need to take to design an ITM and DLP program that’s built for how modern organizations work.
Step 1: Get the right people in place
A successful ITM and DLP program is inherently cross-functional. It eliminates traditional silos between “security” (personnel-focused) and “InfoSec” (network-focused IT). And it gets people involved from across the business, including legal, human resources, compliance, line-of-business leaders, executives and even the board of directors.
Every group should be working together toward the common goal of decreasing organizational risk. Both technical and nontechnical people should be empowered to communicate clearly about ITM and DLP issues.
Step 2: Define your data assets, risks and program requirements
Most businesses have limited and narrowly defined use cases for assessing threats. Typically, they’re ad hoc and reactionary. If you want to expand your use cases, a starting point is to outline what makes your organization most vulnerable.
- Define data assets. What data needs protection? If you don’t know what sensitive data you have, you can’t secure it.
- Identify risky insiders. C-suite executives are often the go-to targets for attackers. But in many cases, it’s a better strategy for bad actors to focus on others. They might go after IT admins who have extensive system privileges, for example. Or they might target employees in public relations or investor relations who have access to valuable or sensitive data.
- Outline compliance requirements. Certain laws and compliance rules are best met through a holistic information protection program. From a legal and privacy standpoint, it’s much better to implement a well-designed program than to avoid one due to fears about potential legal hurdles.
Step 3: Take stock of your capabilities and gaps
Before you can plan your program, you need to understand your current state. This starts with making a critical assessment of your current capabilities, investments and data loss prevention maturity level. That process will help you to answer key questions like:
- What are our technical capabilities and limitations?
- What are our specific pain points or coverage gaps?
- How can we make the best use of our existing investments when we roll out a more comprehensive program?
- What other capabilities do we need to protect our hybrid workforce?
Step 4: Plan your program
Information protection is a complex undertaking. So, keep in mind that it may be months before your ITM and DLP program is fully operational.
At a minimum, your plan should cover governance, background checks, training, user activity monitoring, data management and investigation.
Start with a plan that includes legally supported documented policies and procedures. Most organizations have the resources to manage these essential activities.
Step 5: Roll out and establish a review cycle
To get up and running, create an implementation plan that includes program milestones. This is when you will define key steps, like how to staff your program, your office’s exact responsibilities, when you’ll get expert help from third parties and more.
To ensure your program continues to get funding, you’ll need to conduct clear-eyed self-assessments from time to time. Regular reviews can help improve your program as well. Typically, you’ll conduct reviews at predetermined events, like before the start of a new project milestone.
Step 6: Scale up over time
As noted earlier, it takes time for most ITM and DLP programs to reach full operating capacity. To be effective at managing risk, you’ll want to meet these milestones as your program matures:
- Conduct background checks for everyone
- Level up your training
- Promote internal collaboration
- Define oversight roles
- Fine-tune your data access controls
- Deploy better monitoring across your environment
- Automate prevention and remediation
How Proofpoint can help
Ready to build your own information protection program? Most organizations don’t have insider threat expertise. So, you may want to enlist the help of an expert like Proofpoint managed services. We can provide objective insights to help you design, implement and manage an effective ITM and DLP program.
We also provide the leading people-centric information protection platform. Proofpoint Sigma can help connect the dots between user activity and data movement so that your security team can respond to insider-led breaches in near real time. It protects your company against data loss, malicious acts and brand damage caused by users while saving you both time and costs.
For more details on building and managing your DLP program, download our e-book Getting Started with DLP and ITM. You’ll learn:
- What it takes to set up an ITM and DLP program
- Best practices for getting started and scaling
- Tips for how to measure success











