In the past month, Proofpoint researchers have observed a slight increase in email-based ransomware attacks using ransomware as a first-stage payload. This is notable because for the past year or more attackers have used downloaders as the first-stage payload, which then deliver ransomware as the second- or later-stage payload. A small increase in the amount of ransomware sent as a first-stage payload via email campaigns may herald the return of the large ransomware campaigns we saw in 2018.
These attacks have featured many different families of ransomware and have targeted numerous industries in the United States, France, Germany, Greece, and Italy. They often use native language lures and messages. Ransomware families we’ve seen as first-stage payloads include among others:
- Avaddon (a new family)
- Buran (named for the Russian Space Shuttle)
- Darkgate
- Philadelphia (something previously seen by Proofpoint in 2017)
- Mr. Robot
- Ranion
Each of these ransomware families encrypts the victim's files and holds them ransom for a payment.
Daily volumes ranged from one to as many as 350,000 messages in each campaign, and over one million messages between June 4 – 10, 2020 featured Avaddon ransomware. We’ve seen a variety of themes in these ransomware messages, including some that exploit COVID-19, and numerous industries were targeted. These verticals include education and manufacturing followed by transportation, entertainment, technology, healthcare, and telecommunications.
Below are Avaddon, Mr. Robot, and Philadelphia examples:
Avaddon
Avaddon, a newer ransomware that has targeted U.S. organizations, is notable because it has its own branding and is often part of large-scale campaigns. Over one million messages with Avaddon as the payload were sent June 4-10, 2020, and over 750,000 messages were sent on June 6, 2020 alone. These campaigns were primarily sent to manufacturing, education, media, and entertainment organizations. The June 4, 2020 Avaddon ransomware campaign focused almost exclusively on transportation companies and school districts.
Avaddon is an example of “ransomware-as-a-service” (RaaS), where threat actors pay others for the use of the ransomware rather than building the ransomware and infrastructure themselves.
Recent Avaddon ransomware messages featured subject lines like
- “Do you know him?”
- “Our old picture”
- “Photo for you”
- “Do you like my photo?”
- “Is this you?”
- “Your new photo?”
- “I like this photo”
When opened, the included attachment downloads Avaddon using PowerShell. Once Avaddon runs, it shows the ransom message in Figure 1 and later demands $800 payment in bitcoin via TOR. The Avaddon attackers also provide 24/7 support and resources on purchasing bitcoin, testing files for decryption, and other challenges that may hinder victims from paying the ransom.
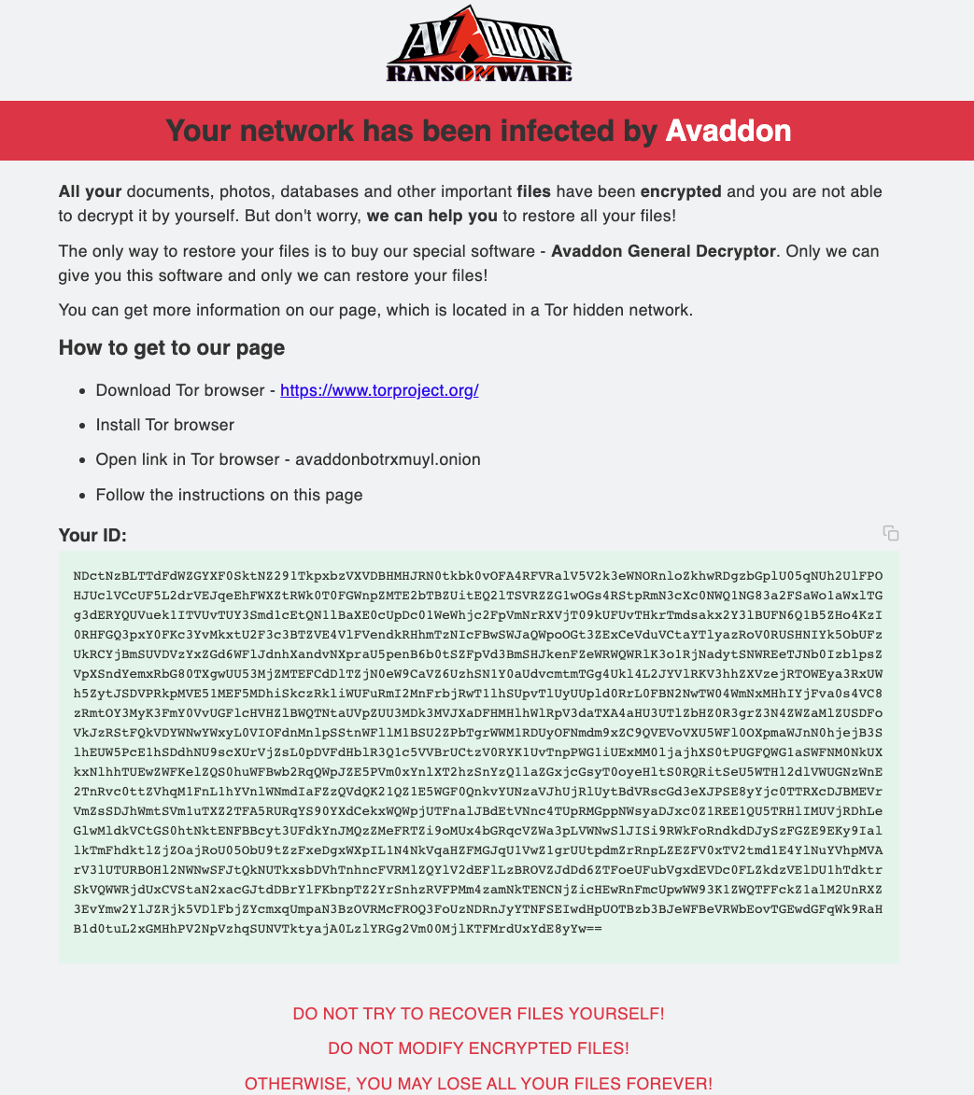
Figure 1 Avaddon Infection Message
Mr. Robot
This Mr. Robot ransomware attack used a COVID-19 lure to persuade targeted users to click. Between May 19-June 1, 2020, a series of Mr. Robot campaigns targeted U.S. entertainment, manufacturing, and construction organizations.
Recipients of these campaigns are sent messages claiming to be from “Departament (sic) of health”, “Departament (sic) of health & human services”, “Health Service”, and “Health Care” with subject lines like:
- Your COVID19 results are ready / 85108
- Your COVID19 results are ready # 85513
- Your COVID_19 results # 99846
- View your COVID19 result # 99803
- human immunodeficiency virus analysis # 93545
- COVID19 virus test result / 61043
- COVID19 virus result / 64745
- COVID19 virus analysis # 83273
- Check your COVID_19 test # 65619
- Your COVID_19 Results No 80420
The recipient is encouraged to click a link in the message as shown in Figure 2. If clicked, Mr. Robot ransomware installs, and a $100 payment demand appears.
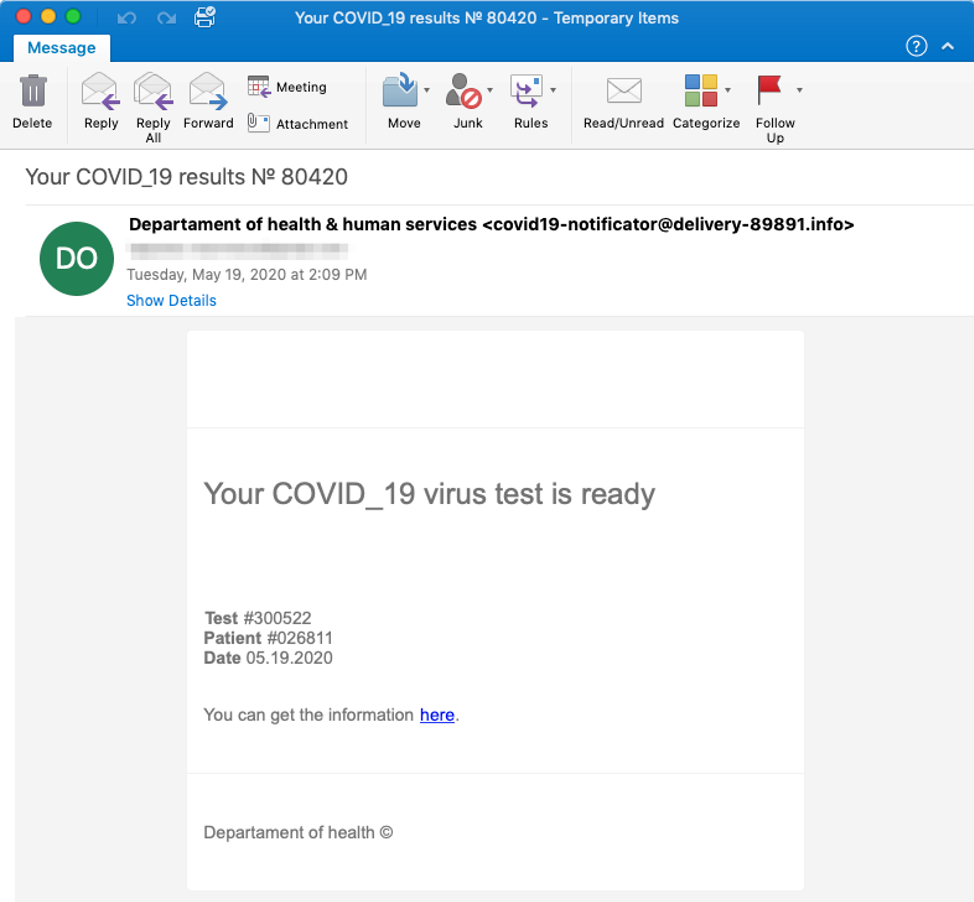
Figure 2 Mr. Robot COVID-19 Lure
Philadelphia
After a nearly three-year hiatus, Philadelphia ransomware has returned with a campaign primarily targeting manufacturing and food and beverage companies in Germany with German-language lures (Figure 3).
These messages claim to come from “Federal Germany Government” and use the flag and insignia of the Federal Republic of Germany, along with a subject that states: “Die Entscheidung, Ihr Unternehmen aufgrund von Covid-19 zu schließen” (translated: “The decision to close your company due to Covid-19”). The recipient is encouraged to click the link which installs Philadelphia as a first-stage payload and shows a ransom message demanding (in English) payment of 200 Euros as shown in Figure 4.
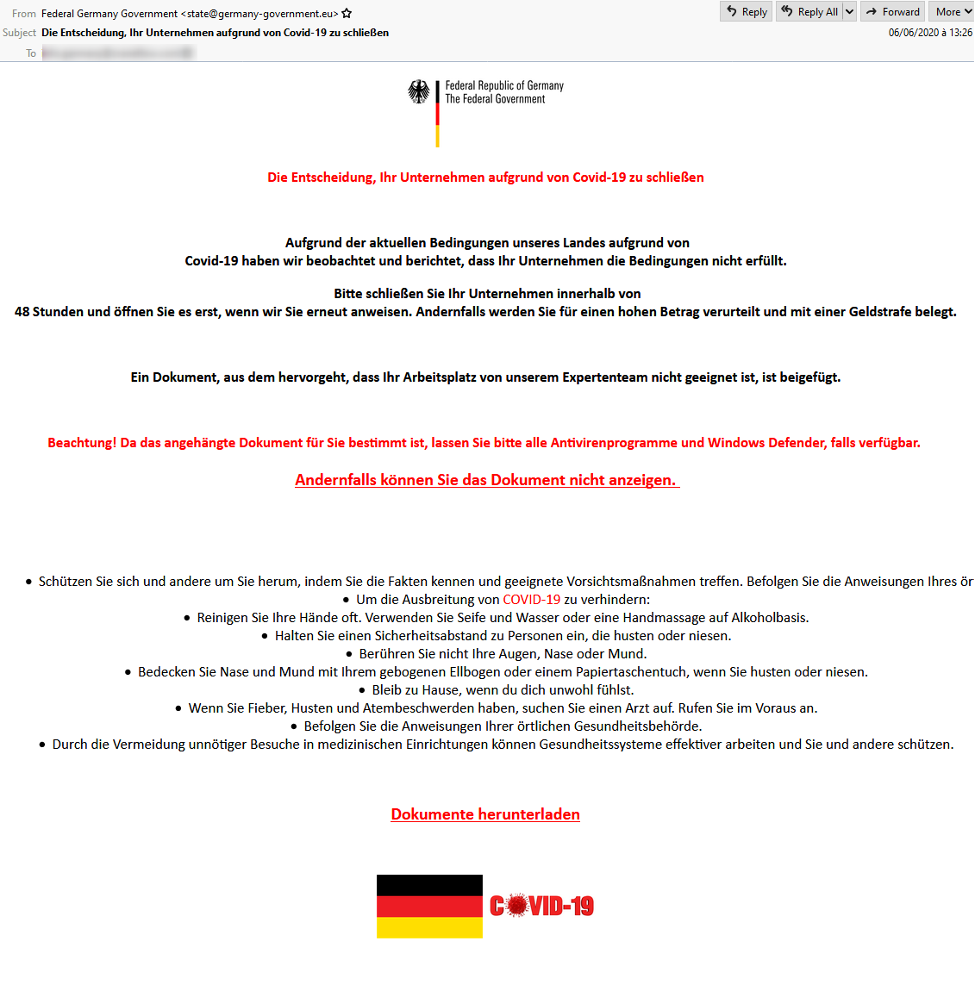
Figure 3 Philadelphia German Lure
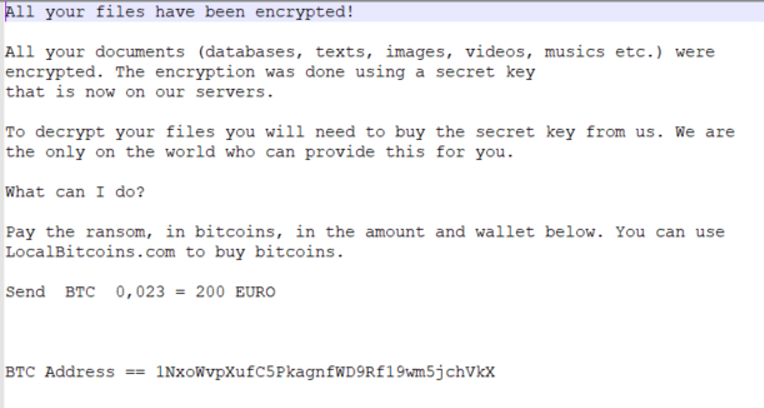
Figure 4 Philadelphia Ransom Note
This recent emergence of ransomware as an initial payload is unexpected after such a long, relatively quiet period. The change in tactics could be an indicator that threat actors are returning to ransomware and using it with new lures. Various actors trying ransomware payloads as the first stage in email has not been seen in significant volumes since 2018. While these volumes are still comparatively small, this change is noteworthy. The full significance of this shift isn’t yet clear, what is clear is that the threat landscape is changing rapidly, and defenders should continue to expect the unexpected.











