Overview
With fall foliage peaking around the northern hemisphere, pumpkin spice lattes warming our cups, and fall in full swing, the end of Oktoberfest is always a good time to look at threats facing German-speaking regions, many of which are unique to these centers of global finance and diplomacy. While Germany, Austria, and Switzerland are all subject to large, indiscriminate global campaigns, many regionally targeted threats are also worth highlighting, both for their local significance and the global trends they help confirm.
Malware Threats
As we have observed globally, German-speaking regions are frequently targeted with downloaders, banking Trojans, and, less frequently, ransomware. However, Germany in particular has experienced attacks with malware less common in other regions. Banking Trojans, by their nature, must be configured with webinjects for regional banks and e-commerce sites, while others rely on German-language emails and lures for distribution in the region.
Proofpoint researchers first documented the Osiris banking Trojan in late July when it appeared in a German campaign. Osiris was a new version of the aging Kronos banker that used the Tor network for communications with its command and control (C&C) infrastructure. Figure 1 shows an example email from this campaign, which used macro-laden Microsoft Word attachments to download and install Osiris.
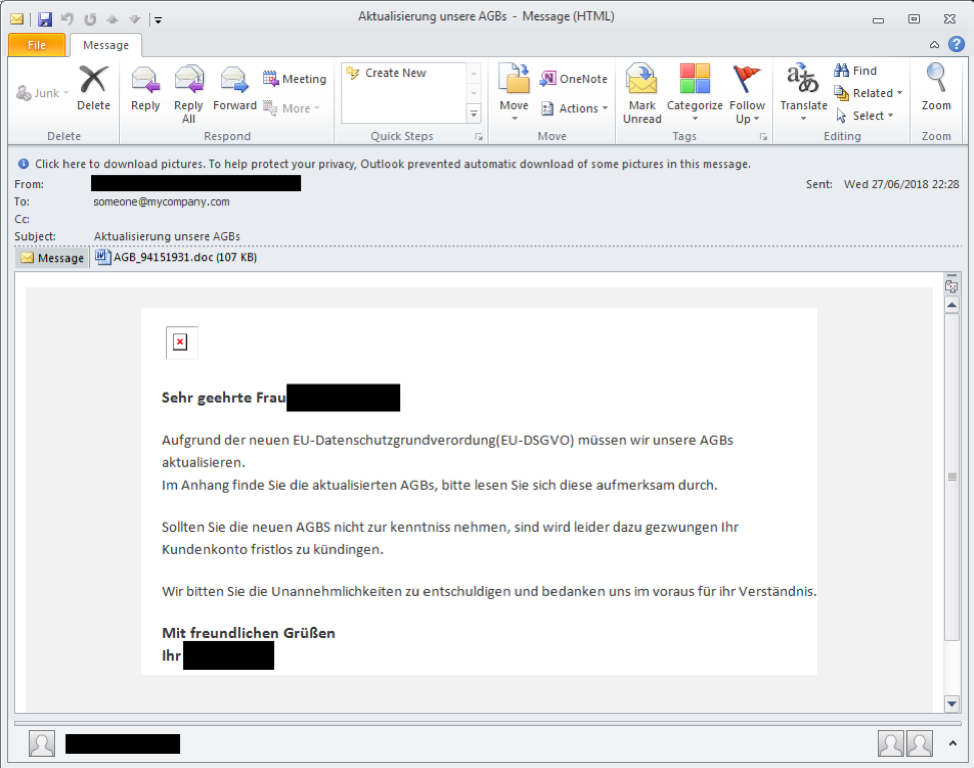
Figure 1: Example email used in the first Osiris campaign
The Retefe banking Trojan, on the other hand, frequently appears in German-language attacks on Swiss targets. Unlike most banking Trojans, Retefe operates by routing traffic involving the targeted banks through its proxy (see Figure 2). Over the past year, Proofpoint researchers have documented weekly, if not daily, Retefe campaigns in Switzerland, as well as campaigns in Scandinavia and Austria.
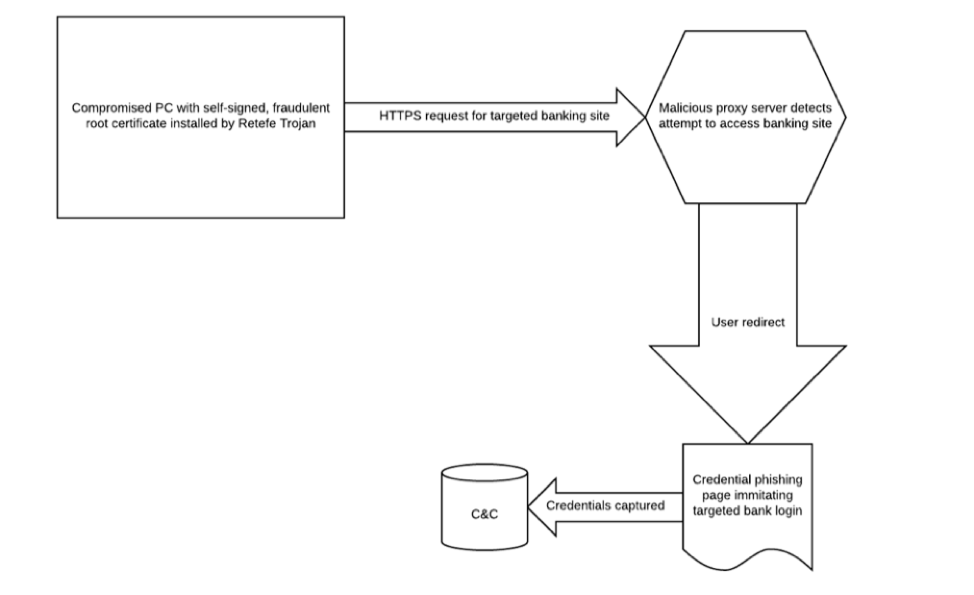
Figure 2: Schematic showing proxy-based attacks used by the Retefe banking Trojan
It is also worth noting that Emotet, another banking Trojan, was originally spotted in Germany, Austria, and Switzerland in 2015, but has since grown into a global threat that still affects German-speaking organizations regularly.
Downloaders appeared in nearly 20% of global malicious email campaigns in the second quarter of 2018, up 7 percentage points from Q1. Germany was no exception to this trend with threat actors distributing the Nymaim downloader almost exclusively in Germany and Poland in recent months. Example subject lines in recent campaigns include:
- Abrechnung Nummer 470136585 vom 12.09.2018 (Billing number 470136585 from 12.09.2018)
- Bank Payment Limited & Co. KG unbeglichene Rechnung Buchung ID 952828587 [User Name] (Bank Payment Limited & Co. KG unpaid invoice booking ID 952828587 [User Name])
- Fwd: [User Name] - OnlinePayment GmbH & Co. KG automatische Konto-Lastschrift konnte nicht vorgenommen werden (OnlinePayment GmbH & Co. KG automatic account direct debit could not be made)
- [User Name]- Bank Payment Limited & Co. KG automatische Konto-Lastschrift ([User Name] - Bank Payment Limited & Co. KG automatic account direct debit)
- [User Name] Ihr angegebenes Girokonto ist nicht hinreichend gedeckt ([User Name] Your specified current account is not sufficiently covered)
In some cases, the emails contained links to zipped Nymaim executables while others used password-protected Microsoft Word documents. Nymaim has been documented downloading the Ursnif banking Trojan and other reconnaissance and downloader malware.
Although distributed at much lower volumes than we observed in 2016 and 2017, ransomware continues to appear in German-language campaigns as well. One such campaign distributing Gandcrab ransomware leveraged the brand of a well-known photographer, and included both a photo and zipped executable attachments (Figure 3). The latter installed Gandcrab when opened.
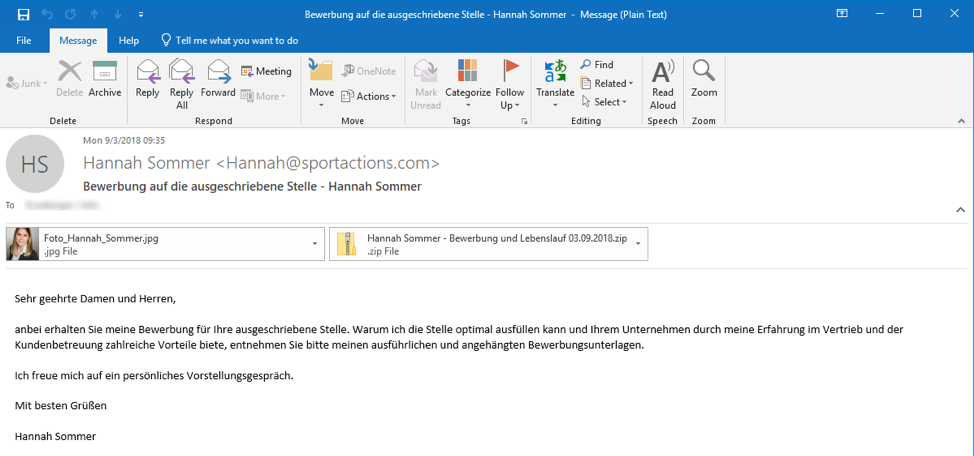
Figure 3: Email purporting to be from a well-known photographer using multiple attachments to distribute Gandcrab ransomware
In another first, we detected the first observed email attack distributing Rapid ransomware earlier this year. The attack targeted German organizations with subjects including:
- "Zahlung bestatigen-1234567890123" ("Confirm payment-1234567890123")
- "Ihre Dokumente-12345678901" ("Your Documents-12345678901")
- "Versicherungsvertrag-123456" ("Insurance contract-123456")
- "Ihre Dokumente: Unfalllinie-1234567" ("Your Documents: Accident Line-1234567")
- "Kommunikation-123456789" ("Communication-123456789")
- "die Information Note-1234567890123" ("the information note-1234567890123")
- "Vorvertragliche Dokumente --12345678" ("Pre-contractual documents --12345678")
- "Vertragskommunikation-123456789012" ("Contract Communication-123456789012")
These messages featured Zip or RAR archive attachments containing Microsoft Word documents. The documents contained macros that, if enabled, downloaded Rapid ransomware.
Proofpoint researchers have also detected AZORult campaigns targeting Germany. AZORult is an advanced information stealer and downloader that has recently been distributed using tax-related lures. Emails with the subject "Ihre steuerliche Identifikationsnummer benötigt eine aktualisierung." (“Your tax identification number needs an update.”) contain a URL linking to the file "Identifikationsnummer aktualisierung hilfe 2018-2019.doc" ("Identification number update aid 2018-2019.doc" (Figure 4). The document in turn uses macros to download AZORult.
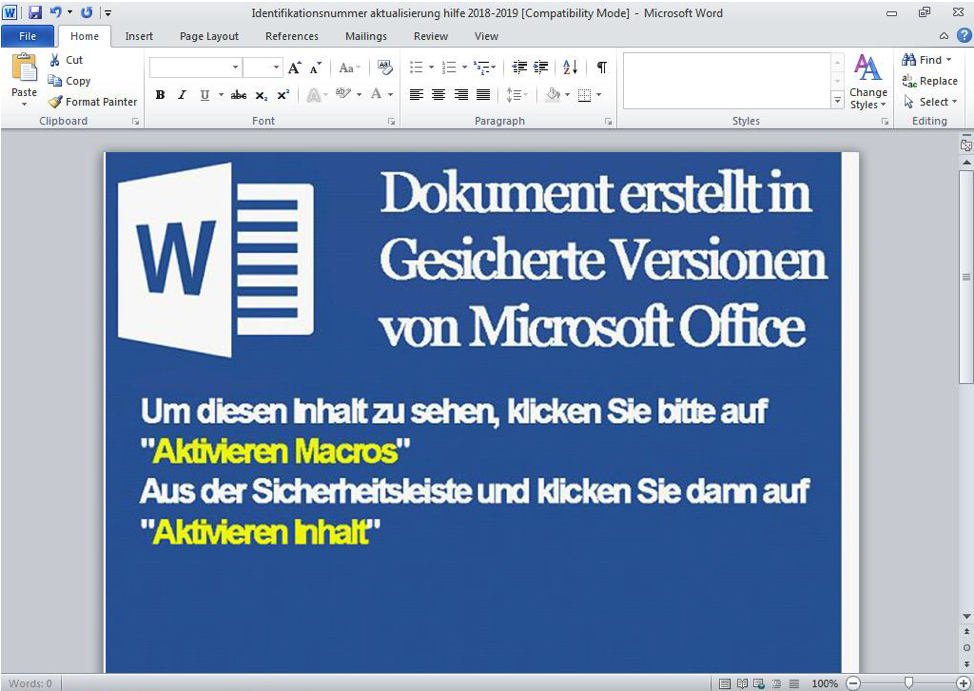
Figure 4: Lure document used to distribute AZORult
Email Fraud
Email fraud, also known as CEO fraud or business email compromise (BEC) has cost German companies millions of Euros; globally, email fraud has resulted in over $12.5 billion in direct losses. Because email fraud attacks rely on social engineering and carefully spoofed communications between attackers posing as trusted business associates and unsuspecting victims, detection remains challenging for traditional tools.
Email fraud attack patterns in Germany parallel global trends. Figure 5 shows the top subject lines categories in English from detected email fraud in Germany over the last year.
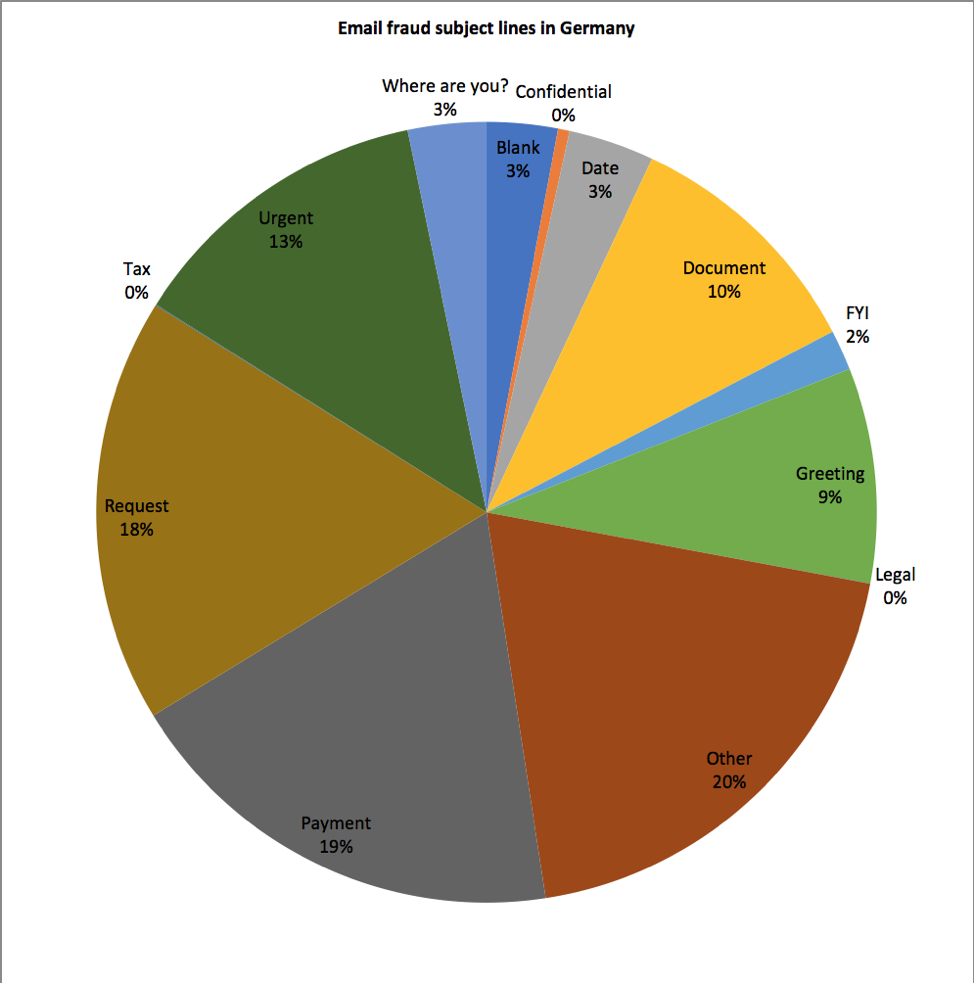
Figure 5: Distribution of subject lines in German-targeted email fraud attacks
Globally, 9.4% of email fraud used so-called “fake chains” -- tactics used to create the appearance of an email history -- in the second quarter of 2018. Over 11% of German email fraud used this technique, but other parameters, such as number of victims targeted per attack were similar to those measured in other regions.
Regardless of the exact presentation, user education and robust next-generation defenses are critical to preventing email fraud.
Phishing
Though far older as an attack technique, phishing remains highly active in German-speaking regions. Proofpoint researchers regularly detect both email attacks and landing pages for credential phishing attempts. These attacks are increasingly sophisticated, using stolen branding and carefully constructed pages, lookalike and typosquatted domains, and social engineering to trick victims into entering a range of credentials.
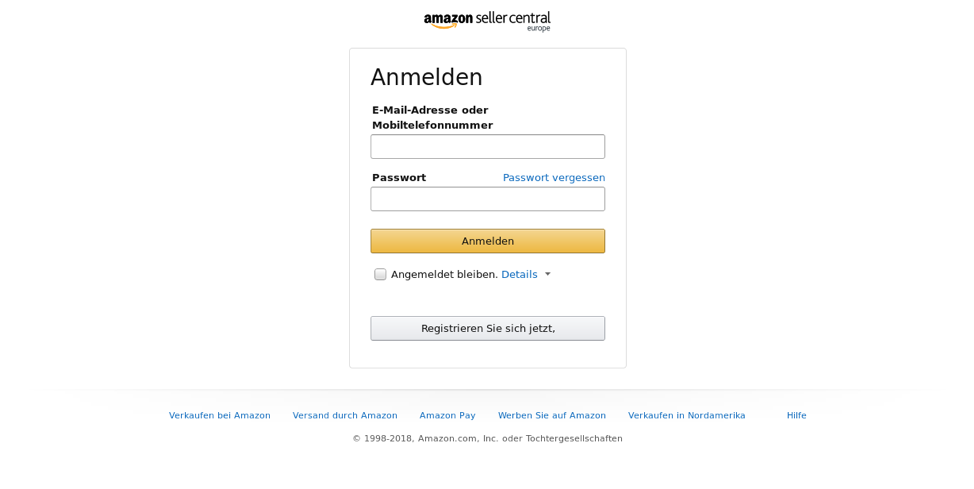
Figure 6: Phishing template for Amazon’s German-language site using stolen branding
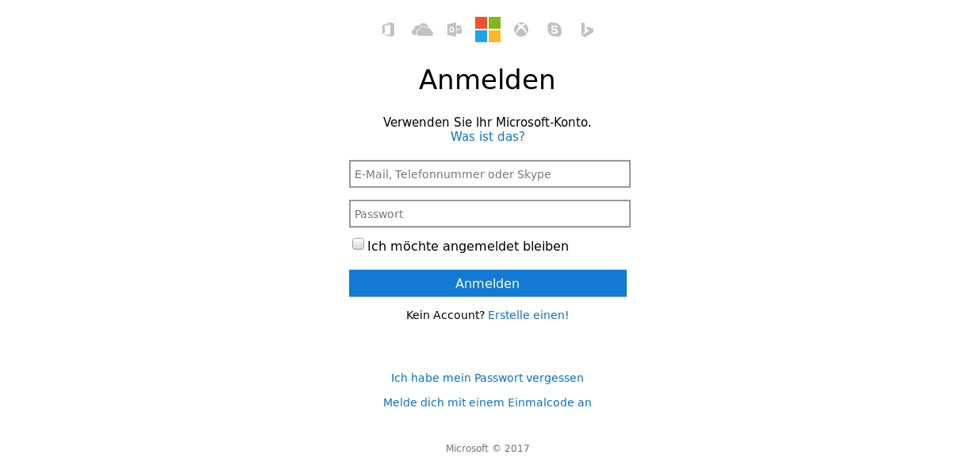
Figure 7: Phishing template for Microsoft services using stolen branding and German language
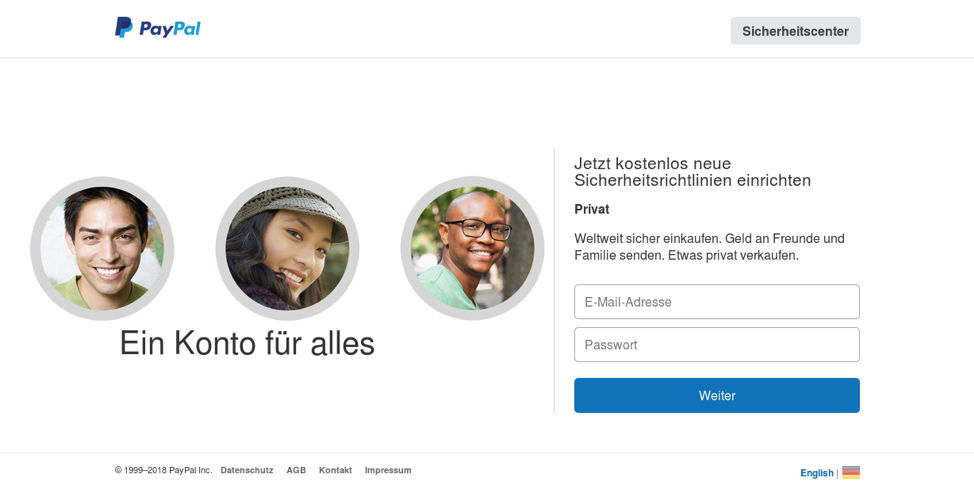
Figure 8: Phishing template for PayPal credentials featuring stolen branding and design in German; note that the only difference between fake page and the legitimate page is the use of an older PayPal logo
Figures 6-8 show samples of these types of attacks, all of which can help attackers obtain credentials, steal directly from organizations and individuals, and establish beachheads within organizations to launch future attacks.
Conclusion
Germany and other German-speaking regions face a variety of online threats. While many mirror those facing regions around the world, some, like the Retefe banking Trojan, are much more frequently observed with German lures and webinjects specific to regional banks. Email fraud mirrors trends elsewhere in the world, but we continue to see growth among BEC actors using German-language lures. Phishing as well continues to become more sophisticated with carefully crafted landing pages and stolen branding designed to trick both enterprise users and consumers. For defenders in these regions -- and worldwide -- a combination of layered defenses, strong threat intelligence, and rigorous end user training are all critical to combatting these threats.











