Table of Contents
Email has been a favorite target for cyber criminals aiming to steal sensitive data, user credentials, and company funds. As one of the most pervasive and effective email scam tactics, Business Email Compromise (BEC) incidents are a common threat, with 70% of organizations experiencing an attempted attack in 2024. These highly targeted, low-volume email attacks impersonate corporate identities to solicit fraudulent wire transfers, steal company data, access customer credentials, and capture other confidential information. While BEC attacks are a frequently reported tactic, they represent the tip of the iceberg when it comes to fraudulent email scams.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we'll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
What Is Email Fraud?
Email is one of the most beneficial ways to communicate with anyone. But it is also a primary tool used by attackers to steal money, account credentials, and sensitive information. Email fraud is an umbrella term that covers any scam or deception carried out via email with the intent to steal information, money, or unauthorized access.
Email fraud (also called email scams) involves intentional deception where cyber criminals use email as their primary weapon to target unsuspecting victims. These attacks can range from simple advance-fee scams targeting individuals to sophisticated BEC schemes designed to trick entire accounting departments into processing fraudulent payments. The common thread across all email fraud is the use of socially deceptive tactics to manipulate recipients into taking actions that benefit the attacker.
Email fraud exploits the trust that people place in electronic communications. Attackers craft convincing messages that appear to come from legitimate sources like banks, colleagues, vendors, or trusted organizations. They use social engineering techniques such as creating urgency, impersonating authority figures, or promising rewards to lower victims’ defenses and prompt immediate action.
If users interact with the email scammer and provide sensitive information, it can cause long-term issues for your organization, including identity theft, financial loss, and data corruption. The financial impact of email fraud continues to grow, with BEC alone resulting in over $2 billion in losses annually. Beyond immediate financial damage, successful email fraud attacks can lead to reputational harm, regulatory penalties, and long-term operational disruption as organizations work to recover from breaches.
Common Types of Email Scams
Email scammers use a variety of tactics to deceive victims, with each method designed to exploit different human vulnerabilities and business processes.
- Phishing: These deceptive emails pretend to be from trusted sources like banks, social media platforms, or popular services to trick recipients into clicking malicious links or entering credentials on fake websites. Phishing attackers cast a wide net with generic messages sent to thousands of potential victims, hoping to catch anyone who might fall for the convincing but fraudulent requests.
- Business email compromise (BEC): Cyber criminals impersonate executives, vendors, or business partners to manipulate employees into transferring funds or sharing sensitive information. These sophisticated attacks often involve CEO fraud, where attackers spoof executive email accounts to request urgent wire transfers, or vendor impersonation, where criminals intercept legitimate invoices and change payment details to redirect funds to fraudulent accounts.
- Spear phishing: Unlike broad phishing campaigns, spear phishing involves highly targeted attacks where criminals research specific individuals or organizations to craft personalized, convincing messages. These attackers use publicly available information about targets’ work relationships, current projects, or personal interests to create emails that appear to come from trusted colleagues or business contacts.
- Tech support scams: Fraudsters impersonate IT providers, help desks, or major technology companies to convince victims their devices are infected with malware or experiencing technical problems. These scams typically involve urgent-sounding emails claiming immediate action is required, followed by requests for remote access to the victim’s computer or payment for unnecessary “repair” services.
- Advance fee scams: These classic schemes promise victims large sums of money, lottery winnings, or valuable prizes in exchange for upfront payments disguised as processing fees, taxes, or administrative costs. Modern versions include inheritance scams, lottery notifications, and investment opportunities that require initial payments before the promised windfall can be released.
- Job offers and recruiting scams: Criminals send attractive employment offers that promise high pay for minimal work, often without requiring interviews or background checks. These scams typically involve requests for personal information during fake application processes, or ask victims to process fraudulent checks while sending portions of the money to specific accounts under the guise of equipment purchases or training fees.
- Invoice and vendor fraud: Scammers create fake invoices from non-existent suppliers or hijack legitimate vendor communications to redirect payments to fraudulent accounts. These attacks often target accounts payable departments with urgent-sounding requests to update banking information or process overdue payments for services that were never actually provided.
- Charity and crisis-based scams: Fraudsters exploit current events, natural disasters, or humanitarian crises to solicit donations for fake charitable causes. These emotionally manipulative emails often use high-pressure tactics and urgent language to encourage immediate donations while impersonating legitimate relief organizations or creating entirely fictitious charities.
How Email Fraud Works
Email fraud follows a predictable pattern that exploits human psychology rather than just technical vulnerabilities. Understanding this typical attack flow helps organizations recognize when they’re being targeted and implement appropriate defenses.
1. Initial Contact
The attacker sends a carefully crafted email designed to appear legitimate and relevant to the recipient. “Unfortunately, it’s very easy to spoof visible email fields,” says Joe Schwartz, VP of Corporate Marketing at Proofpoint. Schwartz warns that criminals leverage this vulnerability to:
- Change the reply-to email address in a way that makes it look like the email is coming from within the organization
- Spoof the display name (which is especially effective on mobile devices that hide the reply-to email address)
- Use a “lookalike domain,” a domain that looks like the company’s but is slightly different (such as using a numeral zero in place of the letter “o”)
- Pretend to be a legitimate business partner or supplier
This initial message establishes credibility by spoofing trusted brands, mimicking familiar communication styles, or referencing current events and personal information gathered from social media or data breaches. The email typically avoids making immediate demands and instead focuses on establishing a plausible reason for contact.
2. Building Trust or Urgency
Once the initial contact is made, attackers work to manipulate the recipient’s emotional state and decision-making process. They create artificial time pressure through urgent language, claim authority through executive impersonation, or build false trust through extended correspondence that mimics legitimate business relationships. This stage often involves multiple touchpoints designed to lower the victim’s guard and make the eventual request seem reasonable.
3. Call to Action
The final stage involves the attacker’s actual objective: getting the victim to take a specific action that compromises security or transfers value. This might involve clicking a malicious link that steals credentials, transferring funds to a fraudulent account, or sharing sensitive information that enables further attacks. The request is typically framed as routine, urgent, or beneficial to the victim.
The Psychology Behind Email Fraud
Email fraud succeeds because it targets fundamental human psychology rather than technical weaknesses. Attackers understand that people make decisions based on emotions first and logic second. They exploit psychological triggers like fear (your account will be closed), urgency (act now or miss out), authority (CEO requesting immediate action), and curiosity (you’ve received an important message). These tactics work because they activate our instinctive responses and bypass rational decision-making processes.
The human element represents both the weakest link and the strongest defense in email security. Attackers specifically target human error because technical security controls have become increasingly sophisticated and difficult to bypass. They know that a single employee clicking a malicious link or processing a fraudulent payment request can circumvent millions of dollars in cybersecurity investments.
Real-World Consequences of Email Fraud
The financial impact of email fraud has reached staggering proportions, with business email compromise alone resulting in $55 billion in total losses according to recent FBI data. According to Andrew Goodman, Senior Manager of Product Marketing at Proofpoint, “Last year (2024), total losses reached $16.6 billion, which is a 33% increase from the previous year. Email continues to be the most exploited attack vector.”
High-profile cases illustrate the devastating potential of sophisticated email fraud campaigns. Google and Facebook fell victim to a $121 million phishing scheme orchestrated by a Lithuanian national who impersonated a legitimate Asian manufacturer over two years. Other notable incidents include Toyota’s $37 million BEC loss in 2019, Ubiquiti’s $46.7 million theft through vendor impersonation, and MacEwan University’s $12 million loss to spear-phishing attacks targeting construction payments. These cases demonstrate that even technology giants and well-resourced organizations remain vulnerable to carefully crafted social engineering attacks.
The scale and frequency of email fraud continue to accelerate, with over 3.4 billion phishing emails sent daily, representing 1.2% of all global email traffic. BEC attacks specifically increased by 33% in the first quarter of 2025 compared to the previous quarter. These statistics underscore that email fraud represents an escalating threat that requires immediate attention and comprehensive defensive strategies across all industries and organization sizes.
Recognizing Email Scams
Email scammers use several strategies to bypass email defenses and trick users into divulging information or running malicious code. Some types of scam emails include a link to an attacker-controlled malicious website where the attacker collects sensitive data from victims. When one method stops working, attackers often revise their approach to improve the number of targeted users affected by their email scams.
Red flags of an email scammer:
- Claims that you must log into a website or your account will be closed. This tactic includes a link to an attacker-controlled website.
- Claims that your payment information is invalid, and you must log into your account and change this information to keep the account active.
- Tells you that personal information is inaccurate, and it must be sent to the attacker either using a reply message or on a website.
- Attaches an invoice for payment.
- Conveys a sense of urgency or confidentiality.
- Claims that you could receive a government refund and asks for sensitive data such as your Social Security number.
- Requires you to submit private data to obtain free products, coupons, or money.
But a growing number of email scams don’t exhibit any of the typical behaviors. They don’t include attachments or URLs. And they hide in plain sight by disguising themselves as everyday business.
These attacks are sometimes called business email compromise (BEC) or email account compromise (EAC). They usually start when the attacker impersonates someone the recipient trusts—perhaps a boss, colleague, or business partner — and asks for something that seems like a standard business request. It might be making a wire transfer or changing payment details, things that take place all the time in the regular course of business. By the time the organization senses something is off, the email scammer already has the money.
Email Scam Examples
Attackers have dozens of common strategies. If you have a free email solution such as Gmail and use your email address on contact forms across the internet, you probably have scam emails in your spam inbox.
Attackers might cast a wide net by sending email scams by the thousands. In this model, the more emails sent, the better the chance of tricking numerous targeted users.
Other attackers might take a more targeted approach, carefully choosing a recipient with the right access to data, systems, or resources. The attacker researches the victim online and tailors the emails to be as personal and convincing as possible. In some cases, the attacker has already compromised a legitimate email account and has access to previous email conversations, calendars, and contacts —ammunition for highly convincing impersonations.
Here’s an example of an email scam:
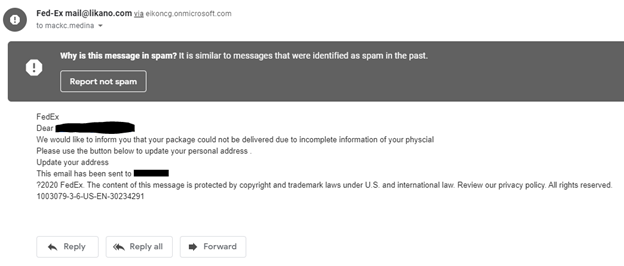
The above image is a message (sent to Gmail’s spam inbox) that an attacker sent, using FedEx to trick a targeted user into sending private data. Attackers use this type of message because someone is always waiting for a FedEx package. If the message is sent to thousands of recipients, it can trick many of them.
Email spoofing is common in scams, but the sender’s email address in the above image is from a public domain unassociated with FedEx. The email gives no contact number but has a single link that points to a malicious web page.
Another giveaway in this email scam example is that the email does not address the recipient by name or have any personal information that an account vendor would have. The email is generic with only the recipient’s email address used in the greeting (the email address is blacked out).
Here are a few common factors in most email scams:
- Use of a trusted common business (such as FedEx, Netflix, PayPal, your bank, and so on).
- Conveys urgency, such as losing an account or product if the targeted user does not respond.
- Includes a generic greeting that does not use a name.
- Includes a convenient button for the targeted user to click and access the malicious site.
- Uses an email address not associated with the official business but deceptively similar to it. For instance, the sender could use the fedexx.com domain to trick users, most of whom don’t bother looking at the return address.
Protecting Against and Avoiding Email Scams
You can’t prevent scammers from using email. But you can take steps towards avoiding email scams to prevent being a victim. For enterprise users, fraud prevention using email filters and authentication (such as DMARC) can block spoofed messages and those from malicious domains. For individuals, always use an email provider that has fraud prevention built into the system.
Email scams target people, not systems. That’s why you need a people-centric approach to stopping them. Here are ways you can protect people from email scams:
- Deploy an email defense that customizes controls based on each user’s unique vulnerability, attack profile, and access privileges. It should detect malicious attachments, unsafe URLs, and social engineering techniques.
- Use email domain authentication technology such as DMARC, along with SPF and DKIM, to prevent email fraud schemes from using your trusted domain, including attacks aimed at your users.
- Prevent email and cloud account compromise with technology that reveals suspicious activity and other signs of takeover. Scan internal emails, which could come from compromised accounts. Use multifactor authentication (MFA) where possible, but keep in mind that it’s not a failsafe solution to account compromise.
- Isolate risky websites and URLs. Web isolation technology can assess suspicious web pages and unverified URLs in a protected container within a user’s normal web browser.
- Conduct regular security awareness training and train users on the latest phishing tactics through simulations and interactive programs, and be on alert for return email addresses that don’t match the sender (including those with domains that are slightly off-brand).
- Implement clear incident reporting procedures so employees know how to quickly report suspected email scams to IT security teams.
- Always keep your security (antivirus and antimalware) software updated for threats that reach the endpoint.
- Update your operating system when patches and new releases are available. Many of these patches remediate vulnerabilities made public by researchers and cybersecurity experts.
- Back up data frequently in case you accidentally fall victim. Your backups can be used for data recovery. Consider using cloud backup storage for the best protection. But remember that many of the costliest email scams don’t use malware at all.
What to Do If You Fall for an Email Scam
Even the most security-conscious employees can fall victim to sophisticated email fraud campaigns. The key to minimizing damage is responding quickly and systematically once you realize you’ve been targeted. Taking immediate action can prevent further compromise and help protect both your personal information and your organization’s assets.
Immediate Actions to Take
When you realize you’ve fallen for an email scam, every minute counts. These immediate steps can help contain the damage and prevent further compromise.
- If you clicked a malicious link or downloaded suspicious attachments, immediately disconnect from the internet to prevent malware from communicating with attackers or spreading to other systems.
- Change all potentially compromised passwords starting with your email account, then any other accounts that use the same or similar credentials, prioritizing financial and work-related accounts.
- Contact your IT security team or help desk immediately to report the incident and get guidance on additional protective measures specific to your organization’s systems and policies.
- Document everything, including the original email, any actions you took, and the time the incident occurred, to help with investigation and recovery efforts.
- Check your accounts for unauthorized activity, particularly financial accounts, and monitor for any suspicious transactions or changes to account settings.
- Run a full system scan with updated antivirus software if you suspect a malware infection, and consider having IT professionals perform a more thorough security assessment.
Internal and External Reporting Channels
Proper reporting helps organizations learn from incidents and can assist law enforcement in tracking down cyber criminals. Most companies have established procedures for handling security incidents that employees should follow.
Internal Reporting
Report the incident to your organization’s IT security team, help desk, or designated incident response contact immediately. Many companies have specific email addresses or phone numbers for security incidents that ensure a rapid response. Your security team can help assess the scope of the compromise and implement additional protective measures.
External Reporting Options
Several government agencies collect information about email fraud to help combat these crimes. The Internet Crime Complaint Center (IC3), operated by the FBI, accepts reports of internet-related criminal activity and uses this data to identify trends and pursue investigations. The Federal Trade Commission (FTC) also collects consumer fraud reports through its online complaint system, which helps track scam patterns and warn other potential victims.
If financial fraud is involved, contact your bank or credit card company immediately to report unauthorized transactions and request account monitoring. For identity theft concerns, consider filing a report with the FTC’s IdentityTheft.gov website, which provides personalized recovery plans and connects victims with relevant resources.
Recovery Steps and Lessons Learned
Getting back on track after falling for an email scam requires both fixing the immediate technical problems and making sure it doesn’t happen again. The good news is that most organizations can recover quickly when they take the right steps and learn from what went wrong.
Technical Recovery
Your first priority is working with your IT team to make sure everything is actually secure before resuming business as usual. This might mean wiping and rebuilding computers, updating security software, or setting up extra monitoring to catch any lingering problems. You’ll also want to change passwords for all your accounts — and this is a great time to finally start using that password manager you’ve been meaning to set up. Strong, unique passwords across all your services can prevent one compromised account from turning into a bigger headache.
Financial Recovery
If money changed hands or your financial information got compromised, time is of the essence. Get on the phone with your bank and any other financial institutions right away to see what transactions can be reversed and what additional monitoring they can put in place. Keep detailed records of everything — all the financial losses, recovery costs, and time spent dealing with the mess. You’ll need this documentation if you’re filing insurance claims or if law enforcement gets involved.
Process Improvements
Here’s where you can turn a bad situation into something positive for your organization. Take a hard look at what warning signs got missed and figure out how to catch similar tricks next time. This might mean rolling out additional security training that focuses specifically on the attack methods that worked against you. The key is being honest about what went wrong without pointing fingers — even the most security-savvy people can get caught by sophisticated scams.
Personal Learning
Think about what made that fraudulent email so convincing in the first place. Was it the urgent tone? The familiar sender name? The official-looking format? Understanding your own vulnerability helps you spot similar tactics down the road. Don’t keep this knowledge to yourself — share your experience with your team and colleagues. Most people appreciate the heads-up about new scam techniques, and your openness can prevent others from falling into the same trap.
Remember, getting fooled by a well-crafted scam isn’t a personal failing. These attacks succeed because criminals have gotten really good at exploiting how our brains work, not because their targets aren’t smart enough. The most important thing is responding quickly and learning from the experience to build better defenses going forward.
How Proofpoint Can Help
Email scams represent one of the most persistent threats facing organizations today, but they don’t have to succeed against your business. Proofpoint’s advanced email security platform combines AI-driven threat detection with comprehensive email filtering to identify and block sophisticated fraud attempts before they reach employees’ inboxes. Our integrated security awareness training solutions transform your workforce from potential victims into active defenders by teaching them to recognize and report the latest social engineering tactics. With Proofpoint’s human-centric approach to cybersecurity, organizations can build layered defenses that protect both people and data from the evolving landscape of email-based threats. Contact Proofpoint to learn more.











