Virtual desktop infrastructure (VDI) predates the recent phenomenon of widespread remote work. But it took the rapid expansion of “anywhere working” over the last two years to really highlight VDI’s value in supporting remote workforce productivity.
However, while VDI makes it easy for remote workers to access corporate assets, it also increases the risk of insider threats. Whether a remote worker is a full-time employee accessing a persistent virtual desktop from a company machine or a contract worker accessing a non-persistent virtual desktop from a personal machine, data can easily leak outside the VDI environment.
So, how can an enterprise reap the productivity benefits of VDI for its remote workers while ensuring protection for intellectual property (IP) and sensitive information? It starts with understanding why corporate assets are at risk in the first place.
Traditional endpoint security isn’t enough
Most modern IT environments use the cloud for data storage, making data present outside the corporate data center and easily accessible from anywhere. Traditional security mechanisms, like perimeter protection, aren’t sufficient for safeguarding data in this scenario. IT administrators need to take a multi-pronged approach instead.
Virtual desktop environments hosted by cloud providers have basic protection at the endpoint. So, an IT administrator should at least enable built-in controls provided by the cloud vendor to prevent data loss from the virtual desktop to the host machine.
However, these built-in controls don’t have the granularity needed to protect sensitive data leakage to the cloud while empowering remote workers to take full advantage of the flexibility of VDI. For example, low risk users within an organization should be monitored to ensure that sensitive data is handled properly and educated in scenarios when it is not. However, high risk users (malicious, compromised, negligent) may need additional monitoring and potentially prevention mechanisms to avoid data loss by malicious insiders. This is where an additional level of protection provided by an insider threat management (ITM) and data loss prevention (DLP) solution, like the one from Proofpoint, can provide a security advantage.
Deploying the endpoint agent in a virtual desktop environment
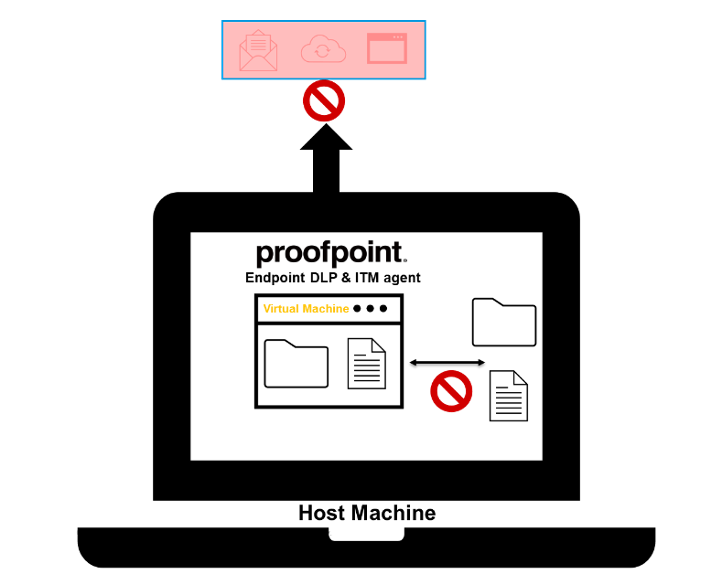
Figure 1: Proofpoint Endpoint DLP and ITM agent on a computer screen
The Proofpoint endpoint agent provides a dual layer of protection. It has two primary modes of operation:
- DLP mode: When the agent operates in DLP mode, it monitors and optionally blocks data loss on the most common data exfiltration operations, like copying to USB, syncing files to mapped cloud-sharing sites, uploading files to the web, and printing.
- Insider threat mode: For high-risk users, the endpoint agent can be configured to operate in the insider threat mode to monitor user activities, such as application use and web browsing.
In both modes, IT administrators can receive alerts about high-risk activities, which can be triaged in the Proofpoint Information Protection console. The administrator can then determine if the alert should be forwarded to a third-party system, like a ticketing system, SIEM (security information and event management) or SOAR (security, orchestration, automation and response).
Such integrations can enable a more efficient incident response workflow with business partners within the organization, such as human resources and legal. Further, the Proofpoint Information Protection platform provides a bi-directional flow for an efficient response workflow through the use of webhooks and APIs so that the analyst time can be better spent on investigations vs. duplicating incident management tasks.
Customer example
A global pharmaceutical company was looking for a scalable, efficient ITM and DLP solution. Its existing DLP solution wasn’t effective at safeguarding the company’s IP and trade secrets in today’s hybrid work environment.
The company also wanted to protect the many virtual desktops provided to its contractors and hosted by Amazon WorkSpaces from Amazon Web Services (AWS). Built-in controls in Amazon WorkSpaces provide basic protection to ensure sensitive information doesn’t leak to the host machine, but the pharmaceutical company needs a DLP solution within the virtual desktop to ensure the same sensitive information doesn’t leak to external systems through cloud-sharing sites or personal email accounts.
The single agent from Proofpoint for ITM and DLP provides the company with on-demand content scanning and prevention capabilities to protect its IP and trade secrets. Further, the insider threat management feature helps monitor high-risk employees by providing administrators with additional visibility into unsanctioned application use and unacceptable web browsing.
Insider Threat Management + Endpoint DLP: a winning solution
The Proofpoint endpoint agent can prevent data loss at the endpoint. However, it’s important to recognize that in today’s cloud-centric world, there are multiple channels for exfiltrating data. These channels include email, web and cloud applications.
Organizations should employ solutions like Enterprise DLP from Proofpoint as part of a multi-pronged strategy to protect data fully within the enterprise. Enterprise DLP provides protection on multiple channels and combines DLP and insider threat visibility across all channels into a single plane of glass.
Register for the Proofpoint and AWS webinar
To learn more about how Proofpoint can help protect your virtual desktop environments, please watch the webinar that we co-hosted with AWS on February 8, 2022. Register here to secure your spot today.











