
Mobile Phone Security Part I: Exposed by Default
By: Mike Bailey
The amount of data stored on your smartphone is simply unprecedented, and end users may not be to blame for its collection. Mobile phone security is complicated, and changing all the time due to OS updates and new OSes. In an attempt to increase battery life and improve privacy, I decided to cleanse my phone in relation to its privacy, location, and other settings. This is strictly a personal device, but as a fairly savvy user I have always been strict about what apps are allowed to use what, especially in relation to location preferences. What I found was shocking.
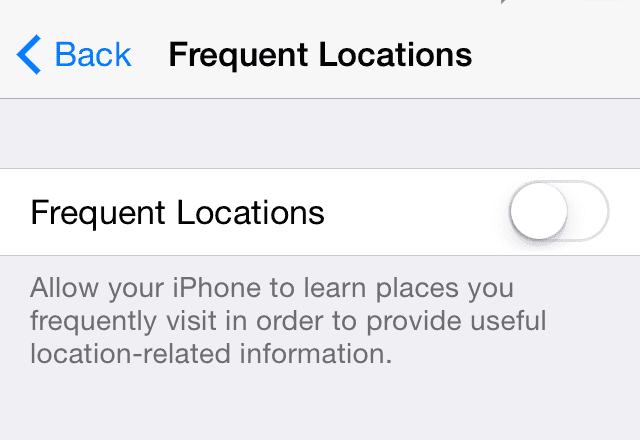
I have an iPhone, and the above is what I saw in System Preferences > Privacy > Location Services > System Services > Frequent Locations. It’s a setting that is unbeknownst to most users tracking their location, likely for advertisements and other internal purposes. It’s buried under so many submenus that most users aren’t likely to find it. By default, this setting is enabled, and it wasn’t an enjoyable experience to see my frequent locations exposed underneath the green “On” toggle.
There are some other location tracking items that are built-in, including the following below (this photo is after I turned these settings off, by default they’re turned on):
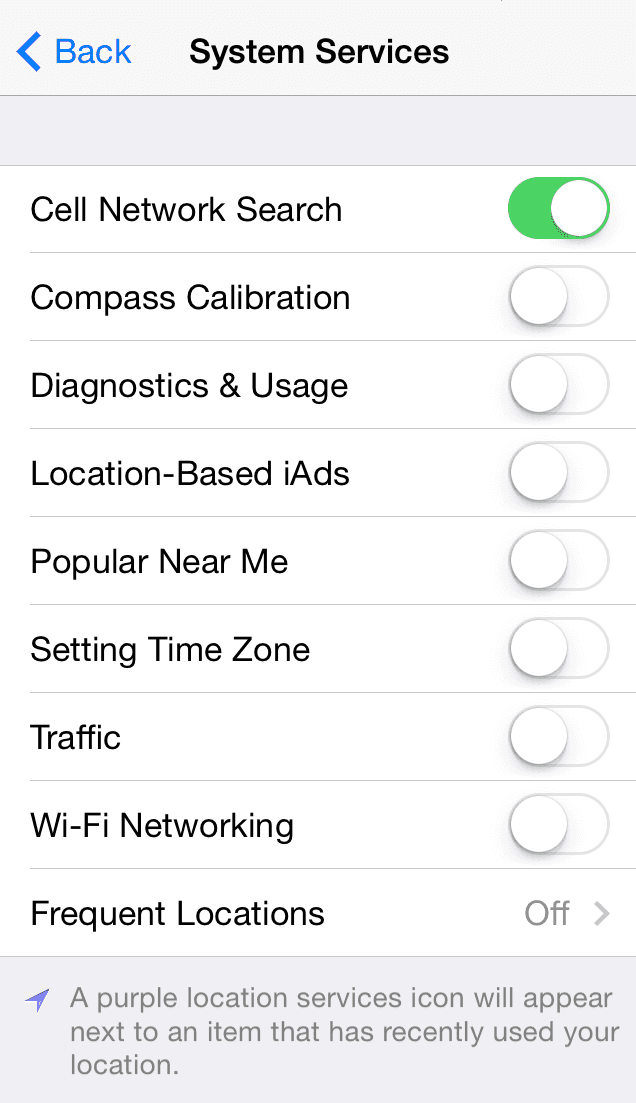
Have you ever wondered how Google knows the current traffic conditions? Similar to the iPhone “Traffic” setting shown above, Android has a built in GPS tracker, which is how you see the green, yellow, or red roads in Google Maps displaying traffic. And this kind of built-in information being submitted to these respective phone companies won’t necessarily flash a navigation icon when active.
Google is upfront about collecting this data, and if you’d like to turn it off they have instructions as well.
As we’ve shown in our training modules, apps don’t necessarily need the data they often request. I’ve noticed an increasing number of applications requesting data they frankly don’t need.
By default, the Google Search application requests access to your photos and Facebook messenger sends your location to other users. As someone who uses these applications frequently, I have to ask, why?
Even if you have location services turned off for an application like Facebook, for instance, your camera application may have access to your location and could attach that information to the photo when you post it.
Employees should be trained to recognize when applications don’t need access to certain information on their phone, and turn items off unless it’s absolutely necessary for the application to function. A lot of the benefits proclaimed frequently by these companies are really nothing more than an agreement to privacy intrusion.
Beyond trusted apps, there are many cases where the apps are listed on trusted app stores but actually contain malware. There are, for instance, a few reasons why applications like the one the application displayed below could be nefarious and something that end users should be aware of. These apps could infect your phone with malware, steal contact information, track your location, or do any number of other alarming privacy intrusions.
And no, your phone, no matter what platform, is not automatically safe. As I mentioned in another post about smartphone security:
“Network World reported that in a recent study by HP, they found that 90% of iOS apps had serious security vulnerabilities.
“More specifically, HP said that 97% of these apps inappropriately accessed private information sources within a device, and 86% proved to be vulnerable to attacks such as SQL injection.”
Things don’t look great for Google Play either. RiskIQ noted in its own study that the percentage of malicious apps on the Google Play store has grown 388% from 2011 to 2013. Even worse is that in 2011 Google was able to remove 60% of malicious apps, which has dropped to only a 23% removal rate in 2013.”
This isn’t just helpful training for employees at work, but also on their own device as well. When making the case for security awareness and training at your organization, the more you can show a marked improvement in everyday end user cases (like for parents managing their privacy or their children’s privacy on devices), the more likely you’ll be able to win favor among your end users and change their behavior.
In Part II, I’ll show you all the ways malicious parties are looking to get access to your personal information. This post won’t include just phishing emails or potential applications above, but new and clever techniques cyber criminals are using to access sensitive data.










