Over the past few years, the topic of phishing consequence models — i.e., formal ramifications for employees who fall for multiple phishing attacks — is one we’ve been hearing more and more infosec professionals talking about. We’ve explored the “carrot vs. stick” conundrum on our blog, and our Security Advisor Alan Levine, a former Fortune 500 CISO with considerable experience in managing cybersecurity teams and programs, has discussed the issue with other industry experts at our Wisdom Conference and in a SecureWorld webinar.
But we also wanted to know what organizations are doing in practice. And so … we asked.
45% of Organizations Use Consequence Models
For our 2018 State of the Phish™ Report, we surveyed our database of infosec professionals about a range of topics, including consequence models. Almost half — 45% — said their end users face ramifications for repeated clicks on phishing tests.
As a follow-up question, we asked what consequences are in place for these so-called “repeat offenders,” and we found that a fair number of organizations go so far as terminating employees who make multiple cybersecurity mistakes:
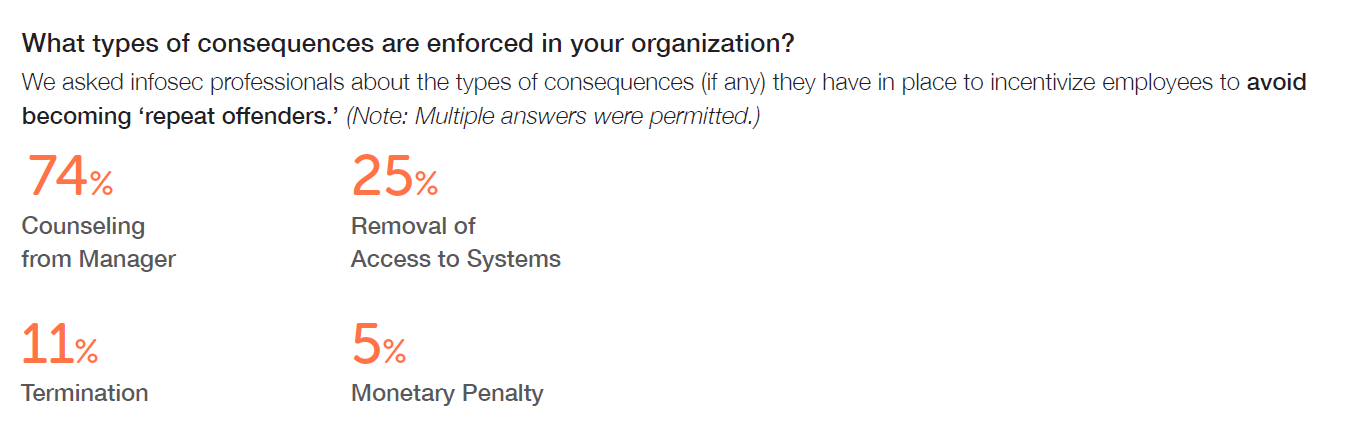
Source: Quarterly surveys of infosec professionals for the 2018 State of the Phish Report
We did allow “Other” as a response for this question, and more than 30% of respondents chose to specify additional consequences that are part of their organization's escalation path. The most common responses included the following:
- Additional computer-based training
- Counseling from the IT department
- One-on-one training from the IT department
- Entry into the organization’s formal discipline process


