Overview
In a study encompassing the first half of 2019, Proofpoint researchers analyzed data from more than one thousand cloud service tenants with over 20 million user accounts. (Tenants are single cloud service deployments in an organization – one organization may be associated with multiple tenants: for example, a G Suite deployment for one department in addition to a corporate Microsoft Office 365 subscription.) We observed over 15 million unauthorized login attempts (or “attacks”), out of which over 400,000 resulted in successful logins. Although we observed large-scale cloud attacks targeting all industries, several trends emerged during the course of this study. Among the industries evaluated, the education and food and beverage sectors were notably vulnerable to successful unauthorized logins. Regulated industries such as healthcare and financial services protected themselves better in comparison, with significantly lower rates of successful attacks. The Fortune 500 companies in our study were heavily targeted and 60% of them experienced at least one compromised cloud account. Certain identified roles including sales representatives and managers were targeted across all industries, presumably because their emails tend to be publicly available and their positions give them access to finance managers, customers, and partners.
In addition to these industry trends, researchers observed the following:
- 85% of organizations were targeted at least once by threat actors
- 45% of organizations experienced at least one compromised cloud account.
- 6% of organizations had an unauthorized login to an executive account
- At organizations with compromised cloud accounts, on average 13 active accounts per organization experienced successful unauthorized logins
- 0.6% of active user accounts were targeted at least once
Taken together, this data demonstrates that threat actors have about a 50% chance of successfully accessing an organization via cloud accounts; history demonstrates that a single compromised account can have a significant impact on an organization’s security.
Trends over Q1 and Q2 2019
In the first quarter of 2019, we observed a substantial spike in unauthorized login attempts against cloud services. Both the volume and efficacy of these attacks moderated in the second quarter. Specifically:
- In Q1, 0.5% of active user accounts were targeted at least once. In Q2, 0.3% of active accounts were targeted.
- In Q1, 50% of organizations analyzed had at least one cloud account compromised by a successful unauthorized login, whereas in Q2, 42% of organizations had compromised accounts.
As noted in a previous blog, a large credential dump in Q1 was the most likely cause of the spike early in the year. In Q2, some organizations appear to have mitigated the risks associated with this credential dump while threat actors burned available credentials in previous attacks.
Top Targeted Industries
Proofpoint compared attacks and their effectiveness against industries represented by at least 10 organizations that were monitored throughout the study period. We found that cloud attacks spared no one particular sector:
- In 12 out of 14 sectors, attackers targeted at least 80% of the organizations under study in each industry.
- Among the industries evaluated, 92% of the analyzed Fortune 500 companies were targeted and 60% experienced a successful unauthorized login.
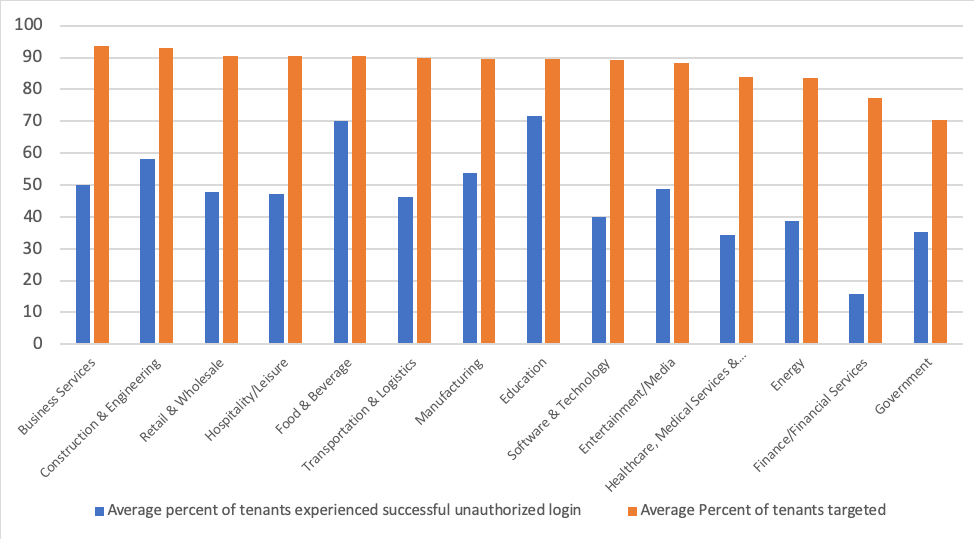
Figure 1: The percent of tenants targeted and that experienced unauthorized logins by industry during the first half of 2019
In the first half of 2019, business services, construction & engineering, and retail and wholesale sectors were slightly more heavily targeted than their peers. However, no single industry was disproportionately targeted or avoided. Regardless of the sector, sales representatives and managers were among the most highly targeted users. The nature of their jobs makes them easier to reach and requires them to respond to unsolicited emails, potentially increasing their exposure to phishing attacks. Threat actors also target sales representatives because they are in frequent contact with people in finance departments and external organizations, enabling lateral movement, supply chain exploitation, and internal phishing.
Most Vulnerable Industries
The education and food and beverage sectors were most vulnerable to cloud attacks, with success ratios (the number of successful unauthorized logins vs. the number of attempts) over 70% in Q1 and Q2 of 2019. Cybercriminals see school districts, colleges, and universities as “easy prey,” with large numbers of students and faculty and decentralized security operations. Common titles among those targeted included “Professor” and “Alumni.” Potentially unused cloud accounts such as those frequently provided to alumni represent ideal targets for brute force attacks and other activities, resulting in spam, malware, and phishing campaigns.
In the food and beverage industry, franchisees were highly targeted and vulnerable. They present an entry point to these organizations’ financial business processes and supply chains, making franchisees ideal targets for wire fraud, lateral movement, and internal phishing. Figure 2 shows the most vulnerable industries we studied based on the effectiveness of attacks.
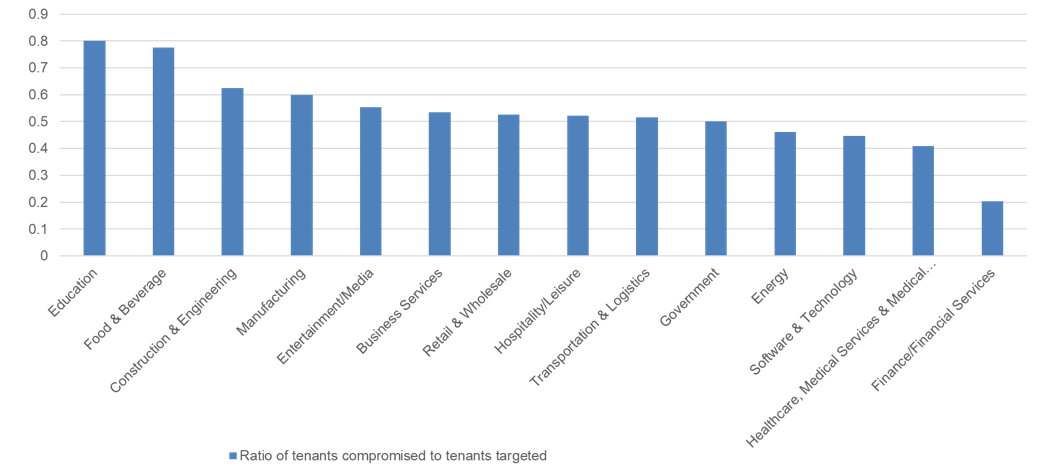
Figure 2: The attack effectiveness ratio by industry during the first half of 2019
Best Protected Industries
Among industries we studied, threat actors had the least success with heavily regulated sectors (Fig. 2), which suggests they implement more stringent security measures in their cloud deployments. In particular, the attack success ratio was 20% for financial institutions and 40% for healthcare organizations, below the average rate of 50%. It is worth noting, however, that colleges and universities are frequently associated with hospitals, national defense interests, and other verticals, increasing the potential risk for organizations outside the specific confines of academia. Moreover, because of the volume of attacks, even seemingly low success ratios still result in significant numbers of potentially compromised organizations even over this relatively short period of time.
Major Threats and New Attack Vectors
In our previous blog, we covered the two prominent attack vectors that pose a major risk to cloud environments – brute force and phishing-related campaigns. Another attack vector is that we have observed involved third party apps that access Office 365 and G Suite data. Infiltration or OAuth token acquisition occurs via phishing, social engineering, baiting, malware, or account compromise. This is a quiet, but persistent data exfiltration methodology and represents a major potential compliance risk. Combating this type of attack requires the ongoing discovery of third-party apps used, OAuth permissions granted, and app reputation. It also requires alerting and the ability to revoke apps automatically.
Many organizations are turning to multi-factor authentication (MFA) as a potential solution. However, threat actors leverage multiple methodologies to bypass or avoid MFA. Attacks that use legacy email protocols such as IMAP are common as discussed in our previous blog. Real-time phishing is a new methodology that phishes not only the first factor but also the second factor during authentication.
Post Account Compromise Activity
After the initial compromise, threat actors can expand their attack by sending internal and external phishing emails. They set up email forwarding rules, install OAuth apps, create new user accounts and upload malware.
Threat actors also launch BEC attacks against employees and partners to commit wire fraud. The majority of successful cloud account brute force attacks result in platforms for spam campaigns, which abuse organizations’ brands and assets. We also observed data exfiltration via malware and email following successful compromises.
Conclusion
This study demonstrates that the cloud threat landscape has no biases in terms of industry; all industries are under attack. Some sectors are more vulnerable, but all organizations can benefit from robust visibility into cloud threats and automated security measures driven by threat intelligence. Appropriate security measures can help prevent or quickly remediate account takeover and further compromises inside organizations or at partners and customers. The Proofpoint Cloud App Security team will continue to monitor emerging trends in user targeting and post-compromise activity.

