During the 2017 US tax season we noted an increase in the use of tax-themed email lures to distribute a variety of malware payloads, in addition to the traditionally popular credential phishing uses. In 2018, Proofpoint researchers have observed another strong season for tax-themed email lures, and the payloads of these campaigns are representative of broader malware trends and highlight notable differences compared to last year.
Tax-themed email lures last year reflected the prevalence of ransomware in email-based malware campaigns at the time, with half of observed campaigns distributing ransomware strains, and the remainder sending banking Trojans and a RAT, relying mainly on document attachments with malicious macros.
Malware campaigns
Starting in January, when overall threat actor activity was still enjoying a relative lull following the holidays, threat actors were leveraging tax-themed lures to spread banking Trojans, ransomware, and remote access Trojans (RAT). RATs have been a popular payload for tax-themed email lures, typified in campaigns distributing a range of RATs such as Orcus RAT, Netwire, and Remcos RAT, and targeting organizations around the US with a wide variety of email subjects:
- Tax preparation Assistance needed
- Tax Accountant needed
- 2017 Tax Return
- my 2017 taxreturn
- Transcript/W-2s
- Action Require!
- Urgent Request!
- Help! Tax Return
- As Usual. Tax Information.
- Dear CPA
- Dear Tax Accountant
While many of these campaigns have been fairly indiscriminate in their targeting, some were also much more narrowly targeted at organizations in vertical such as Legal, Accounting, and others with a particular interest in tax returns and related communications.
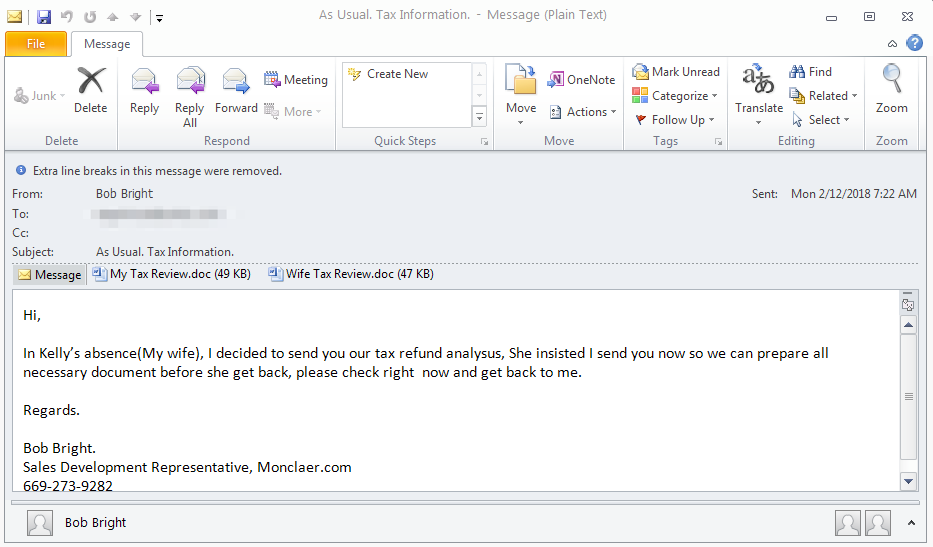
Figure 1: Tax-themed email lure distributing a RAT
The messages included document attachments in Microsoft Word or Excel formats with filenames that often included the names of individuals or keywords like "W2" and used malicious macros to download and install their payloads.
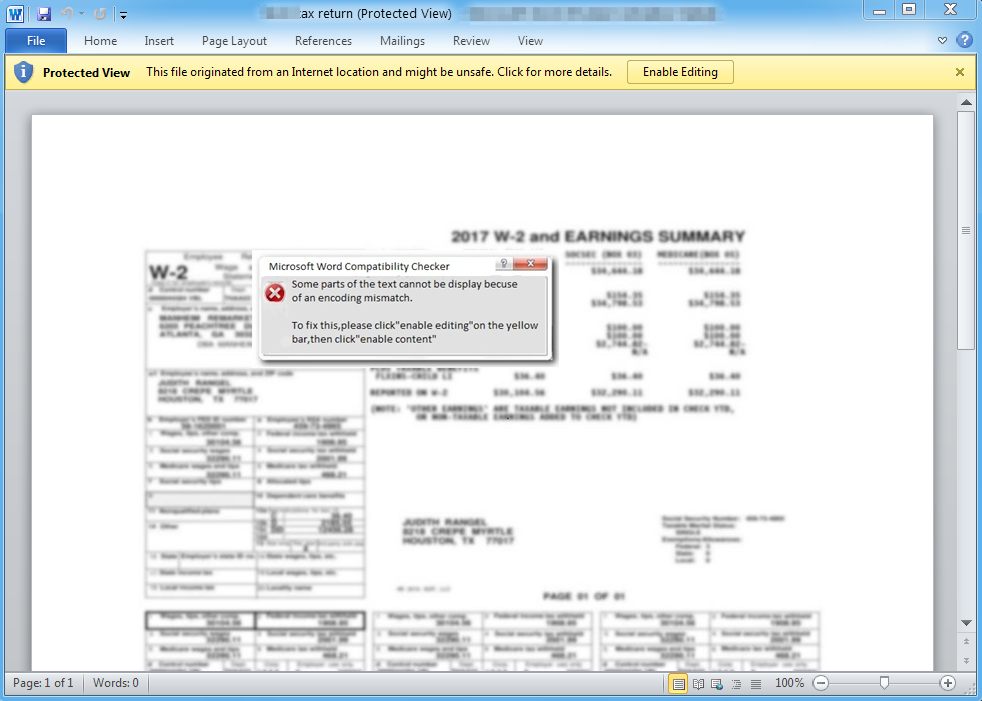
Figure 2: Malicious document attachment with fake error dialog instructing the user to enable embedded content to view the document, which will instead download and install a RAT
As the example in Figure 1 shows, threat actors leveraged the recipients' expectations that sensitive personal financial information would not be sent without some form of encryption to trick the victims into clicking the Enable Content button that would allow the embedded macros to run. While the use of fake encoding or encryption messages in malicious document attachments has been a staple of email-based campaigns for over two years, threat actors continue to innovate with the fake error messages that they display to users, including using more realistic and seemingly technical dialog boxes to get the user to click on that Enable Content button.
Banking Trojans are also a popular payloads for email-based campaigns, and this applies as well to tax-themed email lures. February campaigns distributing Ursnif and Dridex and targeting organizations in the United States exemplify the use of social engineering and realistic details to create a sense of urgency and legitimacy.
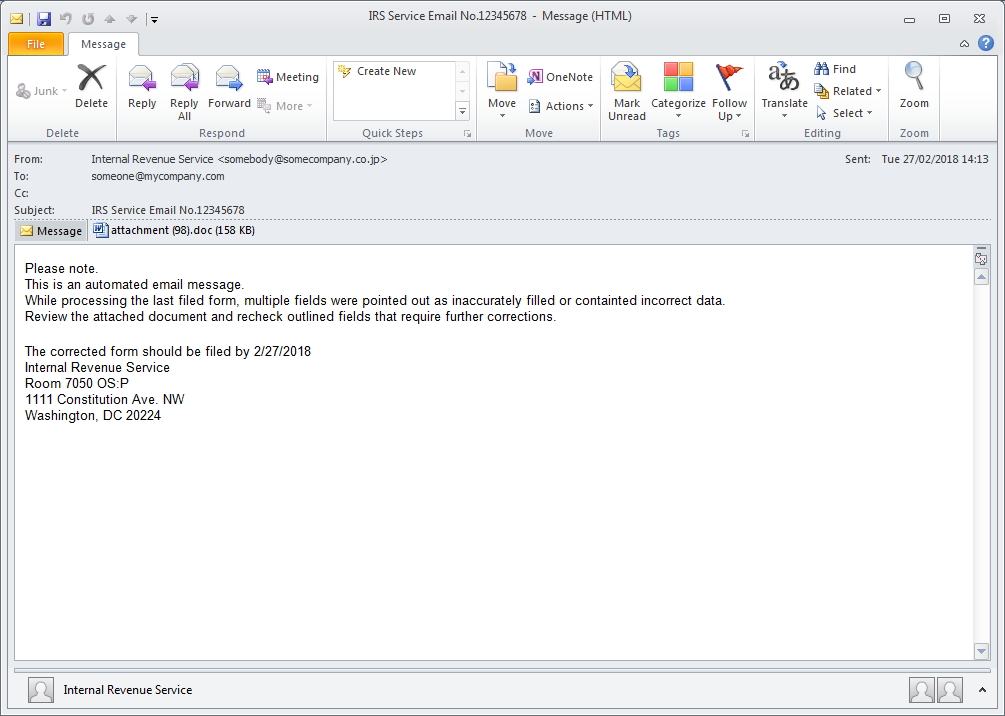
Figure 3: Tax-themed email lure for US-targeted Ursnif campaign
Simple language, realistic details such as including a correct street address for the IRS, and a concise request related to the document attachment are the hallmarks of an effective email lure and reflect the techniques that have predominated in the threat landscape since late 2014.
As in 2017, tax-themed banking Trojan campaigns in 2018 have not been limited to the United States, as campaigns distributing Ursnif, Pykbot (aka Pkybot), and others have demonstrated. Like their US-targeted counterparts, these campaigns used email lures with advertising either overdue taxes or tax refunds to trick the user into opening the attached document and enabling the embedded macros. In addition to geographic targeting, some campaigns were also vertically targeted while others leveraged legitimate email marketing mass-mailing services such as Sendgrid for their sending infrastructure.
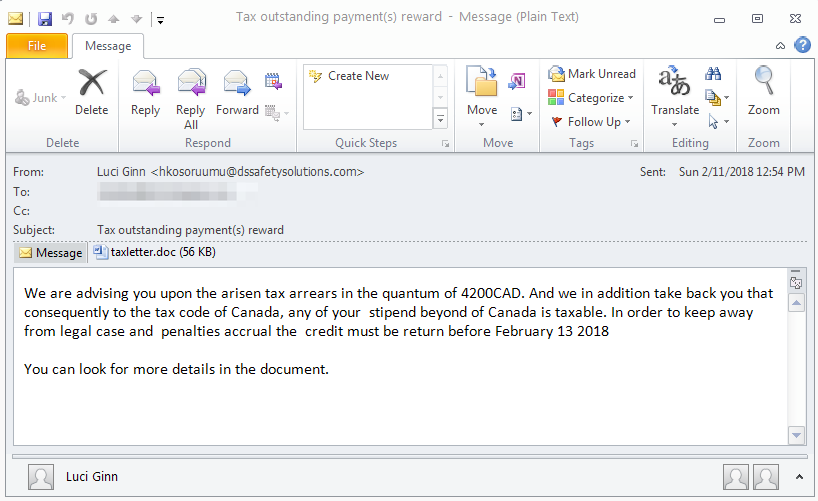
Figure 4: Tax-themed email lure for Canadian-targeted Pykbot / Pkybot campaign

Figure 5: Document attachment featuring stolen branding, with macros that download Ursnif banking Trojan, Australian-targeted campaign
However, as in the broader threat landscape, in tax-themed email lures ransomware remains a persistent danger. An early February campaign employed messages with Subjects such as "IRS Urgent Notification", "Overdue on Realty Tax", and “IRS Urgent Notification-7985662” and Zip or RAR archives attachments containing Microsoft Word documents with macros that would will download Rapid ransomware should the user be tricked into enabling them.
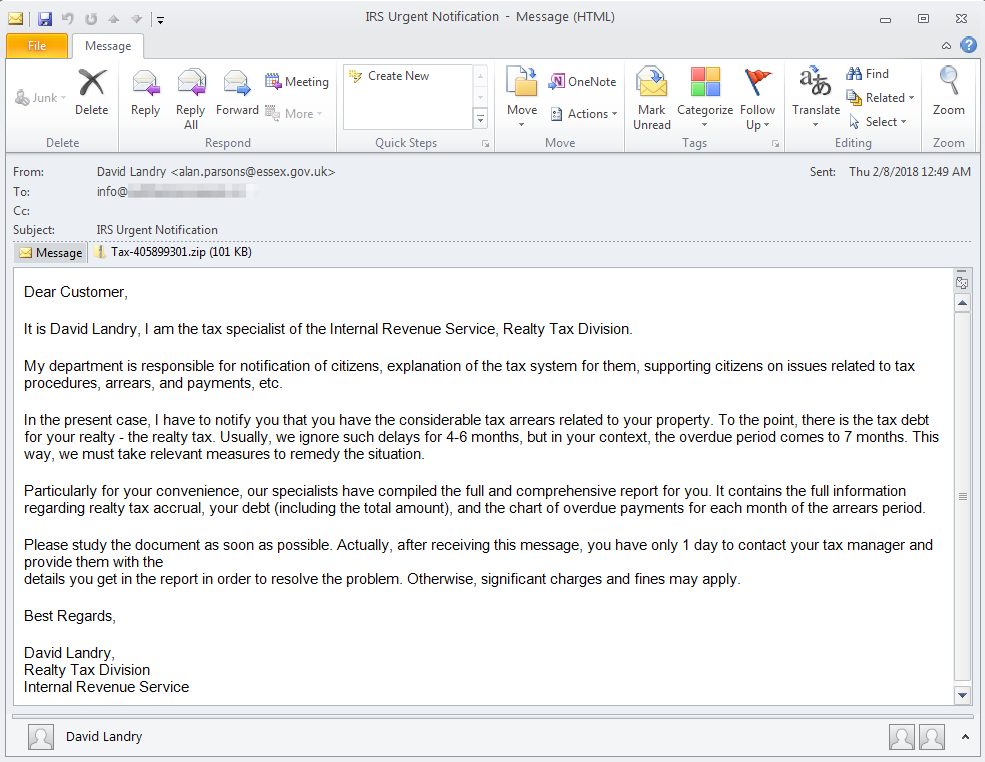
Figure 6: Fake IRS communication email lure used to distribute Rapid ransomware
Credential phishing campaigns
In IRS phishing, attackers attempt to steal a victim’s personal information through the use of a fake IRS login or tax return form page. In the attack, the actor crafts a fake IRS page and hosts it on a server they control, then embeds the URL for this page in a phishing email. The email can be sent as part of a broad-based or highly targeted campaign, and leads to a fake IRS page that carries graphics and branding very similar to those of the legitimate site.
If malware campaigns that used tax-themed email lures reflected a broader trend towards banking Trojan and RAT payloads, tax-themed credential phishing lures highlighted overall consistency of credential phishing lures from 2017 to 2018, with few significant changes in templates and landing pages.
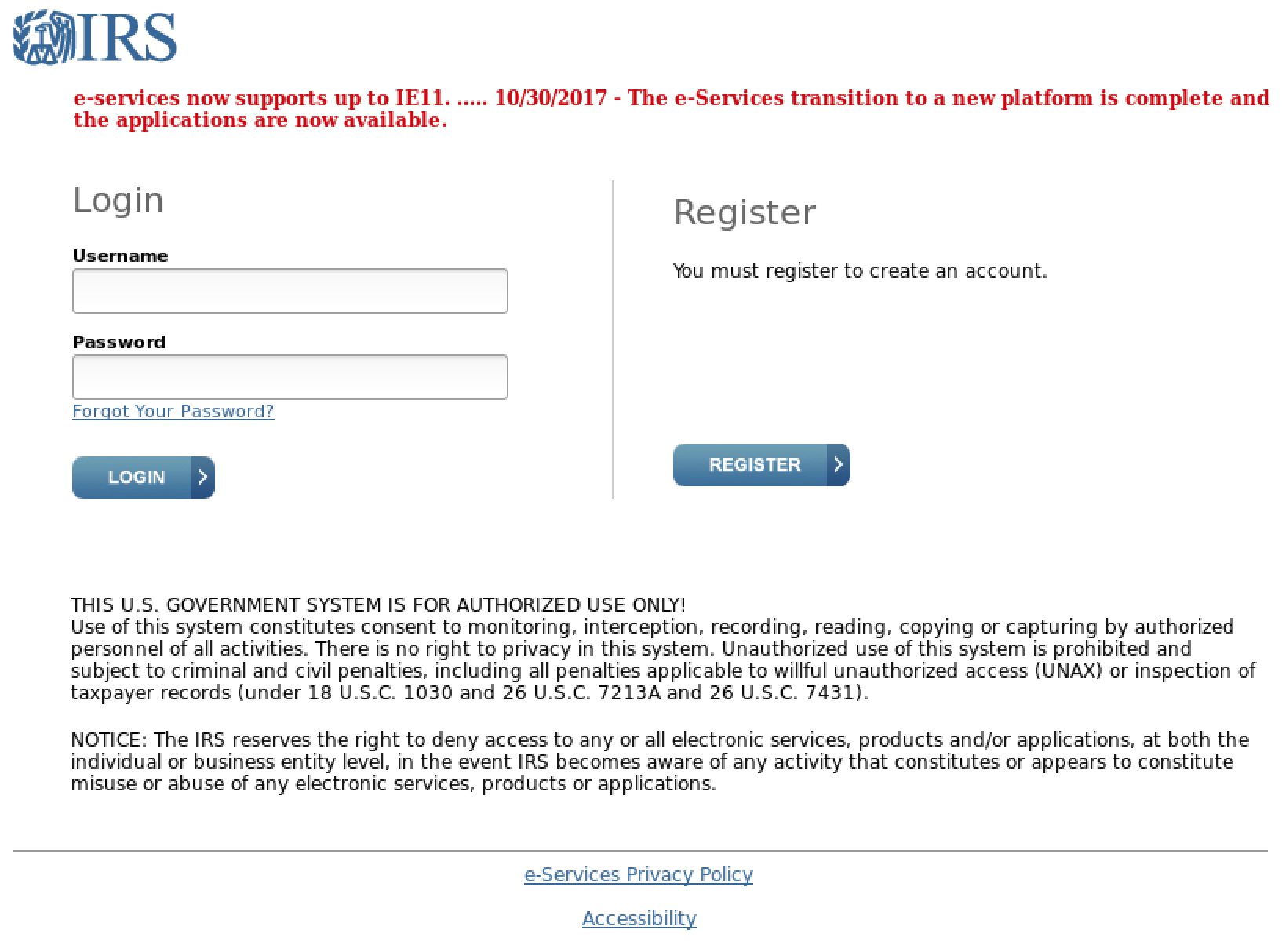
Figure 7: Common tax-themed credential phishing landing page
Against this backdrop of consistency, credential phishing threat actors have been busy updating their IRS lures and landing pages to reflect the current tax year, legal requirements, and other elements that can add to the perceived legitimacy and urgency of these attacks (Fig. 8).
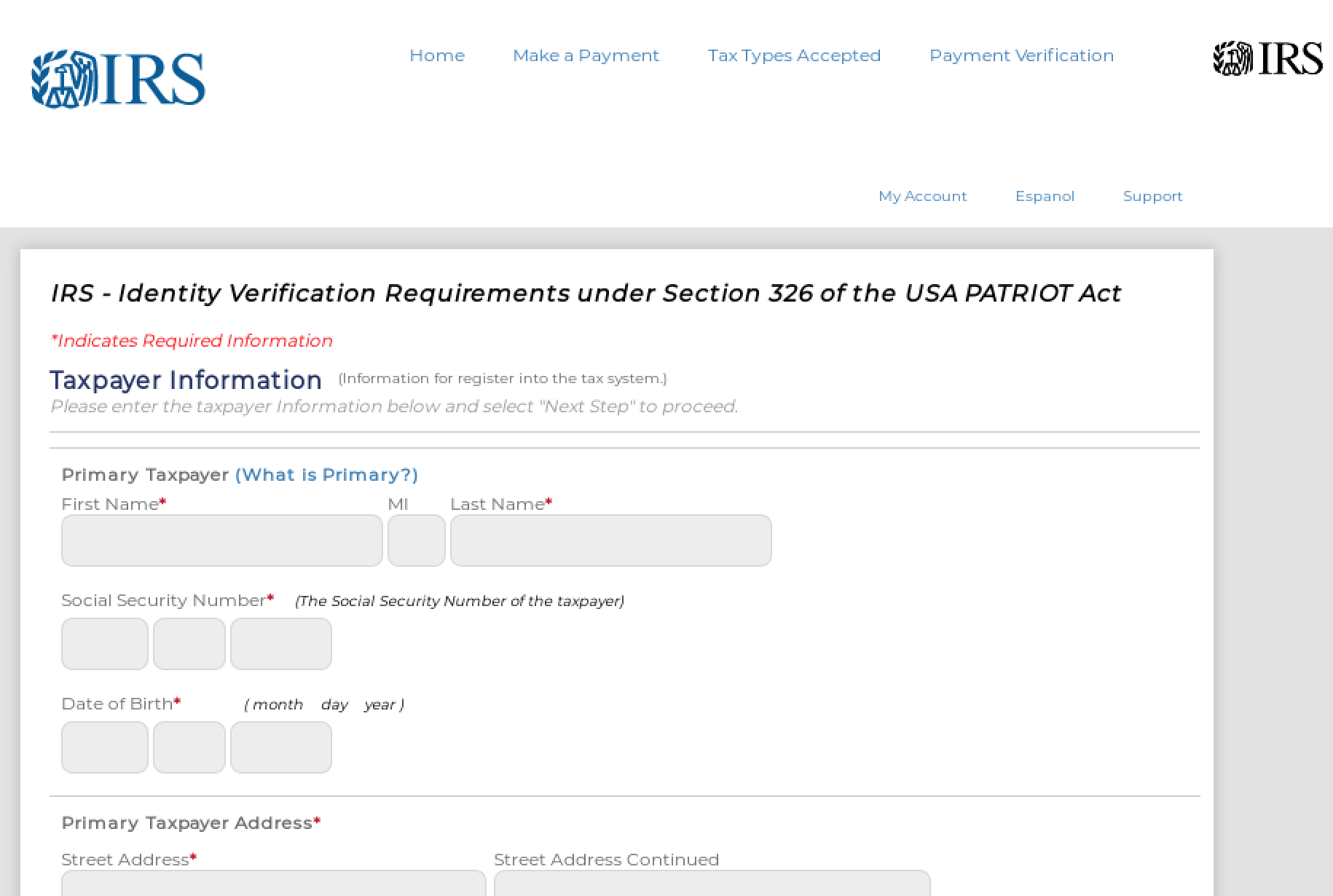
Figure 8: Tax-themed credential phishing landing page that cites the Patriot Act to convince the user to supply their personal information for the purpose of “verification”
In this example, the wording on the landing page is designed to convince the end user that their identity must be verified in accordance with section 326 of the Patriot Act. Section 326 is entitled ‘International Money Laundering Abatement and Anti-terrorist Financing Act of 2001’ and states “These provisions are intended to facilitate the prevention, detection, and prosecution of international money laundering and the financing of terrorism.”
IRS-themed credential phish also borrow from the “locked account” lures common in consumer financial account phishing campaigns, capitalizing on popular news reports of fraudulently filed tax returns and identity theft. For example, the credential phishing landing page below tries to convince the victim that their account has been locked and that they need to provide extensive personal information in order to unlock it, again leveraging stolen branding and page design modeled on legitimate IRS sites to make a realistic-looking landing page.
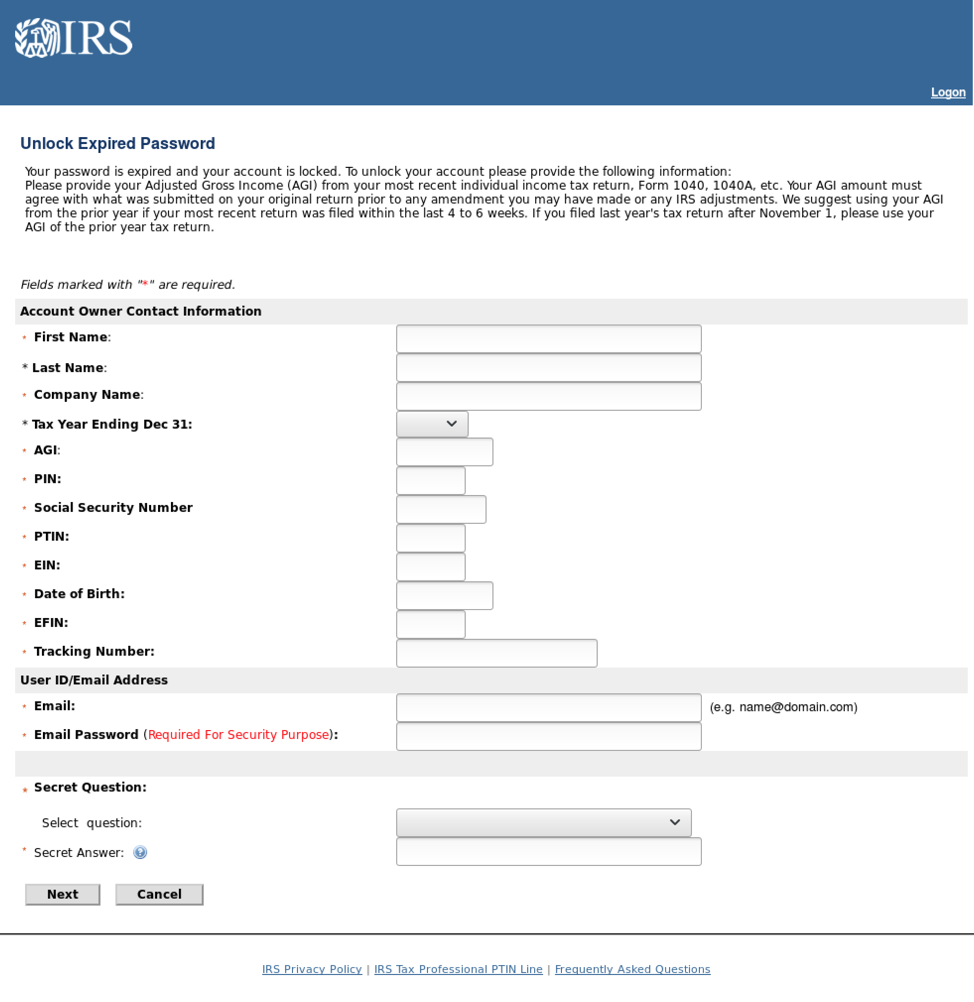
Figure 9: “Locked account” themed IRS credential phishing page
While many IRS credential phishing landing pages continue to ask victims to provide an ever-expanding array of sensitive personal information, some threat actors are taking the opposite approach. Realizing that an individual’s tax returns already contain a rich trove of sensitive details, some campaigns forego requesting credentials and other information and instead simply try to convince victims to upload their tax information directly to the landing page (Fig. 10).
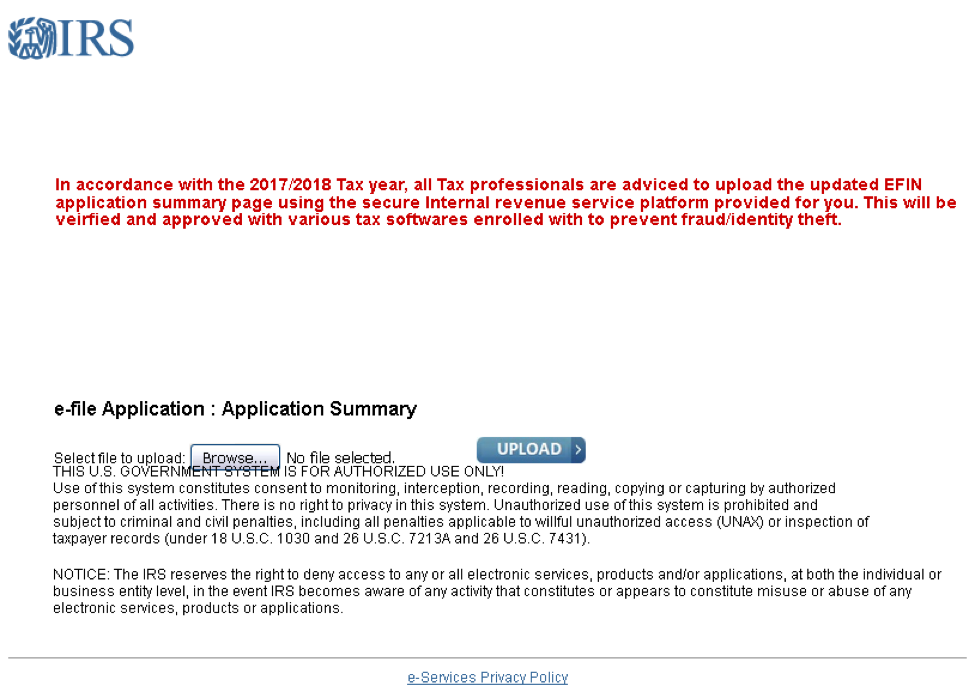
Figure 10: IRS phishing landing page that instructs the user to upload their tax returns, rather than provide credentials and other personal information
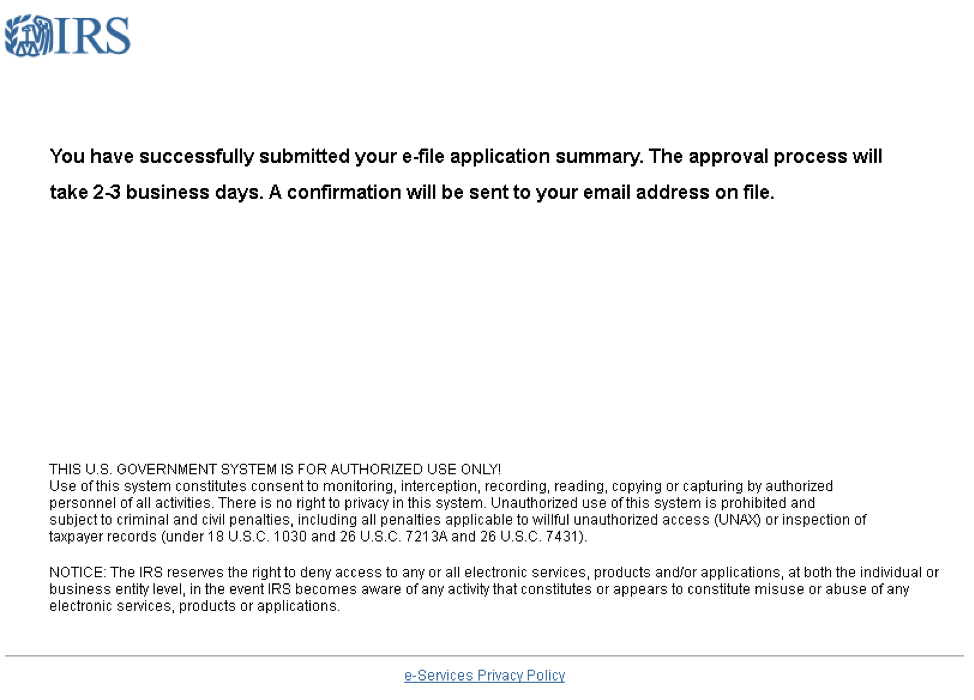
Figure 11: “Successful upload” message on IRS-themed phishing landing page, displayed after the victim uploads their tax returns
Tax preparation services are also being phished, it is common to see credentials for popular tax preparation tools targeted for harvesting using emails that include stolen branding and, in some cases, spoofed or typosquatted domains.
Tax-themed phishing beyond the US
The United States is not the only country where “death and taxes,” as the saying goes, are inescapable. Tax-themed phishing is an international concern, we frequently observe phishing landing pages that abuse various national tax agency names and branding throughout the year.
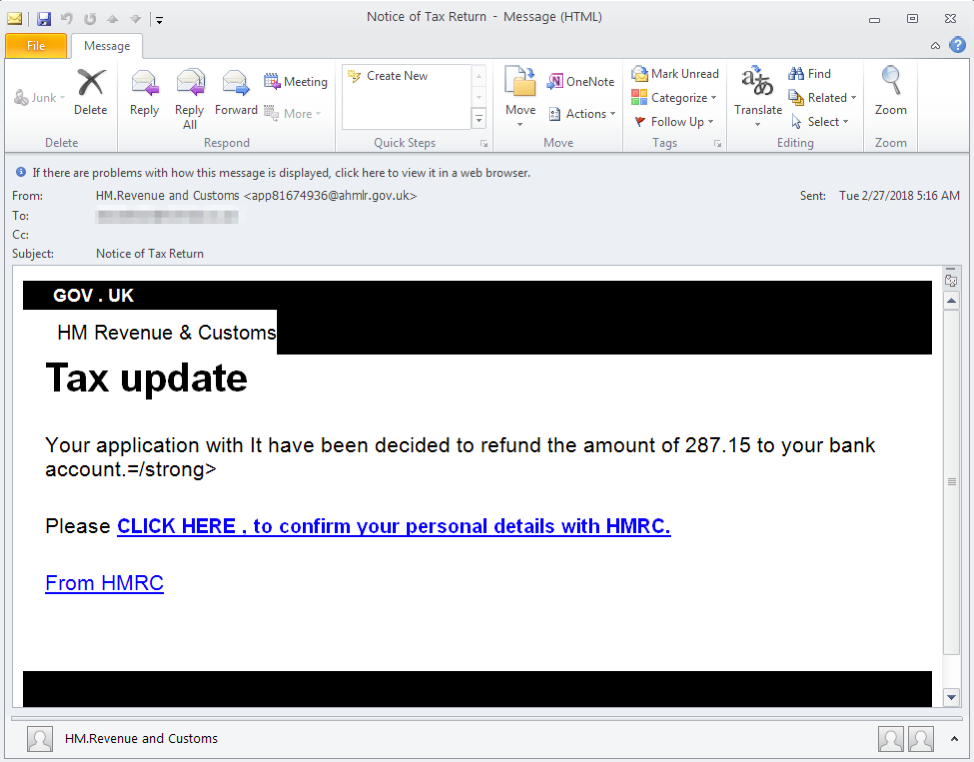
Figure 12: HMRC tax-themed phishing email lure (UK)
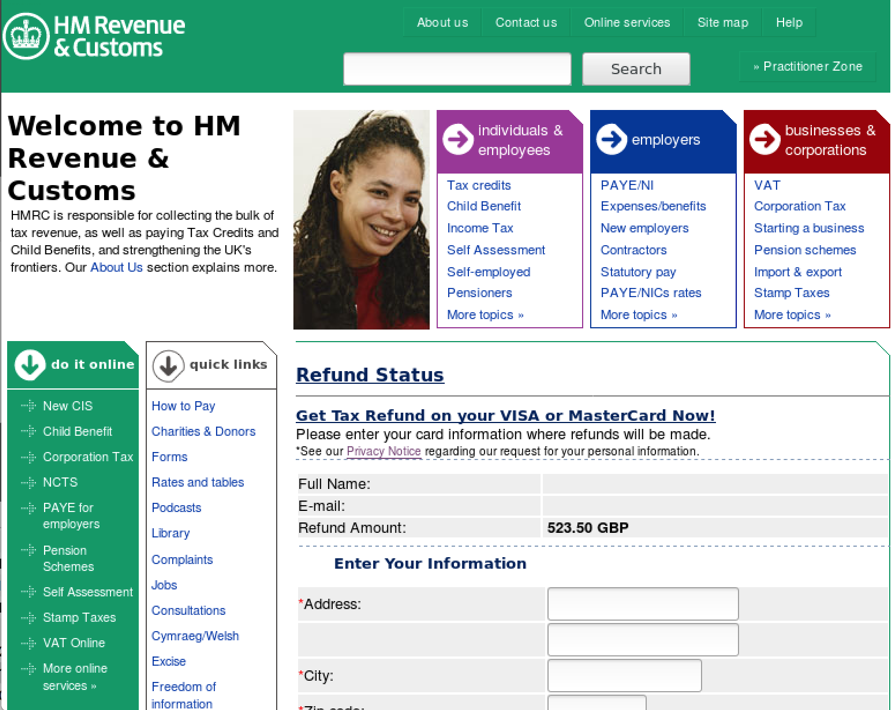
Figure 13: Fake HMRC page used for credential phishing (UK)
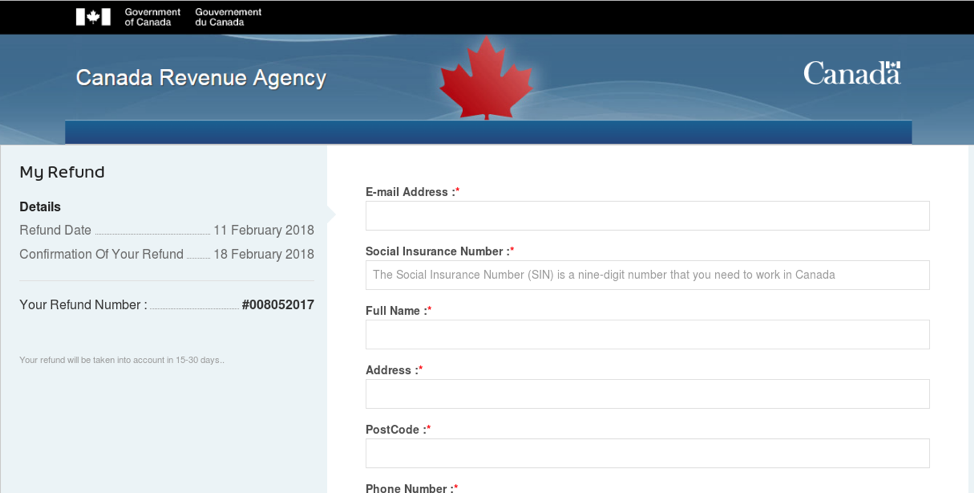
Figure 14: Fake Canadian revenue authority page used for credential phishing (Canada)
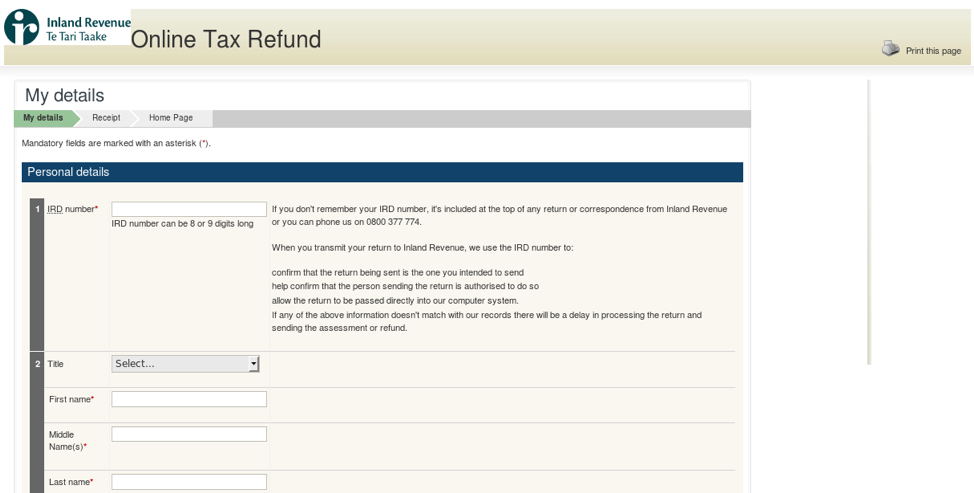
Figure 15: Fake Irish revenue authority page used for credential phishing (Ireland)
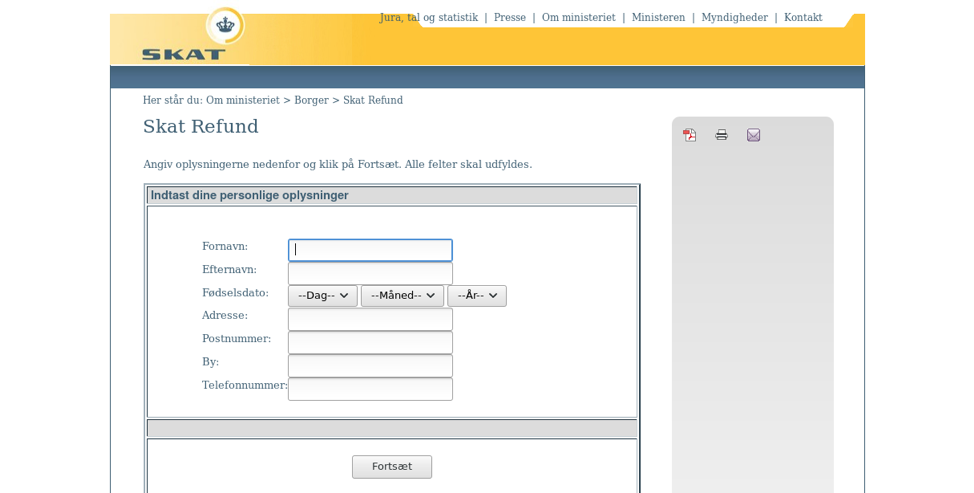
Figure 16: Fake Danish revenue authority page used for credential phishing (Denmark)
Conclusion
Cybercriminals follow the money, and tax season creates a host of opportunities for threat actors to target individuals and organizations for financial theft and fraud using email and social engineering. Tax-themed email lures mirror broader trends in the threat landscape, with threat actors distributing banking Trojans, RATs, and ransomware in both broad-based and targeted campaigns in the US and abroad. Like the cybercriminals' toolkit, this well-worn lure is continually refreshed in email-based attacks.
Selection of Indicators of Compromise (IOCs)
Indicators of Compromise (Rapid Ransomware)
|
IOC |
IOC Type |
Description |
|---|---|---|
|
4853814f0844a50ff3433980982835f9ea9bef7b20e19cbeea6f5a80ff1ff287 |
SHA256 |
Notification-0058291104.doc attachment |
|
hxxps://angrybirdsnew[.]top/fuksol/ccvhosting.exe?rnd=37610 |
URL |
Rapid Ransomware payload URL |
|
hxxps://goalkutoffsa.top/dowloadjs/agentx.exe?rnd=37610 |
URL |
Rapid Ransomware payload URL |
|
83fc3c3ec936e31778d6ef7cb505faebdfb308a700bbae957ecc576796d19914 |
SHA256 |
Rapid Ransomware |
|
decryptsupport@airmail.cc |
|
Rapid Ransomware payment email |
|
supportlocker@firemail.cc |
|
Rapid Ransomware payment email |
Indicators of Compromise (Pykbot)
|
IOC |
IOC Type |
Description |
|---|---|---|
|
071d30bb2961a7e49e1f95b6725d8cbf001a256e49c31a01d2fb048f65a63779 |
SHA256 |
Taxletter.doc attachment |
|
hxxp://bigrussiandomains[.]win/tax.exe |
URL |
Document Payload |
|
b670faa0d89b9e93d32ab9a98847937aeaccf884d9c8d1975c4ac15c496f49aa |
SHA256 |
Pykbot |
|
bigrussiandomains[.]win/js.php |
URL |
C&C |
|
bigbendurofj[.]win/js.php |
URL |
C&C |
|
truecryptforall[.]win/js.php |
URL |
C&C |
|
breetgurot[.]win/js.php |
URL |
C&C |
|
windwildwin[.]win/js.php |
URL |
C&C |
|
bigrusosdartki[.]win/js.php |
URL |
C&C |
|
komptrunkcer[.]win/js.php |
URL |
C&C |
|
metaferumke[.]win/js.php |
URL |
C&C |
|
lionutrasi[.]win/js.php |
URL |
C&C |
Indicators of Compromise (Ursnif)
|
IOC |
IOC Type |
Description |
|---|---|---|
|
177b923ac3f30f5b837911e272d29399420a61657fc55931ec3b4fd7c2968a83 |
SHA256 |
Cpa_invoice.doc attachment |
|
hxxp://94.23.43[.]189/contacts/contacts.all |
URL |
Document Payload |
|
hxxp://37.59.50[.]189/contacts/contacts.all |
URL |
Document Payload |
|
11a76eb0ce0ddbd10e2e573ae6d20f233c052586a96fc91aa6da53e4ad1d6cb5 |
SHA256 |
Ursnif id 1080118 |
|
203.24.188[.]166 |
IP |
Ursnif C2 |
Indicators of Compromise (Tax-themed RAT Example)
|
IOC |
IOC Type |
Description |
|---|---|---|
|
8cabb48e50d72bcc315bc53a5ab62907dae22f68d08c78a5e7ed42270080d4d1 |
SHA256 |
Wife Tax Review.doc |
|
hxxp://maxi.erlivia[.]ltd/luitgfdrwsgyi8hfed4e5.png |
URL |
Document Payload |
|
21e16f82275a9c168f0ce0d5c817cdbbc5d6d7764bb2e2ab8b63dff70f972600 |
SHA256 |
luitgfdrwsgyi8hfed4e5.png (Imminent Monitor) |
|
anotis.publicvm[.]com |
Hostname |
Imminent Monitor C&C |
Selection of ET and ETPRO Suricata/Snort Signatures
2809023 | ETPRO TROJAN Pkybot Checkin
2828152 | ETPRO TROJAN Ursnif Malicious SSL Certificate Detected
2815697 | ETPRO TROJAN Imminent Monitor CnC Response

