Overview
As with most major events and trends, threat actors capitalize on Western holidays to craft lures and scams to trick users into clicking, installing malware, transferring funds, and otherwise acting on behalf of cybercriminals. Whether receiving email fraud messages asking users to purchase fake gift cards or using credit cards at terminals compromised with malware, the holidays present a variety of threats for businesses and consumers alike.
In particular, Proofpoint researchers have observed upticks in business email compromise (BEC) scams related to gift cards, holiday-themed lures in malicious emails, “Black Friday” shopping lures, and fluctuations in point-of-sale malware traffic.
Gift Card and Donation BEC Scams
Email fraud, also known as business email compromise (BEC) continues to evolve, as threat actors refine their techniques and explore new means of stealing from the organizations they attack. The FBI recently posted a public advisory on increases in BEC-style attacks in which threat actors requested that victims purchase gift cards for corporate gift-giving or holiday functions. While this emerging technique only represents a small fraction of overall email fraud, we also identified rapid quarter-over-quarter growth this year in email fraud scams related to gift cards and, in many cases, corporate donations.
Email fraud scams related to gift cards and donations were virtually non-existent in the first quarter of 2018. By the second quarter, however, they represented 1%; this percentage more than doubled by Q3 (Figure 1).
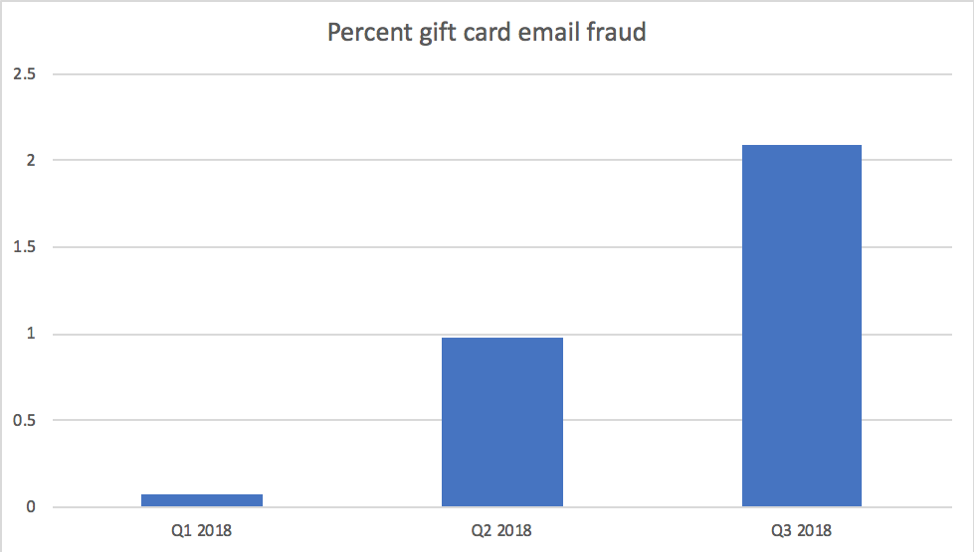
Figure 1: Percent of total email fraud featuring gift card- and donation-related scams by quarter in 2018
Among organizations targeted by email fraud, the proportion experiencing gift card scams also increased rapidly each quarter (Figure 2):
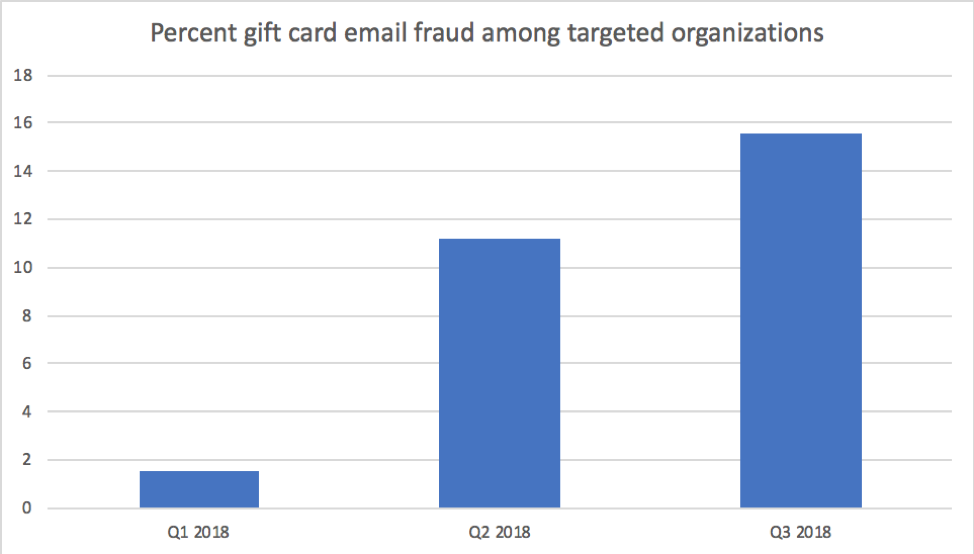
Figure 2: Percent of targeted organizations experiencing gift card- and donation-related email fraud scams by quarter in 2018
Among gift card-related email fraud messages, the top five subject lines were
- itunes gift card
- gift cards
- donation (gift cards)
- amazon gift cards
- gift card
As with most types of email fraud, threat actors targeted companies of all sizes and in all industries. There was no correlation between company characteristics and the likelihood of being targeted by gift card BEC scams.
Point-of-sale malware:
We regularly observe an uptick in so-called point-of-sale (POS) malware activity around Black Friday and coming into the holiday shopping season. Cybercriminals are well aware that these are the busiest shopping days of the year, with countless credit card transactions taking place throughout November and December. Getting POS malware onto even a small number of terminals allows threat actors to scrape credit card data, which can then be used for fraudulent transactions. While the widespread adoption of chip and PIN technology has reduced the effectiveness of some types of POS malware, fraudulent card-not-present transactions are still possible. Moreover, new POS malware has emerged that can calculate authentication codes for chipped cards and use them later for fraudulent transactions.
In 2018, POS malware activity has generally remained fairly steady, with FindPOS continuing unabated as the most common strain we observe in the wild. MagikPOS, however, saw a spike in activity early in November, suggesting potential preparations for the holiday season (Figure 3).
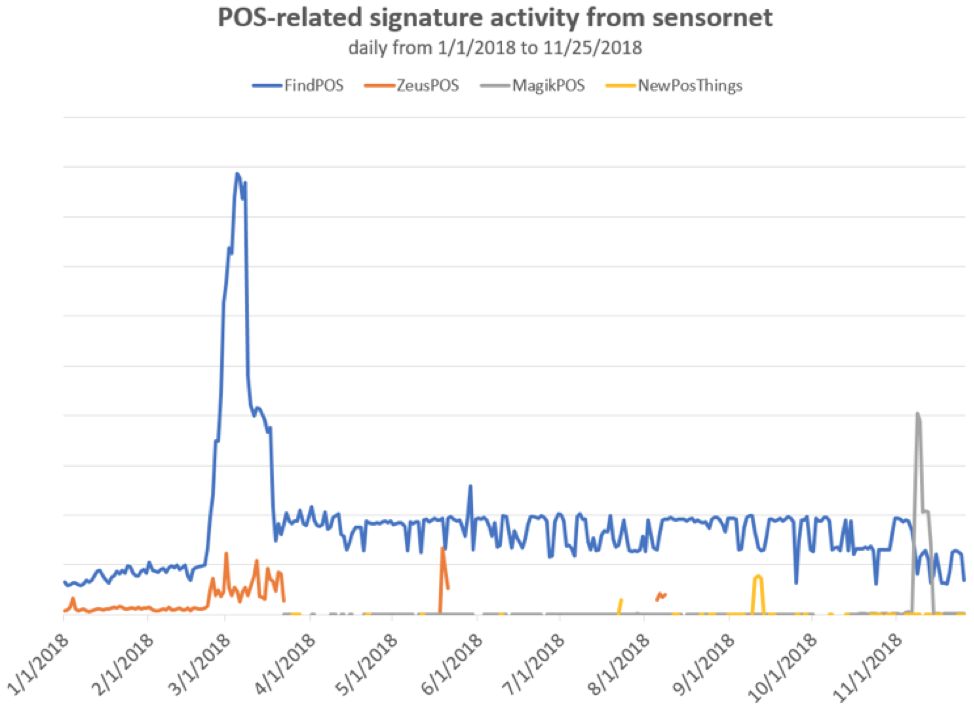
Figure 3: Year-to-date point-of-sale malware activity as detected by Proofpoint IDS sensors
Social media ”angler phishing”
While social platforms have become fairly adept at automatically removing spam comments, more sophisticated threat actors continue to exploit social media channels to directly attack users. Social media support fraud, or “angler phishing” occurs when threat actors attempt to insert themselves into legitimate conversations between brands and users and Black Friday presents many opportunities for users to inquire about available deals, merchandise availability, etc. For example, if a user reaches out to @AcmeAnvils on Twitter, asking whether the local Acme store will have anvils available at Black Friday prices, a cybercriminal may intercept the conversation and offer to hold an anvil if the user provides a credit card number. In this example, the criminal may use an account like @AcmeAnvilsDeals, unbeknownst to the legitimate brand. While this example is somewhat tongue-in-cheek, overall angler phishing is up 486% over this time last year. Users seeking deals on social media should ensure that they are actually interacting with legitimate brands and verified accounts.
Aside from the increasingly pervasive issue of social media support fraud, users should also be on the lookout for more direct malware-bearing threats. In particular, we have been tracking the distribution of malware via holiday e-cards. Attackers are currently abusing Facebook Messenger as a vector for e-card lures, distributing a range of malware from linked attacker-controlled or compromised domains.
Black Friday email spam
Email spam is often not malicious in and of itself. It is generally designed to convince users to click through to a variety of so-called affiliate pages, which may or may not be related to the email spam itself. However, Black Friday-themed spam often takes advantage of recipients’ desire to cash in on increasingly attractive deals, creating tempting clickbait for users. These spam messages may use stolen branding, tantalizing subject lines, and more to convince users to click through, at which point they are often delivered to pages filled with advertising, potential phishing sites, malicious content, offers for counterfeit goods, and more.
Holiday-themed email malware attacks
All holidays and major events provide a variety of fodder for threat actors to create compelling lures and themed email attacks. The threat actors who regularly distribute the Emotet banking Trojan, for example, sent a barrage of Thanksgiving-, Black Friday-, and Cyber Monday-themed malicious spam over the last two weeks. The attached and linked documents (depending upon the email), which the emails claimed were e-cards (Figure 4), Thanksgiving wishes, and shopping discounts with stolen Amazon branding contained malicious code that installed Emotet (Figure 5-7).
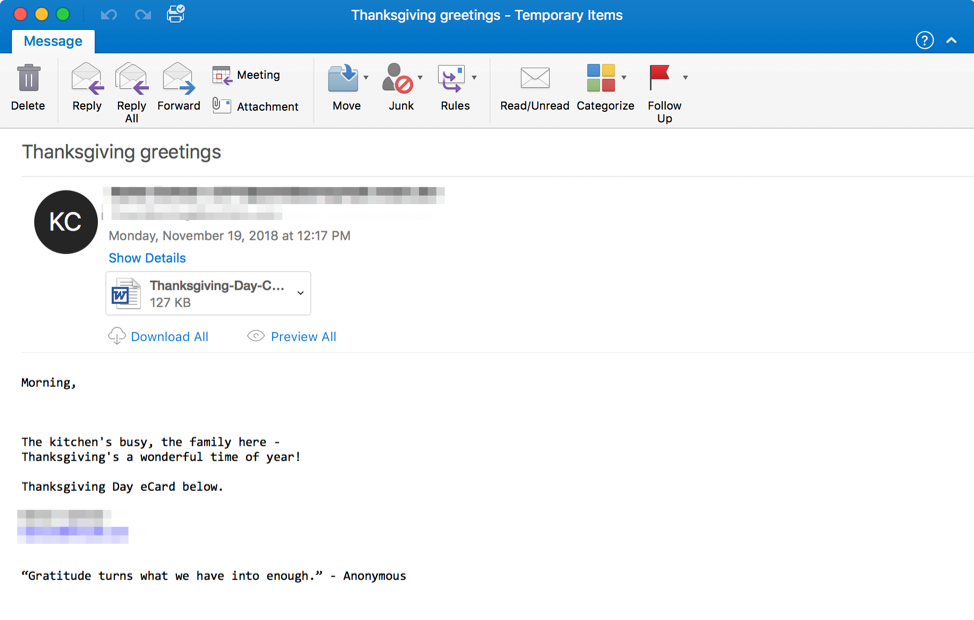
Figure 4: Sample message from a November 19 campaign using a Thanksgiving e-card theme with malicious attachments to distribute Emotet.
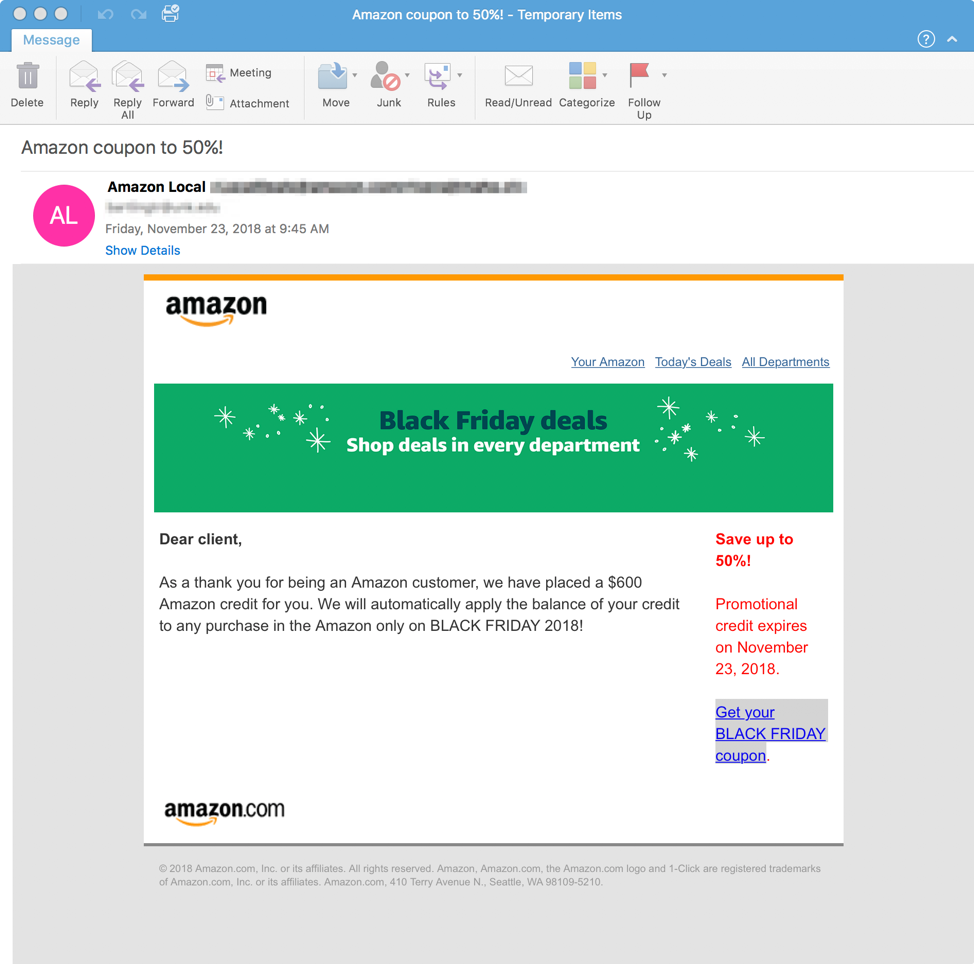
Figure 5: Black Friday-themed Emotet lure using stolen Amazon branding, spoofed sender display name, and a download link leading to a malicious macro-laden document
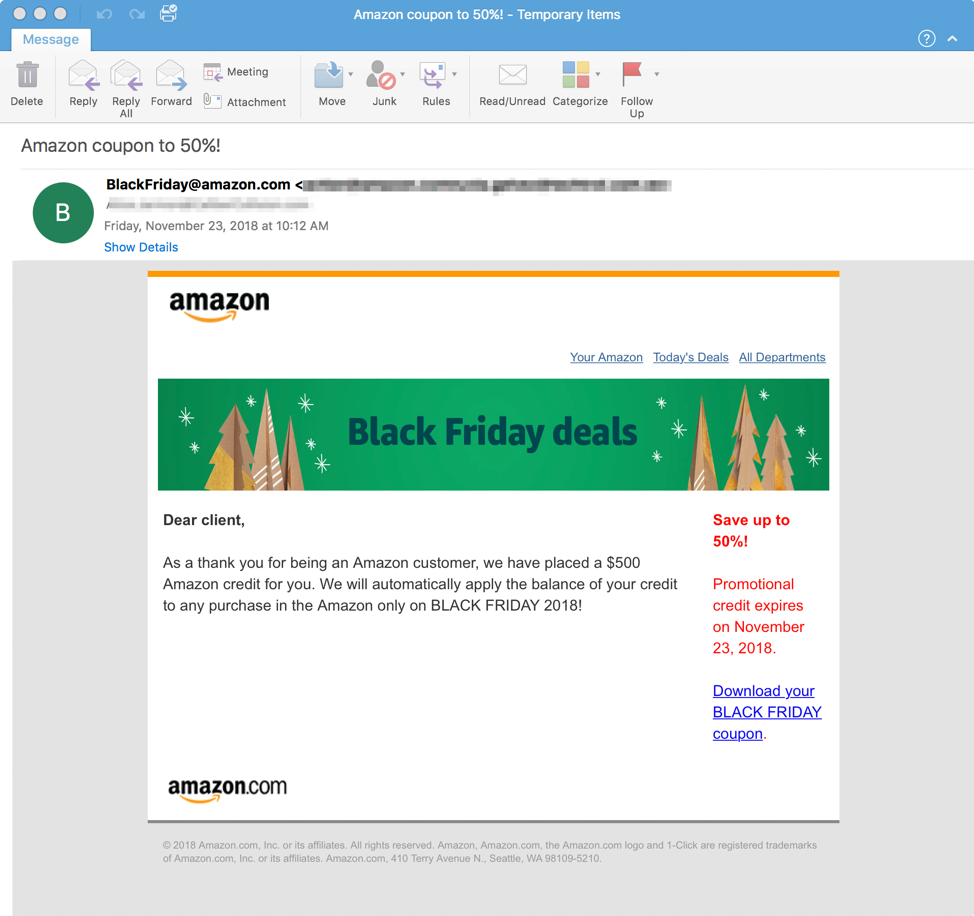
Figure 6: Black Friday-themed Emotet lure using stolen Amazon branding, spoofed sender display name, and a download link leading to a malicious macro-laden document
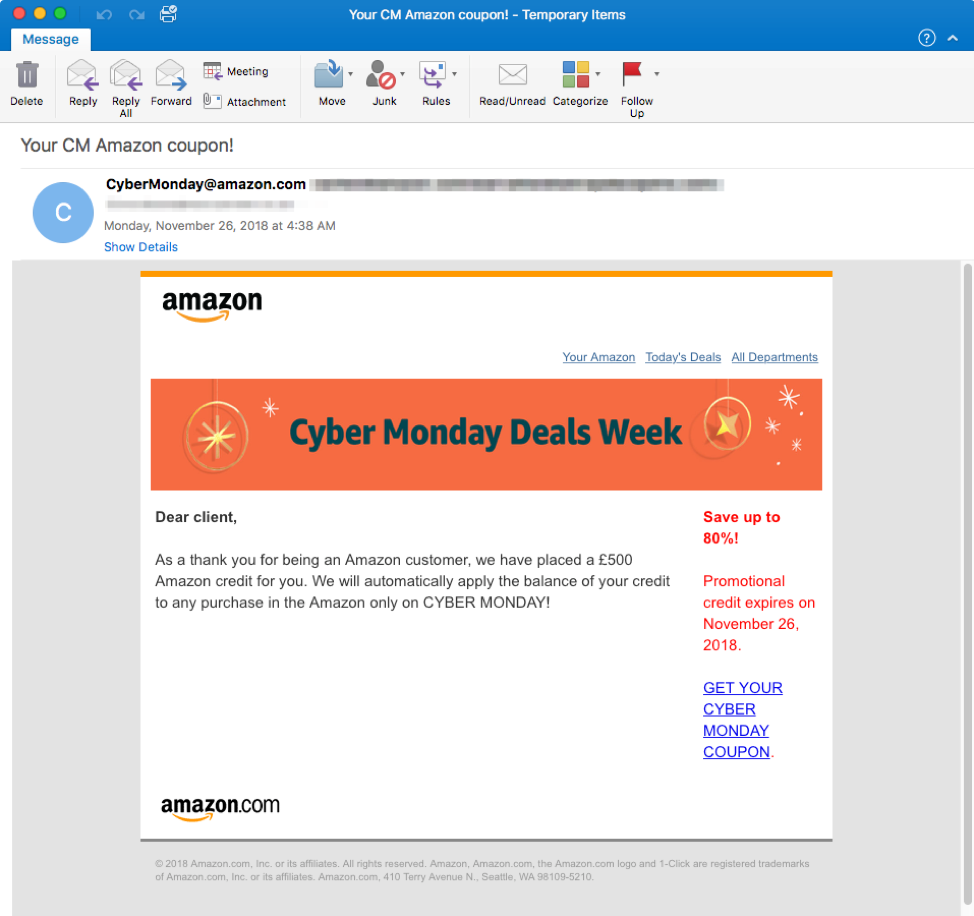
Figure 7: Cyber Monday-themed Emotet lure using stolen Amazon branding, spoofed sender display name, and a download link leading to a malicious macro-laden document. Note that while Black Friday is primarily a US event, Cyber Monday tends to be more international in scope -- In this case, the scam is denominated in British pounds.
While Emotet provides a high-profile and particularly dangerous example of a holiday-themed threat, seasonal lures abound.
Out of office – what’s waiting for you when you come back?
Last year, Proofpoint researchers observed a very large malicious attachment campaign distributed on Thanksgiving Day by the actors behind the massive Dridex and Locky campaigns of the last few years, known as TA505. This particular campaign led to the installation of Scarab ransomware for users who opened the attached documents and enabled content. This was unusual, as established threat actors tend to not send campaigns on major holidays, choosing instead to send them when they know recipients will be in the office. However, we observed similar campaigns around the Christmas holiday, again defying conventional wisdom.
This year, the actor distributing the Emotet banking Trojan sent three large campaigns on Thanksgiving day, Black Friday, and over the weekend, returning to their regular weekday distribution on November 26 with the Cyber Monday lures noted above. TA505 also sent a campaign again this year on Black Friday, as did a number of actors distributing information stealers, RATs, banking Trojans, and more. For unprotected organizations and busy users rapidly making their way through their inboxes after the holiday, malicious messages were ready and waiting, along with a variety of fake Black Friday and Cyber Monday offers.
Conclusion
Although the holidays generally bring a range of online threats from actors looking to take advantage of the “human factor” -- human vulnerabilities of curiosity and fallibility rather than software exploits -- the 2018 holiday season is accompanied by new threats as well as old standbys. Gift card email fraud scams have taken off just in time for the holidays while a larger number of established actors are distributing malware on bank holidays that were relatively quiet in years past. Users should expect these trends to continue across email and social channels this holiday season As always, thorough email hygiene and layers of protection are both critical to avoiding seasonal online threats. As with most things, if offers appear too good to be true or cannot be verified as legitimate email and social media marketing from known brands, recipients should avoid following links and opening files.











