In early 2016, Proofpoint researchers identified a new form of social media-based phishing attack, called angler phishing. The attack technique takes its name from the anglerfish, which uses a glowing lure to entice and attack smaller prey. In an angler phishing attack, a fake customer-support account promises to help customers, but instead attempts to steal credentials. Social media angler phishers create fake customer support accounts that target customers of a wide variety of industries, but we have seen a majority of angler phish attacks focus on customer support accounts for financial services brands.
Proofpoint researchers recently observed an angler fish attack targeting PayPal users that exemplifies this technique. The figures below show examples of angler phishing attempts from two fraudulent PayPal Twitter accounts:
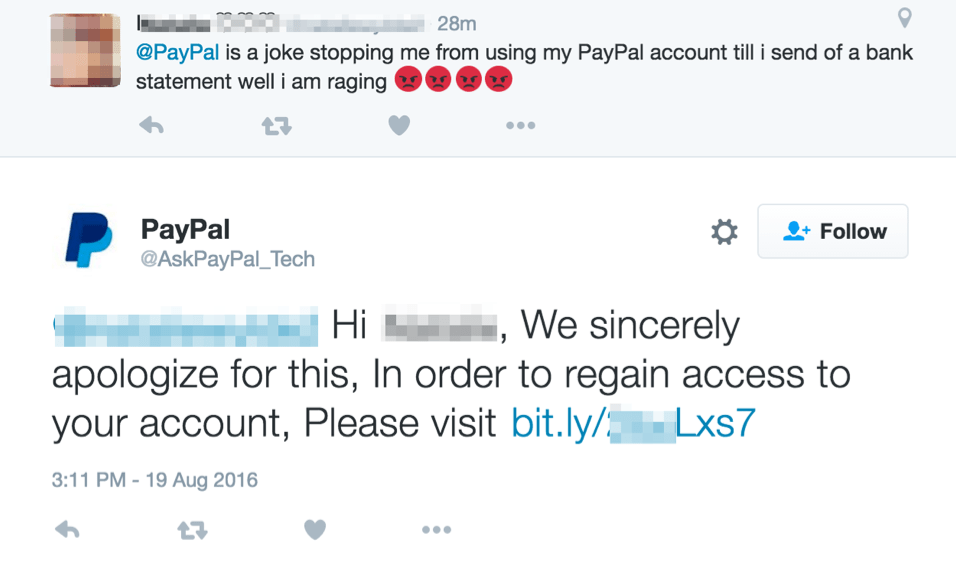
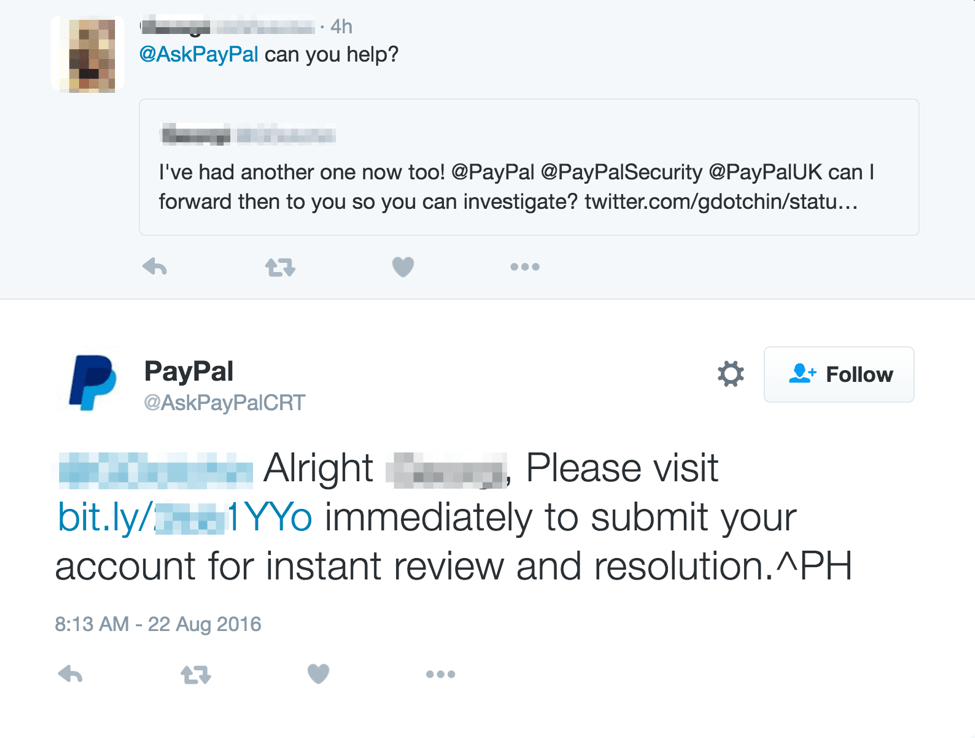
Figure 1: Two examples of an angler phishing attack from two different fraudulent social media customer service accounts
In each of these attempts, the customer is reaching out to the official PayPal Twitter account for support. Since they are mentioning the official PayPal Twitter account through their proper handle, @PayPal, these tweets will show up on the official PayPal Twitter page. From there, the fraudulent PayPal Twitter accounts can monitor for opportunities to target customers that are expecting a response.
The fraudulent PayPal Twitter accounts themselves try to look legitimate. They use the PayPal logo as their account image, and their handle mimics a legitimate support account by adding the word “Ask” to the beginning of the handle. If we visit each of the fraudulent accounts, we also are presented with a page that resembles PayPal’s legitimate Twitter account, thanks to stolen branding:
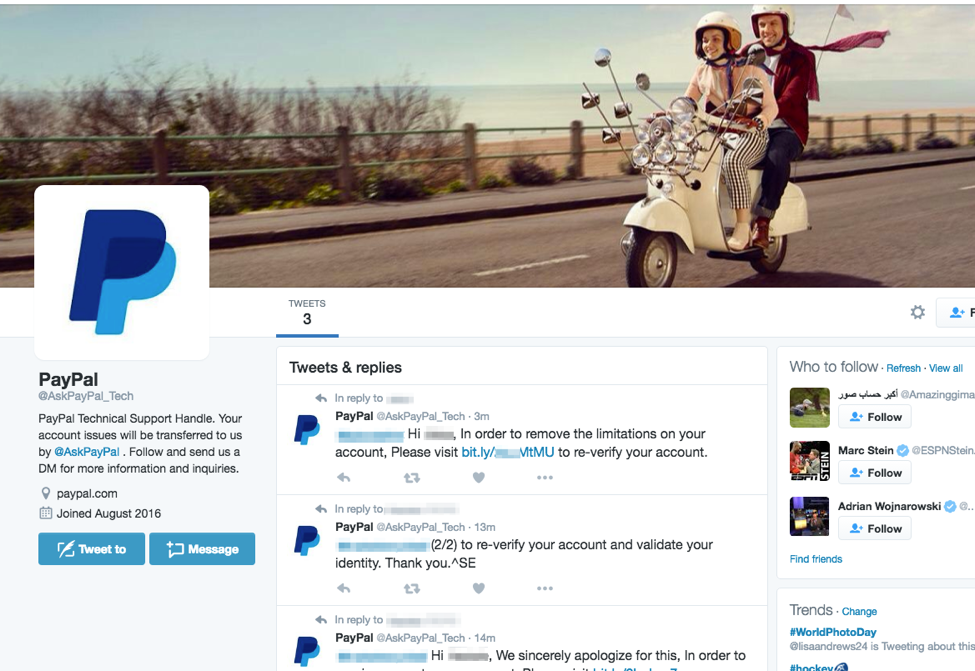
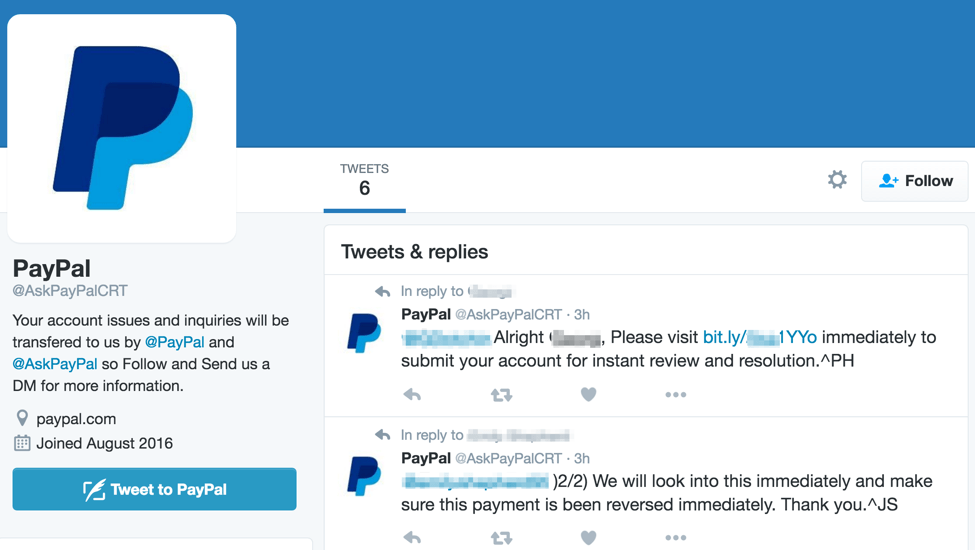
Figure 2: Examples of the main profile page for two fraudulent social media accounts that have reached out to real customers
We can also see that each of these fraudulent accounts have already performed attacks to other customers.
If we visit the links in each of the angler phishing attacks, we are presented with a highly credible login screen. The figure below shows the fake site with stolen branding that is presented when we click on the link given from the AskPayPal_Tech account:
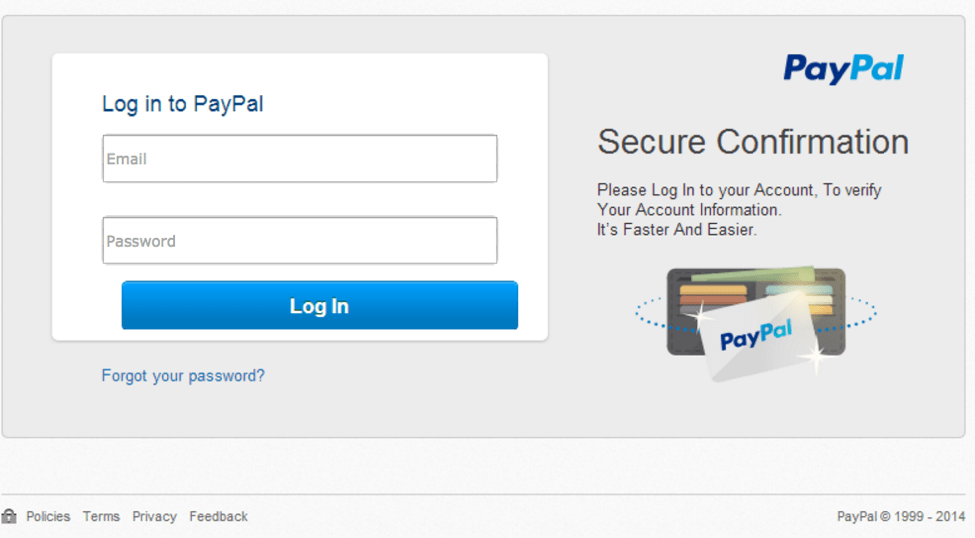
Figure 3: Fake site with stolen branding, which is directed from the angler phishing attack on the AskPayPal_Tech account
And below is the page presented from the AskPayPalCRT account:
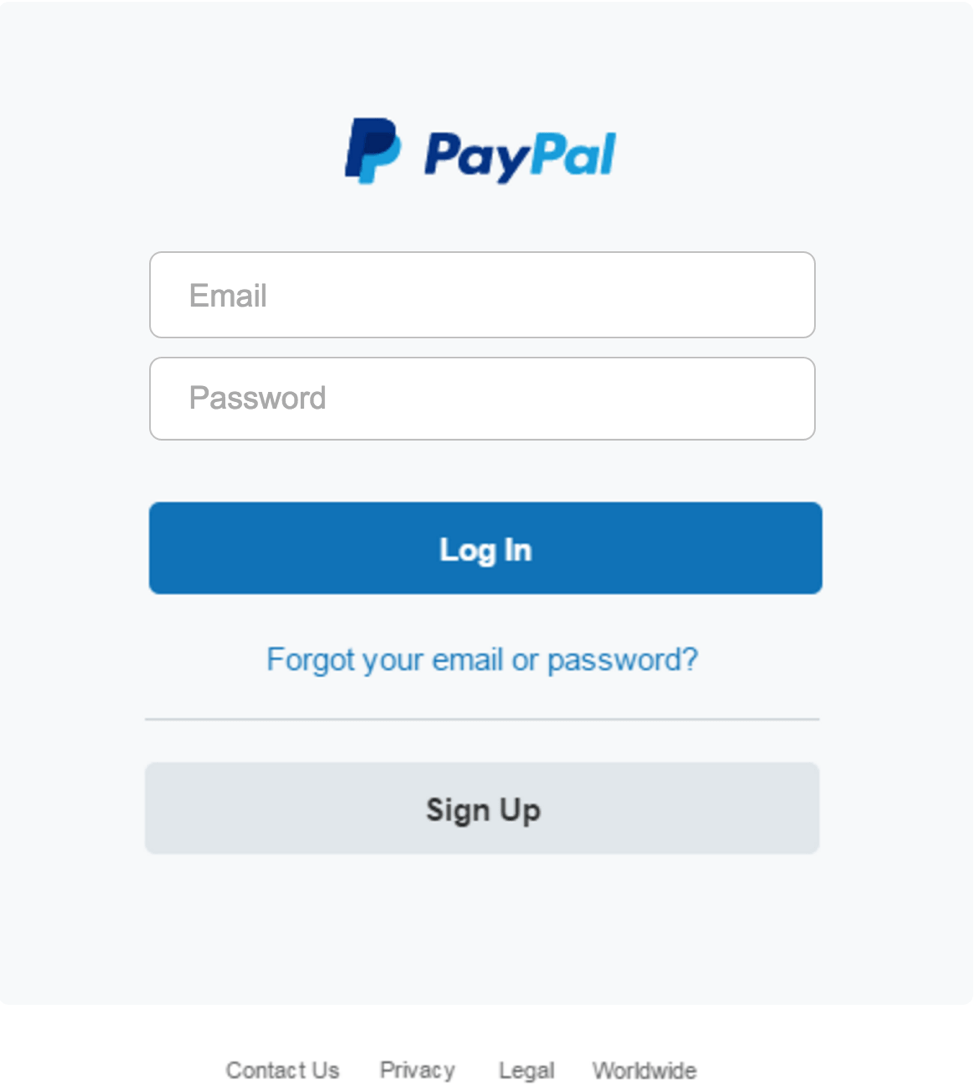
Figure 4: Credential phishing page with stolen branding, which is directed from the angler phishing attack on the AskPayPalCRT account
In both of these cases, the fraudulent but realistic Twitter handle, landing page, and login screen create a convincing lure that can entice users to enter their PayPal credentials into the fraudulent page, providing scammers direct access to their accounts and any funds in them.
PayPal is aware of the issue and is working with Twitter to resolve it.
Conclusion
This recent scam exemplifies the many angler-phishing attacks that we have been seeing. Recent research from the Anti-Phishing Working Group (APWG) reports that over 75% of attacks are targeted at financial service and ecommerce organizations, and Proofpoint’s own research on angler-phishing confirms this. Vigilant social media monitoring and account discovery exercises are effective measures for detecting and preventing social media angler phishing attacks. Proofpoint research shows that most phishing attacks take advantage of non-business hours, and so organizations should consider augmenting manual discovery processes with automated account discovery.
Subscribe to the Proofpoint Blog

