Last September, Proofpoint held our first in-person event since the pandemic in New York City, Protect 2023. In this blog post, our Chief Compliance Officer in Residence John Pepe shares some key insights from the leaders who participated in the Compliance Leader’s Roundtable at that conference. A big part of that discussion was exploring how combining data points from multiple tools can help stop known risk patterns before problems escalate.
“Break the Attack Chain” is a Proofpoint initiative that outlines our approach to prevent and disrupt cyberattacks that target people and their data. The attack chain can basically be broken down into eight steps and three main stages:
- Initial compromise
- Privilege escalation
- Data exfiltration
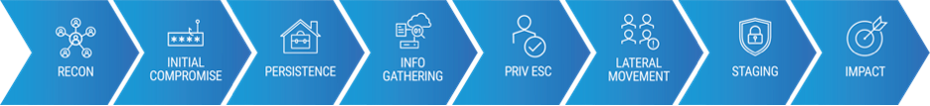
Steps in the attack chain.
We believe that breaking the attack chain is so important that we made it the theme of Protect 2023. When you break the attack chain, you reduce the risks and the impact of cyberattacks. And you avoid a lot of the financial, reputational and operational damage. Proofpoint argues that this starts by taking a people-centric approach to security that focuses on the human factors that enable and motivate attackers.
But this theme isn’t just relevant to cybersecurity. It’s also an important concept that’s relevant to compliance professionals and their current challenges. Recently at the Protect 2023 conference, we explored how the industry is using this idea to rethink the ways it approaches and mitigates risk.
What’s top of mind for compliance professionals right now?
Part of my job at Proofpoint is to provide our customers—some of whom are highly regulated—with executive briefings on compliance and regulatory best practices. I also have a lot of critical discussions with the legal and regulatory communities. So I understand why the concept of breaking the attack chain transcends cybersecurity and really resonates with these groups. That’s why I chose to explore it at Protect 2023 at the Compliance Leader’s Roundtable.
This panel was comprised of a chief compliance officer from a leading financial services provider, the head of surveillance for an asset manager, and a chief information security officer. And our topic was “What’s Top of Mind for Compliance Professionals Post COVID-19."
The discussion was informal and focused on work-from-home (WFH) initiatives during and after the pandemic. Two interconnected areas were of particular interest:
- Risks and programs related to WFH, with a special focus on collaboration platforms
- How behavioral indicators may help to predict potential legal or compliance issues
When talking about insider risks and threats, the panelists explored:
- Best practices for controlling messaging apps and mitigating risks in mobile texts and chat
- How behavioral modeling and analytics can be used to enhance risk monitoring for user conduct
- How combining multiple compliance approaches can help form a holistic risk management program, which can mean integrating:
- Threat detection
- People analytics
- Conduct compliance applications
As part of the conversation, I brought up the topic of employee behaviors and patterns that can lead to legal or compliance issues. The example scenario I offered was of a disgruntled employee who had received an underwhelming bonus or was passed up for a promotion. To get back at the company, this person stole sensitive company data and intellectual property (IP) before they left their job. The panel discussed behaviors or telemetry that might be present in such a scenario. And they talked about whether any data about user conduct might help detect and prevent potential losses.
An integrated approach to breaking the attack chain
What follows are some of the ways that our panelists use tools to mitigate risks. And how Proofpoint can help.
Combining internal and external data
One of the most crucial aspects of a surveillance analyst’s job, especially in financial services, is monitoring employee risk. The roundtable emphasized how important this is. When analysts can catch issues early, they can stop potential legal or compliance issues before they escalate.
To that end, analysts should think about combining tools to help create a complete picture of employee behavior. This can help them to identify patterns that may indicate a problem. It’s a good idea to combine tools that:
- Monitor employee communications. Emails, instant messages and other electronic communications can hold clues to potential issues with an employee or their business conduct.
- Monitor insider risks. Unusual activities, like accessing sensitive data outside of normal business hours, may indicate a threat.
- Monitor trading and transactions. This can help you find employees who are manipulating the market or conducting other illegal activities.
- Analyze employee behavior. If you analyze performance and behavior, it can help to reveal issues before they become major problems.
Proofpoint people-centric analytics provides you with insights into employee behavior and helps you identify risks.
Most of the tools available to compliance analysts today use only one of the above techniques to monitor conduct and insider risk. And few tools can integrate communications and transactions.
However, Proofpoint offers solutions for:
- Data loss prevention (DLP)
- Communications conduct, including transaction correlation
- People analytics
- Insider risk detection
Customers have told us that they have started to use these solutions together as a unified, integrated risk system.
Our panelists said that they use individual tools. But they realized that by using tools together as an integrated risk system, they can better create a comprehensive picture of employee behavior and identify potential issues. The insights they gain can help them to stop a chain of events before it leads to a legal or compliance problem.
Using an integrated risk approach
To illustrate how an integrated risk approach would work, let’s revisit the earlier example of the disgruntled employee. We know that not long before this hypothetical employee left the company, they received an underwhelming bonus, or they were passed up for a promotion. Now, what if we could have broken the chain of events and prevented the data exfiltration? What would that look like?
Using people analytics techniques, a business could manually or automatically record to a person’s profile when an adverse human resource event occurs. In an “integrated” compliance system, this event would contribute to a theoretical “risk score.”
The score would invite heightened supervision of the employee for a certain time period. And during that time, events from other monitoring systems that would normally be “below the line” of issue detection would now be over the threshold because of the elevated risk score.
For instance, when a normally innocuous DLP (data loss prevention) alert is triggered—for example, by a Microsoft Excel file being sent to a personal email address—the analyst would then scan alerts from other systems. The analyst might notice that the employee has been:
- Sending resumes from their corporate email address
- Expressing their dissatisfaction with their job or supervisor in electronic communications
- Accessing job boards via the corporate network
Taken together, these behaviors would suggest that this employee is a “flight risk.” The analyst would then monitor the employee’s activity and intervene when and if they download sensitive files.
Harnessing predictive analytics
What if you could use the data insights that an integrated risk system collects to spot repeated patterns that resulted in legal or compliance issues in the past?
Here’s an example: Let’s say that there are a certain number of behavioral elements that, when taken together, have a high likelihood of developing into a previously identified concern. When legal, compliance and cybersecurity teams combine data, past cases and predictive analytics, they can intercede when enough behavioral elements are triggered to cross a statistical risk threshold.
This surveillance may seem like science fiction. (The technology discussed in the 2002 film “Minority Report”—where law enforcement can predict crimes before they happen—comes to mind.) But it’s not. When you combine electronic communications monitoring, insider risk monitoring, transaction monitoring and people analytics, you can create a comprehensive picture of employee behavior. You can then use data analysis and predictive modeling to identify potential issues before they become major legal or compliance problems.
Learn more
Proofpoint solutions aim to stop bad actors at each stage in the cyberattack chain. We can help you take an integrated approach to breaking the legal and compliance attack chain. Proofpoint solutions use artificial intelligence (AI) and machine learning (ML) to:
- Detect and block threats
- Identify and protect compromised accounts
- Prevent data loss and theft
Want to design your own integrated risk approach? Contact the Proofpoint compliance team by emailing compliance@proofpoint.com.
You can also visit our Intelligent Compliance page to learn more about solutions you can use to break the legal and compliance risk attack chain.











