In this blog series we cover how to improve your company’s security posture with actionable insights. Actionable insights are a critical tool to help you improve your security posture and stop initial compromise in the attack chain. You can use them to identify and respond to potential risks, enhance your incident response capabilities, and make more informed security decisions.
The Proofpoint Threat Protection Platform uses data, detection and research to provide actionable insights for a complete picture of the threats your organization faces—and the best ways to defend against them.
In earlier blog posts, we’ve focused on actionable insights and what you can do to enhance your security posture. We’ve covered people risk, origin risk and business email compromise (BEC) risk. And we’ve explored why ensuring proper context is critical for your insights.
In this post, we discuss the value of efficacy reporting—measuring how well your security controls stop threats—in assessing your risk.
Reduce risk by analyzing efficacy
As the name implies, efficacy reporting helps you understand how effective your security measures are so that you can better protect your organization. These reports show you what’s working well—and areas to improve. They can also recommend ways to strengthen your organization’s security posture.
Transform your approach to email security with actionable insights
Using actionable insights to assess your cybersecurity measures is key to protecting against potential threats. The Proofpoint Targeted Attack Protection (TAP) Threat Insight Dashboard can help with this process. The dashboard provides valuable information about the effectiveness of your email security measures.
Insights
Effectiveness reports in the Proofpoint TAP Threat Insight Dashboard provide a wealth of insights. For example, the “Messages Protected” report shown in Figure 1 shows two critical metrics:
- How many threats were detected and blocked
- How many threats reached their targets
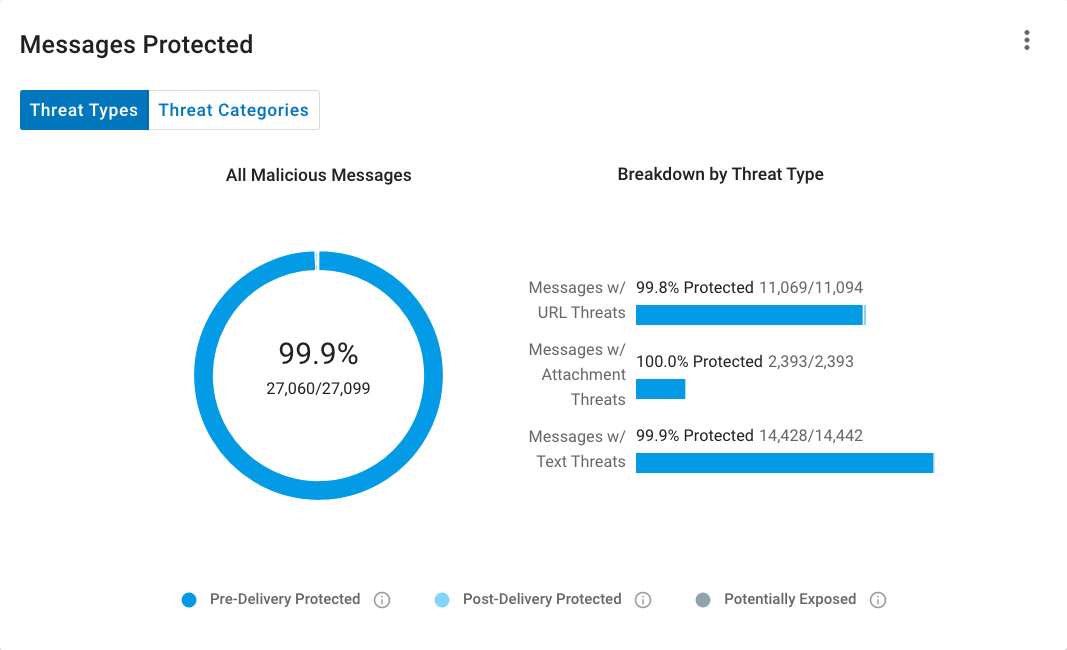
Figure 1. Messages Protected report in the Proofpoint TAP Threat Insight Dashboard.
Toggling between the “Threat Type” and “Threat Category” charts gives you even more insight. You can see how well your security measures work against various kinds of threats and specific areas to improve.
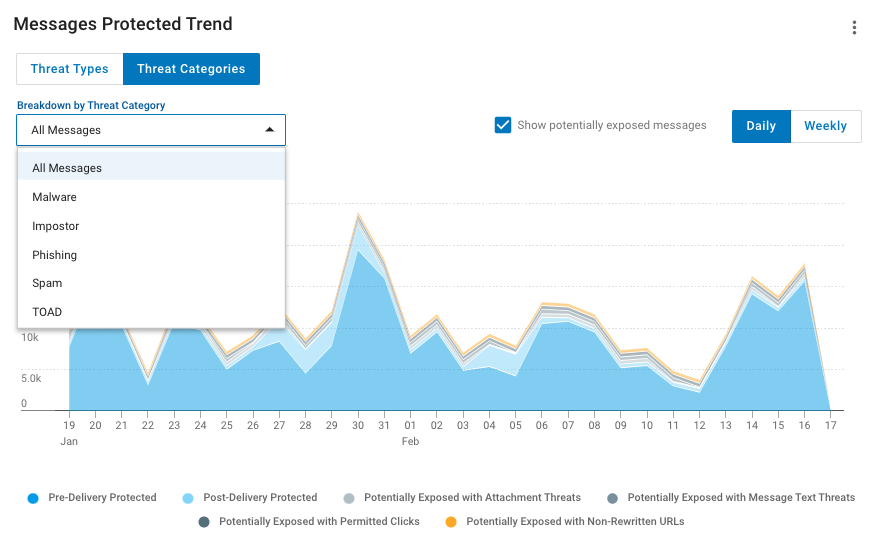
Figure 2. Messages Protected Trend report in the Proofpoint TAP Threat Insight Dashboard.
Meanwhile, the “Messages Protected Trend” report (Figure 2) provides insights into trends over time to show how your email protection measures are evolving and improving. It shows:
- The number of messages protected by security controls within a given time period
- The percentage of total messages protected
This report can help you prioritize security efforts and allocate finite resources.
Targeted controls
A key feature of the Proofpoint TAP Threat Insight Dashboard is the ability to focus on specific controls and assess how they might affect your performance. It can be especially useful if you’re trying to fine-tune your cybersecurity measures or find areas that need more attention.
Here are some examples of actions you can take with targeted controls:
- Email filtering: Effectiveness reports can help you see how well your email filtering controls block spam and phishing. If a high number of these threat types are getting through, you may want to adjust your email filtering settings or consider more layers of protection.
- Endpoint protection: The dashboard can help you understand how well your endpoint controls prevent malware infections. If you see a high number of infections, consider strengthening your endpoint protection, such as updating more often or adding security tools.
- Network security: Effectiveness reports can help assess network security controls. For example, you can see how well your firewalls and intrusion prevention systems are working to block threats. If a high number are getting through, consider fortifying your network security.
- User education: Beyond technical controls, user education can be an important part of your security strategy. Effectiveness reports can help you understand how well your user education efforts are working and reveal areas where people may need more training.
By targeting specific controls and acting on insights from the Proofpoint TAP Threat Insight Dashboard, you can refine your cybersecurity measures to better protect your organization.
Summing up
Efficacy reports will yield insights that can help you:
- Assess the effectiveness of your security measures: You can see how well your security measures are working to protect your organization from threats and take a more targeted approach to improving your security.
- Identify areas for improvement: Efficacy reports can help you see which security measures are performing well—or not. This insight can be especially useful if too many threats getting through or you’re facing a wave of successful attacks.
- Make informed decisions: Efficacy reports can help you better allocate resources and prioritize security efforts. That, in turn, can help you better protect your organization and minimize the impact of any successful attacks.
- Benchmark your performance: Efficacy reports will also help benchmark your performance against industry standards and your own past performance. That insight will give you a sense of how well you’re doing compared with peers and help you identify areas where you may need to improve.
Learn more about your organization’s specific risks
If you’d like help finding and understanding the biggest digital threats to your business, reach out for a free Rapid Risk Assessment. One of our security experts can help you identify some of the biggest digital threats your organization faces—including domain risk—and show you how to mitigate them.
Learn more about the TAP Threat Insights Dashboard and Actionable Insights from Proofpoint here.











