We all know that the internet can be a strange place at the best of times, so it should come as no surprise the world’s cybercriminals contribute their fair share of strangeness. But in the past few weeks our researchers have encountered a handful of malicious campaigns that go way beyond the usual level of bizarre with the phishing lures they used to achieve their social engineering aims.
Tickets to Mars
Just a few years ago, space tourism was making big headlines. It seemed like the age of orbital jaunts was just around the corner, and that NASA would be building moon bases before long. Sadly, there have been setbacks, and for now space remains the preserve of astronauts, scientists and the very rich. But following the “go big or go home” principle, a recent malicious email campaign didn’t just stop at sub-orbital spaceflight or visits to the moon, promising recipients the chance to win a trip to Mars.
With a subject line of “You win a trip to Mars,” the messages contained a PDF featuring an image of a recent Elon Musk biography and a spoofed update dialog for Adobe Reader. The download button on the fake image linked to a tar.gz file containing an executable that ultimately downloaded Redline stealer.
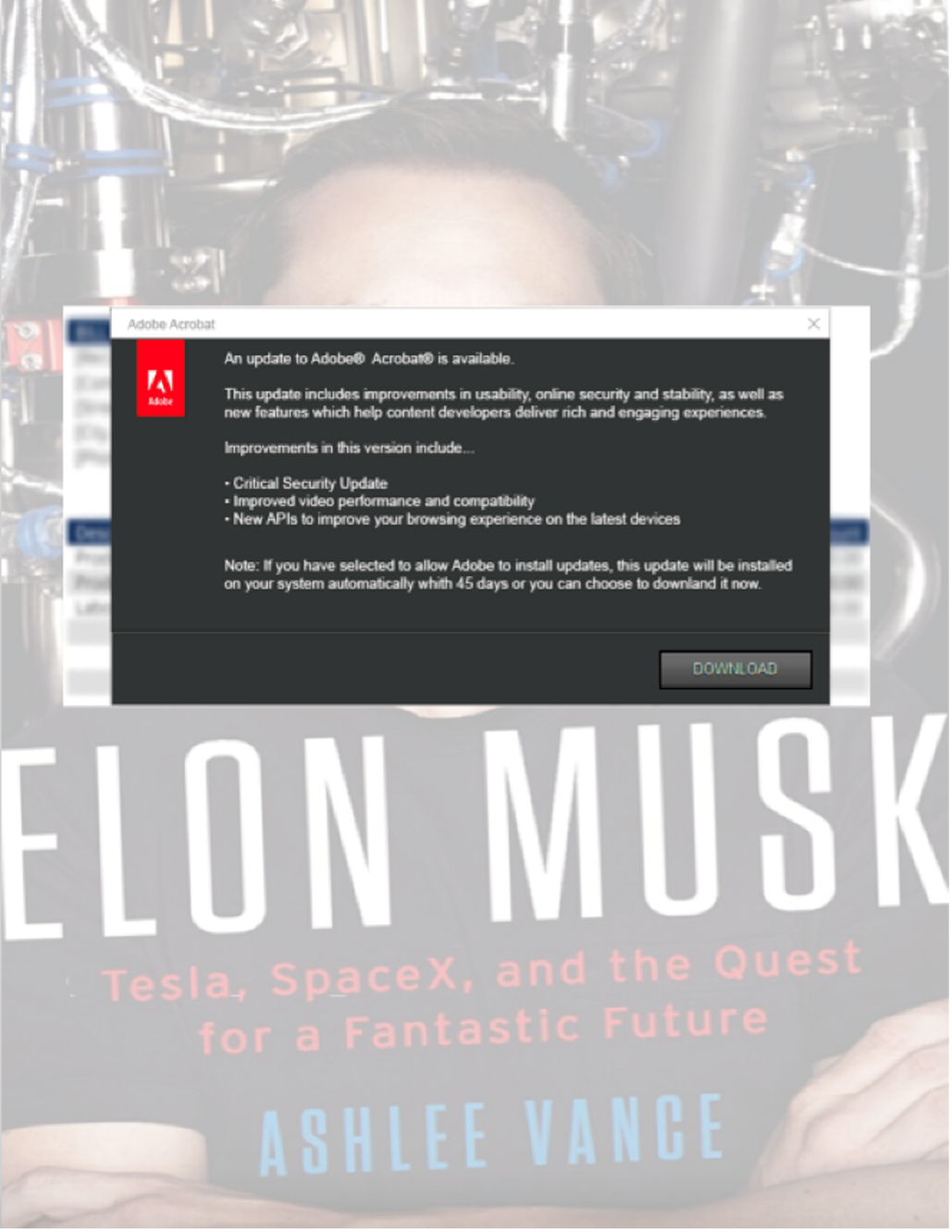
The timing of this campaign is interesting, as native support of this file type in Windows 11 only began in October 2023.
Occasionally threat actors come up with phishing lures so improbable that it’s hard to imagine anyone falling for them. But there is a method in their madness. For some recipients, curiosity alone will be an effective phishing lure. After all, social engineering is about getting your victim to do what you want—in this case, clicking a download link. And you don’t have to believe that you’re really going to win a trip to Mars to be interested in finding out why you’re being offered one.
Rude customer service
We all have bad days, but social media has turned customer complaints into a spectator sport. In this low-volume campaign, an unattributed threat actor distributed phishing lures disguised as messages purporting to be from irate customers called either “Daniel Rodriguez” or “Emma Grace.” Daniel and Emma were so angry about the service they received that they didn’t just send an email to complain—they appeared to have put even more extensive thoughts down in an attachment called “Attitude_reports.svg.”
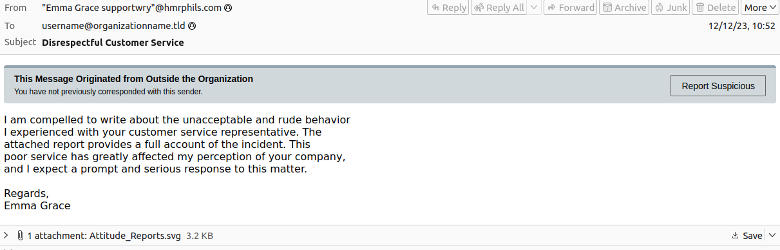
Oddly, SVG is the file extension for Scalable Vector Graphics—an unusual file type in which to jot your thoughts about a disrespectful employee. But if the recipient was conscientious enough to download the attachment, trouble ensued.
The SVG opened in a browser, initiating a complex infection chain leading to the Phemedrone stealer malware. The attack chain was notable for its use of CVE-2023-38831, as well as being an example of the growing use of SVG files in the post-macro landscape.
From Ukraine to Uzbekistan
The conflict between Russia and Ukraine has caused turmoil throughout the region, and even the world’s cybercriminals have been affected. In a recent campaign, our researchers noticed an attacker trying to use the difficulty of sourcing products in Ukraine as a phishing lure to target potential victims throughout Europe on behalf of their partners in Uzbekistan.
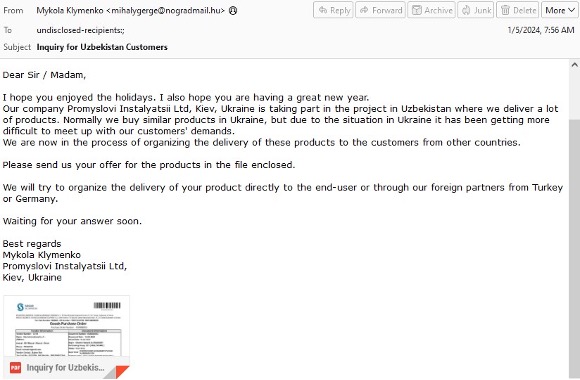
The messages contained a hyperlinked image spoofing a PDF attachment. Victims clicking on the image were directed to a MediaFire URL triggering an infection chain eventually leading to AgentTesla.
For more insights from our threat researchers, subscribe to the Discarded podcast, and be sure to check out our regular Cybersecurity Stop of the Month, Threat Insights blog and our weekly Threat Hub updates.











