With more employees working remotely, cyber criminals are relying even more heavily on social engineering through email to carry out their attacks. It’s a logical strategy. As the 2021 Verizon Data Breach Investigations Report (DBIR) notes, email is the number one threat vector due to its prevalence and popularity—and 85% of breaches involve human error.
And it would seem that attackers are finding little resistance in their quest to reach their targets: Separate research from Gartner Information Security finds that organizations are devoting just 10% of their security spending to the email threat vector.
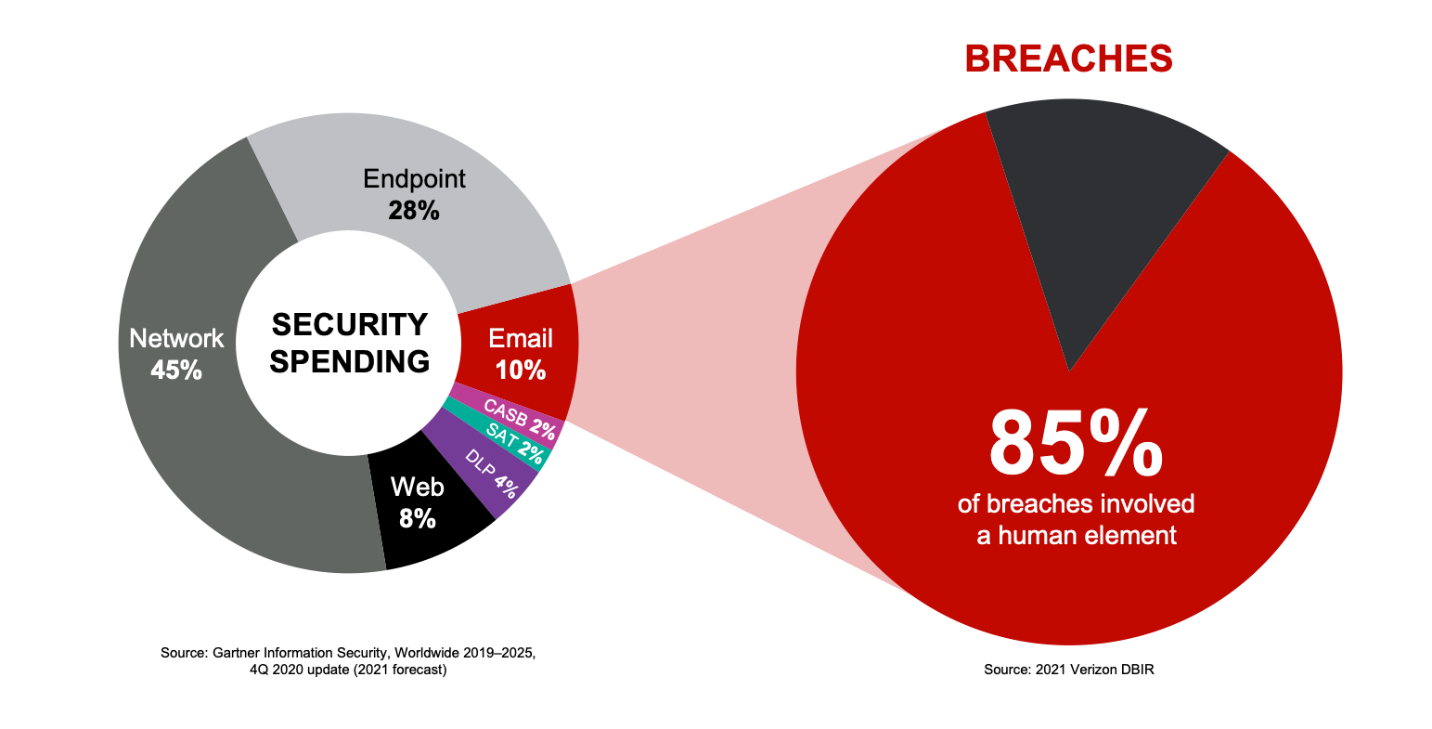
Figure 1. Research from the 2021 Verizon DBIR shows 85% of breaches involve a human element, mostly from email, while separate research from Gartner Information Security shows only 10% of security spending is focused on this critical threat vector
Other research helps to underscore why organizations need to focus more attention on the email threat vector:
- The cost of phishing has nearly quadrupled to almost $15 million annually for organizations, or $1,500 per employee, according to research by Ponemon Institute
- The Anti-Phishing Working Group estimates that phishing attacks doubled in 2020
- Coveware reports that over 50% of ransomware originates from email phishing
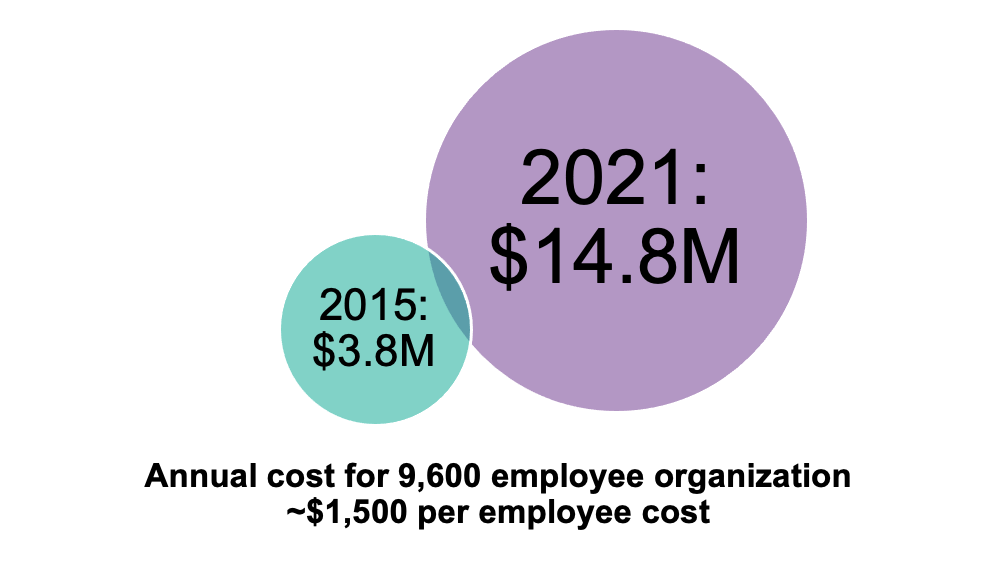
Figure 2. The annual cost of phishing (Source: Ponemon Institute)
Layers of defense make all the difference (and your people do, too)
There’s no silver bullet to stop phishing attacks, which are becoming increasingly more complex and targeted in their approach. And while it’s essential to detect and block threats, these measures alone aren’t enough to create a strong email security posture.
Fully protecting your organization against threats like phishing requires more than one layer of defense. Figure 3 shows the key elements of the layered approach Proofpoint recommends:
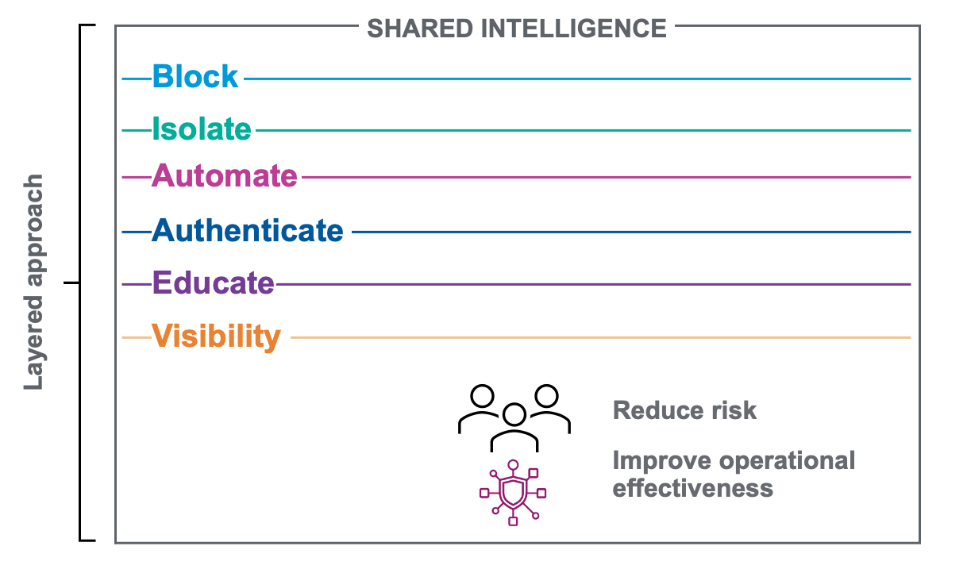
Figure 3. Proofpoint recommends a layered approach to reduce risk and improve operational effectiveness against email and cloud threats
This blog post is the first in a series in which we’ll focus primarily on two critical layers of defense: education and automation (of reported emails).
You need to educate your employees to build their awareness of threats. But to help protect the organization, your employees must also be able to act when they encounter threats. Making it easy for them to report phishing attacks is a prime example—provided that it doesn’t end up overburdening your IT team. That’s where automation comes in.
By educating your users and automating the remediation of reported threats, you can reduce your risk of attack, improve operational effectiveness and build a culture of security awareness in you organization. Ultimately, you can achieve people-centric security, where you are protecting your people, and your people are protecting your organization.
Assessing current behavior and mapping a road to improvement
When looking at user behavior across our customer base, we were surprised by how many organizations reported low phishing simulation reporting rates, with the bottom 25th percentile just having 1.4% of simulations reported by users. This blog series will dive into interesting data like this and also address the following questions:
- How good are users at reporting phishing simulations?
- What kinds of real messages are users reporting to IT security teams?
- How are IT security teams handling these messages?
- What next steps should IT security teams take to improve their organization’s email security posture?
To help answer those questions, we’ll use metrics based on data from the millions of people who use our PhishAlarm email reporting button to report suspicious email messages and our Nexus Threat Graph, which powers our detection stack to determine what type of messages users are reporting.
Stay tuned for our next installment, which we’ll publish soon!











