Proofpoint and CrowdStrike are excited to celebrate our two-year anniversary of working together to provide security solutions to our joint customers. A lot has changed over the last two years, especially around remote work and the types of threats we see attacking people more directly.
Our joint solutions are protecting more than 6.5 million end-users across 400+ joint customers. In the last 14 months, Proofpoint has also added over 103k+ indicators for compromise (IOCs)—file hashes of malicious files previously unknown to CrowdStrike—to custom intelligence at joint customers to help them better protect their endpoints.
The first three Proofpoint and CrowdStrike integrations covered multiple aspects of protection, and you can learn more about them here:
- Post-delivery automated remediation
- Predelivery protection for external email
- Enhanced zero trust security
What's New: Mitigating Risk of Malware Distribution via Internal Email
Now, Proofpoint and CrowdStrike can address an important security gap with an innovative integration: predelivery protection for internal email.
Cyber attackers can use compromised email accounts to laterally spread malware within an organization by taking advantage of the trust between internal users. The Internal Mail Defense solution from Proofpoint reduces this risk by stopping malicious internal-to-internal emails from end-user inboxes.
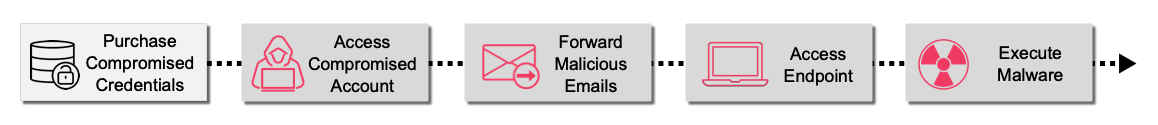 Figure 1. Attack chain: lateral movement of malware via internal mail
Figure 1. Attack chain: lateral movement of malware via internal mail
The Internal Mail Defense enterprise solution sandboxes (via Proofpoint Targeted Attack Protection) any unknown attachment in an internal-to-internal email to mitigate risk of malicious attachments sent from compromised accounts. Our joint customers with CrowdStrike (licensed for Falcon X, CrowdStrike’s threat intelligence) now get the added benefit of ensuring they can mitigate risk from attachments that CrowdStrike has identified as malicious.
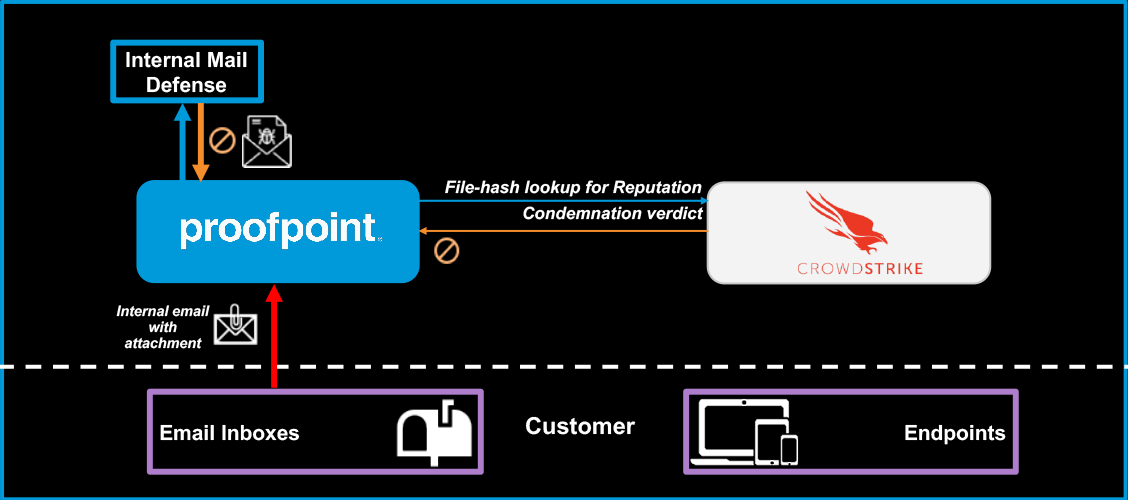
Figure 2. Pre-delivery protection for internal mail
Multi-layered Protection with CrowdStrike
Your people remain the top target for attackers, which is why it’s essential to implement multi-layered defenses to stop targeted attacks. Our partnership with CrowdStrike enables automation of threat intelligence sharing with triggered actions within our respective market-leading product platforms to reduce overall risk for our joint customers.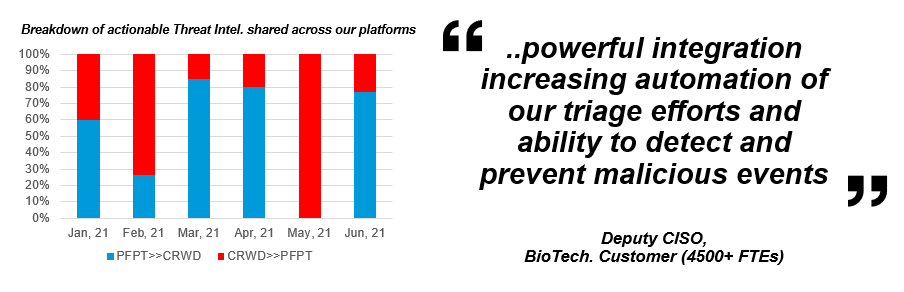
Figure 3. Proofpoint and CrowdStrike threat intelligence breakdown
While no single vendor can provide best-in-class solutions for all your security challenges, it’s incumbent on leaders like Proofpoint and CrowdStrike to collaborate to help transform your security programs. The graph above is a testimony to how our threat intelligence sharing is helping to advance threat protection and remediation across email and endpoints.
Please reach out to recommend security challenges that collaboration between Proofpoint and CrowdStrike might help to solve. Meanwhile, to learn more about this new offering and our other CrowdStrike integrations, visit our partner webpage.
You can also join us at fal.con CrowdStrike cybersecurity virtual conference, from Oct. 12-14, 2021.











