Remote work, easy access to more data and tools, and high employee turnover are increasing the risk of data loss and insider threats. Nearly two-thirds (63%) of CISOs report that their business has experienced sensitive data loss within the past 12 months. Meanwhile, insider threats have jumped by 44% in the past several years.
These dynamics create challenges for security teams that are responsible for identifying—and preventing—risky behavior to minimize damage. After all, data doesn’t lose itself; people lose it. And that’s why people need to be at the center of a modern information protection strategy.
The challenge with information protection, unlike other security controls, is that it directly impacts the end user. Thus, security teams try to implement security controls and monitor users without compromising their experience or slowing down the performance. Here is a look at how they can do that.
Not all users are the same
Every business has insiders—people with authorized access to the company’s systems, networks and data. In other words, insiders are people whom the business trusts.
Even though they have access to sensitive information, not all insiders are threats. Only those people who are careless or who abuse their position of trust are considered insider threats.
This is an important distinction to keep in mind when determining which users to monitor. Instead of collecting endpoint telemetry for all activities for all users all the time, security teams can narrow their focus on getting insights into the riskiest users all the time, and insights into low-risk users some of the time.
Most users are low-risk, everyday users. They represent about 90% of the user population. Given their low risk, it is sufficient to monitor only the data movement associated with these users—the “what,” “where” and “when” of the data they access and use. When a user violates corporate policy, this activity is captured for the security team to review.
Risky users comprise about 10% of the user population. These users include departing employees, privileged users, third-party contractors and Very Attacked People™ (VAPs). Given the greater risk that these users pose to the business, they require monitoring that goes beyond data activity to include user behavior. Screenshots of risky behavior can be captured to provide context and forensic evidence for investigations.
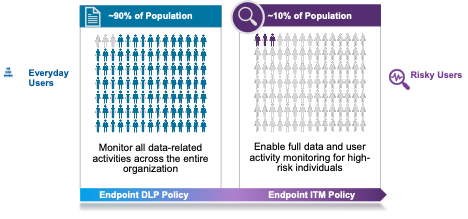
Proofpoint Endpoint DLP can monitor everyday users and risky users.
Monitor everyday users and risky users with a single endpoint agent
Proofpoint offers a combined data loss and insider threat solution. This allows security teams to install a single lightweight endpoint agent with a dual purpose—to monitor everyday users and risky users.
The benefit of using a single agent is to preserve both the user experience and productivity. Because the endpoint agent runs in user mode, it minimizes conflicts with other agents. As a result, users won’t notice it, and system performance won’t be compromised.
Security teams can seamlessly switch a user’s monitoring policy from everyday user to risky user, and back again, as circumstances change.
For everyday users, data activity is captured. Examples of monitored activity may include copying a file to a USB, printing sensitive documents and uploading to cloud sync.
For risky users, data activity and user behavior are both monitored. This may include application use, web browsing, security controls tampering and the use of unauthorized software. Both metadata and screenshots are captured as well. That provides forensic evidence for investigations that involve cross-functional groups such as human resources and legal.
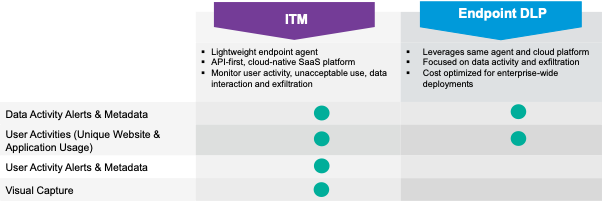
Comparing Proofpoint ITM and Endpoint DLP capabilities.
A departing employee is an example of an everyday user who may become a risky user. After an employee gives notice, they may start preparing for their next opportunity. The employee may plan to take sensitive data with them when they leave, either because they feel entitled to it or because they think it’ll give them a head start at their next job.
While the departing employee may have been monitored as a low-risk, everyday user before, they are now considered risky and monitored more closely with screenshots being captured.
A global hospitality company increases visibility while saving money
A departing employee was the exact use case that prompted a global hospitality company to use the converged Endpoint DLP and Insider Threat Management (ITM) solution from Proofpoint. As a result, the company increased visibility into the activities of its everyday users and risky users. It also saved money by using a converged solution.
The company had been using Proofpoint ITM on a small number of risky users for several years. It had a defined list of use cases for endpoint DLP and ITM. The business was grappling with growing employee turnover and increased remote work, so it wanted to expand its monitoring capabilities. However, it lacked budget.
The ability to monitor both everyday users and risky users provided the company with the visibility and flexibility it wanted—without the need for two separate agents. The business now monitors 18,000 users with Proofpoint Endpoint DLP and a small subset with ITM. The flexibility of the dual agent lets the company dynamically apply the risky user policy as needed.
Visibility and efficiency with a unified console
Proofpoint Endpoint DLP and ITM are part of Proofpoint Sigma. This information protection platform helps companies prevent data loss, investigate insiders and block cloud threats. It also provides a unified console. So whether alerts are generated from endpoint, email, cloud or web activity, security teams can view and investigate them with the unified alert manager. No more pivoting from tool to tool.
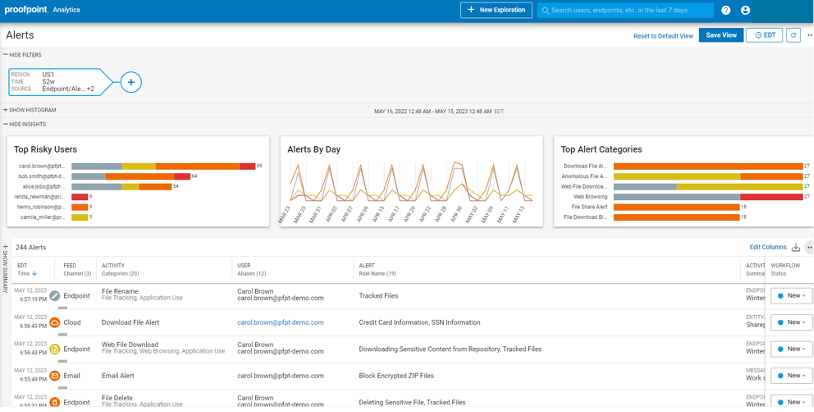
Security analysts can triage alerts in a centralized dashboard.
Learn more
Get more details about Proofpoint Endpoint DLP and ITM.
Find out more about the Proofpoint Sigma information protection platform.











