Back in the day, when a CIO or CISO wanted to lock corporate data down, they could simply say, “no.” If the business didn’t trust USB devices, which can be malware-ridden or used to exfiltrate sensitive data, it could forbid them. Companies would either block certain files from reaching USB or block USB usage completely (often by blocking the ports themselves).
Of course, this never worked perfectly, and today it’s unrealistic (if not impossible) to employ this strategy. For one, BYOD is very common today, so you can’t simply block ports on all hardware. Beyond this, nearly everyone works with sensitive data today—not just IT administrators or executives—so data exfiltration is inherently a larger and more complex problem than it once was. Finally, employees must collaborate more than ever, and those who travel for work cannot always count on a strong internet connection, so USB device usage can be very helpful to transport files.
These are just a few examples of why simply blocking use of removable media is not viable today. It makes more sense to seek visibility and context into user activity than to outright prohibit certain devices or behaviors in today’s complex landscape. Doing so will enable a more proactive security posture and thus decrease instances of actual data exfiltration.
We recently announced the launch of Proofpoint ITM 7.7, which brings immediate context and deeper visibility to potential data exfiltration through USB devices and other removable media. Our correlation of user and data activity within an easy to understand and searchable timeline of events enables teams across the business—from human resources to legal—to effectively collaborate on detecting, investigating and preventing data exfiltration.
Today we want to dive in and explore what the new release offers on a technical level.
How Proofpoint ITM 7.7 Tackles Removable Media Devices & Keyboard Shortcuts
Rather than attempt to block them outright, Proofpoint ITM 7.7 allows organizations to detect data exfiltration attempts through removable media devices, such as:
- flash drives
- external hard drives
- mobile devices (smartphones and tablets)
- SD cards
With 7.7, our users can now detect when these types of removable media are connected to a computer. They can also monitor and detect when any files are being copied or directly downloaded to these types of devices. Analysts also have access to full metadata regarding removable media, including device serial numbers, which allows them to pinpoint with accuracy what happened and where.
Let’s take a look at some common use cases for our new features.
Three Major Use Cases for Proofpoint ITM 7.7
Many of our customers have expressed that they prefer to allow removable media device usage. They simply want to know if someone does something inappropriate (such as attempting data exfiltration) using these devices, and to be able to conduct efficient and thorough investigations if that happens. They also want to be able to breeze through alert triage. Let’s take a look at three key use cases.
Use Case: Alert Triage in a Busy SOC
One of the biggest challenges that many security teams face today is staying on top of alert triage. This is true even when organizations have the resources for a large security team and extensive tooling.
For example, one of our customers told us that their security operations center (SOC) has multiple security tools in use. On an average day, each of their security analysts sees close to 1,000 alerts. To triage these alerts requires the analyst to piece together information from multiple alerts, across multiple tools, manually. A security information and event management tool (SIEM) only narrows down the number of tools the analyst must consult. There is still not enough context for each alert. For this reason, most alerts were going ignored, and analysts were often wasting time on alerts that turned out to be false positives.
With Proofpoint ITM, immediate context is available alongside any alert related to users interacting with data on an endpoint, including using removable media devices in suspicious ways. Analysts can gain immediate visibility into user and data activity before, during, and after an alert using Proofpoint ITM. There is no more piecing together across tools, since it simply takes a few mouse clicks to get the bigger picture.
Use Case: Building Context Around “Outside” Alerts
Another customer relies on alerts from outside sources, including electronic data records (EDR) and call centers, to identify potential threats, including those related to removable media. They then use Proofpoint's screen capture tool to review potentially suspect user sessions.
With Proofpoint ITM, even these “outside” alerts are easy to place context around. The analyst can quickly view the user, machine, removable media device, timeline, and other meta details involved in any alert, building enough context with a few clicks to understand whether an alert needs to be escalated to investigation status or can be safely ignored.
Importantly, this also allows the organization to respect user privacy and only investigate when there is a reasonable suspicion that something inappropriate has taken place.
Use Case: Faster Data Exfiltration Investigations
With traditional means, when a data exfiltration event takes place involving removable media, it can be quite a process to track down who did it, where, and when. In some cases, especially at larger organizations in highly-regulated industries, there may be a whistleblower who points out that some data has been stolen. Now, it’s up to the security team to try to figure out who did it.
The security team might know that a particular type of USB device was used, but they will likely have to interview every single person who possesses this model and try to figure out who actually stole the data (if the claim even proves to be true). This is quite a headache and in some cases can lead to nothing but dead ends.
Proofpoint ITM 7.7 provides a level of context that makes these investigations take hours or days instead of weeks or months. With the new features we will cover in detail below, investigators can quickly hone in via serial number on the specific device used in the data exfiltration attempt. Using the investigative tools we’ll cover below, they can see a timeline of events, view file history, and even play back the user’s actions to definitively prove what went down.
Using Proofpoint ITM 7.7 for Removable Media Monitoring: Key Features
Now, let’s take a look at some screenshots that illustrate the level of detail available and how easy it is to use Proofpoint ITM 7.7 for both proactive and reactive security operations related to removable media.
Let’s say an organization needs to review alerts related to USB drive usage. Here are a few of the key Proofpoint ITM features that can help with triaging these alerts.
File Diary
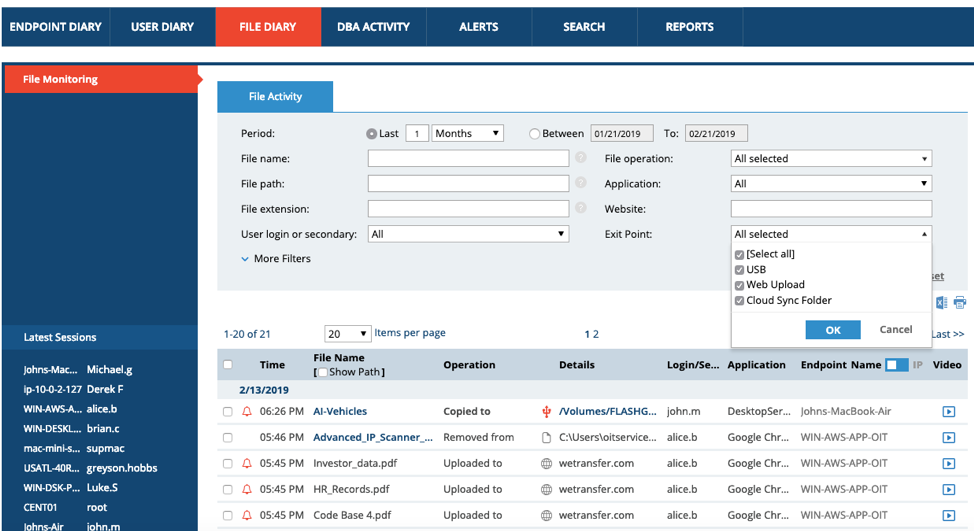
Proofpoint's File Diary now contains visibility into the “Exit Point.” This enables investigators to understand where data exited a device (e.g. via USB upload, Web Upload or Cloud Sync Folder):
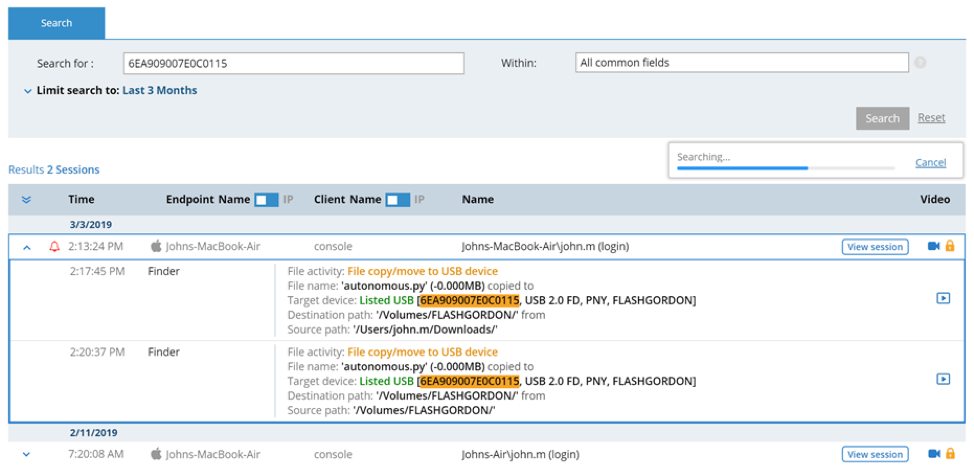
Let’s say the exit point was indeed a USB drive. By clicking on Exit Point > USB, it’s possible to see that a particular sensitive file, “AI-Vehicles,” was copied to a Flash drive. Let’s click on the name of the USB drive.
USB History
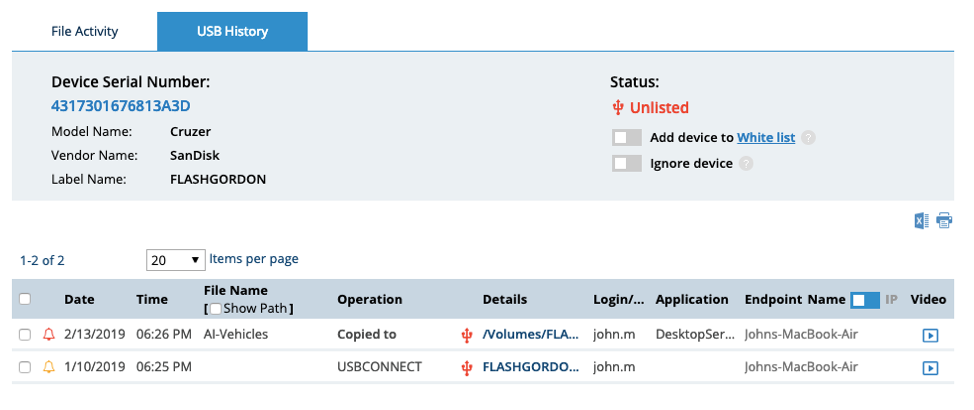
Doing this will allow us to see how the USB drive in question has been used in the past.
Proofpoint ITM shows analysts the device’s serial number and the activities it has been implicated in previously. They can also see the login associated with the USB drive, and the name of the endpoint, which gives significant context about who may be attempting the data exfiltration. (Of course, at this point, if analysts determined that the activity was harmless, they could also whitelist the USB drive and move on to the next alert.)
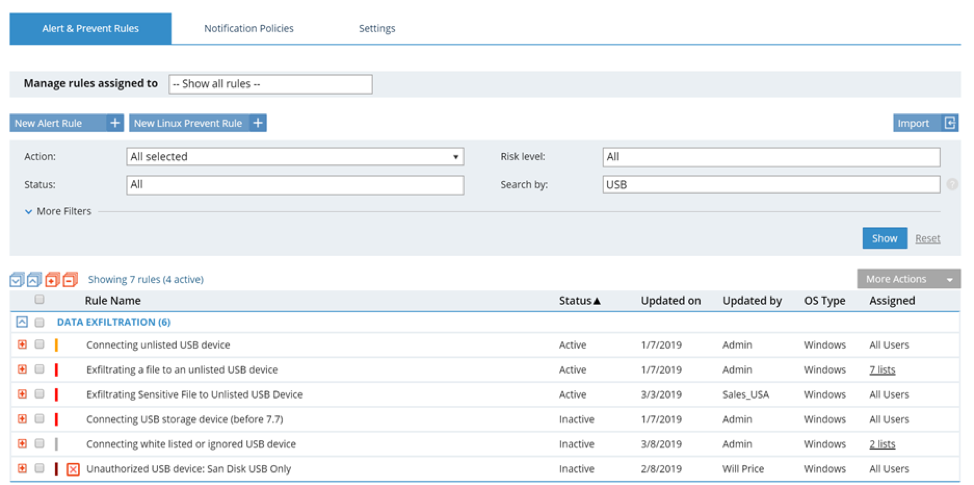
Whitelisting
The first time a new device, for example a USB drive, is connected to an endpoint, it will automatically be flagged by Proofpoint ITM as “Unlisted.” From there, security personnel can decide whether to trust the device by “whitelisting” it. Additionally, if a device is known to be trustworthy and there will be quite a bit of data flowing to it (for example, if a complete computer backup is taking place), it’s also possible to “ignore” the device altogether. This will cut down on alerts and help the security team focus their time and attention.
See how this looks in this screenshot below:

Of course, even if a device has been whitelisted, shady things can still happen and the security team would not want to miss them. For that reason, Proofpoint ITM enables customers to flag certain sensitive files or file types and get alerts related to their movement.
If, for example, someone tries to copy a confidential database of customer names onto a USB drive, Proofpoint ITM will ensure the security team gets a notification to review this activity right away, regardless of whether the device was whitelisted. This way, teams aren’t clogged up with an alert every time a USB device gets used, but they know when sensitive data makes its way onto one.
Timeline View
The timeline below view shows both user activity and file activity in one place, providing useful correlation and context. With the timeline view, analysts can quickly understand whether an alert is real or a false positive. If the alert is real, they can understand whether the user was acting intentionally (malice) or accidentally (negligence). They can also see what led up to the removable media-related activity, and from where to where a file traveled. This is very useful for proactive security strategies, but can also be helpful during a forensic investigation.
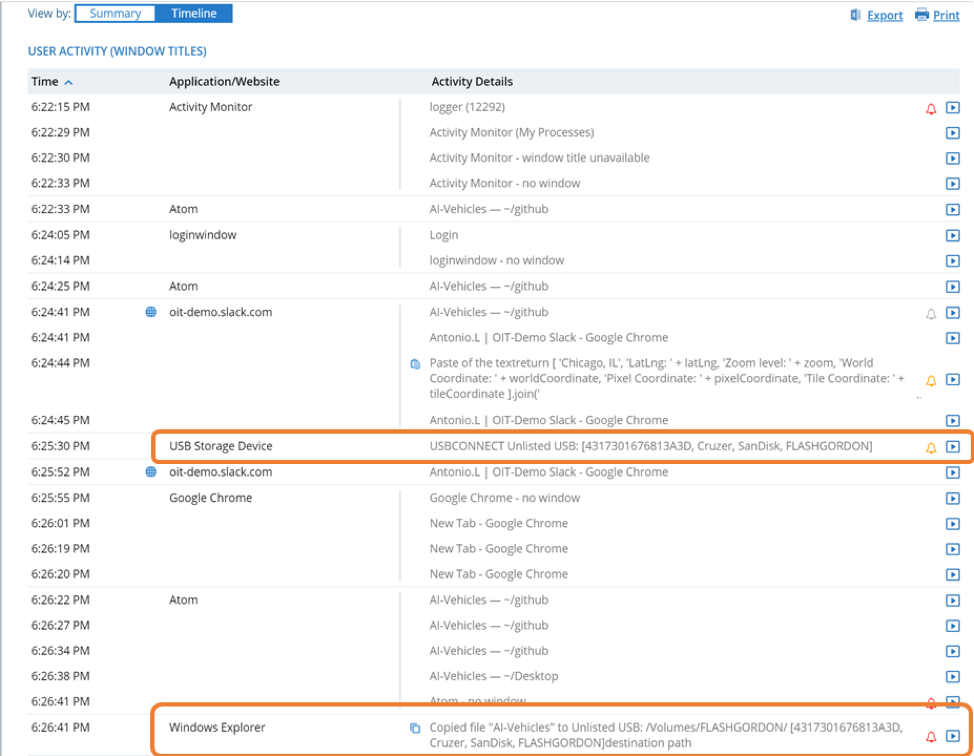
Session Playback
Finally, Proofpoint ITM 7.7 enables session playback for incidents that take place involving removable media. In many cases, this can be a very helpful way to visualize exactly what a user was doing when they moved certain data from one place to another. It may exonerate or implicate them, but either way the analyst walks away with hard evidence of what took place. In the case of the “AI Vehicles” data theft, we can click on “Video” on the far right below:
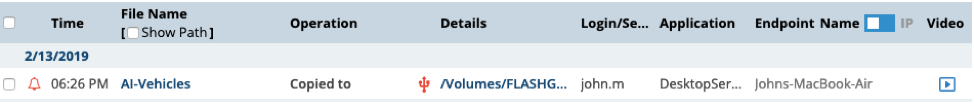
This will give us a clip demonstrating what the user saw on their screen and can help us understand if there was intentional data exfiltration going on.
Conduct Business Securely Without Disrupting Productivity
The world of security is far from black-and-white today, and it’s only getting grayer by the minute. Instead of focusing on defending a rapidly evaporating (if not altogether vanished) perimeter, Proofpoint ITM helps customers focus on proactive security first, while also providing the necessary visibility and context to conduct efficient investigations.
With context-rich visibility into the use of removable media, Proofpoint ITM 7.7’s modern approach to data loss enables businesses to operate securely without disrupting employees’ productivity.
In our next technical blog post, we’ll go over the file activity monitoring policies that are also part of the Proofpoint ITM's 7.7 release. Keep your eyes peeled!
Ready to give Proofpoint ITM 7.7 a shot?
Existing customers:
New to Proofpoint?











