Early indicators of an insider threat risk can help organizations quickly and appropriately respond to out-of-policy behaviors, while maintaining user privacy and decreasing overall organizational risk.
Threats that originate from inside an organization often don't show up until it's too late. After all, insiders don't need to exercise caution in persisting on a network. They rarely take steps to evade defences, and they don’t need to hack systems to get credentials. By working within the organization, they already have access to sensitive data and critical systems every day.
This is why organizations must invest in security solutions that provide early warning or indication when insiders engage in risky or out of policy behavior prior. This is the only way security teams can identify an insider that could pose a threat before the damage is done.
First: A Note on Privacy by Design
Every smart security team today realizes that privacy must be woven into their insider threat detection and response plans. Because while it’s important to be alerted when early indication or warning signs occur, it’s not okay to violate the privacy of your users—especially if your business is one of the many that is beholden to privacy laws like GDPR.
For this reason, it’s important to discuss how an organization can maintain user privacy while still alerting on using these early indicators of insider threat risk. In our view, the best way to accomplish the security/privacy balance is to anonymize user identities. Risky activity should trigger alerts such as those displayed in the screenshot below, but user privacy should not be violated unless there is a clear and present danger (and, even when this is the case, strict privacy protocols around who can access what data and when should be part of any organization’s insider threat management plan).
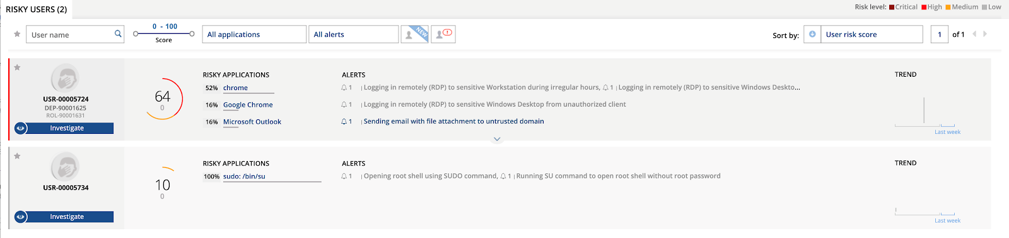
Anonymized Risk Dashboard
This ensures the security team has early indications and visibility into risk factors, while protecting any individual user from privacy violation. Furthermore, Proofpoint's platform provides a great degree of policy flexibility for organizations, and many administrators choose to exclude certain personal data from visibility. This may include banking, healthcare, or insurance information and websites, as well as social media applications. Every organization is different, but today’s regulatory and media climate requires that businesses take privacy seriously, even as they work to secure their organizations. This is why Proofpoint ITM employs “privacy by design” and empowers customers to do the same.
Now, let’s take a look at examples of some common early indications related to insider threat and how organizations can use them to reduce overall risk.
Early Indicators: Developing a New Insider Threat Vocabulary
In the security industry, we need to develop a new vocabulary for early warning signs that indicate insider threats.
Here are the top indicators of insider threat risk (prior to the current pandemic situation), according to our research on usage patterns within our 1,200+ strong customer base. (These are known as “alerts” in the Proofpoint ITM platform.)

Top Insider Threat Risk Indicators
As you can see, there are many different indicators, and the ones that are most relevant can vary depending on business use cases and other factors. These alerts are an ideal place to start when it comes to building a more robust insider threat management program, because they enable an organization to move beyond reactive security into proactive insider threat risk reduction.
Now, let’s discuss how organizations have used some of these early indicators. These risks fall into four broad categories:
- Identifying users with heightened risk factors
- Identifying technical opportunities for misuse and exfiltration
- Detecting signs of intentional misbehavior
- Detecting accidental misbehavior and/or negligence
Identifying Users with Heightened Risk Factors
Many people-driven early indicators are found through conversations. This is why smart businesses recognize that effective insider threat management requires close collaboration with HR, IT and legal teams. HR teams generally have the best understanding of what is happening on a human level within the workforce, including both work and personal issues. For example, HR is likely to be aware of an individual who has been put on a performance plan and may not be at the company much longer. They are also often the first to know when an employee is leaving to join a competitive organization and may have an interest in taking company secrets with them. Similarly, HR and IT work together to handle the digital identities and permissions of users when they join the organization, leave it, or move between departments.
Using information gleaned from conversations with HR, IT, legal, and other stakeholders at the organization, security teams can tailor risk profiles for individuals and groups.
Additionally, we often find organizations who have been through recent mergers and acquisitions or significant hiring sprees usually setup additional early indicators for new users, who may require education on the corporate security policies. One area that’s often forgotten is when existing employees and contractors switch roles within the organization. Security teams should be more careful if these employees and contractors continue to accumulate their access privileges from the previous roles or the practice of decommissioning access privileges is less mature.
Proofpoint customers rely on many of the alerts listed in the Top Insider Threat Risk Indicators chart above. Customers can also combine these alerts with our Lists feature, as shown in the screenshot below.
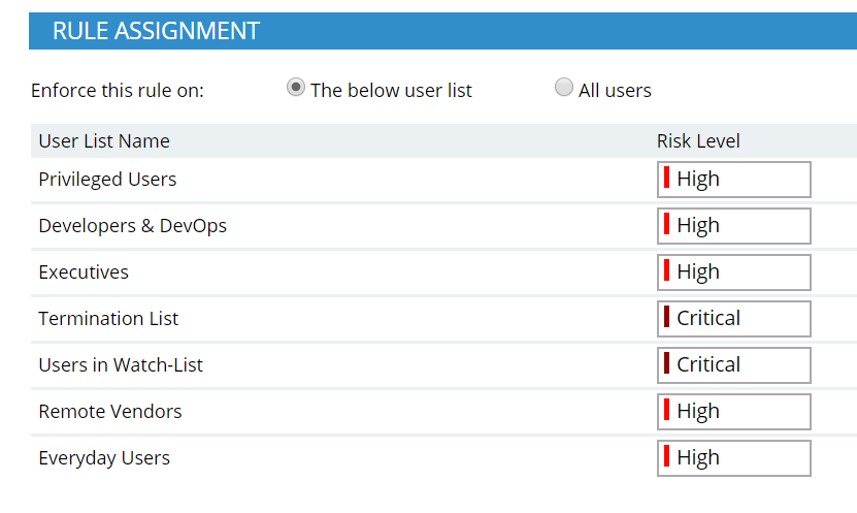
User Group Lists
This enables customers to differentiate the risk severity of alerts based on the list that the user falls under. For example, it makes sense for the alert role of “exfiltrating files to unlisted USB devices” to be set at “critical” for departing users.
Identifying Technical Opportunities for Misuse and Exfiltration
Many organizations lack visibility on user movement of sensitive data and on user activity within critical applications. Often, insider threat risk can increase when exceptions to security policy are issued to users to give them needed technical control. The risk compounds when these exceptions are allowed to go on without a time limitation, or when more and more users across the organization rack up exceptions.
The most popular example of security exceptions we see is allowing the usage of removable media. It never ceases to amaze us the number of users that have been granted an exception to use USB devices at an organization, even when most USB usage across the company is severely restricted (for good reason). The various risky security scenarios related to USB device usage almost always figure in the top five most common issues for our customers.
Of course, these risks go well beyond USB devices though, to include legacy applications still in use with poor logging and using unauthorized messaging and data-sharing applications.
In many healthcare, energy and financial services firms, sensitive customer data and intellectual property lives in legacy mainframes and desktop applications, as well as cutting-edge microservices hosted in the cloud. Unfortunately, these businesses are often stuck relying on certain legacy applications because the cost of ripping and replacing is too high. The security challenge here is that these applications weren’t built with today’s security risks in mind, so there is little hope of early detection of insider threats. Poor audit trails of user activity within those applications leave security teams guessing about what happened and which users were involved if an incident takes place.
In such situations, Proofpoint's alerts around downloading or copying large numbers of files from those specific legacy applications can be very helpful to decrease insider threat risk.
Detecting Early Indicators of Intentional Misbehavior
User misbehavior, defined as intentional misuse of corporate resources, is relatively rare compared to accidental misuse. Criminal insiders account for just 14% of all insider-caused incidents, according to the Ponemon 2020 Cost of Insider Threats Global Report. However, they also cost organizations more than twice as much per incident as negligent insiders.
Additionally, for organizations facing turbulent times and for individuals facing significant personal or work-related issues, misbehavior with corporate assets can grow quite a bit more common.
This is another area where HR can be a very helpful resource to identify users who may pose a higher risk of intentional misbehavior, for example:
- Those who have been passed up for promotions
- Those who are dealing with financial troubles.
In some cases, these frustrations can boil over in the workplace and result in brand damage for the organization as well.
What does this look like in practice? User misbehavior may start with using corporate endpoints for out-of-policy activities, such as gaming or browsing copyright-violating websites. These indicators of insider threat risk may be categorized with low-severity alerts and triaged in batches. IT security may want to set up higher-severity alerts in the case that a user moves onto more critical misbehavior, such as installing hacking or spoofing tools on corporate endpoints.
In the recent past, we’ve also seen a rise of nation-state inspired or sponsored insider threats. In these cases, users with ties to certain nation-states are monetarily or otherwise incentivized to exfiltrate highly sensitive or secretive intellectual property data from their organizations. Often these are non-technical business users working on secretive projects or developers working on sensitive intellectual property.
Again, collaboration with other departments (such as HR, threat-hunting and legal teams) can provide a heads up around rising nation-state involvement in certain locations. Proofpoint ITM customers often combine these internal early warnings with increasing alert severity levels on users who may have a higher insider threat risk profile.
On another note, customers can also use our workplace harassment and violence keyword lists to notify security teams and provide real-time education to the user(s) involved when inappropriate and/or harassing language is used on an organization’s messaging platforms.
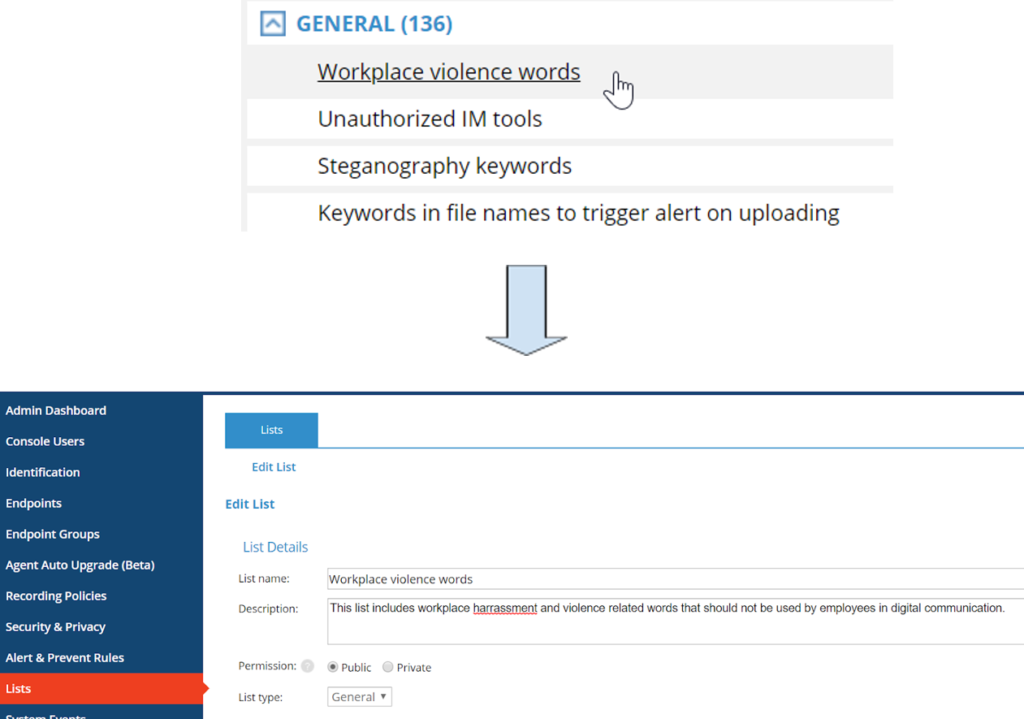
Workplace Harrassment and Violence Lists
Detecting Early Indications of Accidents and/or Negligence
The last category refers to the most common type of insider threat: accidental errors and/or negligent behavior. In fact, 62% of all insider threats are caused by negligence, as the previously mentioned Ponemon report found. We are all using more applications, collaborating with more people and working under tight deadlines in an increasingly competitive work world.
It’s not surprising, then, that users make more mistakes, forget the details of acceptable use policies, or take shortcuts that circumvent security controls.
The best way to manage this type of insider threat risk is to set up alerts that identify accidents and negligence early. For example, good alerts to set up include:
- Usage of unapproved USB devices
- Downloading of files with potentially malicious extensions
- Storage of passwords in plain-text files.
The most common mistakes are related to social engineering attacks on employees and contractors, including credential theft, which accounts for 23% of insider-caused incidents, according to Ponemon.
In addition to detecting signs of social engineering scams and malware proliferation, Proofpoint customers use our contextual intelligence to better understand behavior before and after alerts fire. This enables organizations to determine whether the user was indeed manipulated or phished, or if they acted with malicious intent to harm the organization.
Our customers recognize that there are important differences between accidental and malicious insider threats, and they must be treated differently. That’s why real-time user education is one of our top-used security actions in response to alerts on accidental or negligent behavior. The following screenshot displays the various real-time response actions to triggered alerts that are available to security teams within the platform. Proactive, early education is a much better response to accidental misuse than punitive measures that can lead to even worse consequences for the employee and the organization.
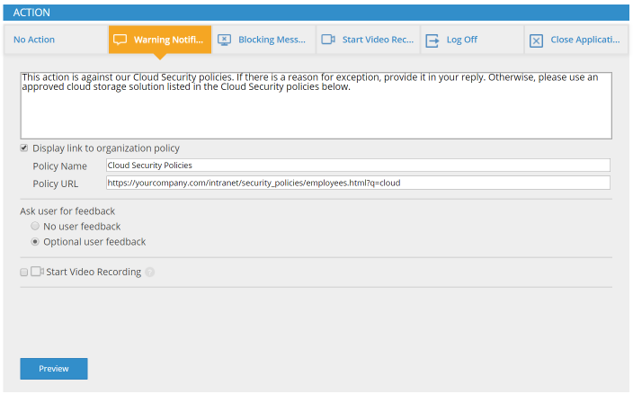
Real-time user awareness response option
Highlighted in orange above is the warning notification option. This will pop up on the offending user’s endpoint if they attempt to complete an action deemed risky by the security team, such as downloading files with potentially malicious extensions.
Indicators of Risk: A Proactive Approach to Insider Threat Management
Proofpoint's top indicators of risk can provide a broad view into how mature insider threat programs operate successfully. As we’ve shared in this blog post, these early indicators or warning signs are uniquely pertinent to users with deep familiarity with and access to your sensitive data and critical systems. They enable organizations to become more proactive, to intelligently separate intentional vs. accidental threats, and to broadly decrease organizational risk.
Learn more about early indicators of insider threats from Dawn Capelli, CISO at Rockwell Automation, and Josh Epstein, VP at Proofpoint, in the SecureWorld eSummit ITM webinar.











