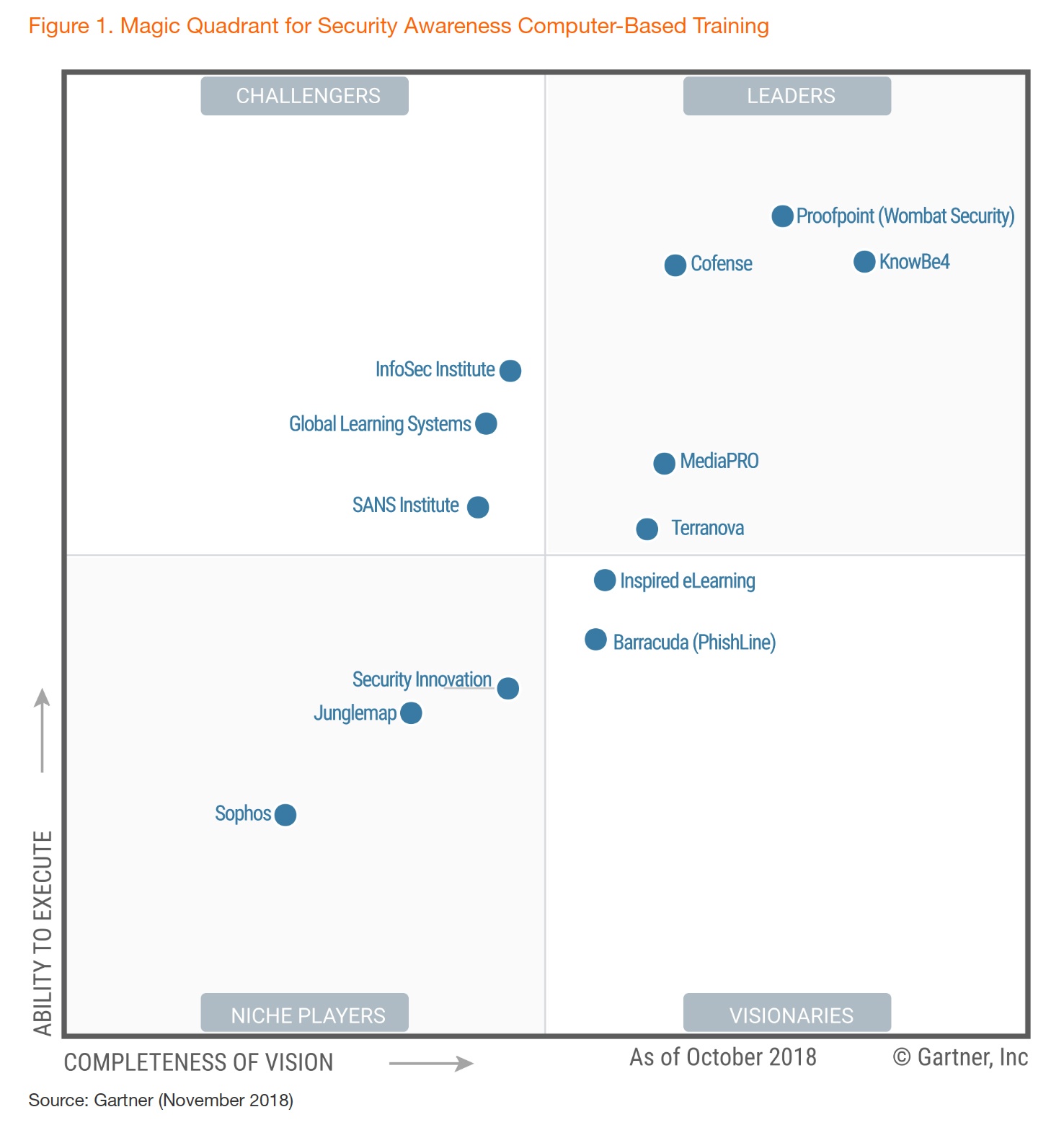
Continuing to Deliver Leading Security Awareness Training
We have been a Leader in the Security Awareness CBT Magic Quadrant since it was first published five years ago, and we believe our continued leadership position, following our acquisition by Proofpoint in March, shows our commitment to moving the security awareness training market forward. Following are some of the recent product innovations that are allowing our customers to deliver effective cybersecurity education that changes end-user behavior and reduces risk:
Training Customization and Personalization
In February, we launched our configurable Password Policy training module, which allows organizations to teach their end users to create strong, effective passwords that comply with specific company policies. Training customization and personalization will be continued areas of focus for us into 2019 and beyond. Our all-new customization center will allow administrators to modify training modules to meet their specific needs. In addition, we will continue to offer more opportunities for organizations to deliver the right content, to the right people, at the right time, further targeting their training in response to emerging threats and end-user behaviors.
Proofpoint Integration
Proofpoint’s focus on people-centric cybersecurity solutions marries with our goal to help organizations improve end-user behaviors and build a stronger last line of defense against phishing, ransomware, and other cyberattacks. Two recent announcements show our ability to integrate Proofpoint’s world-class products and industry-leading threat intelligence with our security awareness training portfolio and expertise:
- Closed-Loop Email Analysis and Response (CLEAR) – Our new CLEAR solution combines Wombat’s PhishAlarm® email client add-in and PhishAlarm Analyzer email prioritization tool with Proofpoint Threat Response Auto Pull (TRAP) to streamline end-user reporting of — and security response to — potential phishing attacks. CLEAR allows users to quickly and easily report suspicious emails directly from their desktop or mobile device. Once reported, CLEAR automatically analyzes messages against multiple intelligence and reputation systems, reducing an organization’s typical threat triage time from days to minutes, without requiring additional work from human analysts.
- Attack Spotlight – Our Attack Spotlights combine Proofpoint threat intelligence and Wombat security awareness tools to provide free, timely, actionable content organizations can use to arm end users against the ever-evolving phishing threat. We release new Attack Spotlights as pressing threats are identified, which means the time between spotting a trending attack and informing end users can be reduced dramatically, from months to days.
Ongoing and deeper integrations with Proofpoint products will ensure that your "Very Attacked People" get the knowledge they need to defend themselves against the advanced threats of today.
Proprietary Research That Provides Actionable Insights Into End-User Behaviors
We analyze our own wealth of security awareness training data and commission independent surveys throughout the year in order to deliver research reports that help organizations identify trends in end-user behaviors and better understand continued knowledge gaps that are putting security postures at risk. This year, we released new editions of our compelling and widely quoted State of the Phish™ and Beyond the Phish® reports, and significantly expanded the scope of our recently published 2018 User Risk Report, which features the results of a survey of 6,000 working adults across six countries (the US, UK, France, Germany, Italy, and Australia). All three pieces of research are excellent resources for any organization that is seeking real-world insights into the need for security awareness training and the types of activities that can minimize end-user risk.
More Innovations to Come in 2019
It is gratifying to again be named a Leader and to be recognized by Gartner for our efforts to deliver the best security awareness training solutions to organizations of all sizes, across all industries, and in all global locations. We marked our 10th anniversary earlier this year, and we know we’ve come a long way since the days when our founders pioneered the use of simulated phishing attacks — but we won’t rest on our laurels. We will continue to lead and innovate in the years ahead as we work to bring the most effective cybersecurity education tools to organizations and end users around the world.
“Cybercriminals are targeting people, not infrastructure, to access critical systems, siphon funds, and steal information. It’s essential to educate today’s workforce on how to identify and help stop the near-constant onslaught of cyberattacks that they will undoubtedly face,” said Kalember.
* Source: Gartner, Magic Quadrant for Security Awareness Computer-Based Training, Joanna G. Huisman, 13 November 2018.
** In 2014, 2015, 2016, and 2017, Wombat Security Technologies was positioned as a Leader in this Gartner Magic Quadrant. Wombat was acquired by Proofpoint in March 2018 and now operates as Wombat Security, a division of Proofpoint.
Please note: This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from /wombat-named-a-leader-2018.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.