When distributing malware to potential victims, threat actors have various options for payload delivery. Malware can be attached to an email, or a direct link to the malicious file can be included in the body of an email. The actor can also email a link to a compromised site and prompt the recipient to download a malicious file, often under the guise of being a software update or other benign file. This final technique, commonly known as a fake downloader, is not new, but it is effective.
Recent fake downloader campaigns observed by Proofpoint researchers appear to be the work of threat actor TA569, also known as SocGholish. TA569 is known for compromising CMS servers and conditionally injecting and redirecting web traffic to social engineering kits.
In June and July 2020, thousands of messages were sent to organizations in Canada, France, Germany, Spain, Italy, the United Kingdom, and the United States. In one campaign from early July alone, Proofpoint observed nearly 18,000 messages from this actor. These campaigns featured links to websites compromised with SocGholish HTML injects.
These injects analyze the user’s geolocation, operating system, and browser. If the user’s environment meets specific conditions, they are led to a spoofed browser update page. These pages use social engineering to convince potential victims to take an action, such as clicking a button, which downloads a JavaScript or HTA file. If executed, the script fingerprints the system and downloads and executes the next stage malware once it verifies the user’s geography is targeted. The observed malware includes a banking Trojan (Chthonic) and/or remote-control software (NetSupport). Chthonic is a variant of the Zeus banking Trojan and NetSupport is a legitimate remote-access application often abused by threat actors.
The top verticals among the intended recipients include education, state governments, and manufacturing, and numerous others. Below are examples of the fake browser update pages in English, French, German, and Spanish:
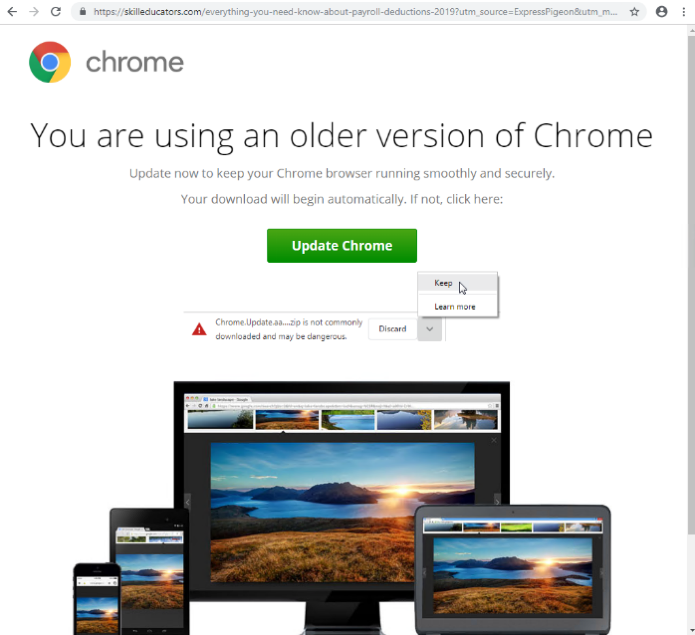
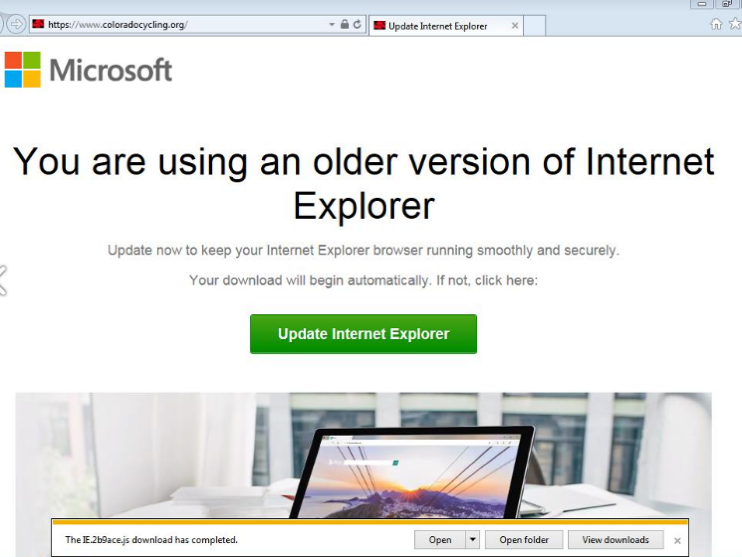
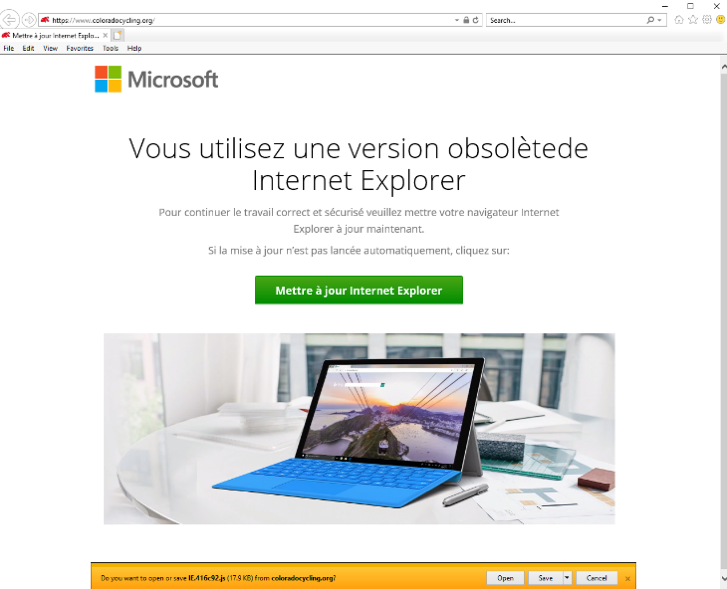
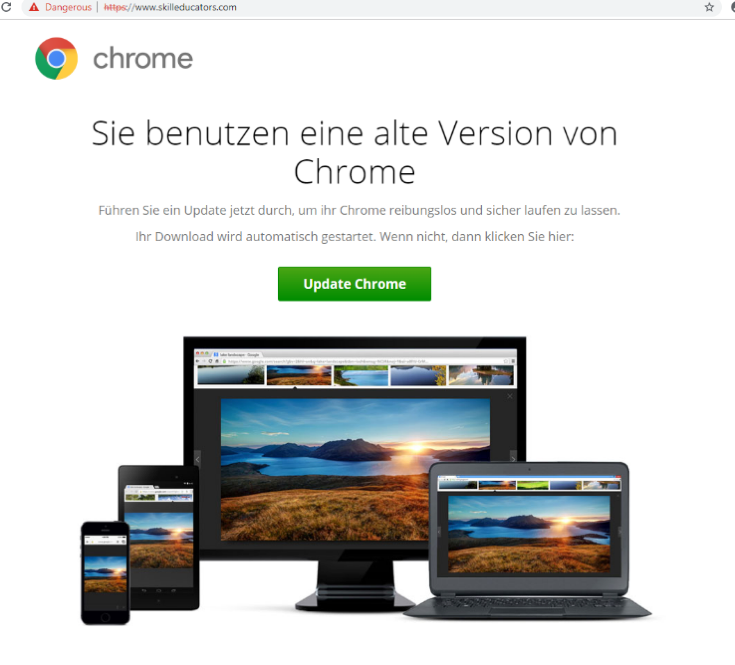
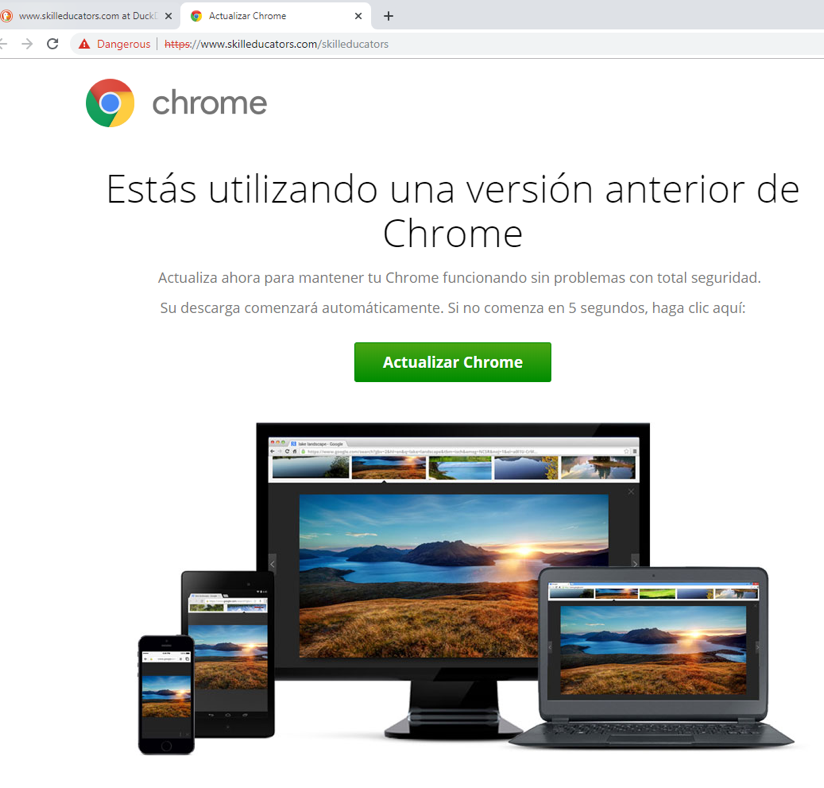
While this technique isn’t new, it’s still effective because it exploits the intended recipient’s desire to practice good security hygiene. Keeping software updated is a common piece of security advice, and this actor uses that to their advantage. These campaigns illustrate that malware and threat actor tactics don’t have to be novel to find success, even in today’s rapidly changing threat landscape.











