Key findings
- The highest volume threat in current Proofpoint campaign data is a phishing kit named CoGUI, which is actively targeting Japanese organizations.
- CoGUI campaigns impersonate well-known companies, mainly consumer and finance brands.
- The objective of the campaigns is to steal usernames, passwords, and payment data.
- CoGUI has some similarities to a phishing kit known as Darcula. Both kits are used by Chinese-speaking threat actors.
- The CoGUI kit has several advanced defense evasion techniques. Proofpoint has created detections and Emerging Threats rules to combat this activity.
- CoGUI activity aligns with recent reporting from Japan's Financial Services Agency regarding phishing campaigns leading to financial theft.
Overview
Proofpoint has observed a notable increase in high-volume Japanese language campaigns targeting organizations in Japan to deliver a phishing kit that Proofpoint researchers refer to as CoGUI. Most of the observed campaigns abuse popular consumer or payment brands in phishing lures, including Amazon, PayPay, Rakuten, and others.
The CoGUI phishing kit is a highly evasive phishing framework identified by Proofpoint researchers, primarily targeting users in Japan. Several campaigns were observed targeting users in Australia, New Zealand, Canada and the United States, but these occurred much less frequently than in Japan.
Due to the high volume of messages targeted at Japanese organizations from threat actors distributing the CoGUI phish kit, Japan has become one of the most targeted countries in Proofpoint data based on campaign volume. However, high volume phishing targeting Japan is not new. In 2020, Proofpoint published a report about Japanese language phishing campaigns targeting Japan using similar techniques.
Japanese authorities recently published details about an increase in phishing activity targeting financial organizations. The goal of the threat actors is to gain access to victim’s accounts for financial gain, and in most cases, using illicit gains to buy Chinese stocks. Proofpoint cannot confirm with high confidence whether this activity is related to CoGUI, but it is one possible outcome of credential phishing. Notably, Proofpoint observed more finance related CoGUI campaigns in April 2025 following the reciprocal tariff announcement by the U.S. government, and some CoGUI campaigns have used tariff themed lures.
Campaign details
CoGUI is a sophisticated kit that employs advanced evasion techniques, including geofencing, headers fencing, and fingerprinting to avoid detection from automated browsing systems and sandboxes. These methods allow the kit to selectively target specific geographic regions while evading security measures, making it a significant threat to potential victims in the targeted countries.
CoGUI has been observed in the landscape since at least October 2024 and tracked by Proofpoint since December 2024. The campaigns typically include a high-volume of messages, with counts ranging from hundreds of thousands to tens of millions per campaign, with an average of approximately 50 campaigns per month campaigned by our researchers.
Campaigns are a timebound set of related activity, and in the case of CoGUI campaigns, typically include activity conducted over three-to-five-day timespans. Proofpoint tracks this activity based on a variety of criteria including brand abuse, sender information, and CoGUI infrastructure used by the threat actor.
Total message volume in campaigns recently peaked in January 2025 with over 172 million messages observed that month. It should be noted that while the majority of these campaigns are directly represented within our TAP product, the overall volume is high enough that some activity may simply be blocked by existing detections and not receive additional contextualization.
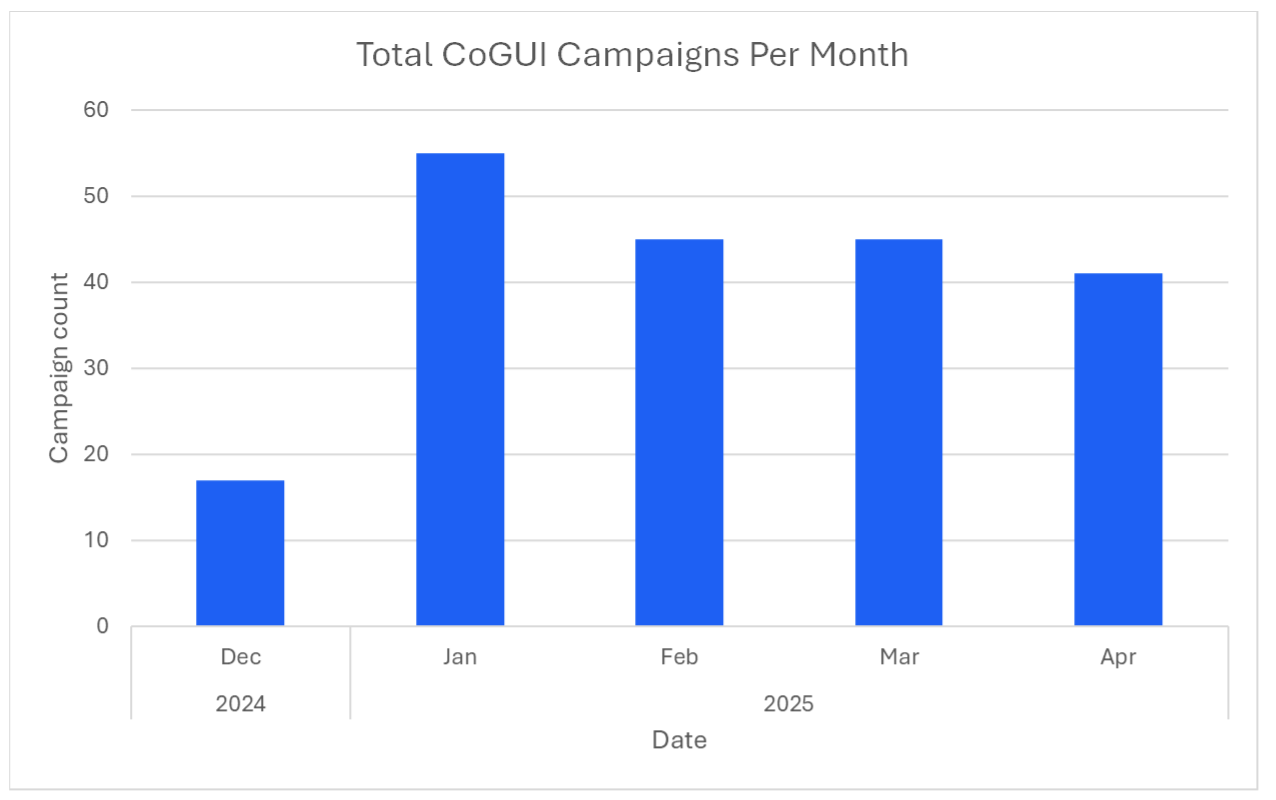
Total CoGUI campaigns observed per month.
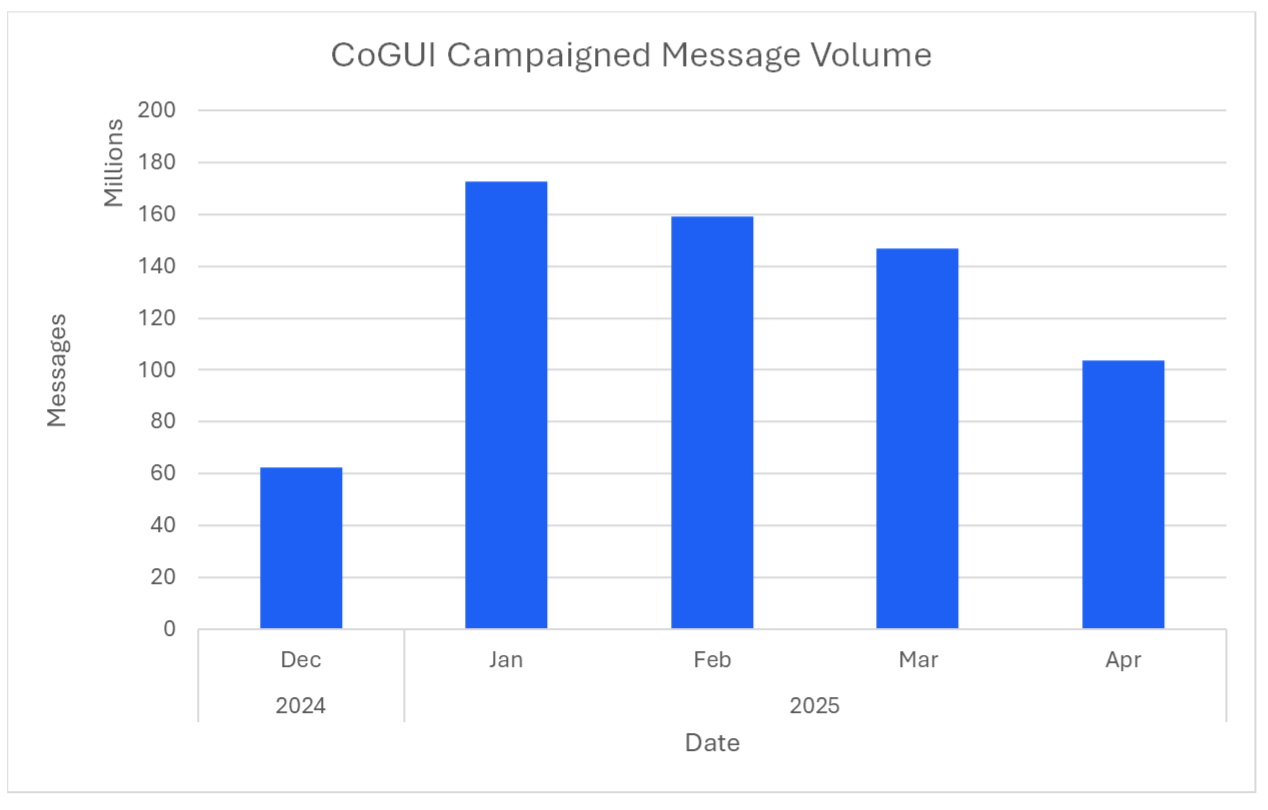
Total CoGUI messages observed in campaigns per month.
The majority of CoGUI campaigns impersonate Amazon, however Proofpoint researchers have also observed the threat actor impersonate payment cards, transport cards, popular banks, retailers like Rakuten and Apple, and Japan’s national tax agency.
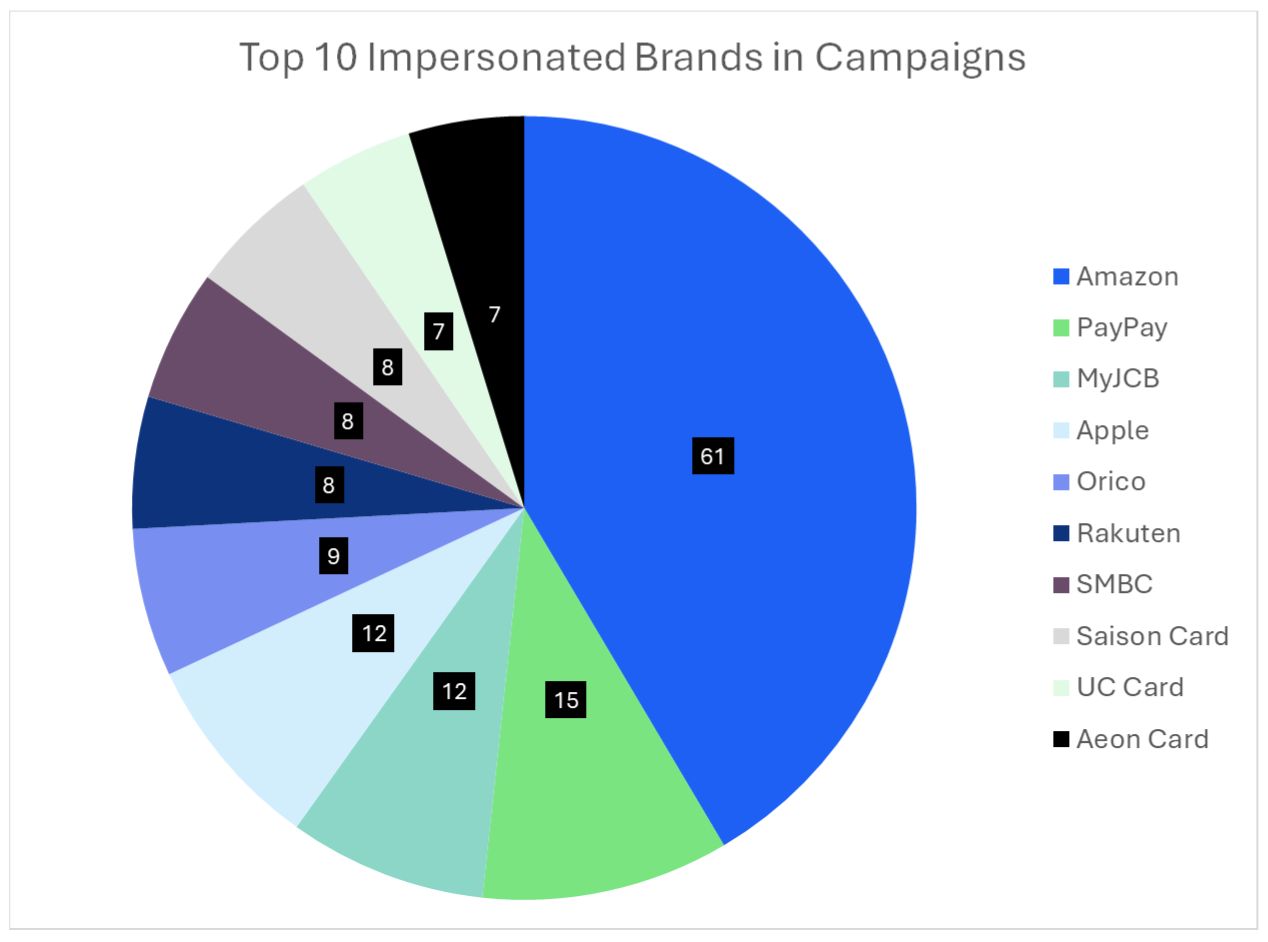
Count of top brands appearing in CoGUI campaigns, December 2024 through April 2025.
The observed campaigns included URLs in the messages that, if filtering was passed, led to credential phishing websites. Notably, observed CoGUI campaigns do not include capabilities to collect multifactor authentication (MFA) credentials. MFA collection capabilities are becoming standard for the most frequently observed email credential phishing services, so it is unusual for such a frequently observed kit to not include this feature. It is possible there are instances of MFA used by CoGUI that we have not observed.
Rakuten example
Proofpoint observed a Rakuten themed CoGUI campaign that included, in some emails, mentions of tariffs. For example, one subject line was “【Emergency Response】AI Investment Strategy for Tariff Crisis: Limited Release of Tools Supervised by Top Analyst Eiji Kinouchi”.
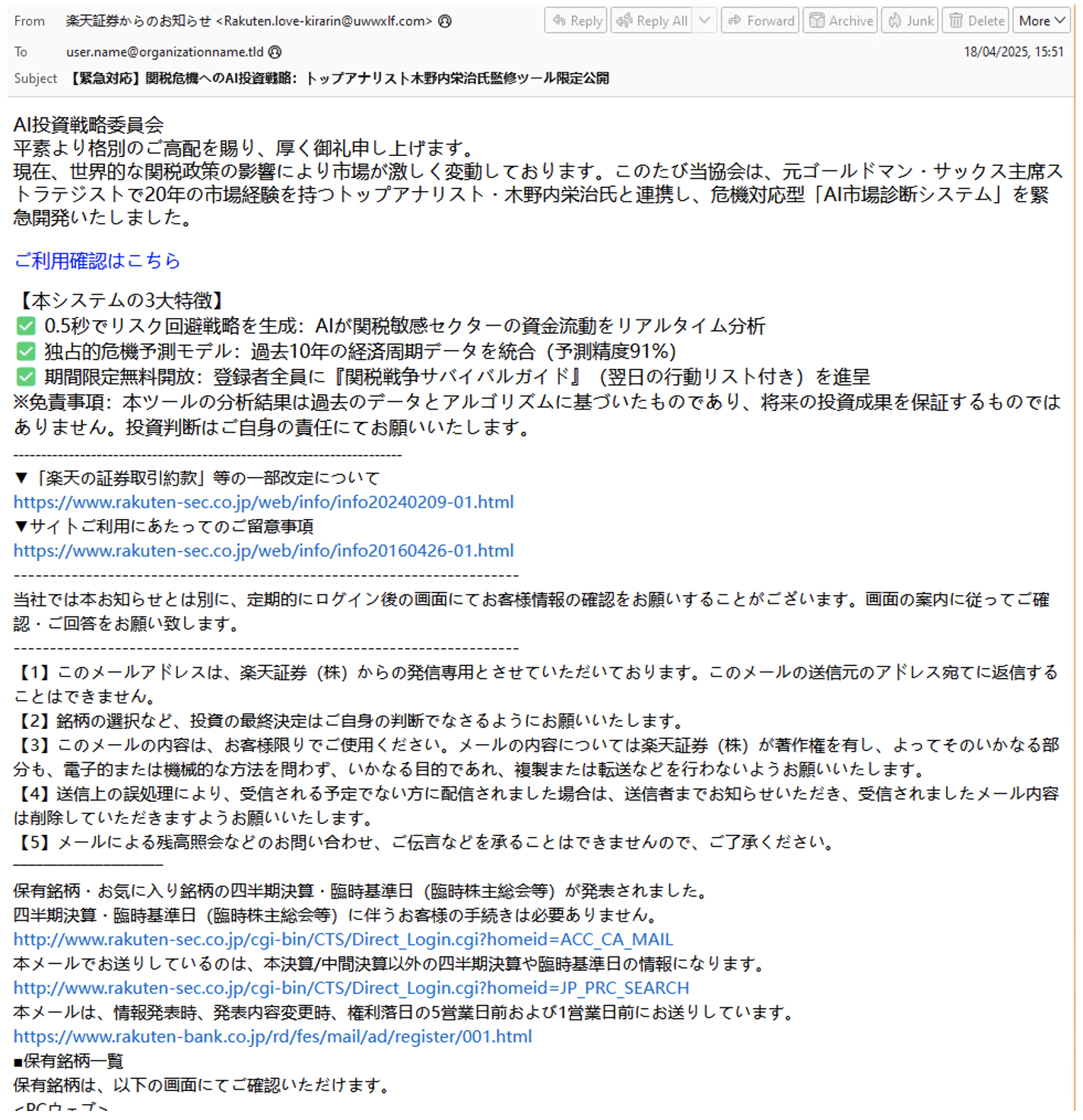
Phishing email impersonating Rakuten.
The emails contained URLs leading to a credential capture webpage impersonating Raktuen, which was designed to collect user credentials. The CoGUI configuration was:
"codeName":"日本rakuten乐天证券"
Notably, this activity aligned with the Japan Financial Services Agency's report on the impact of phishing attacks on securities companies. While the report does not provide indicators of compromise to compare with known campaigns, this Rakuten themed campaign and others impersonating different finance organizations that Proofpoint observed in April appear to align with the techniques described in the agency’s release.
Amazon example
In a campaign observed from 24 to 30 March 2025, messages purported to be from Amazon with the subject “To protect your account, please update your account.”
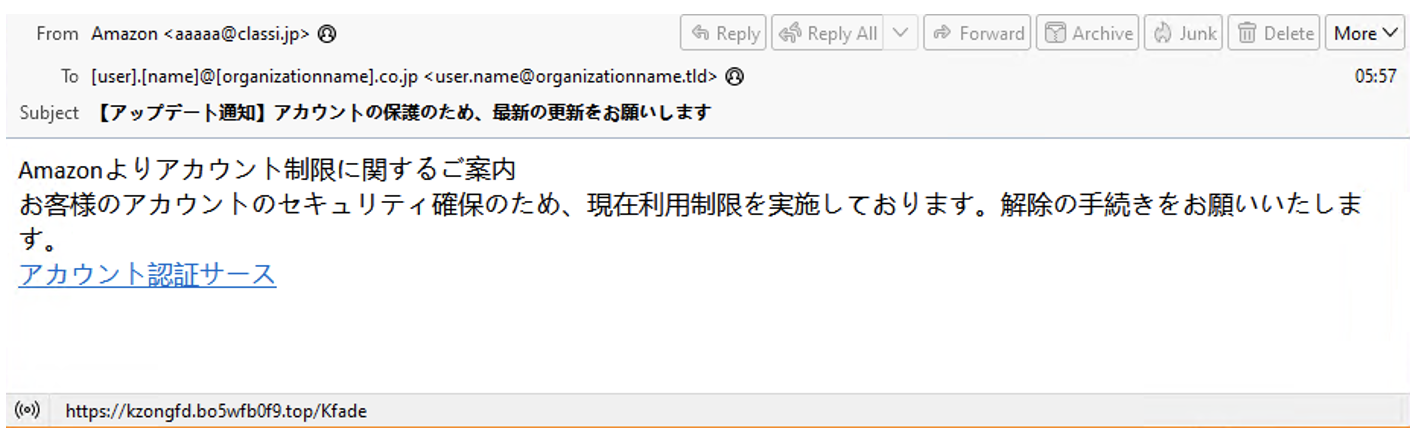
Phishing lure impersonating Amazon.
The messages contained a URL that led to a counterfeit Amazon authentication page leveraging the CoGUI phish kit and designed to collect user credentials and payment information.
The CoGUI configuration was:
"codeName":"日亚amazon无账单"
In this campaign, a user was first directed to enter their username and password for their Amazon account.
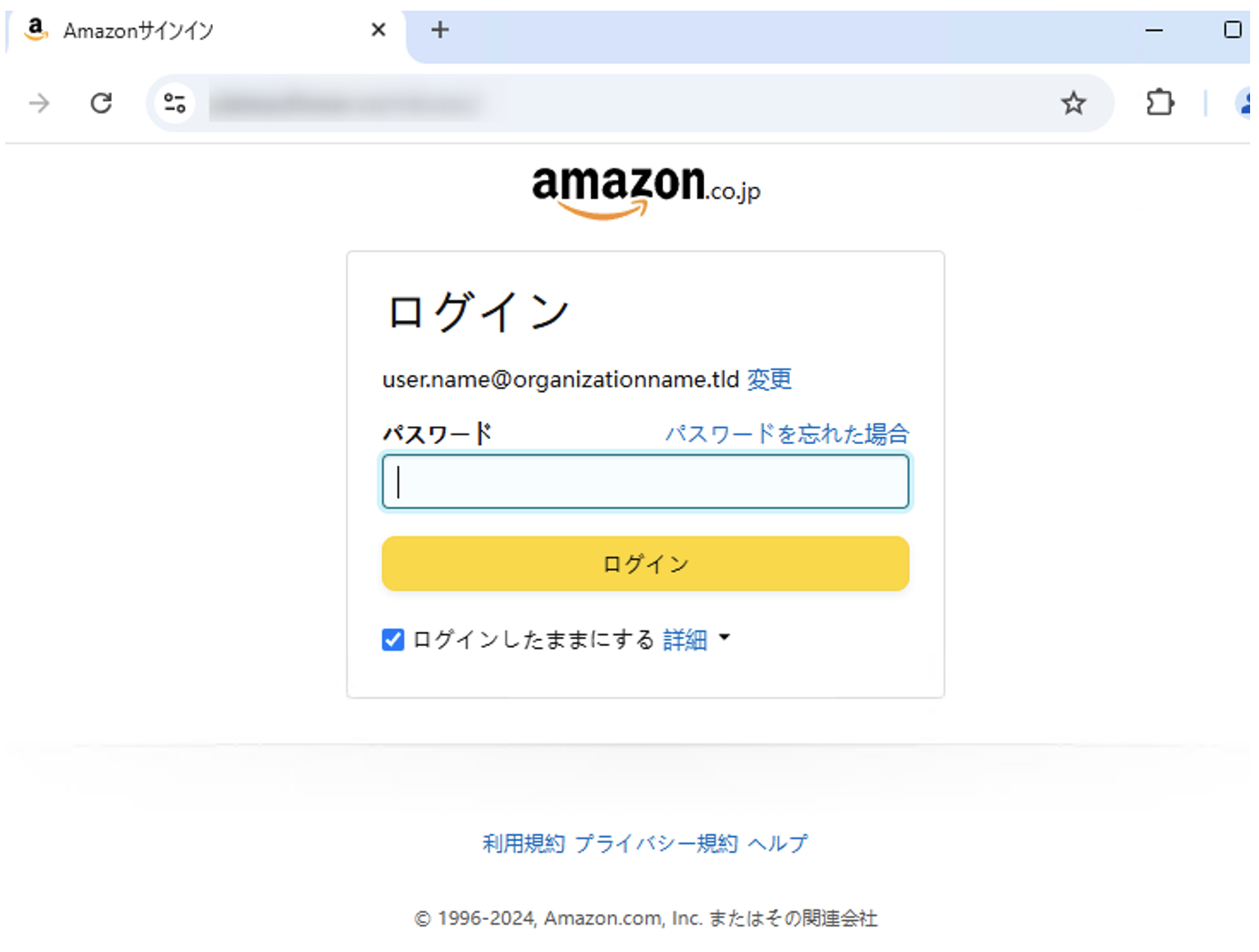
CoGUI landing page impersonating Amazon.
Then, the user was directed to enter their payment details, leading to theft of usernames and passwords as well as credit card information. This is the standard attack flow for retailer themed CoGUI campaigns.
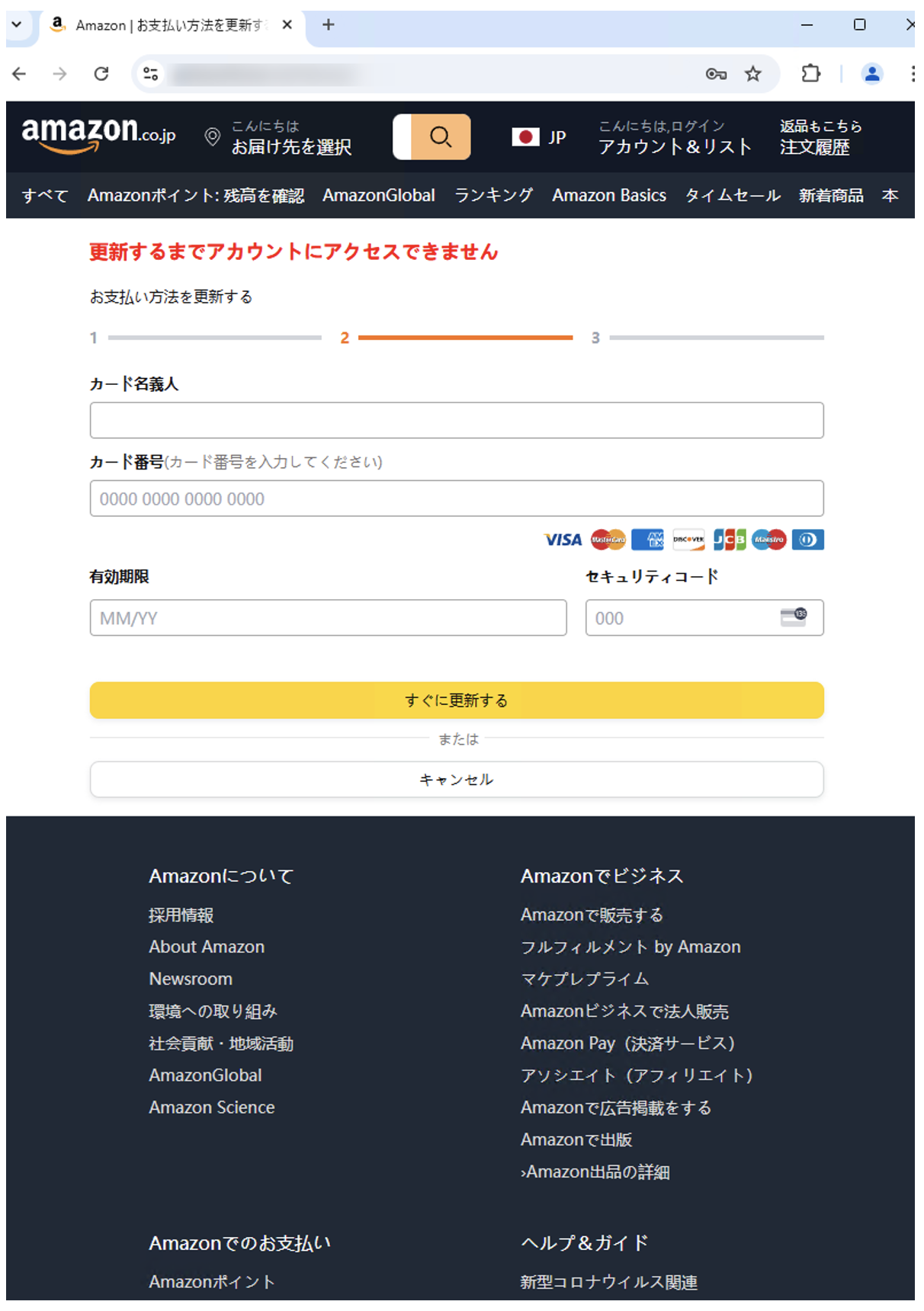
Example of payment phishing page impersonating Amazon.
PayPay example
For payment themed impersonations, the lures and data collected are usually similar. They often use identity verification, payment requests, or gift certificate or “points” for redeeming. For example, from 10 to 16 March 2025, researchers identified a PayPay themed email with the subject “[Spring Thanksgiving] Get an Amazon gift certificate & 100,000 PayPay points with entry!”.
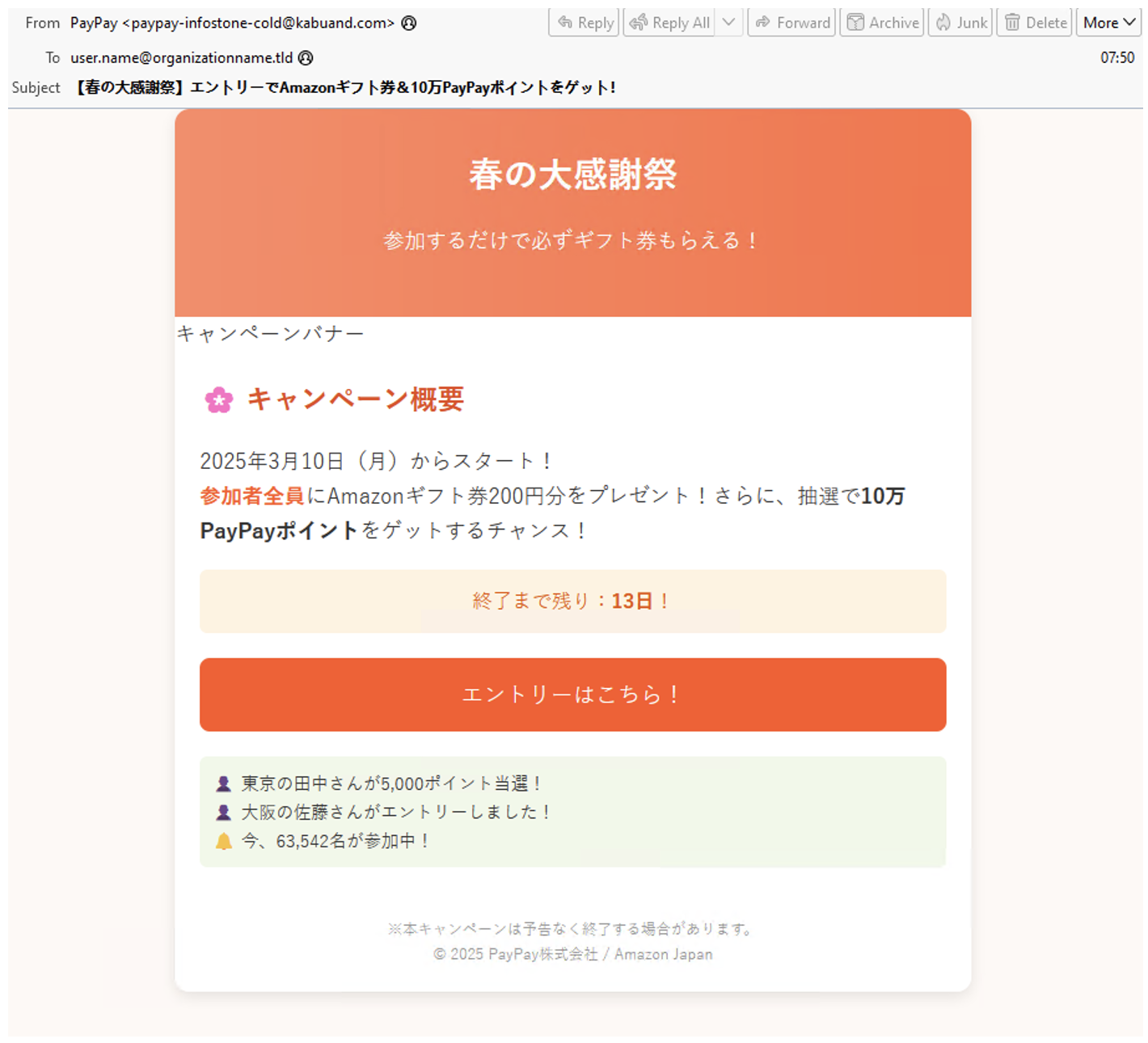
Email impersonating PayPay.
The messages contained a URL which led to a counterfeit PayPay authentication page designed to harvest user credentials and payment information.
The CoGUI configuration was:
"codeName":"日本paypay"
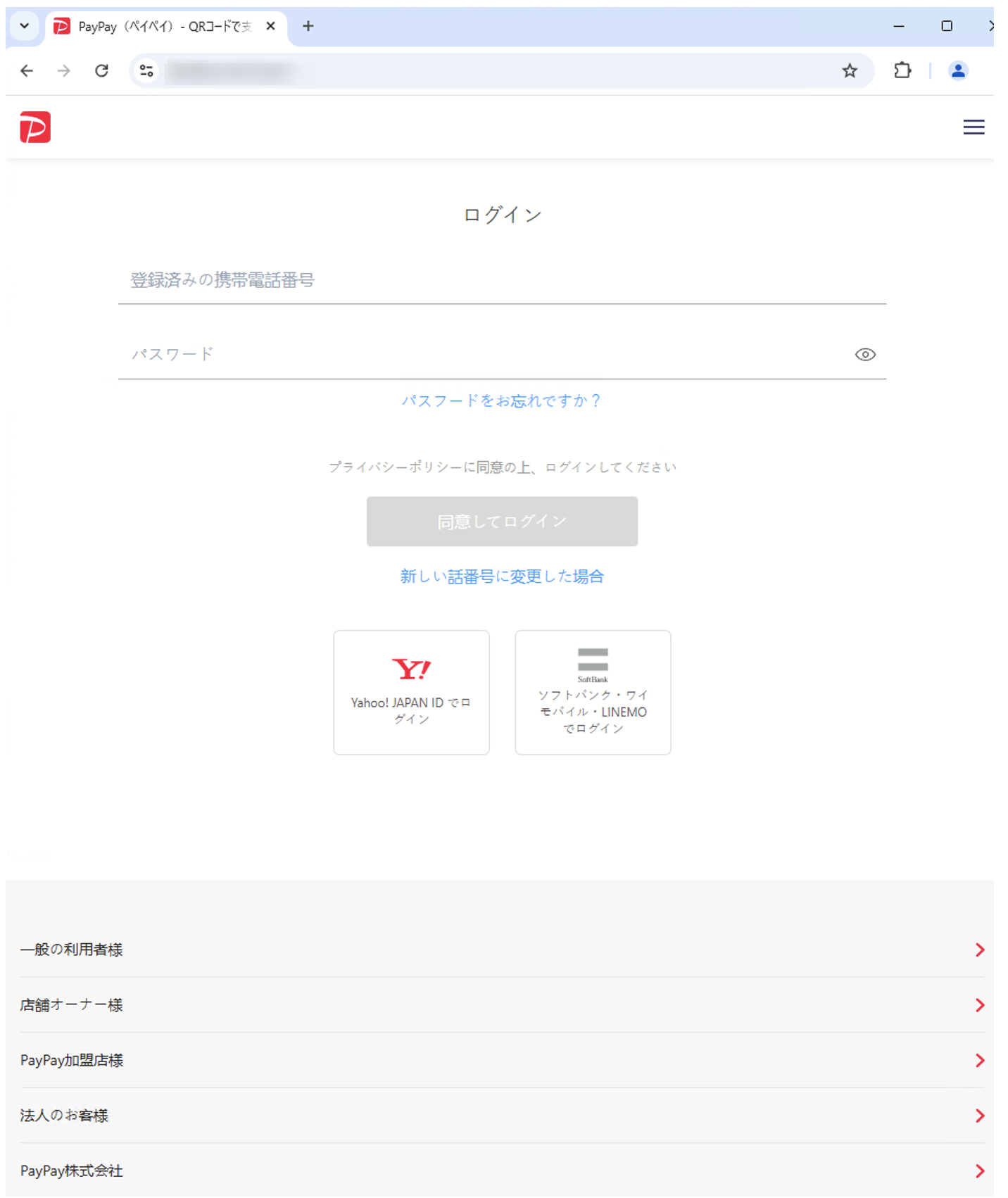
PayPay impersonation CoGUI phishing landing page.
Technical details and relation to Darcula phish kit
Before serving the phishing page, CoGUI profiles the victim’s browser. Victim profiling is used for targeting purposes but may also serve to evade automated analysis sandboxes. Information that CoGUI collects as part of its victim profiling includes:
- GeoIP (geographical location of IP address)
- Language configuration of the browser
- Browser type (e.g. Chrome)
- Browser version
- Monitor screen height and width
- OS Platform (e.g. win32)
- If the victim’s browser is running on a mobile device
Victim browser profiling often varies by campaign. One campaign may target victims on mobile browsers, while another targets victims on a Windows computer. Regardless of the criteria, once the browser profile verification has been satisfied, CoGUI delivers the phishing page. If the browser profile verification is not satisfied, CoGUI redirects the victim to a legitimate website. If the phish is spoofing “Amazon.co.jp”, for example, the victim is redirected to the legitimate Japanese Amazon website.
Interestingly, while investigating CoGUI phish kits, researchers noticed similarities to another type of activity Proofpoint is tracking: Road Toll Smishing. Road Toll Smishing references when United States based phone numbers receive SMS messages about outstanding road toll invoices. The SMS messages ask recipients to immediately begin the repayment process by clicking the URL provided.
Since 2025, Road Toll Smishing infrastructure has evolved to use a phish kit called Darcula. Third-party researchers refer to Darcula as part of a China-based group of activity known as the Smishing Triad. Proofpoint researchers initially thought Darcula Road Toll Smishing may have been related to CoGUI due to their similarities. Some of which include:
- Both initially serve a minimal HTML landing page that later loads assets.
- CoGUI will reference .js and .css files where filenames contain random alphanumeric values and set the HTML Language tag to Japanese e.g. <html lang="jp">.
- Darcula will reference .js and .css files where filenames contain hexadecimal values and use a Vue.js template. However, new variants are starting to appear with random alphanumeric values.
- Both will use the same specific online service to profile the user’s browser. If the profile is satisfactory, then the phish is served. However, Darcula only targets mobile users while CoGUI will target users on mobile or web browsers.
- Both contain Chinese language in code and responses.
- Both will send URLs where the URI is a short, single word.
Ultimately our analysis found that the Darcula phish kit is unrelated to CoGUI and its presence in Road Toll Smishing is notably different.
Proofpoint researchers are able to identify CoGUI with internal detections alongside Emerging Threats PRO CoGUI signatures, which are provided at the end of this report. Likewise, Emerging Threats OPEN and PRO Darcula signatures are also provided. Proofpoint is able to circumvent the evasion techniques employed by CoGUI, which provides customers with protection against known versions and implementations of the phish kit.
Attribution
Given the volume of activity, variety of brand abuse, timing of campaigns using the same branding, and different hosting infrastructure, Proofpoint assesses this phishing kit is used by multiple different threat actors. Based on characteristics of the kit and identified activity, it is likely the users of CoGUI phishing kit are Chinese speaking threat actors who mainly target Japanese-language speakers in Japan. The campaigns observed targeting people outside of Japan also primarily target Japanese-language speakers and organizations with operations and employees in Japan. Proofpoint also assesses that Darcula is used by Chinese-speaking threat actors but the threat actors who use it demonstrate much broader geographic targeting.
The appearance of CoGUI aligns with an increasing trend in Chinese language cybercrime across the threat landscape since 2023, including phishing kits like Darcula and malware campaigns based off Gh0stRAT variants.
Best practices to combat phishing
Phish kits use lures that mimic trusted brands and services to increase the likelihood that users will click the URL payloads provided. These lures often create a sense urgency to complete a task, presenting the URL as a convenient path for the victim to do so. To combat these dangerous but often successful lures, do not immediately click links.
Instead, slow down, visit the official website of the service, and log into your account to further investigate the lures’ claims. Organizations are advised to educate users about phishing impersonating popular consumer and financial brands and to report to IT teams when observed. Organizations are advised to implement multifactor authentication across all applications and services, however, to fully defend against MFA phishing, FIDO or other physical security tokens are recommended.
This slower path reduces the consequences of user credentials and payment information from being exfiltrated.
Emerging Threats detections
2859484 - ETPRO PHISHING CoGUI Phish Landing Page 2024-12-31
2859492 - ETPRO PHISHING CoGUI Phish Landing Page M1 2025-01-02
2859534 - ETPRO PHISHING CoGUI Phish Landing Page M1 2025-01-08
2859535 - ETPRO PHISHING CoGUI Phish Landing Page M2 2025-01-08
2859536 - ETPRO PHISHING CoGUI Phish Landing Page M3 2025-01-08
2859537 - ETPRO PHISHING CoGUI Phish Landing Page M4 2025-01-08
2859538 - ETPRO PHISHING CoGUI Phish Landing Page M5 2025-01-08
2859539 - ETPRO PHISHING CoGUI Phish Landing Page M6 2025-01-08
2859891 - ETPRO PHISHING CoGUI Phish Landing Page 2025-02-04
2859493 - ETPRO PHISHING Darcula Landing Page M2 2024-01-02
2058954 - ET PHISHING Darcula Landing Page 2024-01-03
2859845 - ETPRO PHISHING Darcula Phish Landing Page 2024-01-29
2060401 - ET PHISHING Darcula Credential Phish Socket Response 2025-02-27
2060402 - ET PHISHING Darcula Credential Phish Landing Page M1 2025-02-27
2060403 - ET PHISHING Darcula Credential Phish Landing Page M2 2025-02-27
IOC examples
|
Indicator |
Description |
First Seen |
|
hxxps://zjkso[.]cn/QJSmxXOQ/ |
Example CoGUI Phishing Landing Page, SBI Branded |
28 April 2025 |
|
hxxps://uhlkg[.]cn/HJmOkggh |
Example CoGUI Phishing Landing Page, Rakuten Branded |
16 April 2025 |
|
hxxps://kzongfd[.]bo5wfb0f9[.]top/Kfade |
Example CoGUI Phishing Landing Page, Amazon Branded |
24 March 2025 |
|
hxxps://evrryday[.]com/paypay-login-ne-jp |
Example CoGUI Phishing Landing Page, PayPay Branded |
10 March 2025 |
|
hxxps://ezdrivema[.]com-kpy[.]win/I/ |
Example Darcula, Phish Landing Page, EZ DriveMA Branded
|
URLScan .IO
Submission: On March 01 via manual (March 1st 2025, 3:43:24 am UTC) from US — Scanned from PT
|
|
hxxps://sunpass[.]com-tyjr[.]cc/pay/ |
Example Darcula, Phish Landing Page, SunPass Branded
|
URLScan .IO
Submission: On April 10 via api (April 10th 2025, 10:04:25 pm UTC) from US — Scanned from NL |
|
hxxps://etcady[.]xin/pay/
|
Example Darcula, Phish Landing Page, TxTag Branded
|
URLScan .IO
Submission: On April 09 via api (April 9th 2025, 9:54:38 pm UTC) from US — Scanned from US
|











