What happened
Proofpoint researchers have identified an uptick in campaigns and malicious domains impersonating tax agencies and related financial organizations. This activity aligns with the general increase in tax-related content our researchers typically observe every year from December through April, especially as tax deadlines in the United Kingdom and United States are top of mind for businesses.
Generally, phishing lures leveraging tax themes impersonate government agencies or financial services organizations that users would engage with to file taxes or submit business relevant documentation.
UK targeted phishing
Proofpoint has observed multiple campaigns impersonating HM Revenue & Customs (HMRC). Attackers will use branding and language related to HMRC in phishing lures in an attempt to convince users the email is legitimate.
In one campaign that began on 12 January 2025, the threat actor used “account update” lures impersonating HMRC.
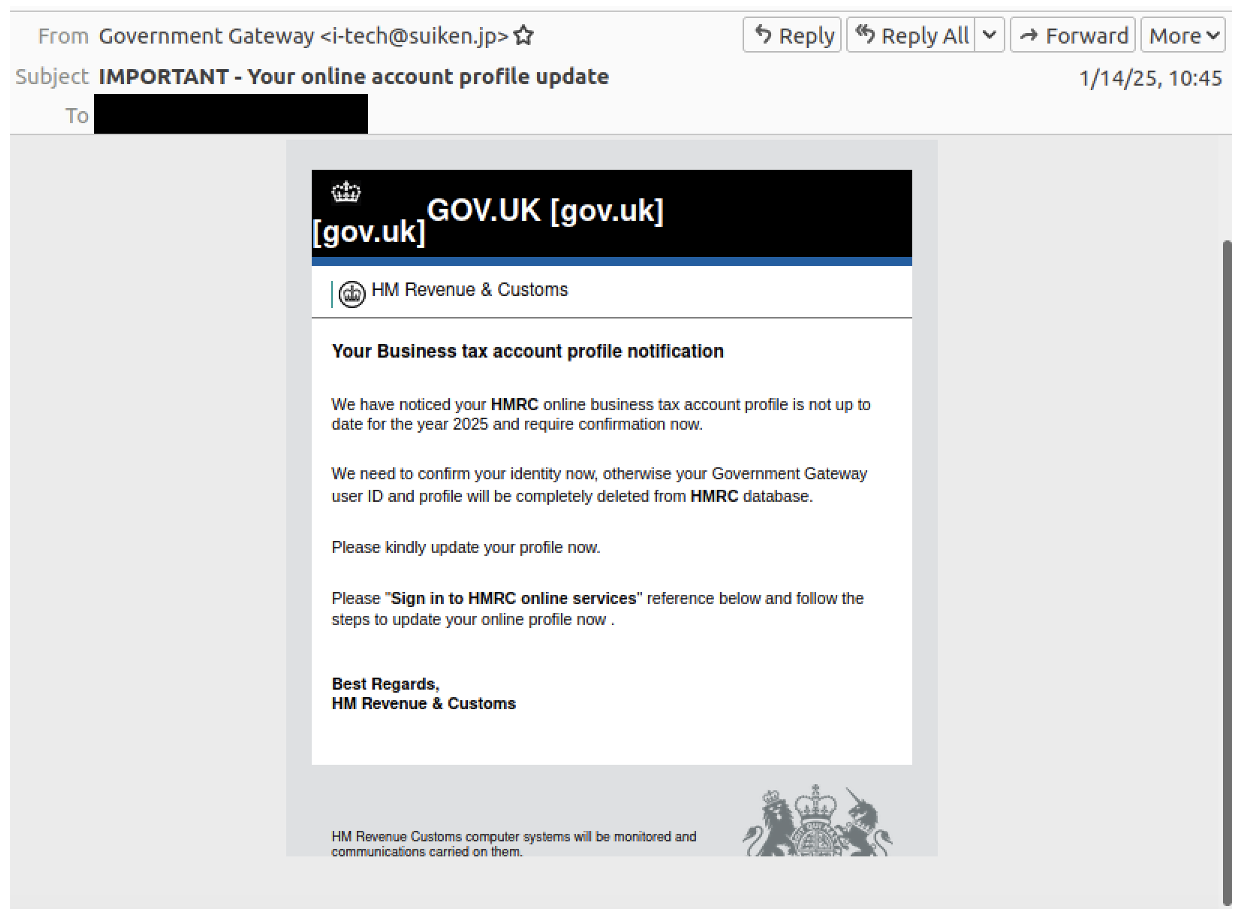
HMRC lure impersonating the agency and distributing credential phishing.
These messages contained URLs leading to actor-controlled credential harvesting websites designed to capture usernames and passwords.
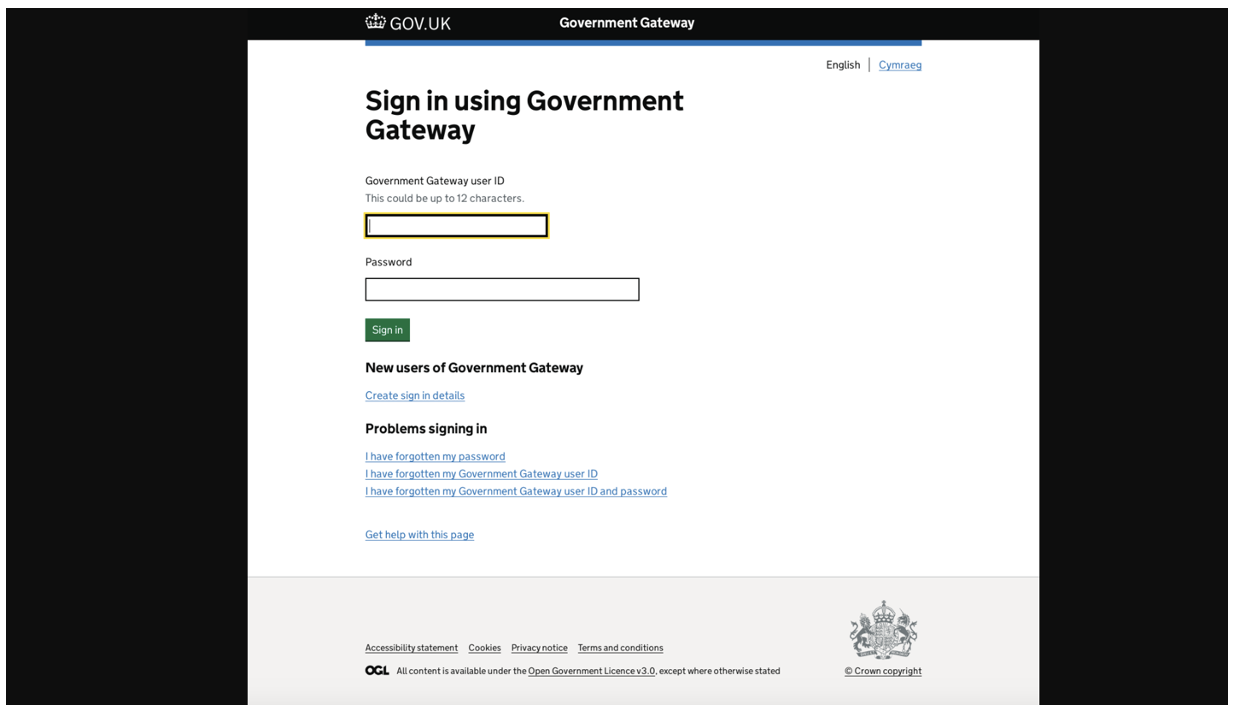
HMRC impersonated website.
The websites impersonated HMRC in an attempt to steal personal information that could be used for fraudulent activity. This campaign included a small number of messages impacting multiple organizations in the UK.
HMRC maintains a list of common phishing and scam lures to educate users on the ways attackers abuse the brand for social engineering purposes.
U.S. targeted phishing
Proofpoint’s Takedown team has observed hundreds of malicious tax-themed domains used in email campaigns in the first few weeks of January 2025. These domains impersonate legitimate companies, applications, and services that are related to accounting, tax filing, and payments. This infrastructure can be used in phishing and malware campaigns targeting organizations with lure content also impersonating these tax related companies.
But not all campaigns leverage lookalike or impersonated domains. On 16 January 2025, Proofpoint identified a campaign impersonating Intuit, but the email sender and phishing infrastructure was generic, with only the path portion of the URL indicating it was a tax-themed campaign.
For example, emails purported to be from Intuit:
From: Intuit QuickBooks <work@secure[.]net>
Subject: Your Tax file Form was rejected
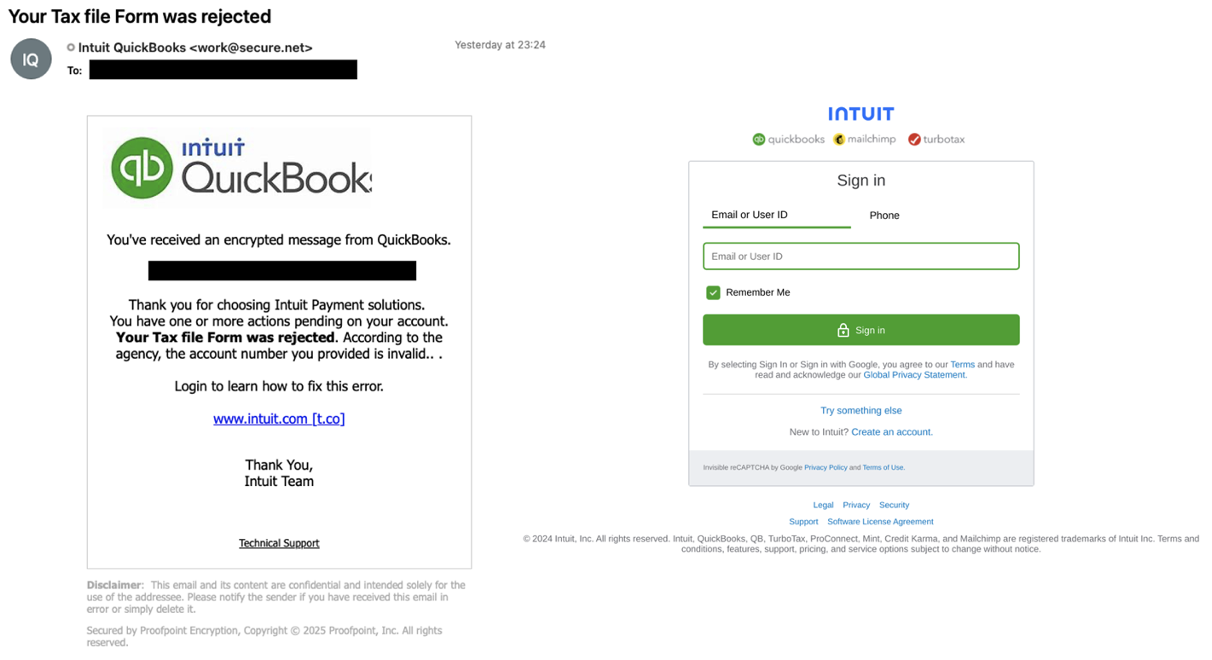
Email impersonating Intuit (left); credential phishing landing page (right).
Emails contained URLs to a fake Intuit authentication page designed to harvest user credentials. In this case, the path portion of the phishing URL indicated brand abuse, in addition to the website impersonating the company (for example: hxxps://fotolap[.]com/.wp-admin/cgi-/intuit/inuit4//). This campaign included over 40,000 messages impacting over 2,000 organizations.
Proofpoint regularly identifies activity impersonating U.S. tax agencies and related organizations, and this activity typically increases in the first quarter of the year.
Swiss targeted fraud
While tax seasons around the world are prime timely themes for threat actors, tax-related lures are often used by threat actors even outside of filing seasons. For example, on 18 December 2024, Proofpoint identified a fraud campaign targeting Swiss organizations.
Messages purported to be federal tax payment reminders and impersonated the Federal Tax Administration. These messages contained URLs leading to a legitimate Revolut payment page, asking users to send a payment via credit card. Proofpoint researchers believe this was not an attack to harvest credit card details, but to get users to pay to an adversary-owned or controlled Revolut account.
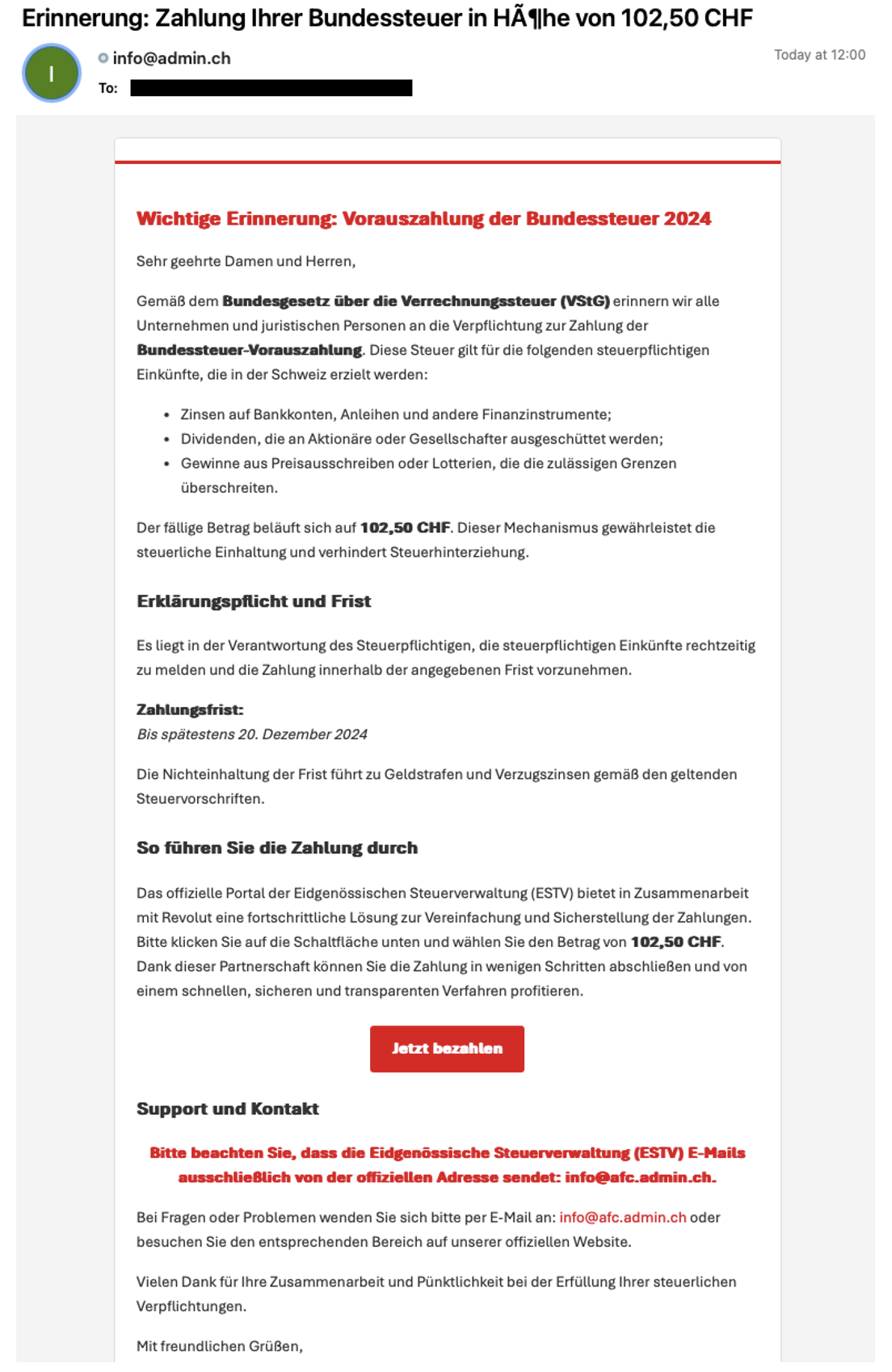
Email lure prompting users to pay into a suspected fraudulent/abused Revolut account.
The message lure told the recipient about a law that allegedly required recipients to pay their tax duties ahead of time. The recipient was requested to make a payment for CHF 102.50 before 20 December 2024. If the payment was not made, the mail threatened fees and additional interest on the payment. The email then continued and told the recipient (fraudulently) that the Swiss Tax Agency partnered with Revolut to conveniently make the payment.
Australia targeted phishing
Australian government-themed phishing is common across the landscape throughout the year, and Proofpoint researchers regularly identify campaigns impersonating myGov, the Australian government services portal.
In a campaign that began on 03 January 2025, messages impersonated myGov with subjects related to government notices or tax updates.
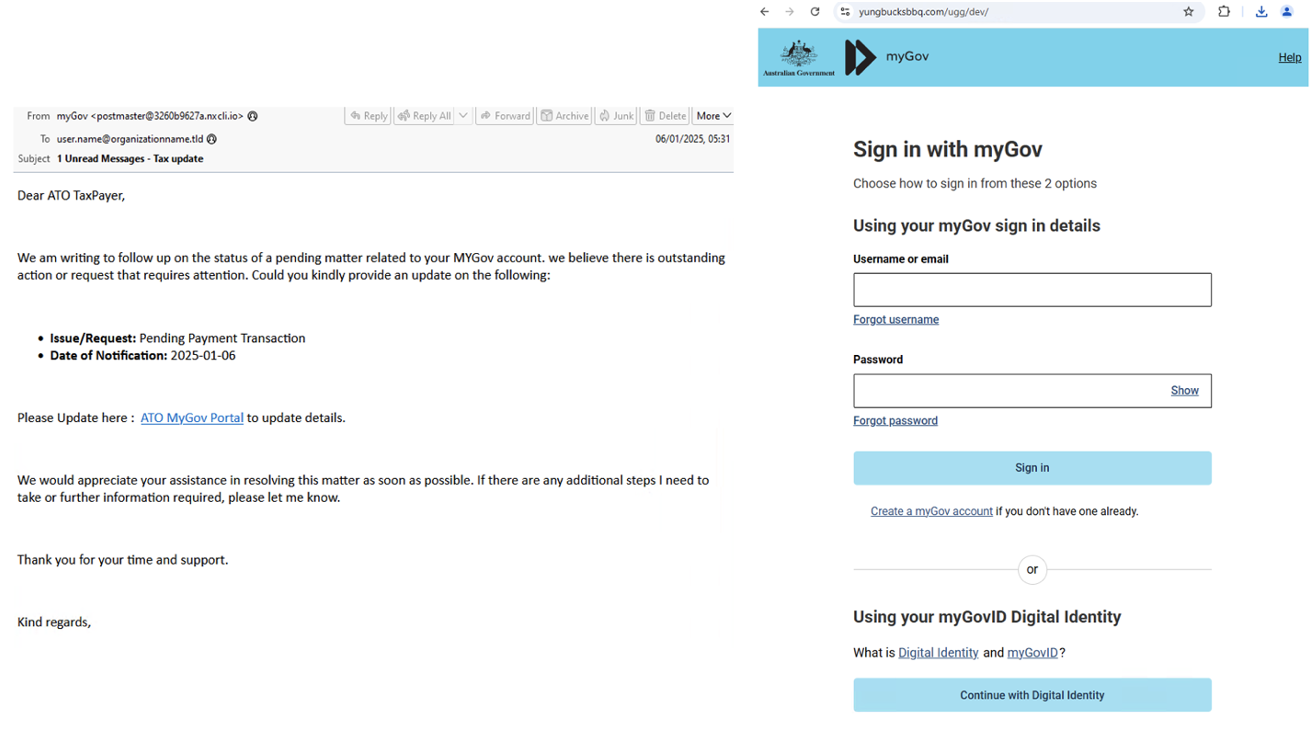
Phishing email impersonating myGov (left); phishing landing page (right).
These messages contained URLs linking to a website that spoofed the myGov portal and was designed to steal user information. The website was protected by Nginx-Lua-Anti-DDoS allowing partial evasion to automated browsing. In addition to usernames and passwords, the website attempted to steal multifactor authentication (MFA) details, and answers to security questions.
Earlier in January, the Australian Taxation Office issued scam warnings for malicious actors conducting phishing attacks impersonating myGov, especially using QR codes.
Tax themed mails deliver malware
While the majority of observed tax-themed campaigns are related to credential phishing, threat actors also use such themes to deliver malware. For example, on 16 January 2025, Proofpoint identified a campaign impersonating a tax software solutions organization to deliver two different malware payloads.
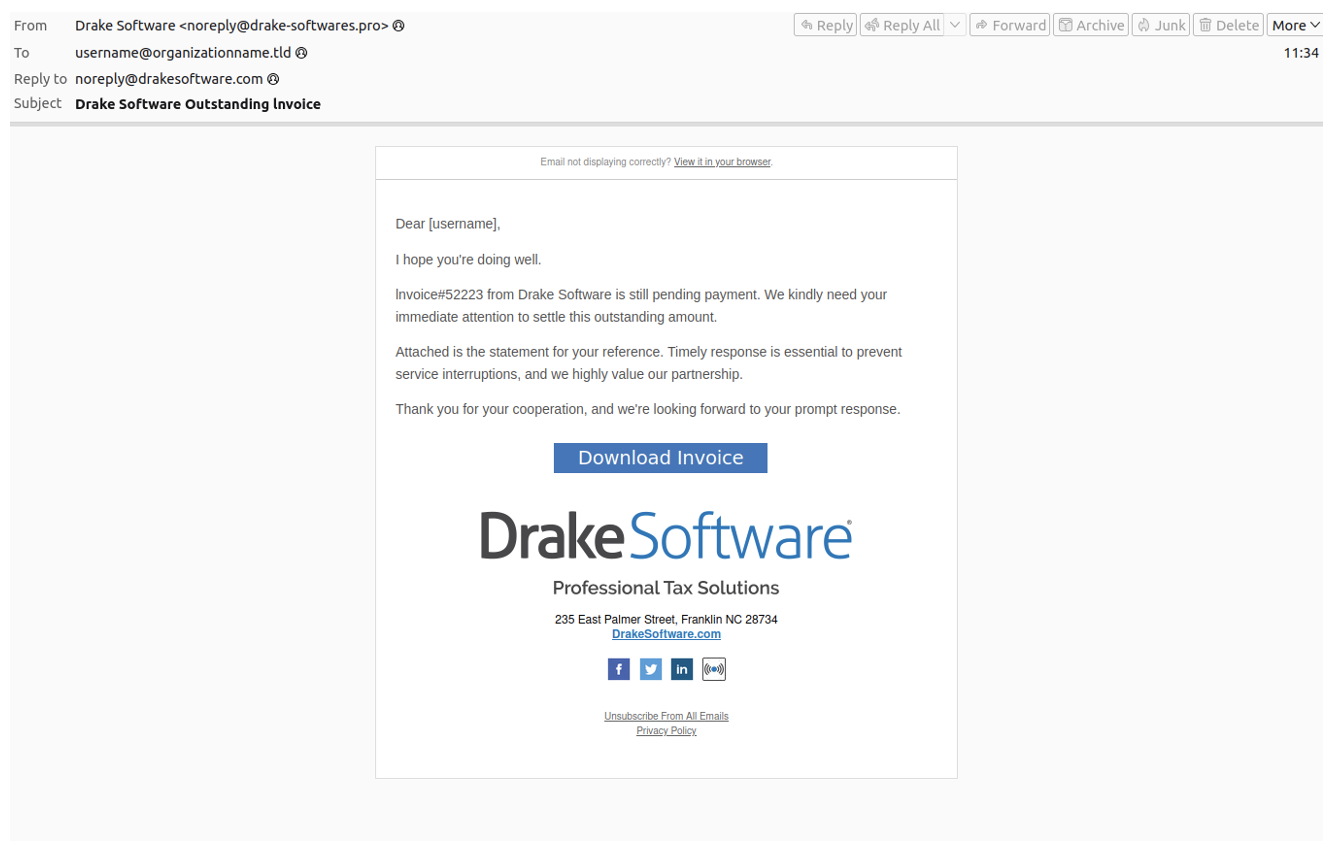
Malicious email impersonating tax software.
These messages contained URLs leading to a download of a JavaScript file hosted on Microsoft Azure. The JavaScript called PowerShell to run a remote PowerShell script. This PowerShell script ran Rhadamanthys malware. Rhadamanthys was then observed to download and run zgRAT. This campaign aligned with activity third-party researchers attribute to a threat actor known as Aggah.
Proofpoint has also recently observed multiple other unrelated malicious campaigns impersonating tax agencies and related software to deliver malware payloads including MetaStealer, XWorm, AsyncRAT, and VenomRAT.
Why it matters
Tax lures are commonly used by threat actors, especially around filing seasons, as people leverage various applications and services to collate and file important business and personal finance information. Such lures can be convincing to recipients who are either expecting communications from authoritative organizations, or would be concerned and worried by receiving an email suggesting they will have fines or fees for incorrectly submitting information. Organizations should educate users about the techniques and lures commonly abused by threat actors.
Example indicators of compromise
|
Indicator |
Description |
First Seen |
|
hxxps://t[.]co/DL9vqURq7G |
Phishing URL in Email |
16 January 2025 |
|
hxxps://clearlivate[.]com/xxx/rest[.]html |
Phishing URL |
16 January 2025 |
|
hxxps://pub-cbdc9a06673740a6aae9a5c61db6da30[.]r2[.]dev/indexqu[.]html |
Phishing URL |
16 January 2025 |
|
hxxps://fotolap[.]com/[.]wp-admin/cgi-/intuit/inuit4// |
Phishing URL |
16 January 2025 |
|
hxxps://fotolap[.]com/[.]wp-admin/cgi-/intuit/inuit4//res[.]php |
Credential Receiver |
16 January 2025 |
|
hxxps://fotolap[.]com/[.]wp-admin/cgi-/intuit/inuit4//panel[.]php |
Credential Receiver |
16 January 2025 |
|
hxxps://drakesoftware[.]blob[.]core[.]windows[.]net/drakesoftware/ |
Example URL Delivering Rhadamanthys |
16 January 2025 |
|
hxxps://cpa01-14-25[.]blogspot[.]com///////nunuchabutra[.]pdf |
PowerShell Redirect |
16 January 2025 |
|
hxxps://cpa01-14-25[.]blogspot[.]com/atom[.]xml |
PowerShell Redirect |
16 January 2025 |
|
hxxps://bitbucket[.]org/!api/2[.]0/snippets/nippleschusu/o7rE59/ |
PowerShell Redirect |
16 January 2025 |
|
hxxps://185[.]208[.]159[.]170:8654 |
Rhadamanthys C2 |
16 January 2025 |
|
hxxps://7fasl[.]ir/gov/ |
HMRC Phishing URL |
12 January 2025 |
|
hxxps://a-line[.]top/admin/gov/ |
HMRC Phishing URL |
12 January 2025 |
|
hxxps://www[.]houzhenkun[.]com/gov/ |
HMRC Phishing URL |
12 January 2025 |
|
hxxps://yungbucksbbq[.]com/wen/approve/ |
myGov Phishing Landing Page |
3 January 2025 |
|
hxxps://revolut[.]me/swisstaxadm |
Fraudulent Revolut URL |
18 December 2024 |











