Proofpoint researchers continue to monitor the latest news and reports around the global Coronavirus outbreak for malicious activity. Aside from the overall increase in activity that the team has observed (which has reached hundreds of thousands of messages), the most notable developments we’ve seen are attacks that leverage conspiracy theory-based fears around purported unreleased cures for Coronavirus and campaigns that abuse perceived legitimate sources of health information to manipulate users.
In this latest round of campaigns, attackers have expanded the malware used in their Coronavirus attacks to include not just Emotet and the AZORult information stealer, but also the AgentTesla Keylogger and the NanoCore RAT -- all of which can steal personal information, including financial information. Attackers have also expanded their attacks to include credential theft. Our researchers have seen fake Office 365, Adobe, and DocuSign sites meant to steal credentials linked to Coronavirus-themed emails.
We have previously written about Coronavirus-themed attacks centered on concerns around economic disruptions in light of the outbreak, specifically around shipping. This trend is continuing and has expanded to include manufacturing as well.
Consistent with this level of tailoring and focus on economic concerns, we are also seeing dedicated attacks against construction, education, energy, healthcare, industry, manufacturing, retail, and transportation companies.
Geographically, in addition to previous targeting against Japan and the United States, we’re also seeing attacks focusing on Australia and Italy, the latter in Italian-language lures.
Campaign Examples
Threat actors have launched a campaign using an email lure that stokes conspiracy theory fears that there is cure for Coronavirus that isn’t being shared. In Figure 1 you can see that the email claims there is a cure being hidden by government entities because the virus is being used as a bioweapon. It then urges the recipient to receive further information on the “cure” by clicking on the link provided in the email.
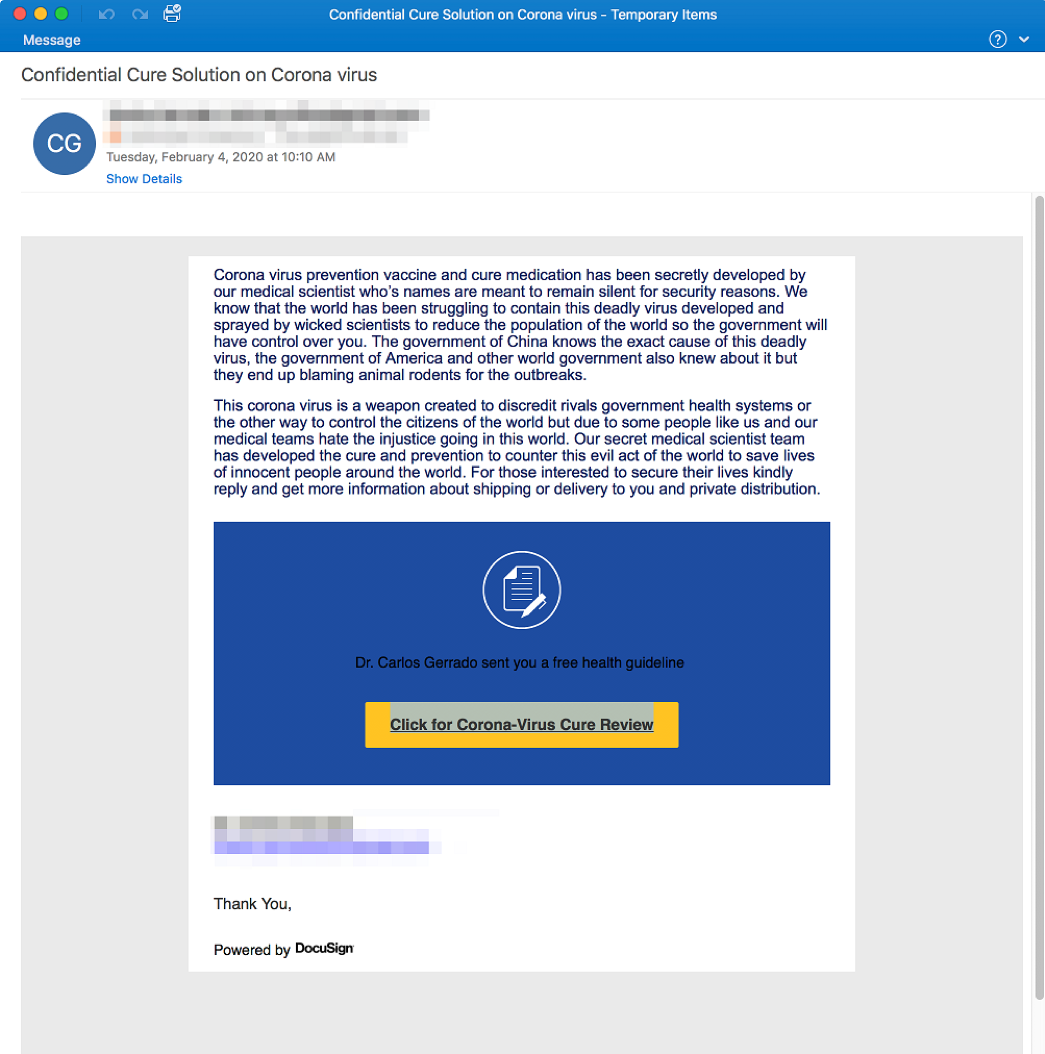
Figure 1 Coronavirus “Secret Cure” Lure
If the recipient clicks on the link, they are taken to a fake DocuSign website where they’re told they need to enter credentials to get the information.
Attackers are also subverting internal businesses’ credibility in their attacks. We have seen a campaign that uses a Coronavirus-themed email that is designed to look like an internal email from the company’s president to all employees shown in Figure 2.
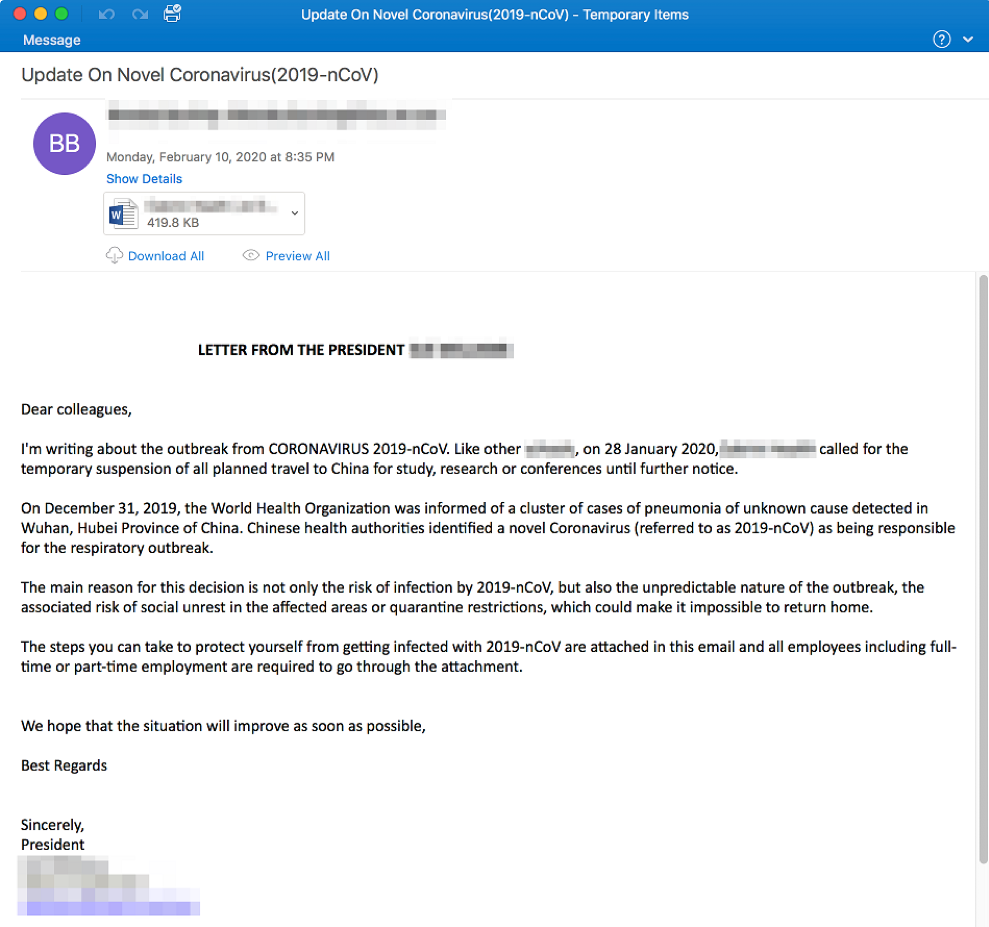
Figure 2 Fake Internal Email from an Organization’s President on Coronavirus
This email is extremely well-crafted and lists the business’ president’s correct name. The messages contain a Microsoft Word attachment with an embedded URL that leads to a fake Microsoft Office website to enter credentials. Once the credentials are entered, the user is then redirected to the legitimate World Health Organization Coronavirus information site, making the phishing transaction seem legitimate.
In looking to subvert and abuse legitimate sources of information, in Figure 3, we see attackers abusing the World Health Organization (WHO) name to distribute an attachment that will install the AgentTesla Keylogger.
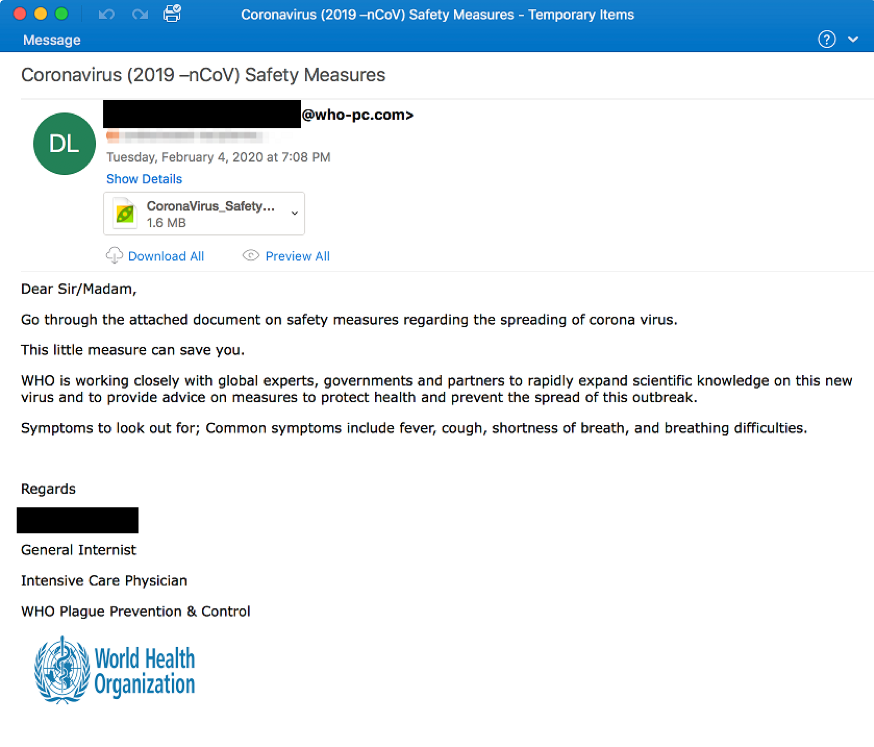
Figure 3 Fake World Health Organization Lure
Once installed, this malware will record all keystrokes and send it to the attackers, a tactic that can give access to online banking and financial accounts.
In Figure 4 we see an email claiming to be from Australia HealthCare, a fake but plausible name for a national healthcare organization, that claims to share Coronavirus prevention tips.
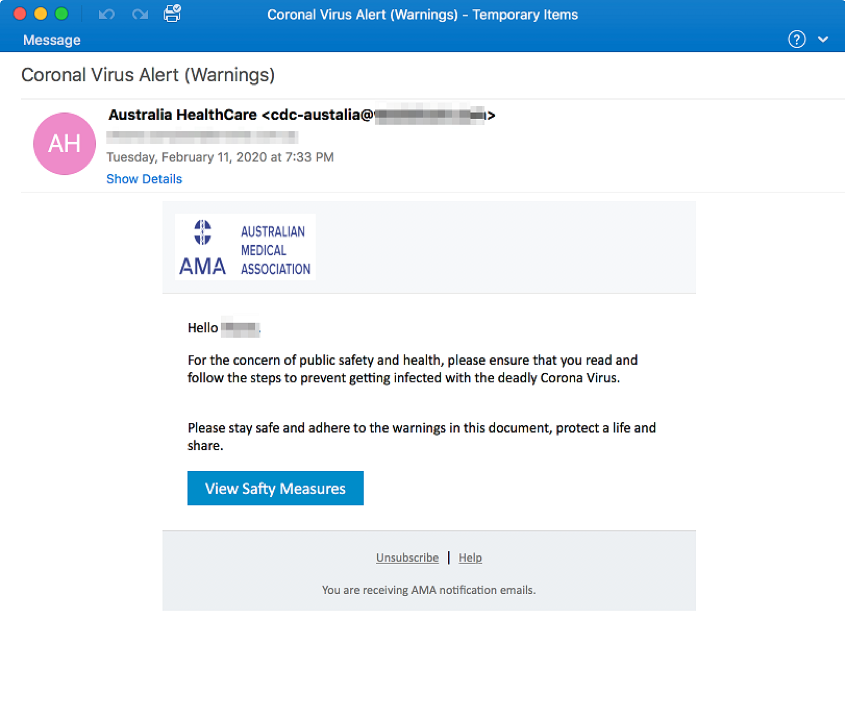
Figure 4 "Australia HealthCare" Lure
In this case, when the user clicks the link, they are taken to a fake Adobe website to enter credentials.
Lastly, attackers have expanded their targeting of economic concerns to include manufacturing as well as shipping. Figure 5 shows an example we’ve seen uses the subject "Coronavirus Update: China Operations" and includes an attachment titled “"Factory Contacts and Office Resumption”, clearly meant to appeal to concerns around possible shutdowns in manufacturing in China due to the Coronavirus outbreak.
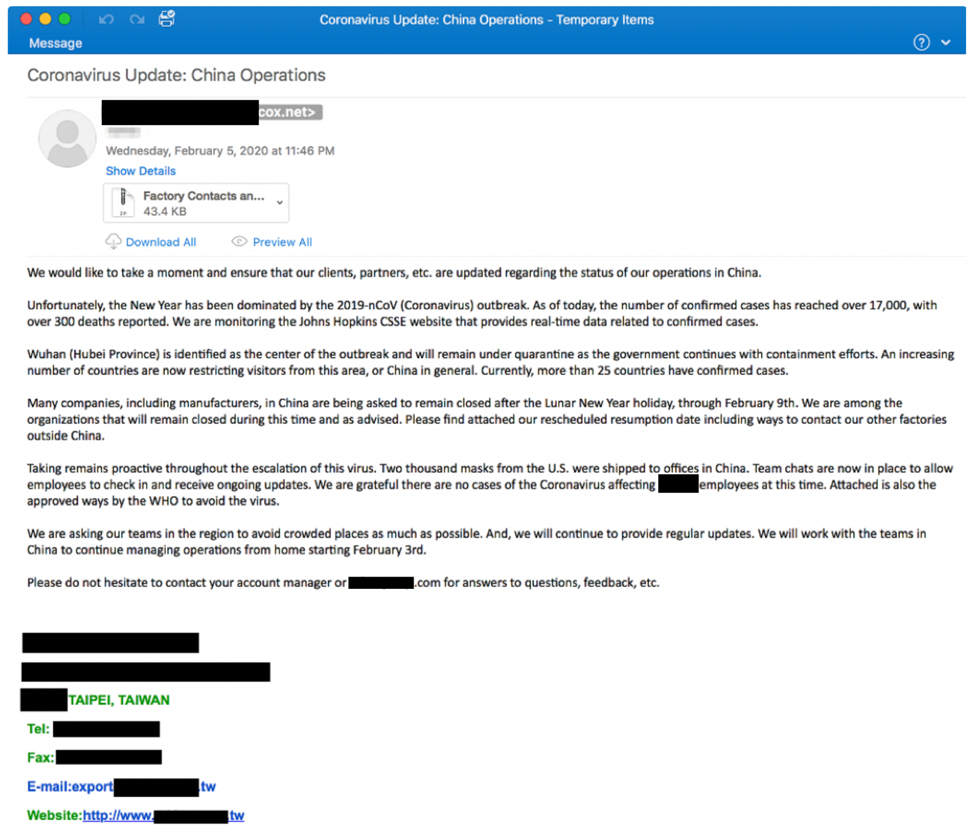
Figure 5 Coronavirus Impact on China Operations Lure
We’ve seen this email targeting manufacturing, retail, and transportation companies primarily: all companies that have reasonable concerns around manufacturing disruptions in China. The attachment tries to install NanoCore RAT, a remote access Trojan that can give the attacker full control over the compromised system. We recently saw this malware being used heavily in attacks against German manufacturing.
Overall, these latest examples serve as a reminder that users should be watchful and exercise caution where Coronavirus-themed emails and websites are concerned. Proofpoint will continue to monitor this situation and share updates as available. We’ll be posting future Coronavirus campaigns and insights on our threat research Twitter account: https://twitter.com/threatinsight

