Recently, the Proofpoint Threat Insight team observed a medium-volume email campaign using fake invoices as lures.
In this recent campaign, our researchers identified two elements that are particularly noteworthy.
First, while this campaign targeted many industries, our researchers found that attackers were targeting manufacturing significantly more than any other industry. In particular, our researchers saw a month-long campaign in October targeting manufacturing in Germany.
Second, the goal of these attacks was to plant a remote access Trojan (RAT) known as “NanoCore” on compromised systems. NanoCore is a malware that is marketed on underground forums for the price of US$19.99. This low price combined with a design focused on ease-of-use means that attackers can cheaply get up and running with get NanoCore and quickly begin using it in malware campaigns. This has contributed to NanoCore’s prevalence for many years amongst numerous threat actors even before we began observing more widespread RAT distribution over the last 18 months.
Moreover, manufacturing, with its complex supply chains and frequently sprawling network infrastructure, is an attractive and potentially lucrative industry at risk of infection and exploitation via Nanocore and other malware.
Attack Overview
While this attack campaign was not exclusively focused on manufacturing, our researchers found that manufacturing was the preferred target in this campaign by a large margin.
This campaign began with the target receiving a fake invoice lure, like that shown in Figure 1.

Figure 1: NanoCore Invoice Lure
In Figure 2 you can see a NanoCore invoice lure in German.
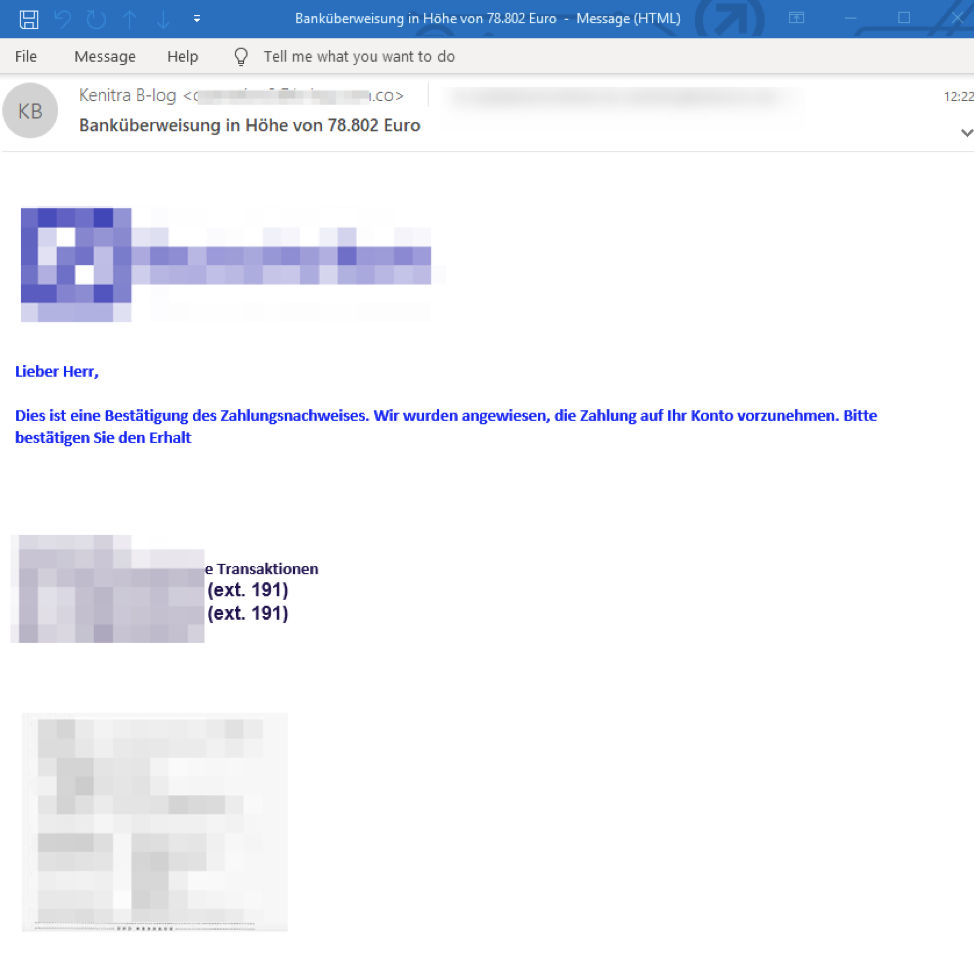
Figure 2: NanoCore Lure in German
The attacks our researchers saw used a combination of both malicious attachments and URLs. Malicious attachments contained a compressed executable (using “.Z” extensions) while malicious links would lead the recipient to download the malware hosted on onedrive.live.com.
The attack sequence is shown in Figure 3.
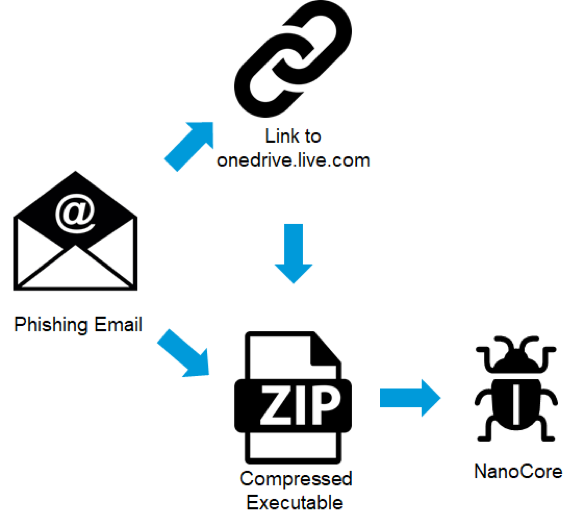
Figure 3: Attack Sequence
Once the user either clicks the link and downloads the executable or runs the attachment, the NanoCore RAT would then be installed on their system.
As a remote access Trojan, once NanoCore is installed, its capabilities include the ability to perform live and offline keylogging, run arbitrary shell commands, take screenshots of desktops and webcams, and upload and/or download arbitrary files. Basically, NanoCore gives the attacker complete control of the system, usually without the victim’s knowledge, and an ongoing presence on the network.
NanoCore Overview
NanoCore is not unique in its capabilities; these capabilities are common across most RATs. One thing that differentiates NanoCore, however, is both its low cost and its ease of use.
Proofpoint’s Threat Insight team has found NanoCore advertised for sale on underground forums for as little as US$19.99, a relatively low price for crimeware.
In addition to its low cost, NanoCore provides relative ease of use. Figure 4 shows the NanoCore control panel. In it you can see the variety of tools and capabilities that NanoCore provides to the attacker once a system is compromised.
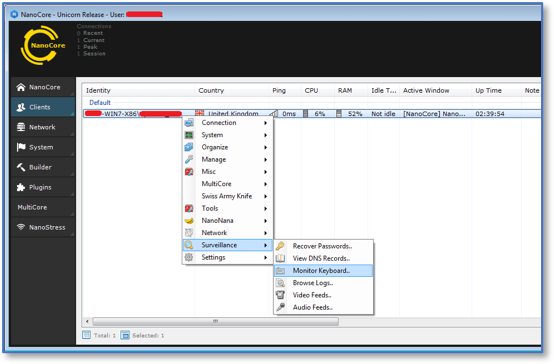
Figure 4 NanoCore Control Panel
NanoCore’s Threat to Manufacturing Today
NanoCore’s low cost and ease of use have given it staying power in the market. It continues to be used maliciously, giving an attacker a great deal of control and an ongoing presence on a network after a successful attack.
Overall, Proofpoint’s Threat Insight team has been seeing broad trends favoring the use of RATs after successful attacks. This may be because RATs provide an ongoing presence and the greatest flexibility for attackers to capitalize on and exploit compromised systems.
This recent campaign using NanoCore is consistent with that trend.
The fact that attackers are focusing on manufacturing in these attacks should serve as a call to action for businesses in that sector to increase their watchfulness. As we see in these attacks, the use of credible invoices as lures shows that while these attackers aren’t necessarily spending a lot of money for the tools in their attacks, they are bringing a level of business sophistication that needs to be matched with an equal level of vigilance.











