Right now, users who are working from home lack the security of your corporate network. Your VPN does not have the capacity to accommodate everyone working remotely. And some of your employees do not have corporate laptops and are using their personal devices instead. To make matters worse, attackers are exploiting Covid-19 phishing lures to steal your users’ credentials and take over their accounts. These conditions have become commonplace almost overnight as countries and states put in place strict Covid-19 control measures such as “shelter-in-place”.
How Proofpoint Can Help Secure Remote Access to Cloud Applications
Securing remote access to cloud applications and data has never been more important. Proofpoint detects risky access and automates security controls for cloud services. Proofpoint Targeted Attack Protection (TAP) customers can connect their Office 365 and G Suite APIs to monitor for compromised accounts. With TAP, you also gain visibility to other risks such as broadly shared files and third-party (OAuth) apps with overreaching permissions to email, calendar, contacts and files. Click on the cloud icon in TAP to access the module below:
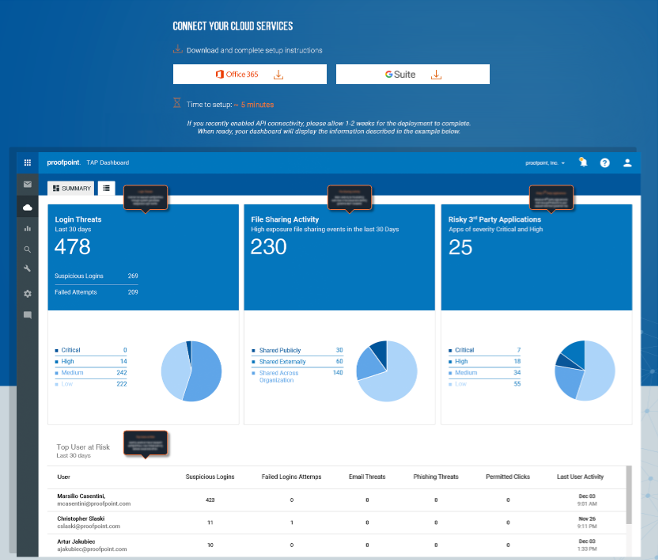
To prevent account takeover, Proofpoint delivers remediation capabilities as well as adaptive access controls. Existing Proofpoint Cloud Account Defense (CAD) and Cloud App Security Broker (CASB) customers can implement adaptive access controls at no additional charge. These controls are delivered via a SAML Gateway, which is easy to implement and integrate with your identity management solution. You can also implement real-time DLP capabilities to strengthen your data security posture. With these capabilities, you can apply risk-based policies based on the user’s role, their device (managed versus unmanaged) and the threat intelligence we have on the user and the attacker. Here are the steps you can take to automate security controls for your cloud accounts and data using Proofpoint CASB.
3 Steps to Configuring Access Policies and Automating Enforcement
Step 1: Automatically Remediate or Block High-Risk Suspicious Logins
When Proofpoint detects a high-risk suspicious login based on threat intelligence and user behavior analytics, you can notify Admin and respond by revoking the cloud session, suspending the user account and/or forcing password change. If you use Office 365 and have a hybrid Active Directory environment, you can enforce these controls with Active Directory on-premises using Threat Response Auto-Pull, Proofpoint’s security orchestration solution, which integrates with Proofpoint CASB.
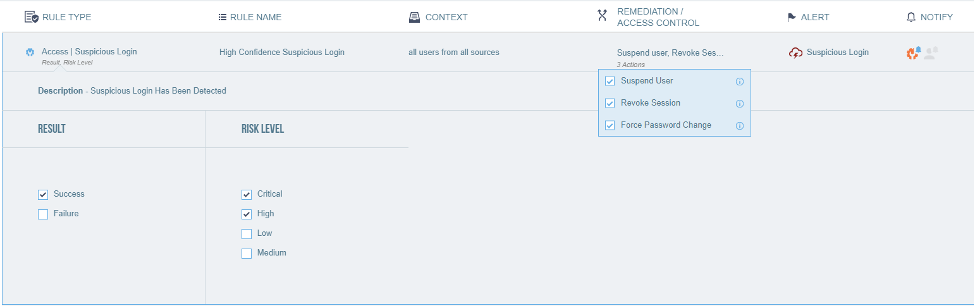
When an attacker’s signature is already known to Proofpoint, you can also prevent such high-risk suspicious logins by using CASB’s adaptive access controls. Proofpoint tracks suspicious logins across tens of millions of accounts and has the best understanding of cloud threats. For example, you can block access to your highly attacked user’s accounts when CASB detects a suspicious login:
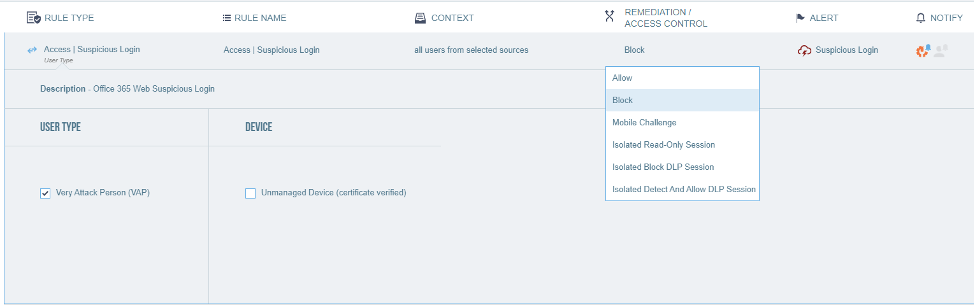
Step 2: Tighten Controls on Remote Users-At-Risk
Just because the cloud enables universal access doesn’t mean you should grant access to everyone. Proofpoint helps you apply adaptive access controls for users who are highly attacked or privileged. For example, if a user is identified as a Very Attacked Person by Proofpoint’s people-centric threat intelligence, you can block their login from a risky IP address such as a Tor server. Proofpoint leverages our own threat intelligence on IP reputation to detect logins from Tor (anonymity network) addresses. Or you can require VIPs (e.g. executives, those with access to privileged information) to multi-factor authenticate (MFA) by mobile challenge if they are logging in from a location outside of their home country. In fact, we recommend that you require your Admins to always use a VPN when remotely accessing cloud apps. You can define IP ranges for your corporate network and VPN and only allow access to an Admin when they are on these approved networks.
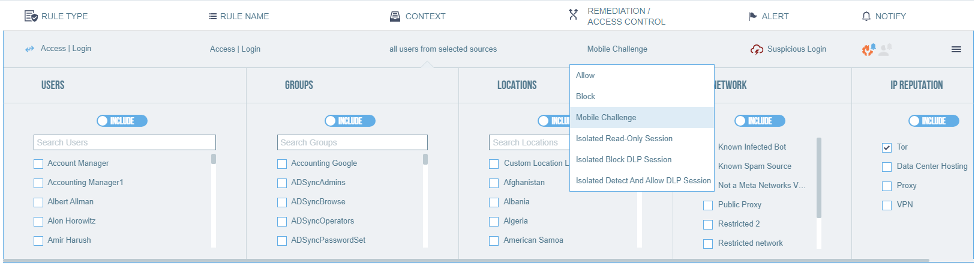
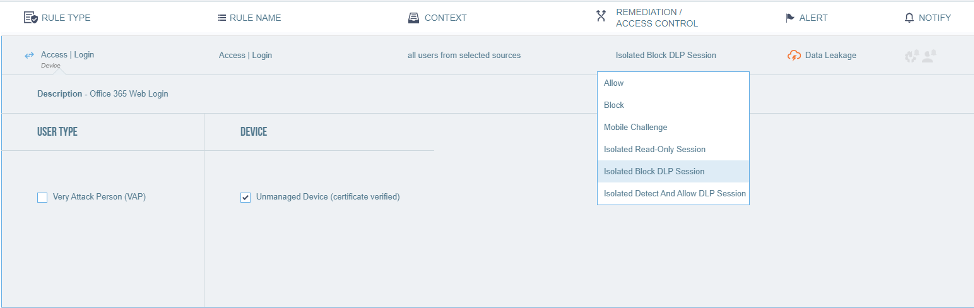
Step 3: Control Access to Data by an Unmanaged Device
Proofpoint CASB detects device certificates, allows you to create data security policies for unmanaged devices and enforces real-time controls via CASB integration with Proofpoint Browser Isolation. For example, if a remote user is off-network and tries to download files to an unmanaged device, you may isolate their web traffic using Proofpoint Browser Isolation and block uploads and downloads while allowing a read-only session. If the user is on the corporate network or the VPN, you can isolate their web traffic, scan files for DLP violations and only block files with sensitive data. You can choose to apply these rules broadly or roll them out at your own pace until you achieve that fine balance of risk versus trust.
Learn More
You can secure remote access to cloud applications by implementing Proofpoint CAD and CASB’s adaptive access controls. You can install and configure the solution in days given our agentless security architecture. If you are interested, contact your Proofpoint account representative.











