On Tuesday, Proofpoint detected a campaign of millions of messages directed primarily at organizations in the US and UK. The campaign employed a straightforward voice message lure with an attachment named “08439801260_20150725_150834.wav.lnk”. (Fig. 1)
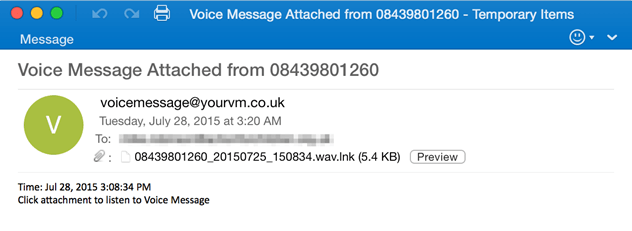
Figure 1: Message with LNK attachment
The use of LNK files to deliver malware in phishing emails is unusual but not unheard of [1], and this campaign caught the eye of at least one other security researcher [2]. In some versions of Windows the “wav.lnk” file was represented with a Windows audio file (WAV) icon, while in others a generic file icon was displayed. (Fig. 2)
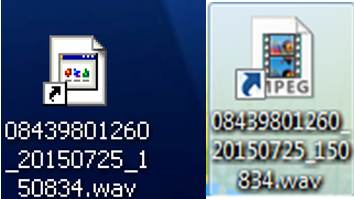
Figure 2: Icon rendering for WAV.LNK file in different versions of Windows
Double-clicking the attachment calls “cmd.exe” to run a series of shell commands. (Fig 3)
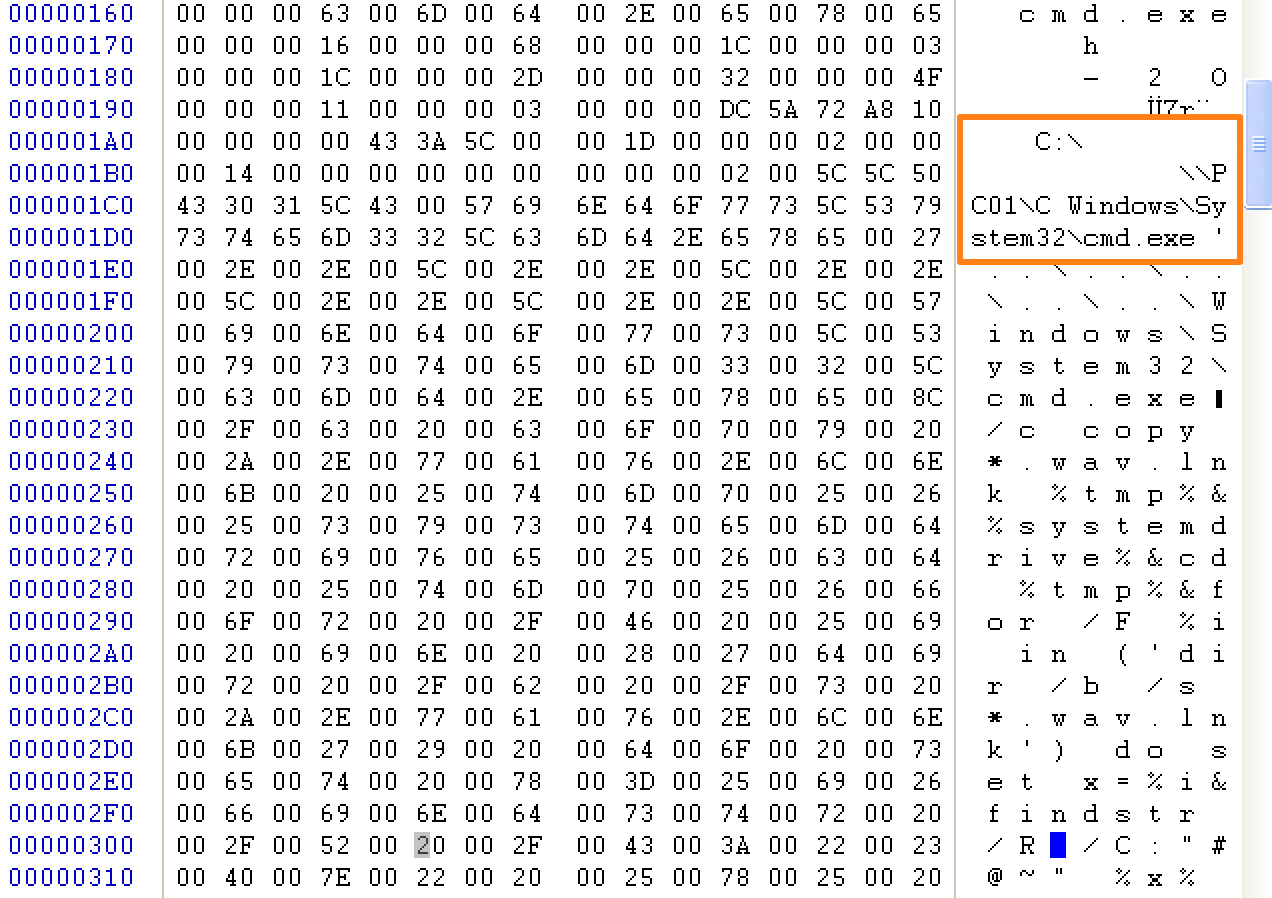
Figure 3: LNK file calling cmd.exe
This copies the LNK file to a temporary directory and extracts out a VBE file from the LNK file (Fig. 4), writes it to disk, then executes it.
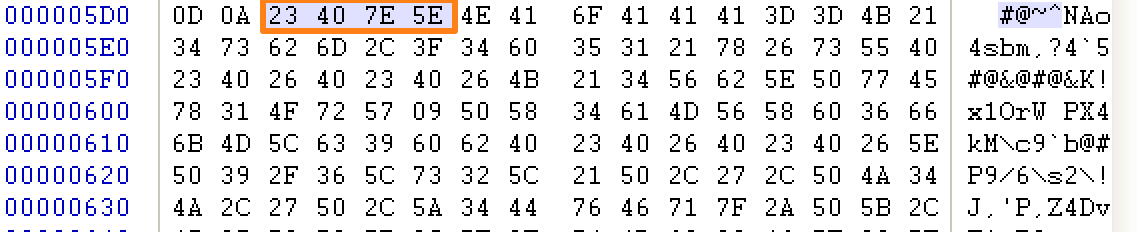
Figure 4: Beginning of VBE file content appended to LNK file
The dynamically generated script file then downloads and executes the Dridex botnet #220 binary from this URL: [hxxp://laurance-primeurs[.]fr/345/wrw.exe].
Despite the size of the campaign, the technique itself was used in a relatively limited manner: only one unique file (i.e., hash) was detected in this campaign, and errors in the scripting resulted a general failure to execute on target systems. (Another recent innovation in the current wave of malicious document attachment campaigns – the use of MIME/OLE formatted documents – began with similar misfires but then went on to become a predominant masking technique [3] [4].) Moreover, some versions of mail client did not display the attachment, replacing it with a warning message that the file was potentially unsafe, and organizations following email security best practices commonly treat LNK files similar to executables (EXE) and strip them from messages before delivery.
Despite these constraints, this campaign showed that the LNK format remains a potentially effective technique, and as a whole demonstrates that threat actors are continuing to innovate and experiment with new delivery and masking techniques in order to stay ahead of adapting defenses.
Indicators of Compromise
URLs called:
[hxxp://laurance-primeurs[.]fr/345/wrw.exe]
Dridex botnet #220 C2 addresses:
93.171.132.5:743
194.58.96.45:4543
31.131.251.33:743
62.210.214.106:448
151.248.123.100:743
References
[1] https://www.trustwave.com/Resources/SpiderLabs-Blog/Lnk-files-in-Email-Malware-Distribution/
[2] https://twitter.com/Techhelplistcom/status/625990539893084162
[3] https://isc.sans.edu/forums/diary/Another+Maldoc+Im+Afraid+So/19699/
[4] https://www.proofpoint.com/us/threat-insight/post/Fleurs-du-malware











