Overview
Credential and financial phishing have been at epidemic levels for years. While email filters and authentication systems have helped turn the tide against phishing actors and create phishing awareness, criminals have turned to social engineering to continue to make money off of these schemes. In particular, many phishers are engaging in two types of attacks that rely on social engineering. One is business email compromise (BEC). In BEC attacks, threat actors target enterprise users in the finance or executive teams with emails and out-of-band communications designed to trick them into wiring large amounts of money to incorrect bank accounts or sending large amounts of personal information to spoofed email accounts. The other technique is part of a broader trend that we have observed gaining traction in late 2016 and into 2017: SMS phishing.
SMS phishing, though not new, is on the rise, targeting consumers and enterprises alike and actors are introducing new techniques to increase its effectiveness. Previously, SMS phishing generally involved a text message with a single link to a fake account login page. Figures 1 and 2 show a ‘traditional’ message and mobile phishing template designed to capture login information for a cellular provider account.
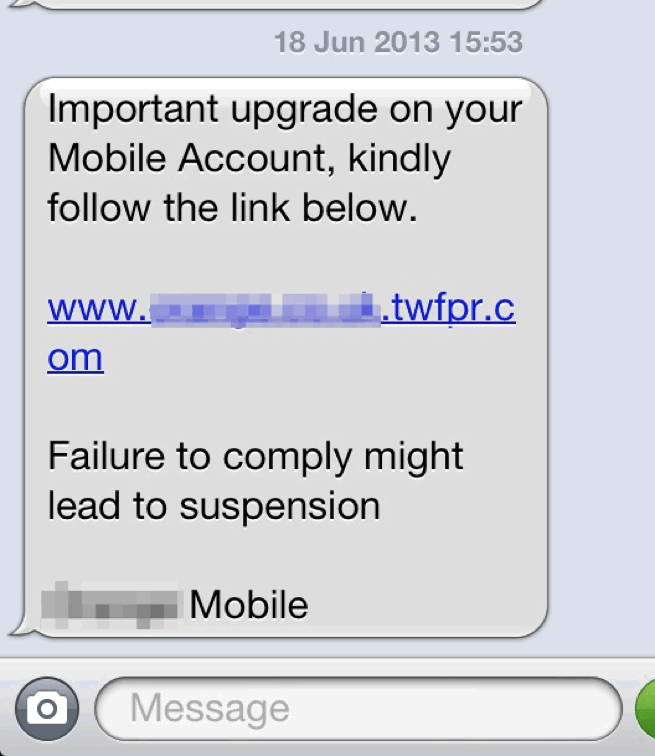
Figure 1: An older-style SMS phishing message
While this message does employ some basic social engineering, the associated phishing template is fairly basic in the information it attempts to collect (Figure 2).
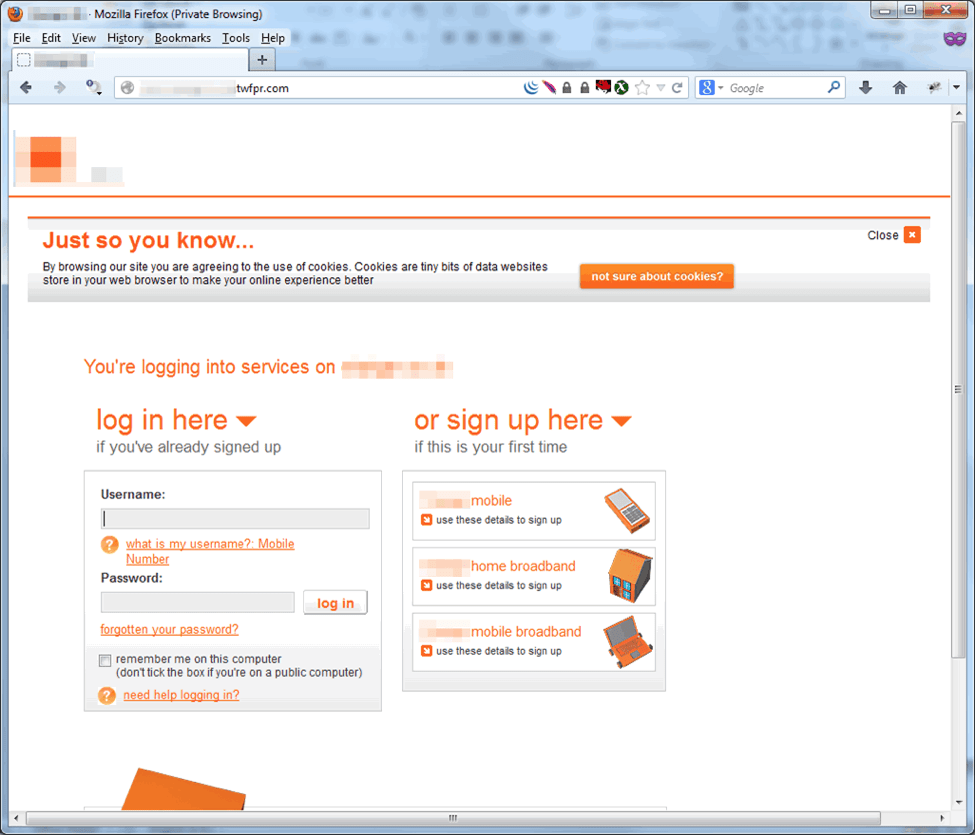
Figure 2: Fake login page for cellular provider phishing scheme; this template only captures the login information in contrast to new attacks designed to harvest more data
Because there are no commercially available SMS inbound filtering products as there are with email, attackers have discovered that sending SMS messages can be highly effective at tricking users. This gap in defenses is compounded by the fact that the small screens of mobile devices make it difficult to determine if websites are legitimate or fake. As the analysis below demonstrates, attackers are also adding new techniques and twists to better leverage the potential effectiveness of SMS phishing schemes beyond the basic approaches shown above.
Analysis
Over the course of a recent week, several Proofpoint researchers received and investigated SMS-based phishing messages purporting to be from a major US bank. Examples of the messages with the bank name and branding redacted appear below; the messages were received from both an email addresses and a phone number and bore legitimate-looking links.
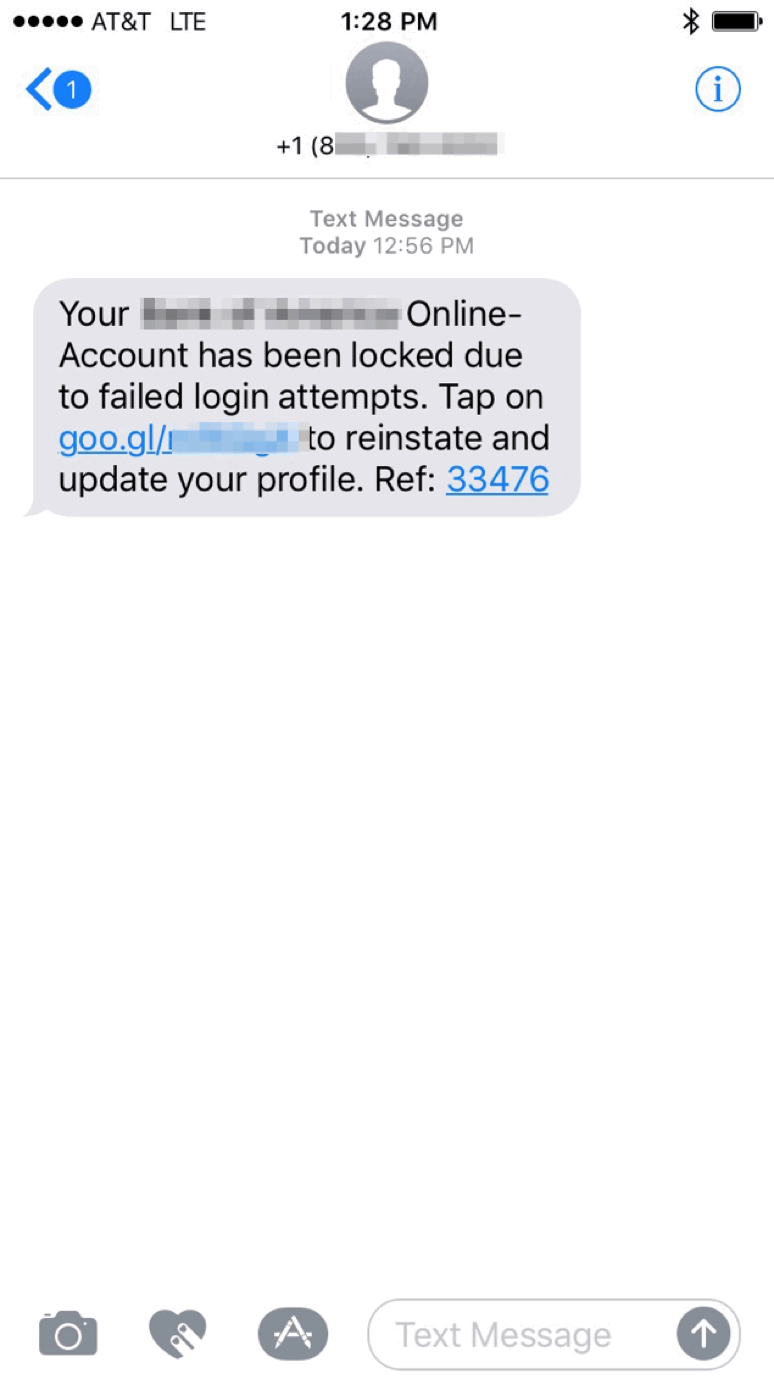
Figure 3: SMS phishing message originating from a phone number
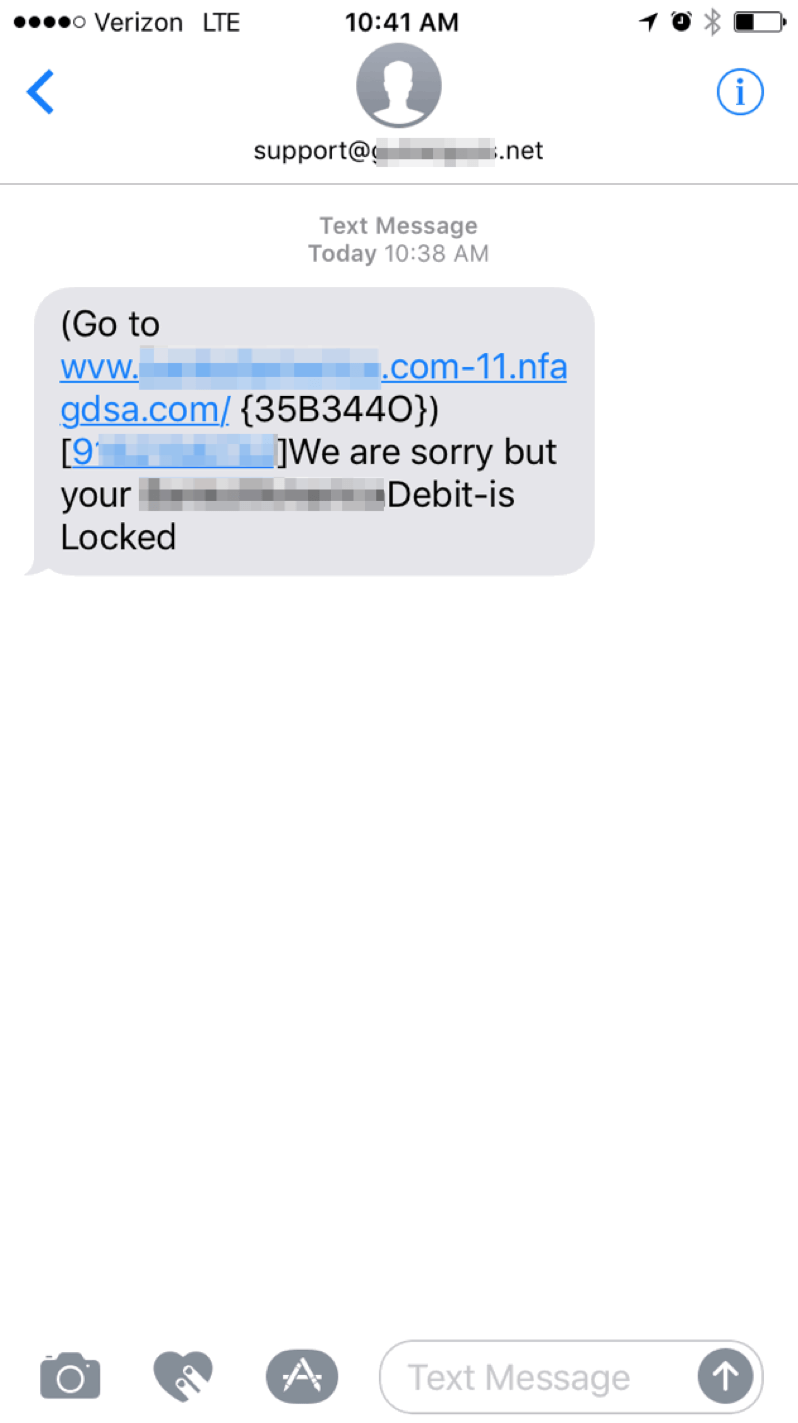
Figure 4: SMS phishing message originating from an email address
Instead of taking users directly to a phishing form or site, the links shown in Figures 3 and 4 initially take users to an image (Figure 5). This technique defeats many phishing filters because the brand name is an image and therefore not machine parseable. After six seconds, victims are automatically redirected to the real phishing site.
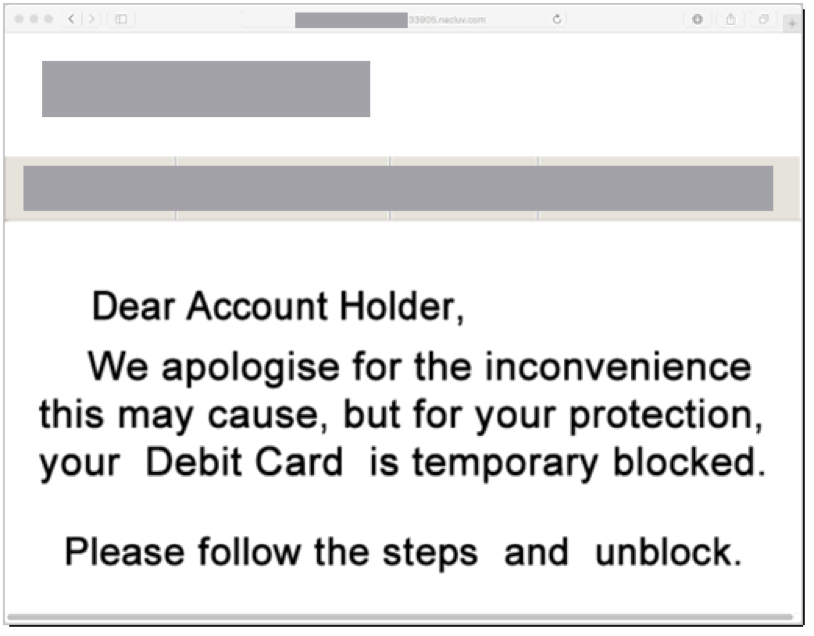
Figure 5: Image initially linked from phishing messages with stolen branding redacted
The phishers then present a clever three-step verification that begins with the victim's phone number and zip code instead of more "traditional" phishing sites that begin by asking for passwords and usernames.
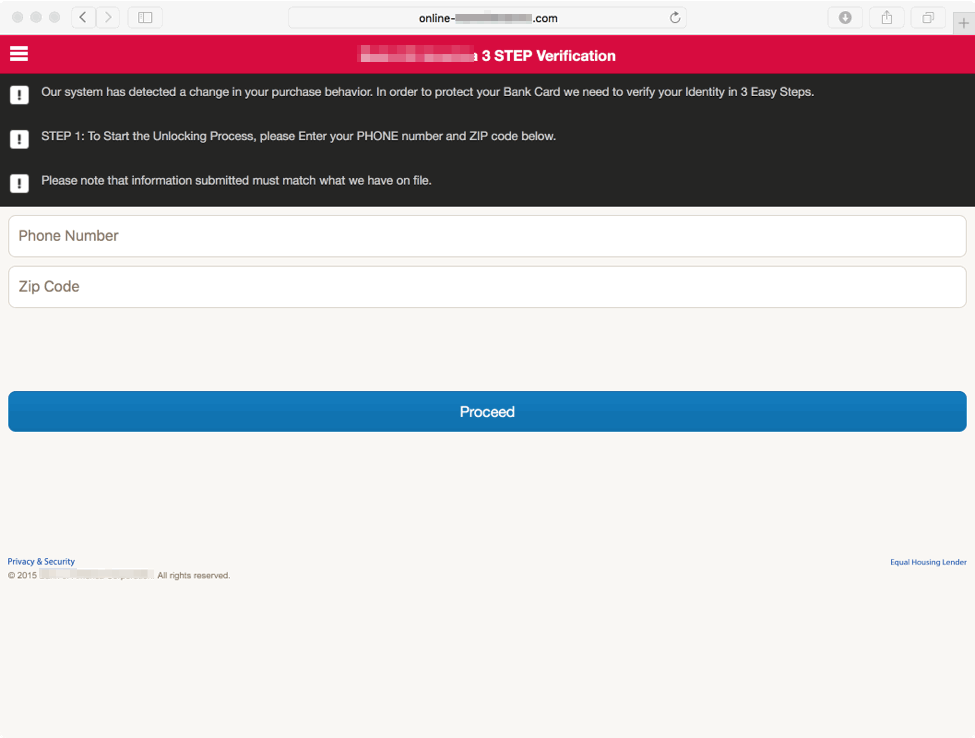
Figure 6: Step 1 of the fake verification process that begins by asking for a phone number and zip code; the link has been redacted but uses a typosquatted domain for the bank.
Victims are then prompted to enter an email address in the next step of the fake verification process. If recipients enter a Gmail address, they are presented with a bogus Gmail login page (Figure 7), creating what appears to be a trustworthy site and account verification transaction. If victims enter their password, the attackers gain control of the Gmail account and can reset passwords for any other services attached to the email address.
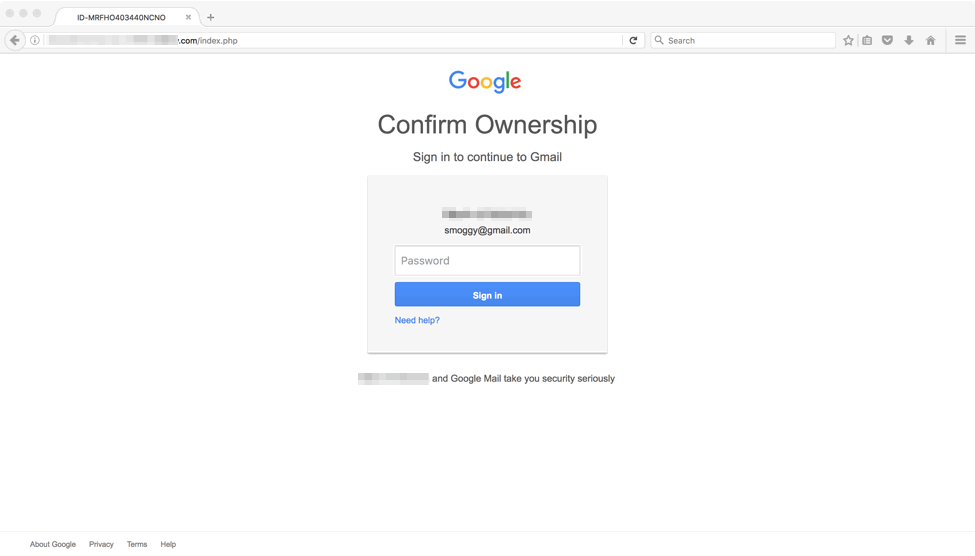
Figure 7: Fake Gmail login page presented as the final step in the phishing attack
If victims instead enter a Yahoo! Email address, they are presented with a similar Yahoo! Login as the final step in the phishing attack.
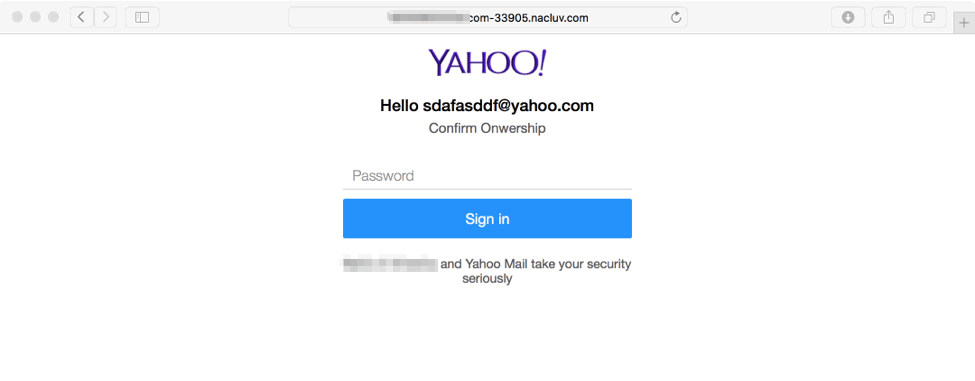
Figure 8: Fake Yahoo! Login presented to victims who enter a Yahoo! Mail address instead of a Gmail address
By this stage of the phish, attackers have captured their victim’s phone number, zip code, email address, and email password. The final stage of the attack brings victims back to the bank phishing site and prompts victims to enter credit card information and their social security number. Even if recipients become suspicious at this point, attackers already have a phone number and access to an associated email account. For many providers, this is enough data to port the phone number away from the original provider and take control of a victim's online identity. In many cases, recipients will also enter credit card data and social security numbers, allowing the attackers to immediately engage in financial fraud and identity theft as well.
Conclusion
SMS phishing like that described here allows attackers to potentially reach large numbers of users with virtually no filtering or protection like that available for email. This attack in particular captures a wide range of information that facilitates both online and financial identity theft by combining multiple phishing steps. This approach means that even of victims do not complete the phish, attackers gain incremental bits of useful information. Given the vulnerabilities associated with this attack vector, mobile users must be especially vigilant against a new wave of SMS phishing.

