It feels like much longer now, but it was just over a year ago when Proofpoint joined forces with three other leading security companies (CrowdStrike, Netskope and Okta) in the Spectra Alliance to create an integrated solution that would help make the shift to remote work as simple and secure as possible. Over the last year, the Spectra Alliance has grown beyond this core focus of securing the remote workforce to building out a framework and integrations that will help organizations accelerate their journey to Zero Trust.
To help all our customers better understand their paths to Zero Trust, the Spectra Alliance has created an on-demand webinar titled, “Your Journey to Zero Trust: What You Wish You Knew Before You Started.” In this joint webinar, a panel of executive leaders from each of the four Spectra Alliance partners discusses the critical role that Zero Trust plays in security modernization and explores the factors organizations should consider, the approaches and options available, and recommendations to begin their journey to Zero Trust.
Elements of Zero Trust
For example, one factor to consider is that scoping Zero Trust generally involves six key elements: identities, devices, applications, data, networks and infrastructure. While not all six are always mandatory, the Spectra Alliance has developed a framework around these elements to help you better understand each one and how each partner and our integrations can help you realize a Zero Trust outcome.
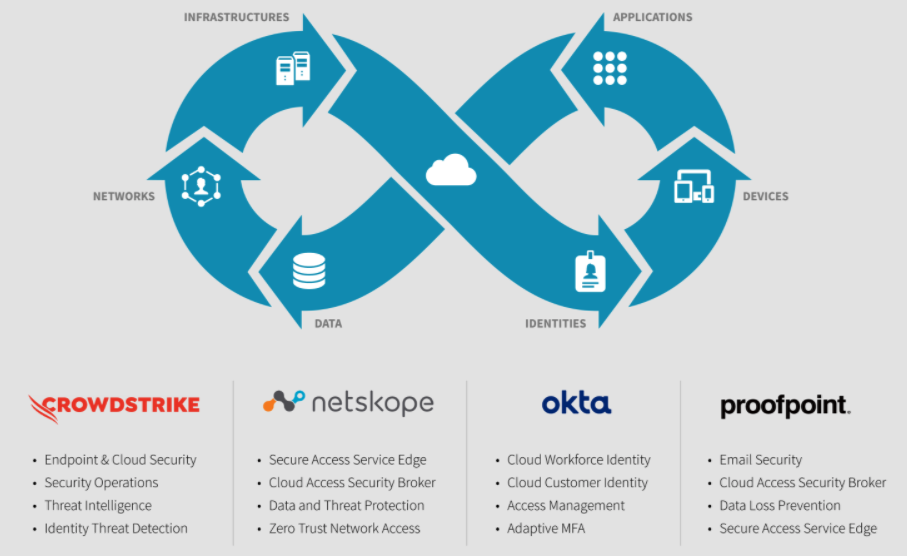
As part of our Zero Trust strategy, Proofpoint provides email and web security, browser isolation, cloud access security broker, enterprise data loss prevention, security service edge and zero trust network access.
Other key questions the Spectra Alliance addresses include the following:
Is Zero Trust right for my organization?
While Zero Trust is a broad initiative, there are a few factors for organizations to consider that would make them especially well-suited for Zero Trust:
- Does your organization have a highly distributed workforce and device ecosystem?
- Do you have a multi-generational, hybrid operating environment?
- Do you have a broad data management landscape and data ownership?
How do I choose the right approach to Zero Trust?
Like so many security frameworks of the past, virtually every security vendor has a Zero Trust story. The Spectra Alliance has broken down four different approaches and provided guidelines for how to think about your strategy and choose which of the approaches is right for your organization and goals:
- Diversified
- Consolidated
- Strategic
- Managed
How does the Spectra Alliance enable a better Zero Trust architecture?
Through the joint research and collaborations that have emerged because of the Spectra Alliance, Proofpoint can help organizations to:
- Increase coverage, for both distributed and in-office scenarios
- Reduce risk against modern and evolving threats
- Reduce costs by streamlining resources, staff and operations
- Deploy frictionlessly, with prebuilt integrations between partners
Some example integrations for Proofpoint within the Spectra Alliance are:
- Proofpoint and CrowdStrike: This integration delivers best-of-breed threat intelligence-sharing and analysis for unparalleled, multi-layered protection for your users and their endpoints, as well as data loss prevention and identity threat protection.
- Proofpoint and Okta: Together, we make security orchestration faster and easier by combining our leading email security and identity solutions. This integration provides accurate, timely responses to stop credential phishing and provide adaptive controls for high-risk users.
Learn more about the Zero Trust approach
To dive even deeper into the various factors and considerations of Zero Trust, download and read the Spectra Alliance e-book, A Strategic Approach to Zero Trust Security.
Also, check out the Proofpoint solution brief, Zero Trust: How to Secure Your Network in the Age of Cloud and Worker Mobility, for our take on how Proofpoint products can help you achieve a Zero Trust architecture.

