In this blog series, we cover how to improve your company’s security posture with actionable insights. Actionable insights are a critical tool to help you improve your security posture and stop initial compromise in the attack chain. You can use them to identify and respond to potential risks, enhance your incident response capabilities and make more informed security decisions.
Figure 1. Steps in the cyberattack chain.
In previous actionable insights blog posts, we covered these topics:
- People risk
- Origin risk
- Business email compromise (BEC) risk
- Ensuring proper risk context
- Risk efficacy
- Telephone-oriented attack delivery (TOAD) risk
- Threat intelligence
- Executive Summary
- Condemnation Summary
In this post, we show you the value of integrating data from Proofpoint Identity Threat Defense into the Proofpoint Targeted Attack Protection (TAP) Dashboard. You can now use this data about your identity risks to stop initial compromise and prevent the lateral movement of threats in your environment.
Get insights about your vulnerable identities
IT and security professionals are always looking for ways to stay ahead of evolving threats and protect their organizations. The TAP Dashboard from Proofpoint has long been a valuable tool in this fight. It provides crucial visibility into email threats and user activity.
Now that the TAP Dashboard uses data from Proofpoint Identity Threat Defense, it has become even more powerful. Rich data about identity risks can help you see the impact of a potential compromise without having to leave the TAP Dashboard.
Let’s explore what this looks like in the dashboard—and how you can use this identity data to strengthen your security posture.
Insights for supercharged visibility
One new addition to the People page in the TAP Dashboard is the Identity Threat Attack Paths column. It reveals the currently available attack paths for each user, which are based on their identified vulnerabilities.
No more digging through separate tools. You can now have a clear picture within the TAP Dashboard of how a threat actor could use each identity to escalate privilege and move laterally.
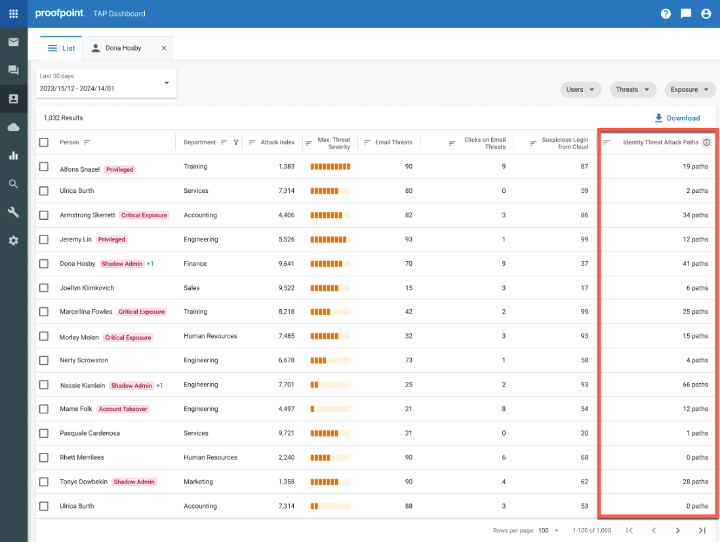
Figure 2. Identity Threat Attack Paths column in the TAP Dashboard.
You can also view identity risk factors for each user. This allows you to gain a deeper understanding of the potential impact of compromise for each user. The metrics you can view include:
- Overall risk exposure
- Number of potential attack paths associated with the user
- Key identity vulnerabilities associated with the user
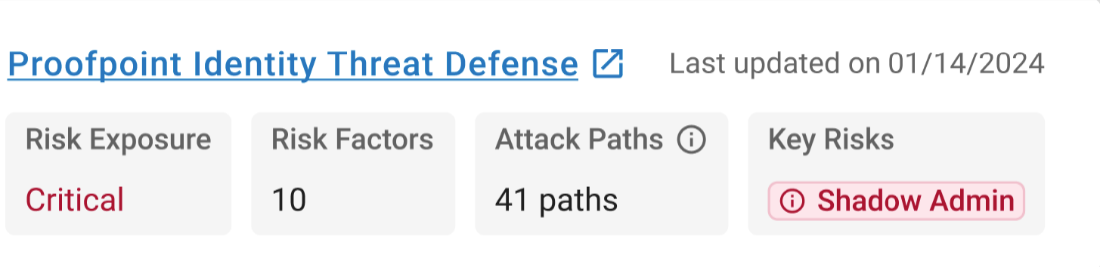
Figure 3. Identity risk factors for individual users.
This data can help you to prioritize your response efforts. You can use it to better focus on securing the identities that might be used to cause the most harm to your business.
Example use case
Take this example of a hypothetical user named Dona Hosby, a 47-year-old finance director. She has access to client accounts and sensitive financial data. Despite her crucial role in the business, Hosby tends to be less cautious about clicking on suspicious email links and attachments.
From the TAP Dashboard, Hosby is identified as a Very Attacked Person™ (VAP) with a high attack index. However, this risk level is not unique to her; others in the company share similar risk levels.
With data enrichment from Proofpoint Identity Threat Defense, the TAP Dashboard shows that Hosby is also a shadow admin, which exposes her to critical risks. A shadow admin is an individual or account that has elevated privileges or access rights that are not in compliance with the company’s security policies.
We can also see the number of lateral attack paths (41) an attacker could take from Hosby’s identity. This information can help the security team to pinpoint which VAPs in the organization pose a higher post-compromise risk. Figures 4 and 5 show what these insights look like in the TAP Dashboard.
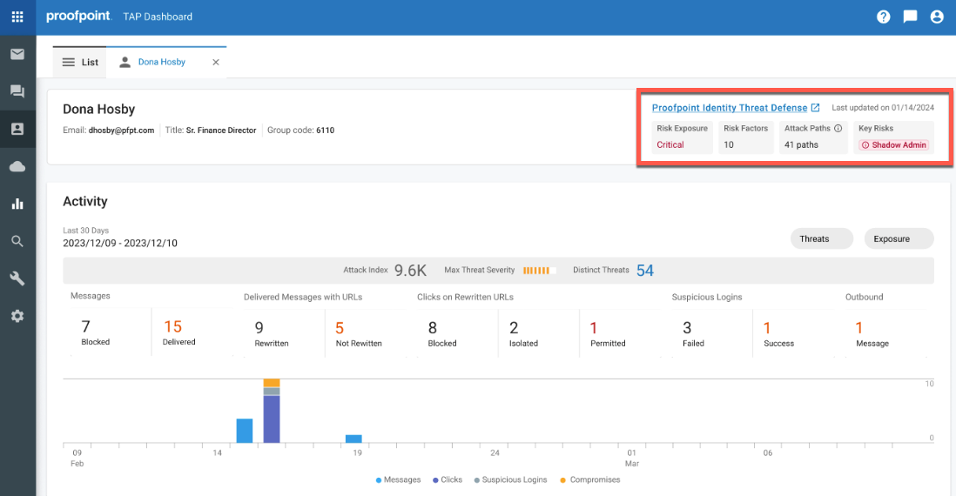
Figure 4: Example identity risk metrics in the TAP Dashboard for Dona Hosby.
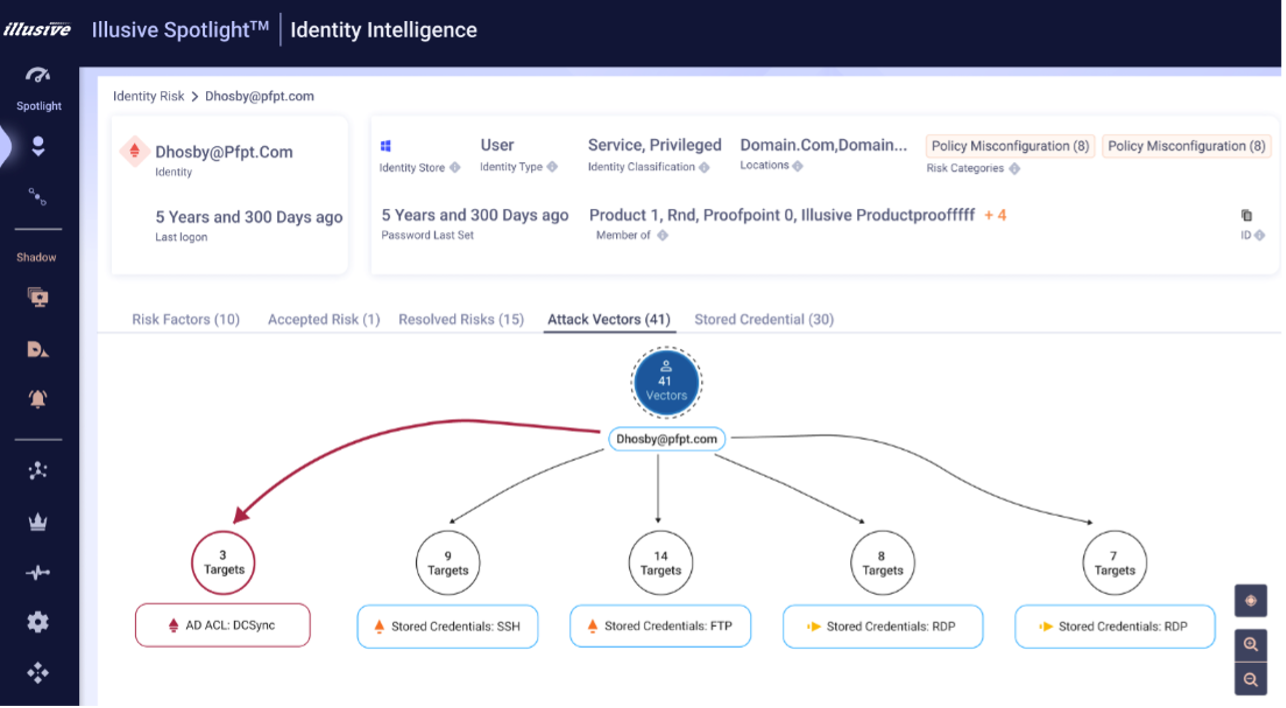
Figure 5. A more detailed view of the 41 Attack Paths for Dona Hosby in Proofpoint Identity Threat Defense.
Insights help you take a proactive approach to security
This integration with Proofpoint Identity Threat Defense isn’t just about visibility. It’s about empowering you to act and break the attack chain before your critical business systems are impacted. Here’s how:
- Increase response efficiency. You can quickly identify high-impact users with delivered malicious messages based on their identity risk score. That allows you to prioritize investigations and incident response, ensuring the most critical threats and key individuals are addressed first.
- Prioritize VAPs. By understanding the potential impact of a compromised VAP, you can make informed decisions about additional security controls, training or monitoring measures.
- Tailor user training. You can equip your users with the knowledge they need to avoid falling victim to attacks. Use the identity data to find users with higher IT privileges and tailor your security awareness training accordingly.
- Implement advanced security controls. For users that are both highly targeted and have a high potential impact, consider deploying advanced security controls like multifactor authentication (MFA), endpoint detection and response (EDR) or more intense monitoring to help mitigate the risk of a successful compromise.
Remember that breaking the attack chain and improving your security posture is about stopping threats before they can reach your most critical IT and business assets. When you use the actionable insights from the Proofpoint Identity Threat Defense integration in your TAP Dashboard, you can:
- Detect and remediate identity vulnerabilities before attackers can exploit them.
- Focus your security efforts on the users and threats that pose the greatest risk.
- Empower your users to make informed decisions and stay safe online.
A holistic view of the threat landscape
This integration is another significant step forward in the ongoing commitment from Proofpoint to provide comprehensive, human-centric security solutions. By combining the power of Proofpoint TAP and Proofpoint Identity Threat Defense, you can gain a holistic view of your threat landscape and get the tools you need to break the attack chain proactively.
Don’t wait to unlock the potential of this powerful new integration. You can explore the new features in your TAP Dashboard today and take control of your email security.
Additional resources
By working together, we can create a safer digital world for everyone. You can learn more about the approach that Proofpoint takes to breaking the attack chain here.
To find out more about Proofpoint Identity Threat Defense, check out this brief.











