Last Time in the BEC Taxonomy Series…
Proofpoint researchers in the second of the Business Email Compromise (BEC) taxonomy series began delving into the Theme tier of the Email Fraud Taxonomy framework (Figure 1), focusing on invoice fraud and demonstrating how the framework works in a real life example. Now we will explore another salient and timely theme category, payroll redirects, which can be of concern this time of year with tax season and the potential for threat actors to target tax refunds in this type of scheme.
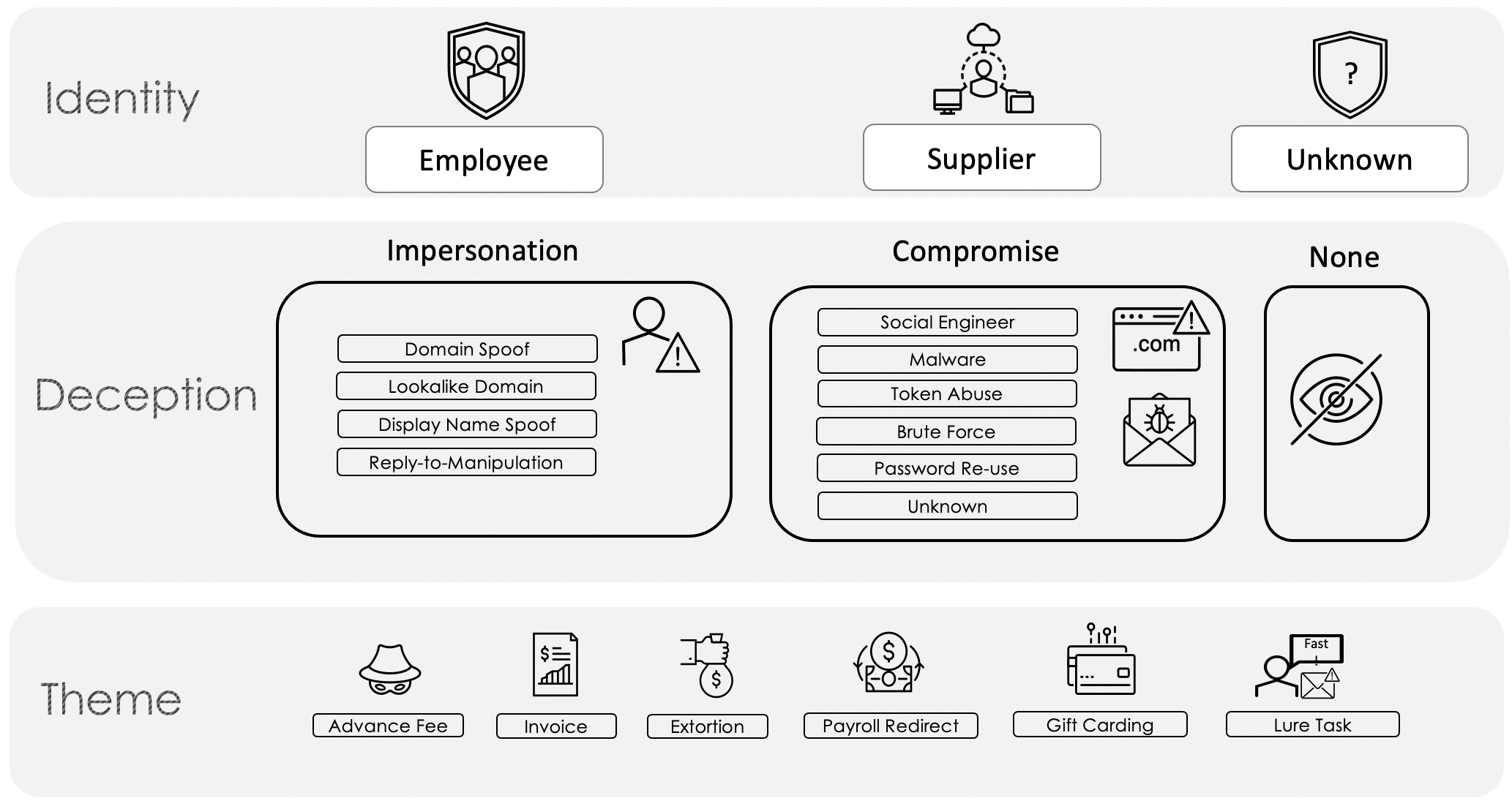
Figure 1. Email Fraud Taxonomy Framework.
What are Payroll Redirects?
Payroll redirects, also called payroll diversions, are email fraud attacks that typically target finance, tax, payroll, and human resources employees. These are some of the simplest attacks as the only goal for the threat actor is to provide new, threat actor-controlled direct deposit information for the impersonated employees’ paycheck or even their tax refund.
Proofpoint detects on average about 2,000 payroll redirect attempts daily (Figure 2) and considers them to be a medium risk to businesses and organizations, with an average loss of $7,904 per incident, according to the FBI Internet Crime Complaint Center’s report on BEC from 2019. The IRS has included payroll redirects on its most recent Dirty Dozen list of tax schemes for 2020, alerting tax filers that fake IRS documents can be used in these schemes to lend credibility to the bank account change requests.
Figure 2. 24-hour view of payroll redirect attempts seen by Proofpoint
Payroll Redirect and the Email Fraud Taxonomy Framework
Payroll redirect schemes can occur via either Deception means (per the Proofpoint Email Fraud Taxonomy Framework in Figure 1 above), impersonation or compromise, but most commonly occur via impersonation. In instances where a threat actor has access to a compromised account, they are more likely to attempt fraud that has the potential for a higher payout, such as an invoice fraud scheme, than a payroll diversion would garner.
Figure 3. Anatomy of a payroll redirect attack via impersonation
Via impersonation (Figure 3), the threat actor sends a generic sounding email from a free mail account using the employee’s name. The use of free mail is by far found in the majority of payroll attacks. Threat actors in payroll redirects also like to impersonate individuals higher up in the target’s organization, such as a CEO or other executive, for the chance to score a bigger paycheck. In the attempts to redirect senior-level paychecks, threat actors can be seen using email addresses with executive themes in an effort to lend credibility and urgency. In such cases, the Taxonomy Framework would appear as follows (Figure 4):
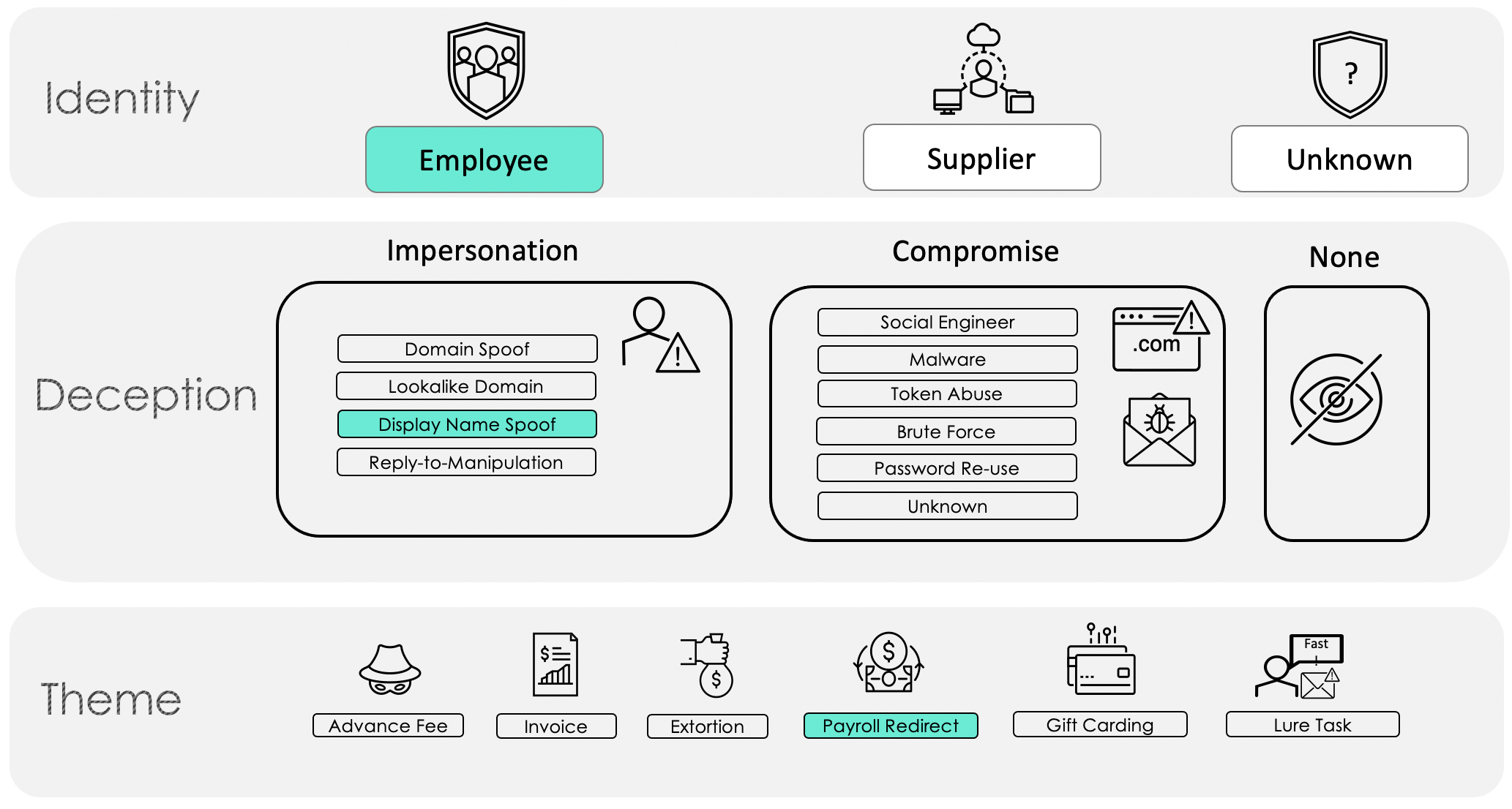
Figure 4. Payroll redirect scheme using a spoofed email display name
Real World Examples
One element that appears universal in payroll redirect schemes is their simplicity. In one of Proofpoint’s recently observed payroll redirect attacks, the threat actor sent a number of emails to individuals in the Payroll department of a large company in an attempt to convince them to redirect the salaries of various employees the threat actor was impersonating. Each of the fraudulent emails, as seen in Figure 5, used the same language and only differed in who the email was sent to, who was being impersonated, and the language used (English, German, or Spanish).
Figure 5. Sample of emails impersonating employees in payroll redirect
Such attempts can surprisingly be even simpler and more brazen, such as attempting to impersonate the CEO of a company as in the following example (Figure 6).
Figure 6. Payroll redirect email impersonating a CEO
Despite the low-tech nature of these attacks, they still manage to be effective because they exploit a normal process that Payroll, Finance, Tax, or HR employees commonly receive.
Keep Reading…
In our next BEC blog post we will tackle another category in the Theme tier, extortion.











