North Korean advanced persistent threat set its sights on cryptocurrency. A “pig butchering” victim speaks out. And the latest news on our podcast.
This week on The Threat Hub: TA444 is a North Korean state-sponsored advanced persistent threat (APT) notable for its primary goal of financial gain rather than espionage. Since 2017, the group has targeted cryptocurrency, embracing a start-up mentality that will be familiar to anyone who knows the worlds of Bitcoin and blockchain. In a new Threat Insight post, our researchers explore how this APT has made use of rapid iteration, legitimate cloud services and distribution that borrows heavily from conventional email marketing. And the approach is definitely paying off, with TA444 stealing nearly $400 million in 2021 and more than $1 billion in 2022. Check out the blog for an overview of TA444’s recent tactics, techniques and procedures.
We've covered the topic of “pig butchering” several times now across our podcasts and blogs. In a recent article, City A.M. looked at the problem from the perspective of a U.K.-based victim. The article contains details about how this type of scam unfolds across multiple interactions, with commentary from our Threat Research team about the underlying social engineering techniques.
And on this week’s Five-Minute Forecast, Microsoft takes action against XLL abuse, ransomware profits fall by 40% as a majority refuse to pay, and cyber attackers start the year with a campaign targeting salary adjustments.
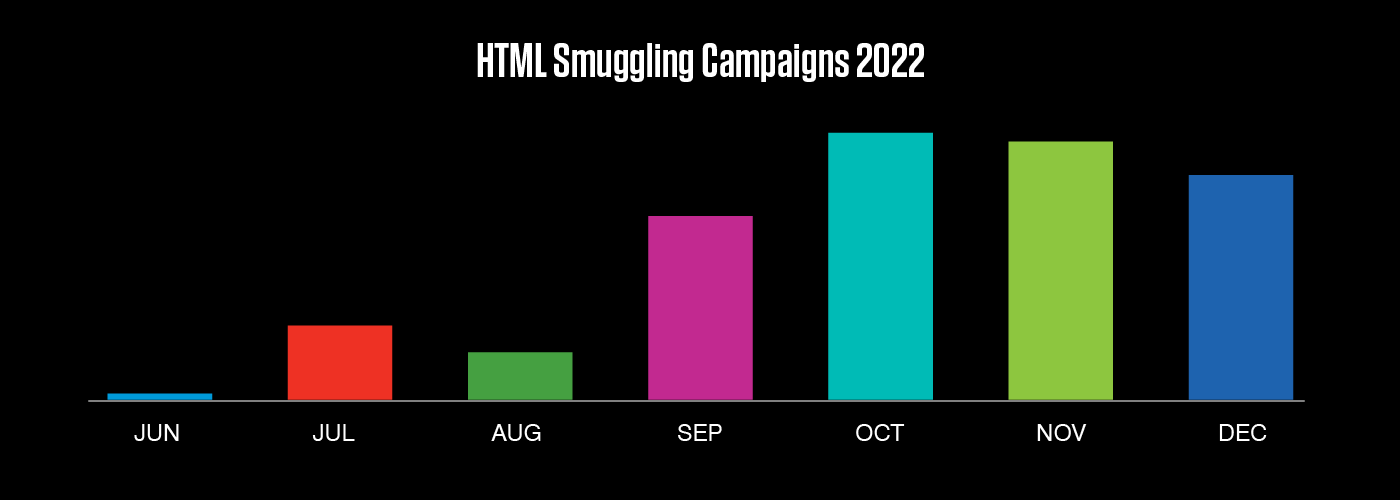
In an HTML Smuggling attack, malicious code is concealed within an HTML document. The technique has been on the rise since Microsoft took action last year to curb use of Office macros to distribute malware. We saw the technique surge during the latter half of 2022, with volume peaking in Q4.
Equip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyberattackers target people. They exploit people. Ultimately, they are people. That’s why the Human Factor report focuses on how technology and psychology combine to make people so susceptible to modern cyber threats. In this first volume, we take a closer look at attacks that rely on social engineering, including business email compromise (BEC) threats, email fraud and phishing.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.


