Recruiters targeted with fake resumes by sophisticated attacker TA4557. And all the latest news on our podcast.
This week on The Threat Hub: Our researchers uncover new activity by threat actor TA4557, targeting recruiters. TA4557 is a skilled, financially motivated attacker that our researchers have been monitoring since 2018. In this campaign, the group responds directly to real-world job listings. The initial email is benign, expressing interest in the role. If the recipient responds, the attack chain commences, ultimately leading to delivery of the more_eggs downloader.
The campaign uses both URLs and attachments (PDF and Word) to deliver malware. In the case of the former, TA4557 includes a link to a bogus resume website. In one instance, the attacker did not include a link at all, but asked the recipient to visit the domain from their email address to access a portfolio. This was probably an attempt to evade automated detection of a suspicious domain. The bogus site uses filtering to qualify potential victims, sending unsuccessful visitors to a plain-text resume. Victims that pass the filter are shown a CAPTCHA which downloads a ZIP file containing an LNK shortcut that initiates the process to ultimately drop more_eggs on the victim’s computer. Check out the full Security Brief for more details, plus a list of IoCs and Emerging Threats signatures.
And on this week’s Five-Minute Forecast, CISA warns of two attacks against U.S. government servers exploiting an unpatched vulnerability in Adobe ColdFusion, Nissan investigates a cyberattack and potential data breach in Australia and New Zealand, and a preview of the next Discarded episode on APT group TA422 from Selena Larson.
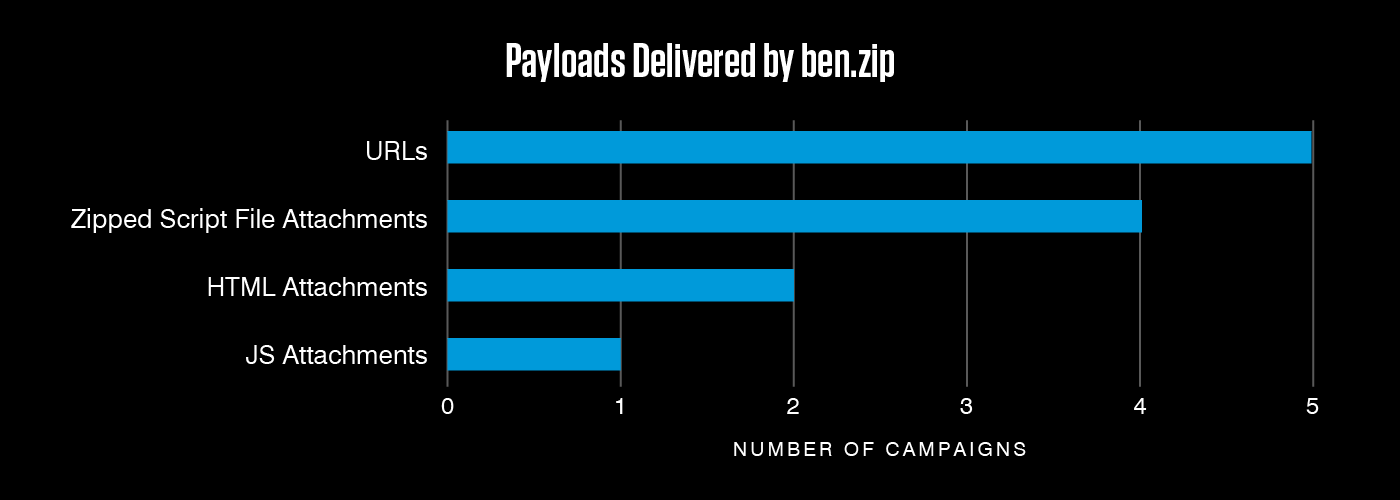
Ben.zip, a new malware kit, has been seen in multiple campaigns delivering AsyncRAT over the past month. With the exception of two campaigns that delivered thousands of messages, most were low volume. The kit can use a range of techniques for delivery, including URLs and multiple attachment types.
Equip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyberattackers target people. They exploit people. Ultimately, they are people. That’s why the Human Factor report focuses on how technology and psychology combine to make people so susceptible to modern cyber threats. In this first volume, we take a closer look at attacks that rely on social engineering, including business email compromise (BEC) threats, email fraud and phishing.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.


