

Stop Human Targeted Attacks
Proven AI Protection, Now via API
Industry-leading threat protection solution—via API or Gateway. 85 of the Fortune 100 trust Proofpoint to stop 99.99% of email security threats before they become compromises
Defend against AI exploits delivered over email.
See the announcements from Protect 2025.
Enhance Microsoft and Google to stop 99.99% of email threats
Proofpoint integrates deeply with Microsoft and Google to deliver advanced email threat protection that goes beyond native controls. Together, we provide stronger, more resilient email security services—so your users stay productive and your organization stays secure.
Nexus, Proofpoint’s Threat Intelligence & AI Platform brings:
Simple. Intuitive. Fully automated.
Watch how Core Email Protection sets up in minutes to stop threats in days
Flexible deployment options that work best for you
API or SEG - Which is right for you?
Some of our customers value comprehensive protection and customization. Others lean into rapid deployment and simple configurations. That’s why Proofpoint offers flexibility in how we enable customers to deploy our email security services—whether that be through a Secure Email Gateway, or via API.
Experience the benefits of our Core Email Protection
Get total visibility
Our unparallelled email threat data provides you with the risk insights you need for rapid investigation and remediation. With our deployment, customers get robust people, organization and threat actor risk data to ensure the SOC is always up to date on risks faced by the organization.
Read our blog on how a customer eliminated blind spots.

Future proof for tomorrow’s threat landscape
We prepare our customers to reduce risk everywhere users interact, today and in the future. Proofpoint helps customers further reduce risk with user and collaboration protection, prevention for accidental and intentional data loss, and integrations across the modern security stack.
Stop the widest variety of advanced threats
We stop the broadest range of email cyberattacks with industry leading precision and intuitive classification. Security admins get visibility into the attack landscape faced by their organization, including the emerging threats and tactics used to reach users.
View our series on stopping BEC, Phishing and Ransomware.

Realize the most efficient SOC
Our platform maximizes automated protection with high efficiency workflows, enabling teams to focus on the most important tasks. Integrated search and alert-based workflows combined with threats summarized by generative AI means more risk reduced in less time.
Read our blog on eliminating guesswork in classifying email threats.

Key features that stop human-targeted attacks
Proofpoint Nexus mitigates risks with AI and threat intelligence
Proofpoint Nexus threat intelligence platform delivers seamless orchestration of advanced AI, machine learning, behavioral analysis, threat intelligence and visual threat detection. By integrating these diverse methods into a cohesive system, Proofpoint Nexus provides a powerful, adaptive defense that dynamically responds to emerging threats.

Up to the minute protection for the risks targeting your people
Our team of threat researchers investigates email threats, tracking new campaigns and threat actor activity within and outside of the Proofpoint ecosystem. Protection against newly discovered threats is automatic, with visibility into threat actors, trends and insight available on-demand.

Seamless experiences for end users
Real time, contextual warnings
We empower your users to make informed decisions on suspicious emails, with in-the-moment contextual warning banners. These include an integrated “report suspicious” button, making it easy to report suspicious messages even on a mobile device.
Intuitive email reporting workflows
We make it easy for users to report suspicious messages across all devices, and communicate that activity back to the submitting user. Once submitted, emails are automatically classified, triaged and remediated. If we discover that a user-reported message is malicious, we’ll automatically remove all instances of it from all user inboxes.

URL & Malware Protection
Organizations continue to receive a barrage of malicious links and attachments via email, which can only be stopped with advanced email security. Predictive sandboxing, URL extraction, evasion detection and browser isolation are just some of the advanced techniques we use to achieve the highest efficacy defense against malicious payloads.

Business Email Compromise (BEC) Protection
Zero payload impersonation attacks like BEC attacks are among the most challenging to detect due to the possibility of legitimacy. The Nexus Relationship Graph (RG) and Language Model (LM) engines conduct an AI based analysis, while leveraging header attribute mismatches, a DMARC feedback loop, and sender behavior insights to stop BEC in its tracks.
TOAD Protection
Also known as callback Phishing, Telephone Oriented Attack Delivery (TOAD) encourages recipients to move from email and onto a phone call. The Nexus Machine Learning (ML) and Computer Vision (CV) engines detect known threat behavior, including the presence of malicious phone numbers, QR codes and image-based impersonations to detect and block TOAD attacks.
Automated protection
For all email, internal and external
Proofpoint scans email from external and internal senders, ensuring that emails from all sources are checked for indicators of compromise. When internal communications are flagged for anomalies, Proofpoint provides adaptive controls to mitigate the risks of an account takeover.
Automated Quarantine Post-Delivery
If a malicious message is detected post-delivery, we automatically move it to quarantine. And we follow forwarded mail and distribution lists.
Click time protection
Our secure email gateway re-writes URLs to protect users on any network and device to detect if a message has been weaponized post-delivery. When users click on re-written URLs, automated browser isolation and real-time sandboxing protect against malware and credential theft.
We’re recognized as an industry leader by leading analyst firms and customers alike.

A Leader in the 2025 Gartner® Magic Quadrant™ for Email Security

Proofpoint Recognized as Overall Market Leader Frost Radar™: Email Security, 2024
Proofpoint is the only vendor that delivers on all five areas for email security as an integrated platform. — Gartner
Proofpoint gives us automated, continually updated threat intelligence that goes into the system. … It also gives us granular insight into different types of BEC threats.
Because it’s so accurate and does such good job at stopping stuff that’s bad, we don’t have to assign resources to go in and do specific individual investigations all of the time.
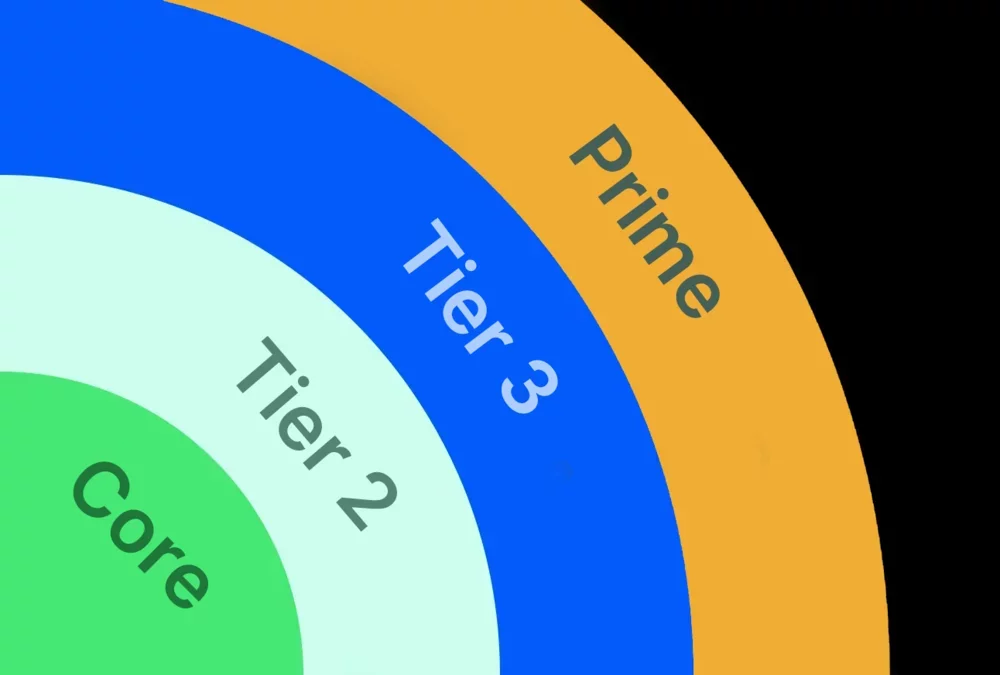
Future proof with Proofpoint Collaboration Security Prime
Collaboration Security Prime
Proofpoint Collaboration Security Prime is our premium solution for protecting trusted interactions and stopping AI-scaled attacks across multiple channels and stages. Built on our industry-leading email security, Prime extends protection beyond email to messaging and collaboration tools, cloud applications, and the supply chain—all through a single, integrated platform."
Request a demo
Learn how our integrated platform helps you:
-
Stop cyberattacks
-
Prevent data loss
-
Reduce human risk across your environment















