Last week attackers exploited Coronavirus fears by sending malicious health information emails aimed at Japanese-language speakers. This week Proofpoint researchers uncovered new Coronavirus-themed email attacks that focus on concerns around disruptions to global shipping. In this latest notable effort, attackers are nearly exclusively targeting industries that are particularly susceptible to shipping disruptions including manufacturing, industrial, finance, transportation, pharmaceutical, and cosmetic companies (in that order).
While this specific Coronavirus-themed email campaign is narrow in its focus, it features malicious Microsoft Word documents, exploits a two-and-a-half-year-old vulnerability, and installs AZORult, an information stealing malware. The malware actors doing this appear to be from Russia and Eastern Europe, and while they aren't part an APT group, they clearly understand the economic concerns surrounding the Coronavirus. All emails with Coronavirus-themes and attachments should be treated with caution, even if they don’t appear to be directly health related.
A Coronavirus-related shipping supply disruption would negatively impact each of the company types listed above and it’s clear these attackers are aware that a major event like Coronavirus can have secondary impacts on industries. This awareness demonstrates not just technical sophistication, but economic sophistication as well. In addition to the health concerns around Coronavirus, there are increased concerns globally about Coronavirus’ potential economic and international supply chain impact.
Below is an example of this targeted email campaign:
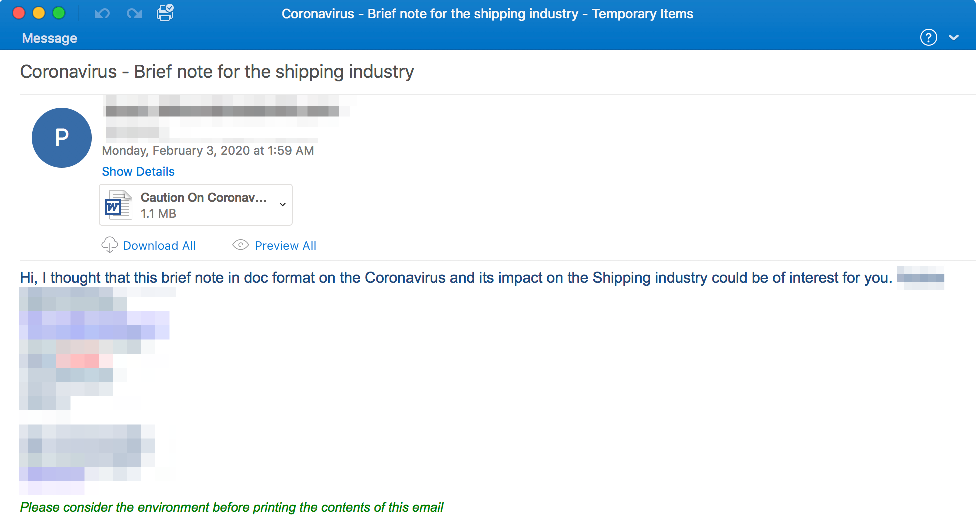
Figure 1 Coronavirus-theme Shipping Industry Lure
The Microsoft Word document that’s attached seeks to exploit a two-and-a-half year-old Microsoft Office vulnerability (CVE-2017-11882) which leverages Equation Editor. This vulnerability has been used in malicious documents by multiple threat actors in multiple attacks over the past two-and-a-half years. Its use in this campaign likely points to its proven effectiveness in other attacks and the attacker’s belief that the industries they’re targeting are slow to deploy patches.
Once the document is opened it installs AZORult which is information stealing malware we’ve seen since at least 2016. In late 2018, we also saw AZORult being used in sextortion scams with ransomware. In these attacks, we don’t see AZORult downloading ransomware currently. However, because of AZORult’s configurable nature and past use in conjunction with ransomware that remains a real threat.
In light of this latest attack, organizations that have concerns around global shipping should exercise extra caution around Coronavirus-themed emails. People and organizations broadly should be exercising extreme caution around any emails, links or websites related to Coronavirus because of the demonstrated, increased risk that attackers will seek to use concerns around it as lures.

